實驗需求:
- 需求一拓撲:
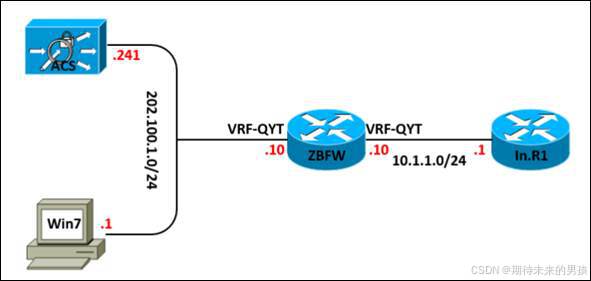
按照以上拓撲所示,完成以下需求:
- 參考以上拓撲,配置設備IP地址,使用UNL里Secure第四天拓撲即可。(有興趣的同學課后也可按照PPT原拓撲做做實驗);
- 配置Zone-Base Policy Firewall,Zone Nname為Inside/Outside,并配置VRF,名字為QYT,監控Inbound的ICMP/Telnet流量;
- 內部地址10.1.1.1靜態一對一轉換到外部地址202.100.1.101;
- 配置User-Base FW,Username=user1,Group=group1,監控PC去往10.1.1.1的HTTP流量;
- 配置Radius,在滿足需求4的同時,Reset掉uri中的“who”關鍵字。
設備配置:
1) 參考以上拓 ,配置設備 IP 地址,使用 UNL 里 Secure 第四 撲即可。
bridge irb
bridge 1 protocol ieee
bridge 1 route ip
!
zone security 2-inside
zone security 2-outside
zone security inside
zone security outside
zone security DMZ
class-map type inspect match-any in-out
?match protocol icmp
?match protocol tcp
class-map type inspect match-any 2-in-out
?match protocol icmp
?match protocol tcp
!!
policy-map type inspect in-out
?class type inspect in-out
? inspect
?class class-default
? drop
policy-map type inspect 2-in-out
?class type inspect 2-in-out
? inspect
?class class-default
? drop
!
zone security 2-inside
zone security 2-outside
zone security inside
zone security outside
zone security DMZ
zone-pair security in-out source inside destination outside
?service-policy type inspect in-out
zone-pair security 2-in-out source 2-inside destination 2-outside
?service-policy type inspect 2-in-out
zone-pair security 1-2 source inside destination DMZ
?service-policy type inspect 2-in-out
!
interface FastEthernet0/0
?ip address 10.1.1.10 255.255.255.0
?zone-member security inside
?duplex half
!
interface FastEthernet1/0
?ip address 202.100.1.10 255.255.255.0
?zone-member security outside
?duplex half
!
interface FastEthernet2/0
?no ip address
?zone-member security 2-inside
?duplex half
?bridge-group 1
!
interface FastEthernet3/0
?no ip address
?zone-member security 2-outside
?duplex half
?bridge-group 1
!
interface BVI1
?ip address 192.168.1.10 255.255.255.0
?zone-member security DMZ
測試:
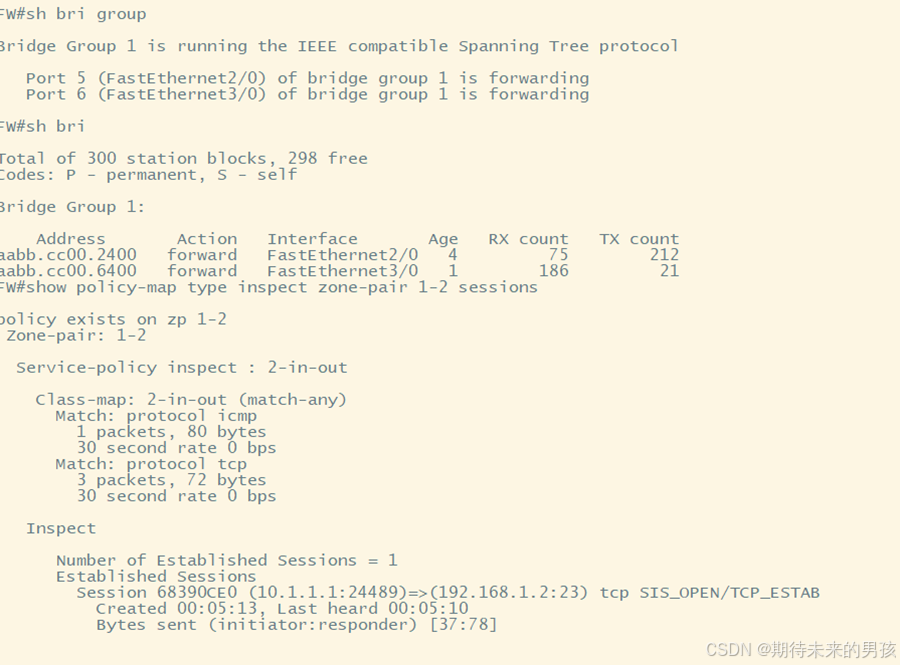
5-7層過濾
ip access-list extended in-out
??? 10 permit ip 10.1.1.0 0.0.0.255 202.100.1.0 0.0.0.255
class-map type inspect match-all in-out
?match access-group name in-out
?match protocol http
parameter-map type regex shrun
?pattern [Ss][Hh]/[Rr][Uu][Nn]
class-map type inspect http match-any in-out.http
?match? request uri regex shrun
?match? request header length gt 4096
?match? req-resp protocol-violation
!
