1、身份認證與權限
前面我們在操作k8s的所有請求都是通過https的方式進行請求,通過REST協議操作我們的k8s接口,所以在k8s中有一套認證和鑒權的資源。
- Kubenetes中提供了良好的多租戶認證管理機制,如RBAC、ServiceAccount還有各種策路等。
- 通過該文件可以看到已經配置了RBAC訪問控制
- /usr/lib/systemd/system/kube-apiserver.service
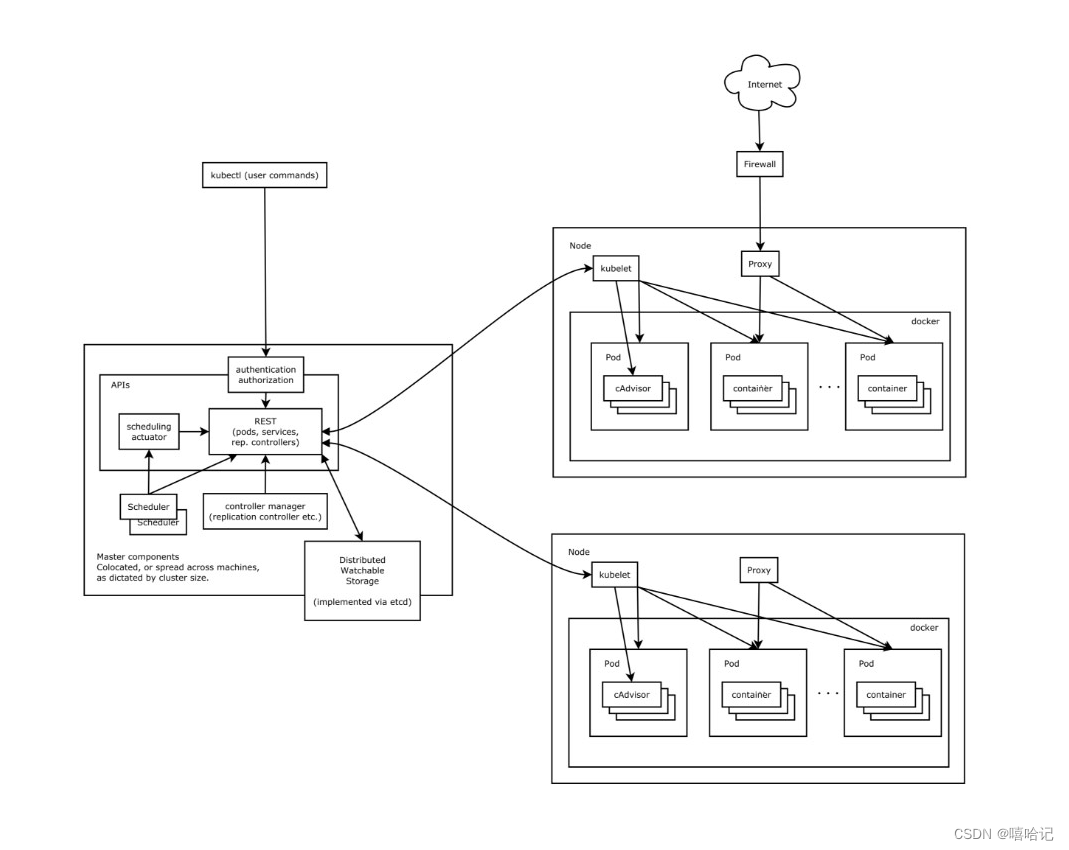
2、認證
所有kubernetes集群有兩類用戶:由Kubernetes管理的ServiceAccounts(服務賬戶)和(Users Accounts)普通賬戶。
- 普通賬戶是假定被外部或獨立服務管理的,由管理員分配key,用戶像使用Keystone或google賬號一樣,被存儲在包含usernames和passwords的list的文件里。
- 需要注意:在Kubernetes中不能通過API調用將普通用戶添加到集群中。
- 普通帳戶是針對(人)用戶的,服務賬戶針對Pod進程。
- 普通帳戶是全局性。在集群所有namespaces中,名稱具有唯一性。
- 通常,集群的普通帳戶可以與企業數據庫同步,新的普通帳戶創建需要特殊權限。服務賬戶創建目的是更輕量化,允許集群用戶為特定任務創建服務賬戶。
- 普通帳戶和服務賬戶的審核注意事項不同。
- 對于復雜系統的配置包,可以包括對該系統的各種組件的服務賬戶的定義。
2.1 服務賬戶的控制器(Service Account Adminssion Controller)
通過Admission Controller插件來實現對pod修改,它是apiserver的一部分,創建或更新pod時會同步進行修改pod,當插件處于激活狀態(在大多數發行版中都默認情況)創建或修改pod時,會按以下操作執行:
- 1.如果pod沒有設置ServiceAccount,則將ServiceAccount設置為default。
- 2.如果pod引用的ServiceAccount存在,否則將會拒絕請求。
- 3.如果pod不包含任何ImagePullSecrets,則將ServiceAccount的ImagePullSecrets會添加到pod中。
- 4.為包含API訪問的Token的pod添加了一個volume。
- 5.把volumeSource添動加到安裝在pod的每個容器中,掛載/var/run/secrets/kubernetes.io/serviceaccount。
2.2 服務賬戶的控制器(Token Controller)
API的訪問是基于token的認證,創建對應的service account 都會關聯到對應的token,這個是由Token Controller來進行管理的。Pod去訪問API的時候是需要證明具有相對應的權限的。
2.3 服務賬戶的控制器(Service Account Controller)
Service Account Controller在namespaces里管理ServiceAccount,并確保每個有效的namespaces中都存在一個名為"default"的ServiceAcount。
2.4 拓展命令
[root@k8s-master ~]# kubectl get sa
NAME SECRETS AGE
default 0 9d
[root@k8s-master ~]# kubectl get serviceaccounts
NAME SECRETS AGE
default 0 9d[root@k8s-master ~]# kubectl get serviceaccounts --all-namespaces
NAMESPACE NAME SECRETS AGE
default default 0 9d
ingress-nginx default 0 3d19h
ingress-nginx ingress-nginx 0 3d17h
kube-flannel default 0 9d
kube-flannel flannel 0 9d
kube-node-lease default 0 9d
kube-public default 0 9d
kube-system attachdetach-controller 0 9d
kube-system bootstrap-signer 0 9d
kube-system certificate-controller 0 9d
kube-system clusterrole-aggregation-controller 0 9d
kube-system coredns 0 9d
kube-system cronjob-controller 0 9d
kube-system daemon-set-controller 0 9d
kube-system default 0 9d
kube-system deployment-controller 0 9d
kube-system disruption-controller 0 9d
kube-system endpoint-controller 0 9d
kube-system endpointslice-controller 0 9d
kube-system endpointslicemirroring-controller 0 9d
kube-system ephemeral-volume-controller 0 9d
kube-system expand-controller 0 9d
kube-system generic-garbage-collector 0 9d
kube-system horizontal-pod-autoscaler 0 9d
kube-system job-controller 0 9d
