CA認證中心簡述
CA :CertificateAuthority的縮寫,通常翻譯成認證權威或者認證中心,主要用途是為用戶發放數字證書
功能:證書發放、證書更新、證書撤銷和證書驗證。
作用:身份認證,數據的不可否認性
端口:443
證書請求文件:CSR是Cerificate Signing Request的英文縮寫,即證書請求文件,也就是證書申請者在申請數字證書時由CSP(加密服務提供者)在生成私鑰的同時也生成證書請求文件,證書申請者只要把CSR文件提交給證書頒發機構后,證書頒發機構使用其根證書的私鑰簽名就生成了證書文件,也就是頒發給用戶的證書
一:搭建CA認證中心
配置一個自己的CA認證中心
[root@ca?~]#?vim?/etc/pki/tls/openssl.cnf?+?basicConstraints=CA:FALSE? #?把FALSE改成TRUE?把本機變成CA認證中心
配置認證中心,生成私鑰與根證書
[root@ca?~]#?/etc/pki/tls/misc/CA?-newca

這里配置了CA認證中心 ,在里面就生成了CA認證根證書的私鑰 ,在配置完結束之后 ,就會生成一個根證書,這個根證書中有這證書的公鑰
到此CA認證中心就搭建好了
查看生成的CA根證書 :
[root@ca?~]#?vim?/etc/pki/CA/cacert.pem Certificate:Data:Version:??()Serial?Number:d5:bc:ed::bb:7c:a9:3bSignature?Algorithm:?sha256WithRSAEncryptionIssuer:?C=CN,?ST=beijing,?O=IT,?OU=IT-OPS,?CN=damowang.cn/emailAddress=damowang.cn@gmail.com#?上面是CA認證中心信息Validity Not?Before:?Aug???::??GMTNot?After?:?Aug???::??GMTSubject:?C=CN,?ST=beijing,?O=IT,?OU=IT-OPS,?CN=damowang.cn/emailAddress=damowang.cn@gmail.com Subject?Public?Key?Info: #?CA認證中心公鑰信息Public?Key?Algorithm:?rsaEncryptionPublic-Key:?(?bit)Modulus:????????????????????:bc:f2:4e:b3:ac:cf:ec:c7:6c:9a:7f::8f:ab:bc:b0:2f:b6::a7:cd:::a6::f3::3a::8c:d5:::3a:::da:9f:ae:5d:b0:c1::3e:8f:9e:::2b::b5::d3:8e:c0:de::7d:e2:????????????????????:::6c:bf:b2::dc:::b0:a5:2e::a4:????????????????????::::6e::f7:8e:3a:d5:ab::cb:5b::????????????????????????????ee:a4:e9:e6:6c:ae:::d2:a0::db:b7:::f5:0e::3f:8c:a6:e8::5b:a1::da:1a:ec::????????????????????:::::9e::f0:3e::ea:a1:ff:::c0:b1:::5f::6e::c4:8d:e5:a2:b4::ff:6d:b3:2b:db:::fa:a6::d5::ec:ba::d4:f3:::e9::c0:ba:f4:5b::e5:f5:f7:::dc::bc::6b:2b:0e:::::3c:2a::a0:????????????????????::::af:ee::d5:3b::::cd:b2:ab:fa::5d::eb:8a:e5:3c::a2:3b:e3:8b:d0::6e:::0d::6b::e4:::5d:bc::da:4b:4f:d2:c8:::c6:c3:b8:b5:eb:e3:ff::f5::????????????????????:edExponent:??