policy-map type inspect http in-out-http-1
?class type inspect http in-out.http
? reset
? log
policy-map type inspect in-out-http.policy
?class type inspect in-out
? inspect
? service-policy http in-out-http-1
?class class-default
? drop
!
zone-pair security in-out-http source inside destination outside
?service-policy type inspect in-out-http.policy
測試
*Apr 18 12:34:12.678: %APPFW-4-HTTP_URI_REGEX_MATCHED: URI regex ([Ss][Hh]/[Rr][Uu][Nn]) matched - resetting session 10.1.1.2:49215 202.100.1.1:80 on zone-pair in-out-http class in-out appl-class in-out.http
*Apr 18 12:35:51.826: %APPFW-4-HTTP_PROTOCOL_VIOLATION: HTTP protocol violation (0) detected - resetting session 10.1.1.1:22772 202.100.1.1:80 on zone-pair in-out-http class in-out appl-class in-out.http
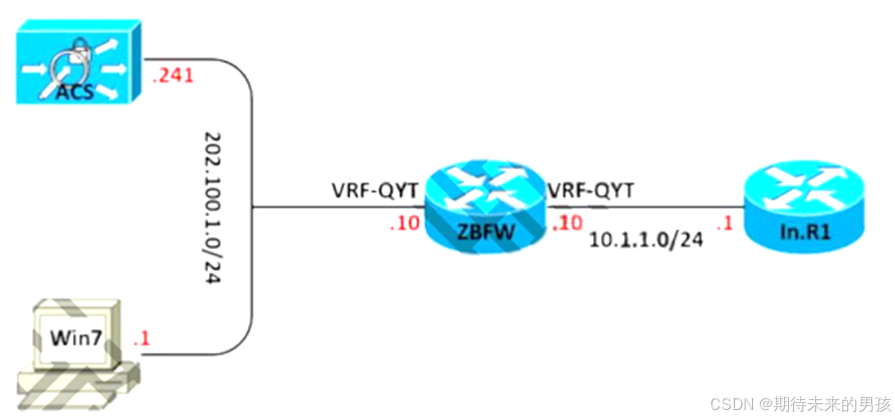
2) 配置 Zon -Base Policy Firewall,Zone Nname 為 Inside/Outside,并配置 VRF,名字為 QYT,監控 Inbound 的 ICMP/Telnet 流量
class-map type inspect match-any in-out
?match protocol icmp
?match protocol tcp
?match protocol udp
?match protocol ftp
?match protocol telnet
!
policy-map type inspect in-out
?class type inspect in-out
? inspect
?class class-default
? drop
!
zone security insidee
zone security outside
zone-pair security in-out source insidee destination outside
?service-policy type inspect in-out
!
ip vrf QYT??
!
interface FastEthernet2/0
?ip vrf forwarding QYT
?ip address 202.100.1.10 255.255.255.0
?zone-member security outside
?duplex half
!
interface FastEthernet3/0
?ip vrf forwarding QYT
?ip address 10.1.1.10 255.255.255.0
?zone-member security insidee
?duplex half
!
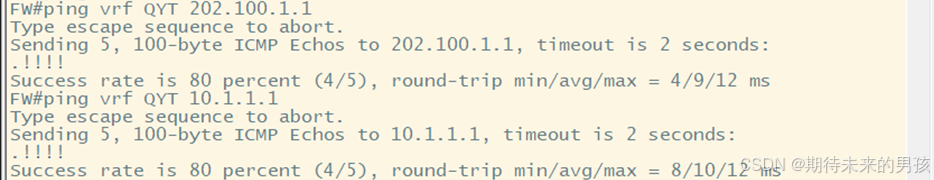
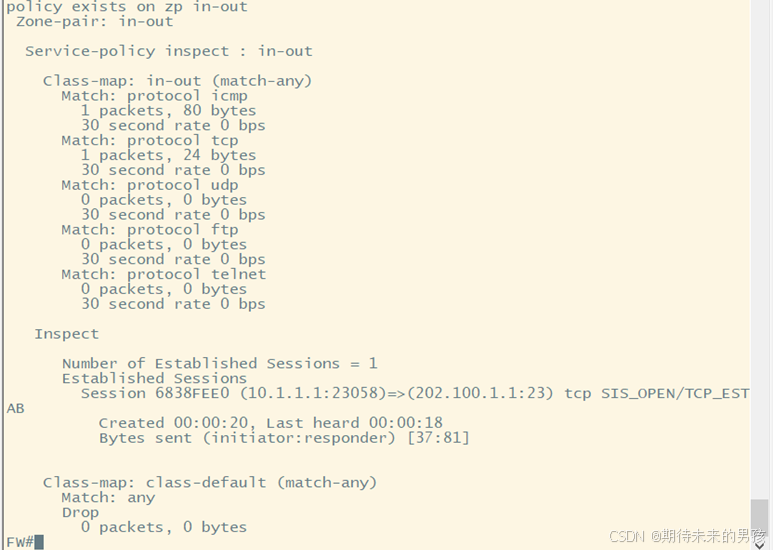
3) 內部地址 10.1.1.1 靜態一對一轉換到外部地址 202.100.1.101
interface FastEthernet2/0
?ip nat outside
!
