難度:5/10
考察技能:?Windows admin, Autopsy 使用
場景:分析USB設備使用情況
Autopsy使用注意:用管理員打開,在實際分析時注意先復制一個鏡像文件,保存好原文件
常用的Windows USB 取證的位置:
Windows XP:
Registry Key: USB-related information is stored in:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USB\
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR\
SetupAPI Logs: C:\WINDOWS\setupapi.log
Windows 7 had a few changes:
SetupAPI Logs moved to: C:\WINDOWS\INF\setupapi.dev.log
The category Windows Portable Devices was added: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Portable Devices\Devices
Windows 8/8.1 added:
DeviceClasses: Additional device information may be found under:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceClasses
Windows 10 and Windows 11:
The category Device Container ID was added:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\usbccgp
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\usbhub
其他取證位置:
Windows Event Logs:
- System event logs may contain entries related to USB device insertions and removals.
- Event Viewer path: Applications and Services Logs\Microsoft\Windows\DriverFrameworks-UserMode\Operational
Windows Prefetch:
- USB-related executables may be found in C:\Windows\Prefetch\.
Mounted Devices:
- Mounted device artifacts: HKEY_LOCAL_MACHINE\SYSTEM\MountedDevices
UserAssist:
- Tracks user interaction with USB devices in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist.
挑戰場景
A highly confidential document has been stolen from Prime Minister’s laptop and has been sold in the Dark Web. Can you help the intelligence services figure out how this happened?
1. 計算機名稱是什么?What is the computer name?
我們可通過在結果面板中查看操作系統信息來獲取終端主機名。在標黃的SYSTEM條目中即可找到主機名。
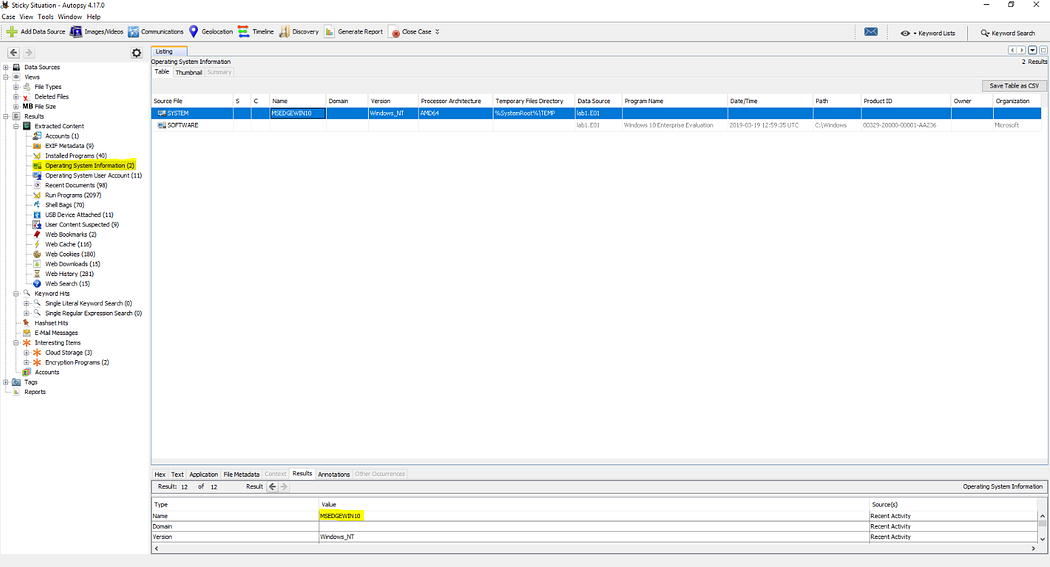
2. 操作系統安裝時間 When was the OS installed?
