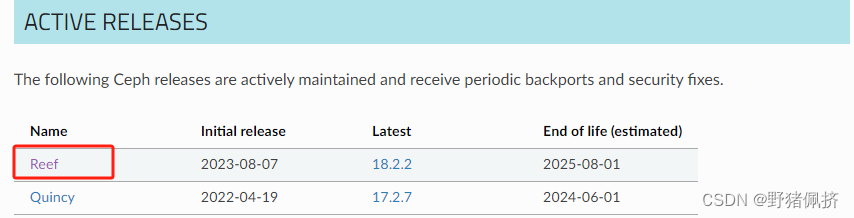
當前ceph
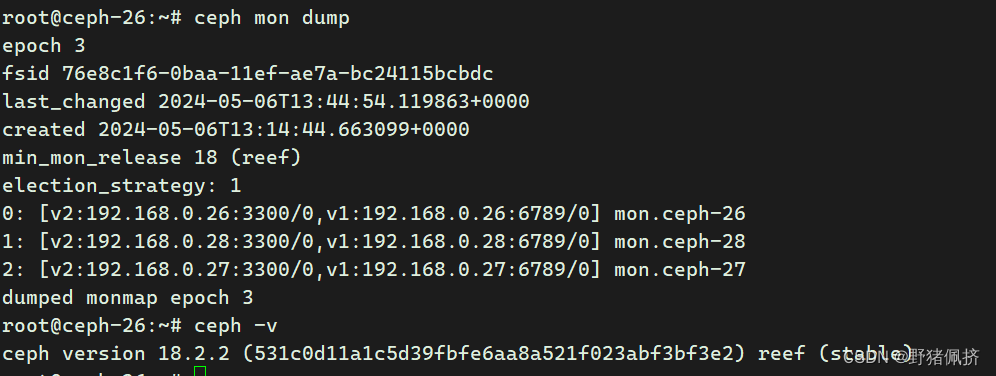
你的ceph集群上執行
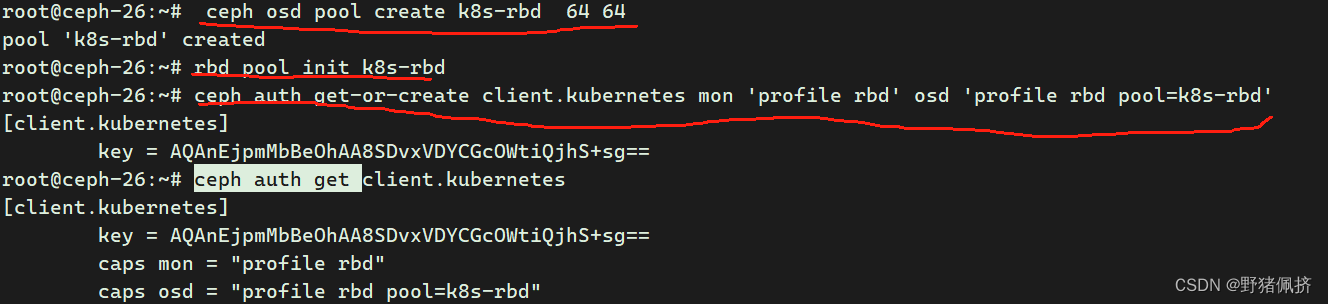
1.創建名為k8s-rbd 的存儲池
ceph osd pool create k8s-rbd 64 642.初始化
rbd pool init k8s-rbd3 創建k8s訪問塊設備的認證用戶
ceph auth get-or-create client.kubernetes mon 'profile rbd' osd 'profile rbd pool=k8s-rbd'
部署 ceph-rbd-csi
cat <<EOF > csi-config-map.yaml
---
apiVersion: v1
kind: ConfigMap
data:config.json: |-[{"clusterID": "76e8c1f6-0baa-11ef-ae7a-bc24115bcbdc","monitors": ["192.168.0.26:6789","192.168.0.27:6789","192.168.0.28:6789"]}]
metadata:name: ceph-csi-config
EOF###說明###
"clusterID": "76e8c1f6-0baa-11ef-ae7a-bc24115bcbdc" 通過 ceph mon dump 中的 fsid 獲取
創建名為“ceph-csi-encryption-kms-config”的ConfigMap,因沒有使用KMS,配置內容為空(不能省略,否則后面容器啟動會報錯
cat <<EOF > csi-kms-config-map.yaml
---
apiVersion: v1
kind: ConfigMap
data:config.json: |-{}
metadata:name: ceph-csi-encryption-kms-config
EOF
最新版本的Ceph - CSI還需要另一個ConfigMap對象來定義Ceph配置,以添加到CSI容器內的Ceph .conf文件中:
cat <<EOF > ceph-config-map.yaml
---
apiVersion: v1
kind: ConfigMap
data:ceph.conf: |[global]auth_cluster_required = cephxauth_service_required = cephxauth_client_required = cephxkeyring: |
metadata:name: ceph-config
EOF
創建 secret對象,存儲訪問ceph的 key
cat <<EOF > csi-rbd-secret.yaml
---
apiVersion: v1
kind: Secret
metadata:name: csi-rbd-secretnamespace: default
stringData:userID: kubernetesuserKey: AQAnEjpmMbBeOhAA8SDvxVDYCGcOWtiQjhS+sg==
EOF###說明###
userID 為上面在 ceph 集群中創建的 kubernetes
userKey 通過下面獲取,這里無需通過 base64 加密,切記!# ceph auth get client.kubernetes
[client.kubernetes]key = AQAnEjpmMbBeOhAA8SDvxVDYCGcOWtiQjhS+sg==caps mon = "profile rbd"caps osd = "profile rbd pool=k8s-rbd"