kube-system kube-proxy 0 9d
kube-system metrics-server 0 4d15h
kube-system namespace-controller 0 9d
kube-system nfs-client-provisioner 0 40h
kube-system node-controller 0 9d
kube-system persistent-volume-binder 0 9d
kube-system pod-garbage-collector 0 9d
kube-system pv-protection-controller 0 9d
kube-system pvc-protection-controller 0 9d
kube-system replicaset-controller 0 9d
kube-system replication-controller 0 9d
kube-system resourcequota-controller 0 9d
kube-system root-ca-cert-publisher 0 9d
kube-system service-account-controller 0 9d
kube-system service-controller 0 9d
kube-system statefulset-controller 0 9d
kube-system token-cleaner 0 9d
kube-system ttl-after-finished-controller 0 9d
kube-system ttl-controller 0 9d
3、鑒權
3.1 Role 普通角色
代表一個角色,會包含一組權限,沒有拒絕規則,只是附加允許。它是Namespaces級別的資源,只能作用與Namespace之內,不可以跨命名空間使用。
- 查看已有的角色信息
- kubectl get role -n ingress-nginx nginx-ingress-role -o yaml
[root@k8s-master ~]# kubectl get role -n ingress-nginx ingress-nginx -oyaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role # 角色
metadata:annotations:meta.helm.sh/release-name: ingress-nginxmeta.helm.sh/release-namespace: ingress-nginxcreationTimestamp: "2024-02-25T11:35:57Z"labels:app.kubernetes.io/component: controllerapp.kubernetes.io/instance: ingress-nginxapp.kubernetes.io/managed-by: Helmapp.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginxapp.kubernetes.io/version: 1.9.6helm.sh/chart: ingress-nginx-4.9.1name: ingress-nginxnamespace: ingress-nginxresourceVersion: "482050"uid: a0df64a1-2e1b-4daf-b777-c7afcc23669crules: # 規則,可以根據角色對一些資源做什么操作
- apiGroups: # api分組- ""resources: # 資源- namespaces # 增對命名空間verbs: # 動作- get # 獲取命名空間的信息
- apiGroups: - ""resources:- configmaps - pods- secrets- endpointsverbs:- get - list- watch
- apiGroups:- ""resources:- servicesverbs:- get- list- watch
- apiGroups:- networking.k8s.ioresources:- ingressesverbs:- get- list- watch
- apiGroups:- networking.k8s.ioresources:- ingresses/statusverbs:- update
- apiGroups:- networking.k8s.ioresources:- ingressclassesverbs:- get- list- watch
- apiGroups:- coordination.k8s.ioresourceNames:- ingress-nginx-leaderresources:- leasesverbs:- get- update
- apiGroups:- coordination.k8s.ioresources:- leasesverbs:- create
- apiGroups:- ""resources:- eventsverbs:- create- patch
- apiGroups:- discovery.k8s.ioresources:- endpointslicesverbs:- list- watch- get
[root@k8s
3.2 ClusterRole 兄弟角色
功能與Role一樣,區別是資源類型為集群類型,而Role只在Namespace。
- 查看某個集群角色的信息
- kubectl get clusterrole view -oyaml
[root@k8s-master ~]# kubectl get clusterrole
NAME CREATED AT