從上圖SOFTWARE條目中同樣可獲取系統安裝日期。
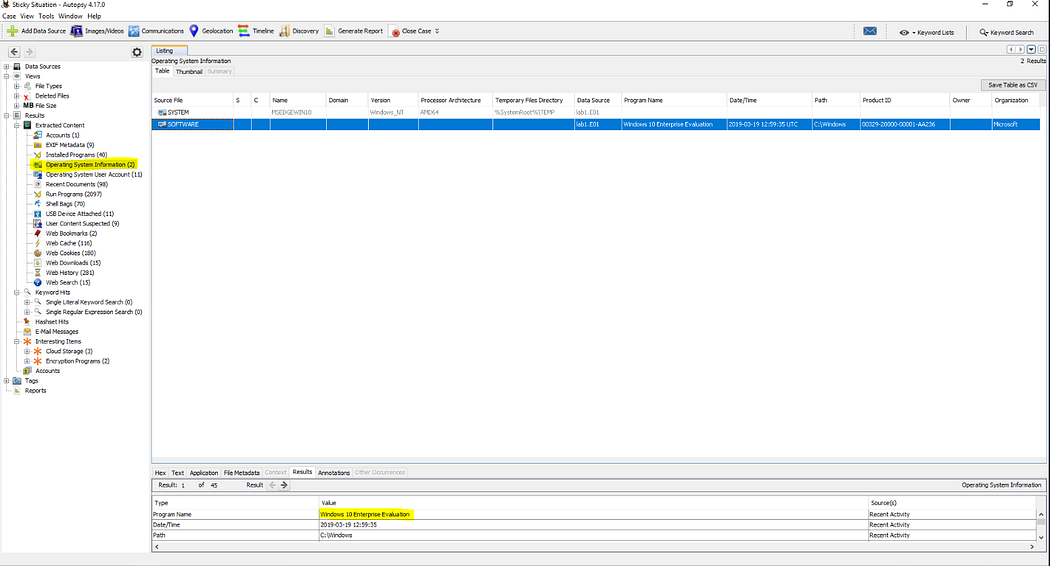
3. 計算機時區設置 What is the Timezone of the computer?
通過分析"TimeZoneInformation"注冊表鍵值可確定時區。Autopsy會自動導出注冊表配置單元以加速取證分析。?
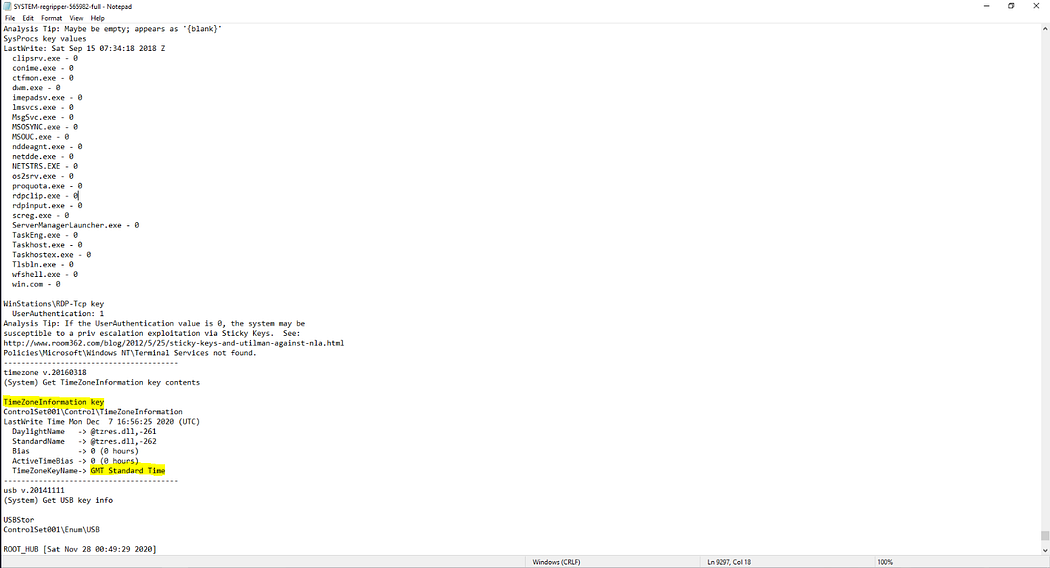
TimeZon?