再部署官網提供的yaml文件
$ kubectl apply -f https://raw.githubusercontent.com/ceph/ceph-csi/master/deploy/rbd/kubernetes/csi-provisioner-rbac.yaml
$ kubectl apply -f https://raw.githubusercontent.com/ceph/ceph-csi/master/deploy/rbd/kubernetes/csi-nodeplugin-rbac.yaml$ wget https://raw.githubusercontent.com/ceph/ceph-csi/master/deploy/rbd/kubernetes/csi-rbdplugin-provisioner.yaml
$ kubectl apply -f csi-rbdplugin-provisioner.yaml$ wget https://raw.githubusercontent.com/ceph/ceph-csi/master/deploy/rbd/kubernetes/csi-rbdplugin.yaml
$ kubectl apply -f csi-rbdplugin.yaml
創建SC
cat <<EOF > csi-rbd-sc.yaml
---
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:name: csi-rbd-sc
provisioner: rbd.csi.ceph.com
parameters:clusterID: 76e8c1f6-0baa-11ef-ae7a-bc24115bcbdcpool: k8s-rbd <<<<<<<<<<<<<<<<<---------------(注意你的池)imageFeatures: layeringcsi.storage.k8s.io/provisioner-secret-name: csi-rbd-secretcsi.storage.k8s.io/provisioner-secret-namespace: defaultcsi.storage.k8s.io/controller-expand-secret-name: csi-rbd-secretcsi.storage.k8s.io/controller-expand-secret-namespace: defaultcsi.storage.k8s.io/node-stage-secret-name: csi-rbd-secretcsi.storage.k8s.io/node-stage-secret-namespace: default
reclaimPolicy: Delete
allowVolumeExpansion: true
mountOptions:- discard
EOF
####創建一個pvc 試一試
cat <<EOF > raw-block-pvc.yaml
---
apiVersion: v1
kind: PersistentVolumeClaim
metadata:name: raw-block-pvc
spec:accessModes:- ReadWriteOncevolumeMode: Blockresources:requests:storage: 1GistorageClassName: csi-rbd-sc
EOF
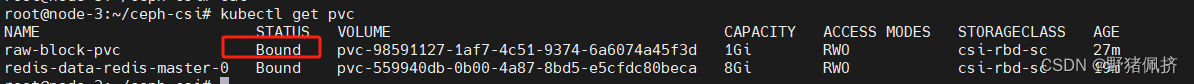
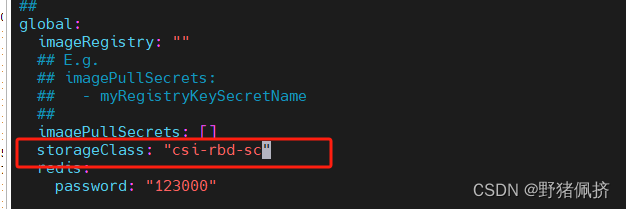
helm在部署一個redis





銷售數據排行榜)

)









:Pandas餐飲信息表分析——交叉表、離群點分析,多維分析等高級操作)