()X509v3?extensions:X509v3?Subject?Key?Identifier:????????????????::C9:B3:C1:BF:F9:4D:D4:::BC:9B:A5:C0:CC:6B:D9:5D:BDX509v3?Authority?Key?Identifier:keyid:::C9:B3:C1:BF:F9:4D:D4:::BC:9B:A5:C0:CC:6B:D9:5D:BDX509v3?Basic?Constraints:CA:TRUESignature?Algorithm:?sha256WithRSAEncryption?????????:f7::3b:::::2e:ad:f6:af::4c:8b::ac::?????????:8d::8b::6a:b8:1e::b0:5d:c1:ee:d2:c6:a6:1e::4d::b6::2e:c3::a4:f0:f9:9e:d4:2f:c2::::5e:b3::::b4::1f:3d:cb:d7:2f:f8::6e:a5:8a:e6:f6:8f::aa:4b:9a::b5:0e:db:::0b:8a:9b:2b::6d::c0::8f:cd:::::d5:4f:4f:8e:eb:7a::2c:::8e::1c::3a:e8::b4:2e::4a:a4::1a::8d::d9:b5:6e::::::::a4:ac:1b:::::6f:8b:a9:ff:d4:d2:7e:9c:8f:4a:c7::e7::2b::::5f::6c::2d:b5:a7:1d:0c:f1:a2:d8::2c::::3c::9c:?????????:d4:1a:d1:7b:a3:7f:f6:::e3::f1:7e:::af::2b::6d:cb:af:d0::ad:e4::1c:ee:b9::d8::::7b::ba::ac::f1::c0::2e:::::7b::8f:?????????::::b3:a4:::b9::ef:0b::7f:::bf:2f:?????????::9b:d6-----BEGIN?CERTIFICATE-----MIIDxTCCAq2gAwIBAgIJANW87VS7fKk7MA0GCSqGSIb3DQEBCwUAMHkxCzAJBgNV BAYTAkNOMRAwDgYDVQQIDAdiZWlqaW5nMQswCQYDVQQKDAJJVDEPMA0GA1UECwwG SVQtT1BTMRQwEgYDVQQDDAtkYW1vd2FuZy5jbjEkMCIGCSqGSIb3DQEJARYVZGFt b3dhbmcuY25AZ21haWwuY29tMB4XDTE4MDgwNjE0NTMxNFoXDTIxMDgwNTE0NTMx NFoweTELMAkGA1UEBhMCQ04xEDAOBgNVBAgMB2JlaWppbmcxCzAJBgNVBAoMAklU MQ8wDQYDVQQLDAZJVC1PUFMxFDASBgNVBAMMC2RhbW93YW5nLmNuMSQwIgYJKoZI hvcNAQkBFhVkYW1vd2FuZy5jbkBnbWFpbC5jb20wggEiMA0GCSqGSIb3DQEBAQUA A4IBDwAwggEKAoIBAQC88k6zrM/sx2yafyWPq7ywL7Y2p80mgqZH85I6iIzViEQ6 lCfan65dsME0Po+eNxArZbVA047A3lR94iQVB2y/siHcFjCwpS5UpEOGaABu3/eO OtWr38tbI+6k6eZsrpdw0qAI27cXI/UOMD+MpugIW6EB2hrsGBgxURAUnt3wPnLq of9UR8CxAzBfOG4xxI3lorQy/22zK9tgQvqmctVy7LoY1PNAcukWwLr0WyDl9feF UtwBvGFrKw5AOYRFPCo3oGk4knev7nbVO3DMNM2yq/p5XXjriuU8lKI744vQl25U hQ3daxLkdYJdvBbaS0/SyGZ2xsO4tevj/2n1lWDtAgMBAAGjUDBOMB0GA1UdDgQW BBSJUcmzwb/5TdRRc7ybpcDMa9ldvTAfBgNVHSMEGDAWgBSJUcmzwb/5TdRRc7yb pcDMa9ldvTAMBgNVHRMEBTADAQH/MA0GCSqGSIb3DQEBCwUAA4IBAQCQ9xQ7MjFi