admin 2024-02-19T14:04:43Z
cluster-admin 2024-02-19T14:04:43Z
edit 2024-02-19T14:04:43Z
flannel 2024-02-19T15:33:13Z
ingress-nginx 2024-02-25T11:35:57Z
kubeadm:get-nodes 2024-02-19T14:04:44Z
nfs-client-provisioner-runner 2024-02-27T12:25:28Z
system:aggregate-to-admin 2024-02-19T14:04:43Z
system:aggregate-to-edit 2024-02-19T14:04:43Z
system:aggregate-to-view 2024-02-19T14:04:43Z
system:aggregated-metrics-reader 2024-02-24T13:26:02Z
system:auth-delegator 2024-02-19T14:04:43Z
system:basic-user 2024-02-19T14:04:43Z
system:certificates.k8s.io:certificatesigningrequests:nodeclient 2024-02-19T14:04:43Z
system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 2024-02-19T14:04:43Z
system:certificates.k8s.io:kube-apiserver-client-approver 2024-02-19T14:04:43Z
system:certificates.k8s.io:kube-apiserver-client-kubelet-approver 2024-02-19T14:04:43Z
system:certificates.k8s.io:kubelet-serving-approver 2024-02-19T14:04:43Z
system:certificates.k8s.io:legacy-unknown-approver 2024-02-19T14:04:43Z
system:controller:attachdetach-controller 2024-02-19T14:04:43Z
system:controller:certificate-controller 2024-02-19T14:04:43Z
system:controller:clusterrole-aggregation-controller 2024-02-19T14:04:43Z
system:controller:cronjob-controller 2024-02-19T14:04:43Z
system:controller:daemon-set-controller 2024-02-19T14:04:43Z
system:controller:deployment-controller 2024-02-19T14:04:43Z
system:controller:disruption-controller 2024-02-19T14:04:43Z
system:controller:endpoint-controller 2024-02-19T14:04:43Z
system:controller:endpointslice-controller 2024-02-19T14:04:43Z
system:controller:endpointslicemirroring-controller 2024-02-19T14:04:43Z
system:controller:ephemeral-volume-controller 2024-02-19T14:04:43Z
system:controller:expand-controller 2024-02-19T14:04:43Z
system:controller:generic-garbage-collector 2024-02-19T14:04:43Z
system:controller:horizontal-pod-autoscaler 2024-02-19T14:04:43Z
system:controller:job-controller 2024-02-19T14:04:43Z
system:controller:namespace-controller 2024-02-19T14:04:43Z
system:controller:node-controller 2024-02-19T14:04:43Z
system:controller:persistent-volume-binder 2024-02-19T14:04:43Z
system:controller:pod-garbage-collector 2024-02-19T14:04:43Z
system:controller:pv-protection-controller 2024-02-19T14:04:43Z
system:controller:pvc-protection-controller 2024-02-19T14:04:43Z
system:controller:replicaset-controller 2024-02-19T14:04:43Z
system:controller:replication-controller 2024-02-19T14:04:43Z
system:controller:resourcequota-controller 2024-02-19T14:04:43Z
system:controller:root-ca-cert-publisher 2024-02-19T14:04:43Z