interface FastEthernet3/0
ip nat inside
!
ip nat inside source static 10.1.1.1 202.100.1.101 vrf QYT extendable match-in-vrf
!
ip access-list extended Outside-to-Inside.telnet
permit tcp any host 10.1.1.1 eq telnet
policy-map type inspect out-in
?class type inspect Outside-to-Inside.telnet
? inspect
?class class-default
? drop!
zone-pair security out-in source outside destination insidee
?service-policy type inspect out-in
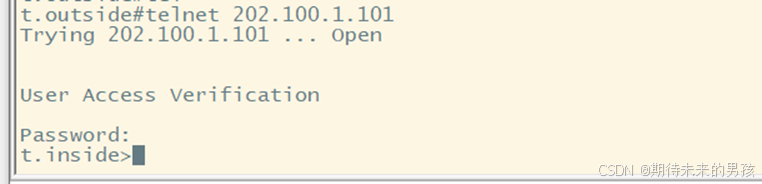
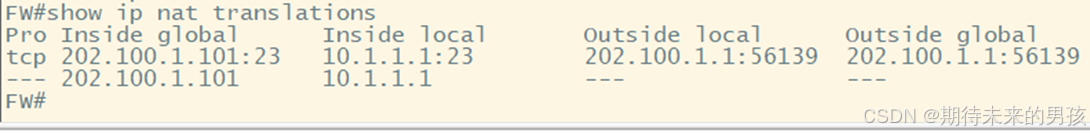
4) 配置 User-Base FW,Use name=user1,Group=group1,監控 PC 去往 10. 1.1.1的 HTTP 流量
ip http server
zone security inside
zone security outside
aaa new-model
!
aaa authentication login default? local
aaa authorization auth-proxy default local
!
aaa attribute list user1
?attribute type supplicant-group "group1"
!
username user1 privilege 15 password 0 cisco
username user1 aaa attribute list user1
!
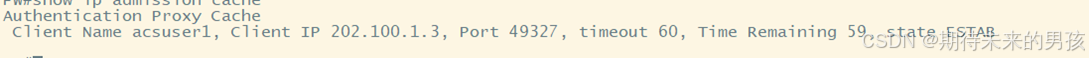
ip admission name qytanng proxy http
!
interface FastEthernet0/0
?ip address 202.100.1.10 255.255.255.0
?ip admission qytanng
?zone-member security outside
?duplex half
!
class-map type inspect match-all out-in-http
?match protocol http
?match user-group group1
class-map type inspect match-all out-in-icmp
?match protocol icmp
?match user-group group1
!
policy-map type inspect out-in
?class type inspect out-in-icmp
? inspect
?class type inspect out-in-http
? inspect
zone-pair security out-in source outside destination inside
service-policy type inspect out-in
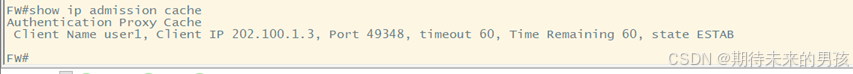
5) 配置 Radius,在滿足需求 4 的同時,Reset掉 uri 中的“who”關鍵字
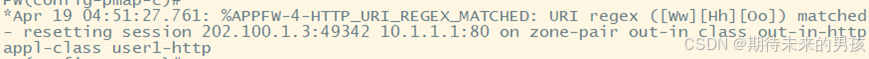
parameter-map type regex who
?pattern [Ww][Hh][Oo]
class-map type inspect http match-all user1-http
?match? request uri regex who
!
policy-map type inspect out-in
class type inspect out-in-http
? inspect
? service-policy http user1-http.p
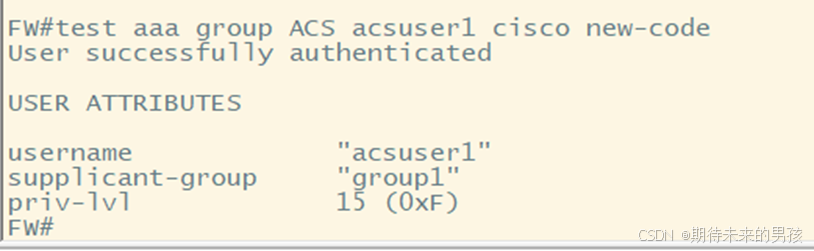
aaa group server radius ACS
?server-private 202.100.1.4 key cisco
aaa authentication login default group ACS
aaa authorization auth-proxy default group ACS








(模擬)(對各位進行拆解))




)


)