iC6t9q8nTItSrAOYjUeLSGq4HmCwXcHu0samHldNZLZlLsOBpPD5ntQvwjkYg16z cISRtJMfPcvXL/h2bqWK5vaPAKpLmoS1DttSGQuKmytZbSDAQo/NhYUJeNVPT47r eiMsA1mONhwROugmtC5FSqRFGlCNF9m1bmaHZpk2cUikrBto3TkUb4up/9TSfpyP SsdA5xMrMomIX4NsmC21px0M8aLYkyxwhAA8AZwg1BrRe6N/9mZ34yfxfkNUr5Ar h23Lr9BDreSAHO65Ith0OCR7MLoRrBTxAsASLhZT3ZV7WI9SdDhms6QgcLkn7wtJ fyaVvy9jAZvW-----END?CERTIFICATE-----
查看根證書的私鑰 :
[root@ca?~]#?vim?/etc/pki/CA/private/cakey.pem????#?CA認證下根證書的私鑰-----BEGIN?ENCRYPTED?PRIVATE?KEY-----????????????????????????????????????????????????????????MIIFDjBABgkqhkiG9w0BBQ0wMzAbBgkqhkiG9w0BBQwwDgQInT7FONSpFscCAggA MBQGCCqGSIb3DQMHBAi1VvUPV2DgKwSCBMjHCgsNdj+BrCSvkFaHtX6iGaitR7WJ bBEWrarlcGGVdAHYW6Hwpb548FXXLhXagTcU1gj6EP8ylJ5+ZsQtXM6B/HlzX+c6 TKTdS4QBotFUqb2BRZkN0Une4k17RxDNW6Por4OEEk4hs6xpr0up5ihV5L2H3JWw Q+9zL8SUflXBXOsrdPFKzs5iE8u7zJgff1xR9W11IEXBs3ScqRQ6iuFJjebAam+7BkHkpXeV0hOp7BjjJKMUg9wUAy7ar7kVJnGR5rq5FAD1r786J01jmc6V+yRkiL8g l6wrTOyVvunt+9qc+f7YkjwN9TZ1Fb4pTCIjbtziKmkrHKy/xQX3hMICgQbwMuFz/QlOWBrBTv14nyZpfg3UlFo1PacAG7l5prLO34K/6KqnvVSMFRw0m513eWVs5FUf 2DVjIqDhBVxnxRaX+S+FWjoGsptXpXNKExqhlGkbv/bZqLbBA0crotXKgG1I7qqI zSrKKynqjf1MUF7z2bt4AsAdpJgdRRT94+lKRxqrnCVnhF76KXEpAO98DNLVHMk9 xRI7xTKv32GnSgE5YraYBLoCXrhGoqM/6eMy70mAWleRE6JId/9ZiPQO23cme8rJ zzjAFgH9AtewXc4crG2yfVtqZ0pxJBfY9b20E730x5enIOjNEQ1cWAT4yk0KkliJ dv4lq9xwBQnvsPIs3hAI4JEDMrf+VQohhZ/EO5puAoSopAKppdJAq8Mt5RuXgEqT n3sd1WV6i/Crszvyjdhsdpms3HECpV2FDQyheGN1Ms7Evl4+T2LMjQSvimLRaM4G kxg+a/AqGgmTkxXh5mOAO4/jhNIr/xFTA6FjlEtzVMbqBOFFmWnOlmbr6Ik/iDxn AD2Ebqeoyj3t/q+najLHFBANOtboOISgCQFWqgIWNW5W2wdCTHVDqf/18v2eMKXo IYiNV3IwuzzXud2iFAsLnx1i136BwPXJr0Q2BxfI5k9+7JcPVKvtf8rzjes1a89j cnbepAepeHXCm8JFAQIFrWJI5FaInXf+kTlr/HrFlI7XxNTk49EugAq702EE75rZ EAenZrEj0dV4uOay+p+ay3mK6774FO5RxM6oZWzjbmydtTcXjrqqRqJn5WDjREfB XrsQnCbMPoHaCrrUpZOIyZJu6wNgAdiXI0CkPfWBAXHireBMzmS6iICE3C5dZ3k+XoXiglggCuGw4M/cIdOOOPKFetrMe541k6w+p1ZQrK1jxJfKOb7xaR1a4CBzLh5s