system:controller:route-controller 2024-02-19T14:04:43Z
system:controller:service-account-controller 2024-02-19T14:04:43Z
system:controller:service-controller 2024-02-19T14:04:43Z
system:controller:statefulset-controller 2024-02-19T14:04:43Z
system:controller:ttl-after-finished-controller 2024-02-19T14:04:43Z
system:controller:ttl-controller 2024-02-19T14:04:43Z
system:coredns 2024-02-19T14:04:45Z
system:discovery 2024-02-19T14:04:43Z
system:heapster 2024-02-19T14:04:43Z
system:kube-aggregator 2024-02-19T14:04:43Z
system:kube-controller-manager 2024-02-19T14:04:43Z
system:kube-dns 2024-02-19T14:04:43Z
system:kube-scheduler 2024-02-19T14:04:43Z
system:kubelet-api-admin 2024-02-19T14:04:43Z
system:metrics-server 2024-02-24T13:26:02Z
system:monitoring 2024-02-19T14:04:43Z
system:node 2024-02-19T14:04:43Z
system:node-bootstrapper 2024-02-19T14:04:43Z
system:node-problem-detector 2024-02-19T14:04:43Z
system:node-proxier 2024-02-19T14:04:43Z
system:persistent-volume-provisioner 2024-02-19T14:04:43Z
system:public-info-viewer 2024-02-19T14:04:43Z
system:service-account-issuer-discovery 2024-02-19T14:04:43Z
system:volume-scheduler 2024-02-19T14:04:43Z
view 2024-02-19T14:04:43Z
[root@k8s-master ~]# kubectl get clusterrole ingress-nginx -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:annotations:meta.helm.sh/release-name: ingress-nginxmeta.helm.sh/release-namespace: ingress-nginxcreationTimestamp: "2024-02-25T11:35:57Z"labels:app.kubernetes.io/instance: ingress-nginxapp.kubernetes.io/managed-by: Helmapp.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginxapp.kubernetes.io/version: 1.9.6helm.sh/chart: ingress-nginx-4.9.1name: ingress-nginxresourceVersion: "482047"uid: 8f7e381f-75a3-4d6e-90f0-13e6ce14e1ae
rules:
- apiGroups:- ""resources:- configmaps- endpoints- nodes- pods- secrets- namespacesverbs:- list- watch
- apiGroups:- coordination.k8s.ioresources:- leasesverbs:- list- watch
- apiGroups:- ""resources:- nodesverbs:- get
- apiGroups:- ""resources:- servicesverbs:- get- list- watch
- apiGroups:- networking.k8s.ioresources:- ingressesverbs:- get- list- watch
- apiGroups:- ""resources:- eventsverbs:- create- patch
- apiGroups:- networking.k8s.ioresources:- ingresses/statusverbs:- update
- apiGroups:- networking.k8s.ioresources:- ingressclassesverbs:- get- list- watch
- apiGroups:- discovery.k8s.ioresources:- endpointslicesverbs:- list- watch- get
3.3 RoleBinding 命名空間級別角色權限綁定
Role或ClusterRole只是用于制定權限集合,具體作用與什么對象上,需要使用RoleBinding來進行綁定。
作用于Namespace內,可以將Role或ClusterRole綁定到User、Group、Service Account上.
-
查看rolebinding信息
-
kubectl get rolebinding --all-namespaces
-
查看指定rolebinding的配置信息
-
kubectl get rolebinding <role_binding_name> --all-namespaces
-oyaml
[root@k8s-master ~]# kubectl get rolebinding --all-namespaces
NAMESPACE NAME ROLE AGE
default leader-locking-nfs-client-provisioner Role/leader-locking-nfs-client-provisioner 41h
ingress-nginx ingress-nginx Role/ingress-nginx 3d17h
kube-public kubeadm:bootstrap-signer-clusterinfo Role/kubeadm:bootstrap-signer-clusterinfo 9d
kube-public system:controller:bootstrap-signer Role/system:controller:bootstrap-signer 9d
kube-system kube-proxy Role/kube-proxy 9d
kube-system kubeadm:kubelet-config Role/kubeadm:kubelet-config 9d
kube-system kubeadm:nodes-kubeadm-config Role/kubeadm:nodes-kubeadm-config 9d
kube-system metrics-server-auth-reader Role/extension-apiserver-authentication-reader 4d16h
kube-system system::extension-apiserver-authentication-reader Role/extension-apiserver-authentication-reader 9d
kube-system system::leader-locking-kube-controller-manager Role/system::leader-locking-kube-controller-manager 9d
kube-system system::leader-locking-kube-scheduler Role/system::leader-locking-kube-scheduler 9d
kube-system system:controller:bootstrap-signer Role/system:controller:bootstrap-signer 9d
kube-system system:controller:cloud-provider Role/system:controller:cloud-provider 9d
kube-system system:controller:token-cleaner Role/system:controller:token-cleaner 9d
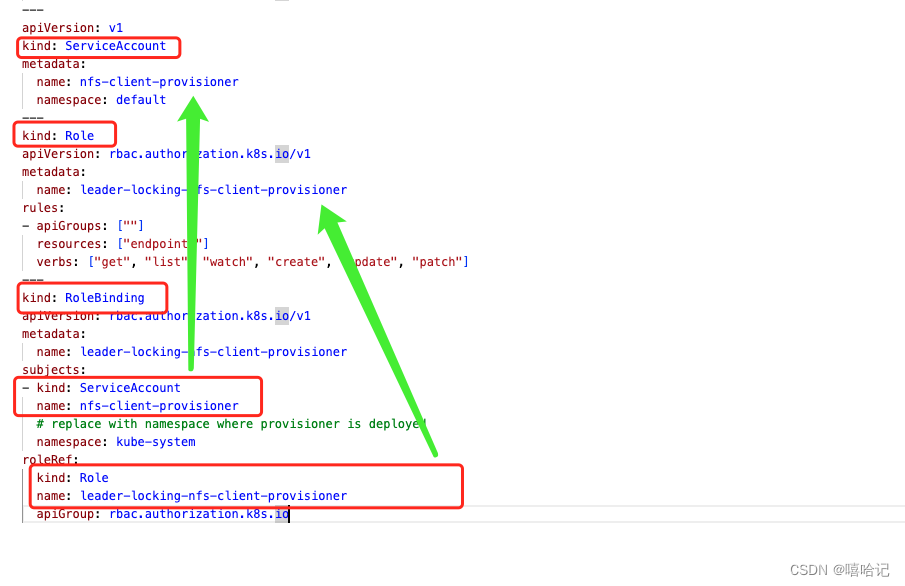
3.4 ClusterRoleBinding 集群角色權限的綁定
- 查看ClusterRoleBinding信息
- kubectl get clusterrolebinding
- 查看指定ClusterRoleBinding的配置信息
- kubectl get clusterrolebinding <clusterrole_binding_name> -o yaml
[root@k8s-master ~]# kubectl get clusterrolebinding
NAME ROLE AGE
cluster-admin ClusterRole/cluster-admin 9d
flannel ClusterRole/flannel 9d
ingress-nginx ClusterRole/ingress-nginx 3d18h
kubeadm:get-nodes ClusterRole/kubeadm:get-nodes 9d
kubeadm:kubelet-bootstrap ClusterRole/system:node-bootstrapper 9d
kubeadm:node-autoapprove-bootstrap ClusterRole/system:certificates.k8s.io:certificatesigningrequests:nodeclient 9d
kubeadm:node-autoapprove-certificate-rotation ClusterRole/system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 9d
kubeadm:node-proxier ClusterRole/system:node-proxier 9d
metrics-server:system:auth-delegator ClusterRole/system:auth-delegator 4d16h
run-nfs-client-provisioner ClusterRole/nfs-client-provisioner-runner 41h
system:basic-user ClusterRole/system:basic-user 9d
system:controller:attachdetach-controller ClusterRole/system:controller:attachdetach-controller 9d
system:controller:certificate-controller ClusterRole/system:controller:certificate-controller 9d
system:controller:clusterrole-aggregation-controller ClusterRole/system:controller:clusterrole-aggregation-controller 9d
system:controller:cronjob-controller ClusterRole/system:controller:cronjob-controller 9d
system:controller:daemon-set-controller ClusterRole/system:controller:daemon-set-controller 9d
system:controller:deployment-controller ClusterRole/system:controller:deployment-controller 9d
system:controller:disruption-controller ClusterRole/system:controller:disruption-controller 9d