amt6sDqr2AR60e7uBpr8R2FKmKtj8AVVL4UZFvxiU532vMB4zWjsvjluXdCXTzzp Wzzw6TXs+pQvYRnJNqqTu6tUZtmZiA+RFlfmyi0wfV5MbL6UOE4SNQuMJCFGiXE4 gj2zKhb4jP/zgDEeppaE/RqAQ14zu0keTEp8srnZUrMakcBjSrX6mSdHddjtHOHJ k2bjsGJp7Iakx5H90UAQ4J5sgQ2cejpgTPpnEeLaij6iKz7Do4+IC5Lk8KkDsCYn VuMtxid3J8MTmTkRdpJCRK6KJNtf23AS1Uovxvek7Yg67PtKiAI55uXfLXdvxdfH DpT+LpxGGi1dYB7Y2kA61H8d3tFLcs8istSezdlTwVY6e+aE2Q6B+BOINECGRCSY jCM= -----END?ENCRYPTED?PRIVATE?KEY-----
二:使用證書搭建https
1、安裝httpd :
[root@client?~]#?yum?-y?install?httpd [root@client?~]#?vim?/etc/httpd/conf/httpd.conf? //?把?#ServerName?www.example.com:80?改成?ServerName?192.168.94.111:80 [root@client?~]#?systemctl?start?httpd
?2、client 生成證書請求文件
生一個私鑰密鑰 :
[root@client?~]#?openssl?genrsa?-des3?-out?/etc/httpd/conf.d/server.key
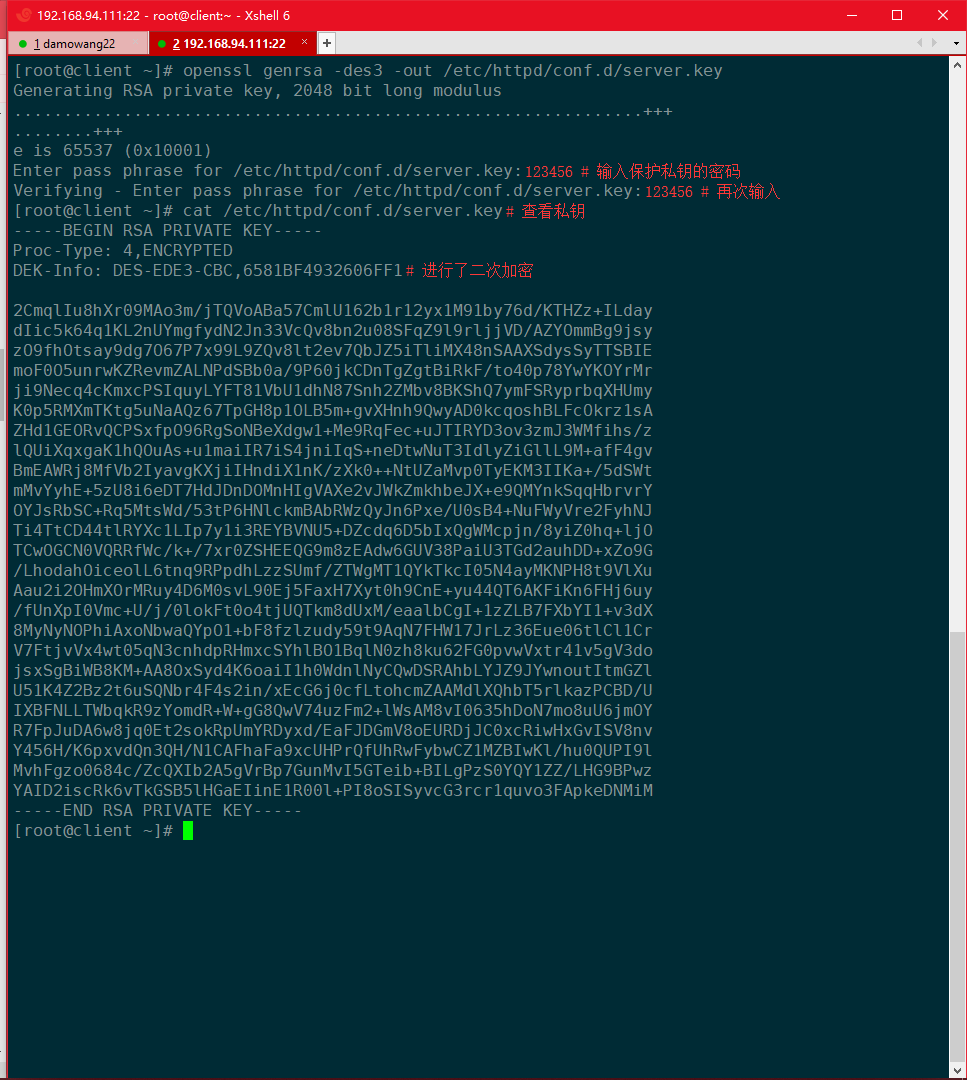
生成請求文件 :
[root@client?~]#?openssl?req?-new?-key?/etc/httpd/conf.d/server.key?-out?/server.csr???? #?注意后期添加的國家,省,城市等信息要和CA保持一致

3、將證書請求文件發給CA服務器:
[root@client?~]#?scp?/server.csr?192.168.94.22:/tmp/
4、CA認證中心進行CA簽名
[root@ca?~]#??openssl?ca?-keyfile?/etc/pki/CA/private/cakey.pem?-cert?/etc/pki/CA/cacert.pem?-in?/tmp/server.csr?-out?/server.crt

這里的認證中心進行的簽名是用自己的私鑰進行簽名
5、CA認證中心進行頒發證書
在頒發之前,CA認證中心會使用自己的公鑰進行加密
[root@ca?~]#?scp?/server.crt?192.168.94.111:/
三:使用證書實現https
SSL:(Secure?Socket?Layer)安全套接字層,通過一種機制在互聯網上提供密鑰傳輸?其主要目標是保證兩個應用間通信數據的保密性和可靠性,可在服務器端和用戶端同時支持的一種加密算法?目前主流版本SSLV2、SSLV3(常用)。SSL四次握手安全傳輸:加密協議:?SSL?3.0?或?TLS?1.0C?------------------------------------------------->?S??1.?請求一個安全的會話,協商算法C?<-------------------------------------------------?S??2.?將自己Server端的證書給客戶端,證書中包括了64自己的公鑰C?------------------------------------------------->?S??3.?客戶端用瀏覽器中存放CA的根證書檢測client證書,如果對,使用CA根證書中的公鑰解密?得到CA的公鑰;?然后生成一把對稱的加密密鑰,用client的公鑰加密這個密鑰發給CA?,?后期使用對稱密鑰加密數據C?<------------------------------------------------>?S??4.client使用私鑰解密,得到對稱的加密密鑰然后,使用對稱加密密鑰來進行安全快速傳輸數據
?