system:controller:endpoint-controller ClusterRole/system:controller:endpoint-controller 9d
system:controller:endpointslice-controller ClusterRole/system:controller:endpointslice-controller 9d
system:controller:endpointslicemirroring-controller ClusterRole/system:controller:endpointslicemirroring-controller 9d
system:controller:ephemeral-volume-controller ClusterRole/system:controller:ephemeral-volume-controller 9d
system:controller:expand-controller ClusterRole/system:controller:expand-controller 9d
system:controller:generic-garbage-collector ClusterRole/system:controller:generic-garbage-collector 9d
system:controller:horizontal-pod-autoscaler ClusterRole/system:controller:horizontal-pod-autoscaler 9d
system:controller:job-controller ClusterRole/system:controller:job-controller 9d
system:controller:namespace-controller ClusterRole/system:controller:namespace-controller 9d
system:controller:node-controller ClusterRole/system:controller:node-controller 9d
system:controller:persistent-volume-binder ClusterRole/system:controller:persistent-volume-binder 9d
system:controller:pod-garbage-collector ClusterRole/system:controller:pod-garbage-collector 9d
system:controller:pv-protection-controller ClusterRole/system:controller:pv-protection-controller 9d
system:controller:pvc-protection-controller ClusterRole/system:controller:pvc-protection-controller 9d
system:controller:replicaset-controller ClusterRole/system:controller:replicaset-controller 9d
system:controller:replication-controller ClusterRole/system:controller:replication-controller 9d
system:controller:resourcequota-controller ClusterRole/system:controller:resourcequota-controller 9d
system:controller:root-ca-cert-publisher ClusterRole/system:controller:root-ca-cert-publisher 9d
system:controller:route-controller ClusterRole/system:controller:route-controller 9d
system:controller:service-account-controller ClusterRole/system:controller:service-account-controller 9d
system:controller:service-controller ClusterRole/system:controller:service-controller 9d
system:controller:statefulset-controller ClusterRole/system:controller:statefulset-controller 9d
system:controller:ttl-after-finished-controller ClusterRole/system:controller:ttl-after-finished-controller 9d
system:controller:ttl-controller ClusterRole/system:controller:ttl-controller 9d
system:coredns ClusterRole/system:coredns 9d
system:discovery ClusterRole/system:discovery 9d
system:kube-controller-manager ClusterRole/system:kube-controller-manager 9d
system:kube-dns ClusterRole/system:kube-dns 9d
system:kube-scheduler ClusterRole/system:kube-scheduler 9d
system:metrics-server ClusterRole/system:metrics-server 4d16h
system:monitoring ClusterRole/system:monitoring 9d
system:node ClusterRole/system:node 9d
system:node-proxier ClusterRole/system:node-proxier 9d
system:public-info-viewer ClusterRole/system:public-info-viewer 9d
system:service-account-issuer-discovery ClusterRole/system:service-account-issuer-discovery 9d
system:volume-scheduler ClusterRole/system:volume-scheduler 9d
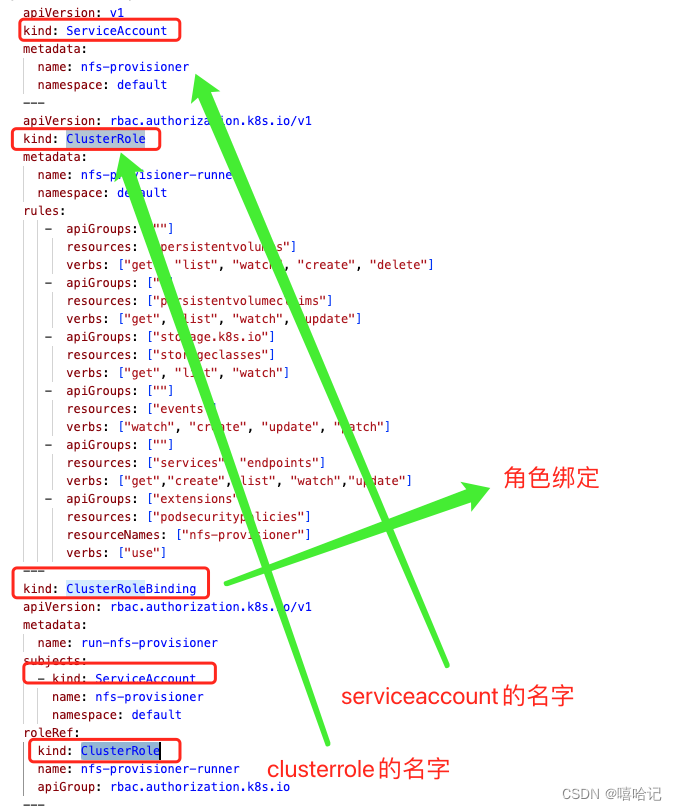








——垃圾回收、析構與IDisposable)






)



)