1、配置HTTPSweb服務器
[root@client?~]#?yum?-y?install?mod_ssl????#?安裝SSL模塊 [root@client?~]#?cp?/server.crt?/etc/httpd/conf.d/????#?復制證書 [root@client?~]#?vim?/etc/httpd/conf.d/ssl.conf #?SSLCertificateFile?/etc/pki/tls/certs/localhost.crt?把路徑改成/etc/httpd/conf.d/server.crt #?SSLCertificateKeyFile?/etc/pki/tls/private/localhost.key?把路徑改成/etc/httpd/conf.d/server.key [root@client?~]#?systemctl?restart?httpd Enter?SSL?pass?phrase?for?192.168.94.111:443?(RSA)?:?******???#?私鑰密碼
測試 :
[root@client?~]#?netstat?-antup?|?grep?443tcp6???????0??????0?:::443??????????????????:::*????????????????????LISTEN??????1634/httpd
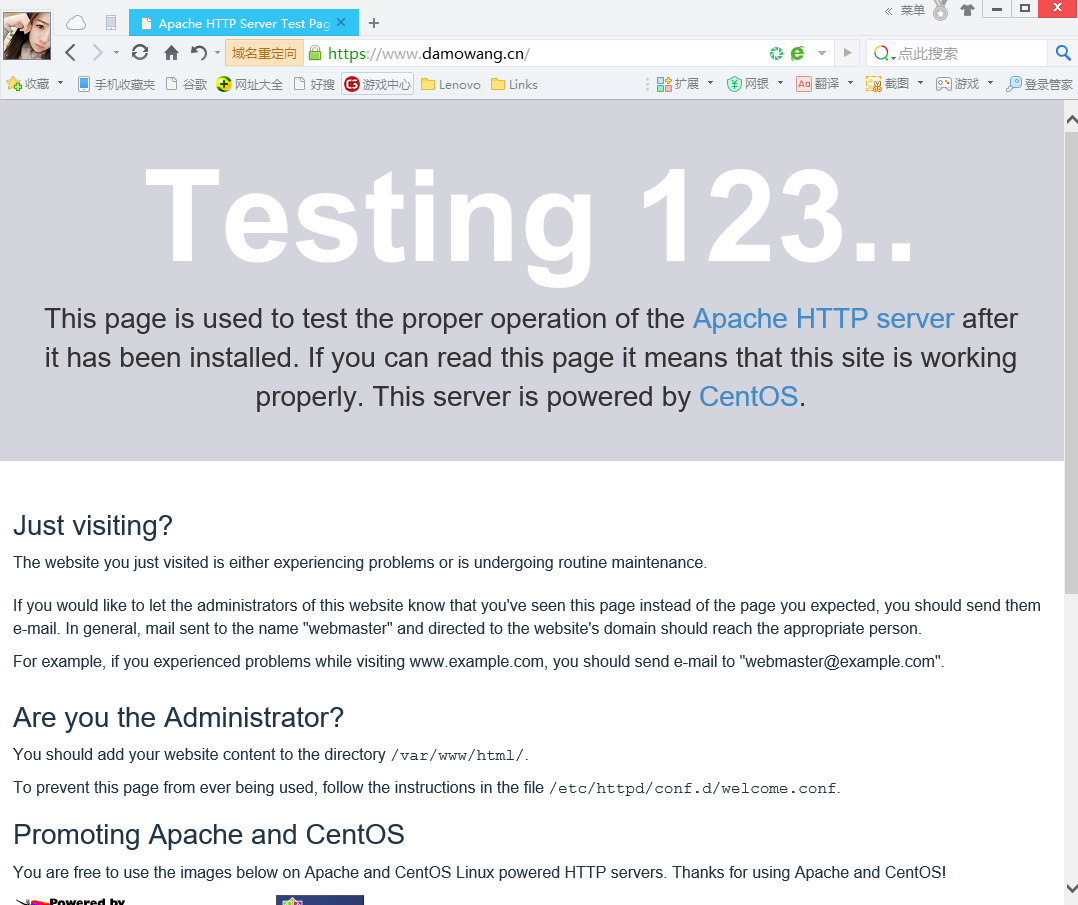
訪問https://192.168.94.111

到這就已經認證成功了 但是沒有被信任
查看一下證書
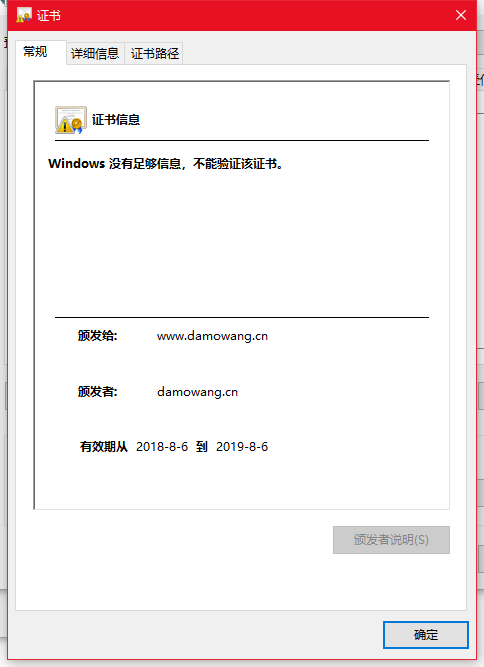
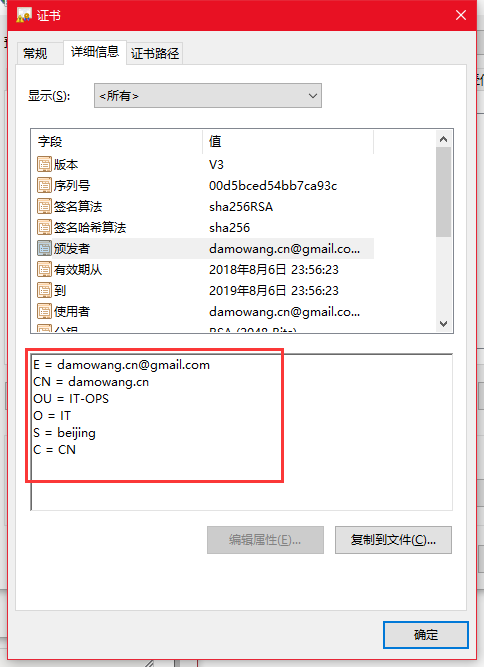
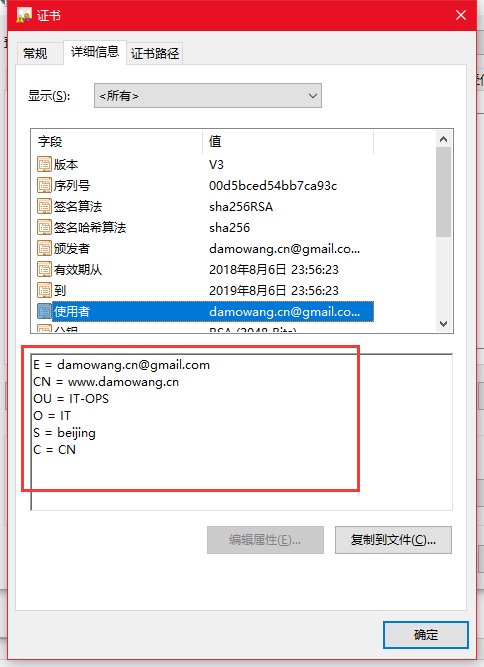
因為之前填寫Common Name 是www.damowang.cn的域名?
修改物理機hosts文件
192.168.94.111 www.damowang.cn?
重新用域名訪問應該就可以被信任了
?
轉載于:https://blog.51cto.com/13848248/2177399


)





)



)

)