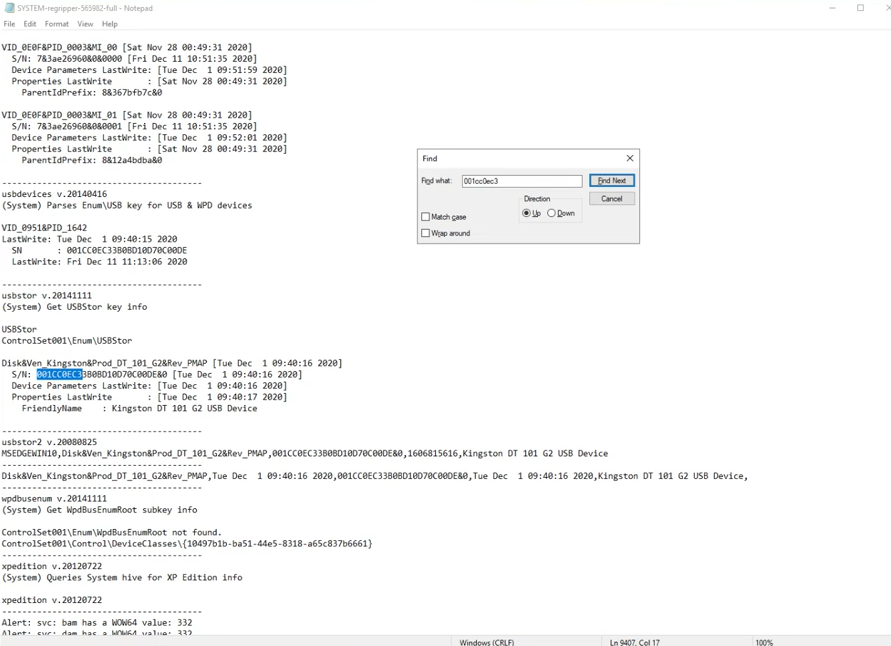
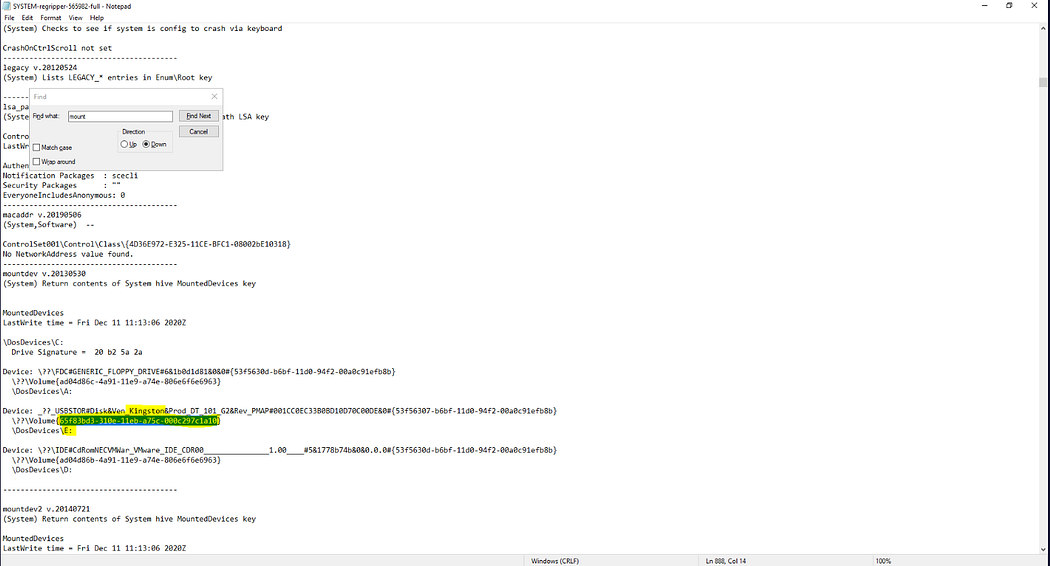
4. 首個連接的USB大容量存儲設備序列號 What is the serial number of the first USB mass storage device connected?
從系統注冊表配置單元的"USBSTOR"鍵值中可獲取該信息。
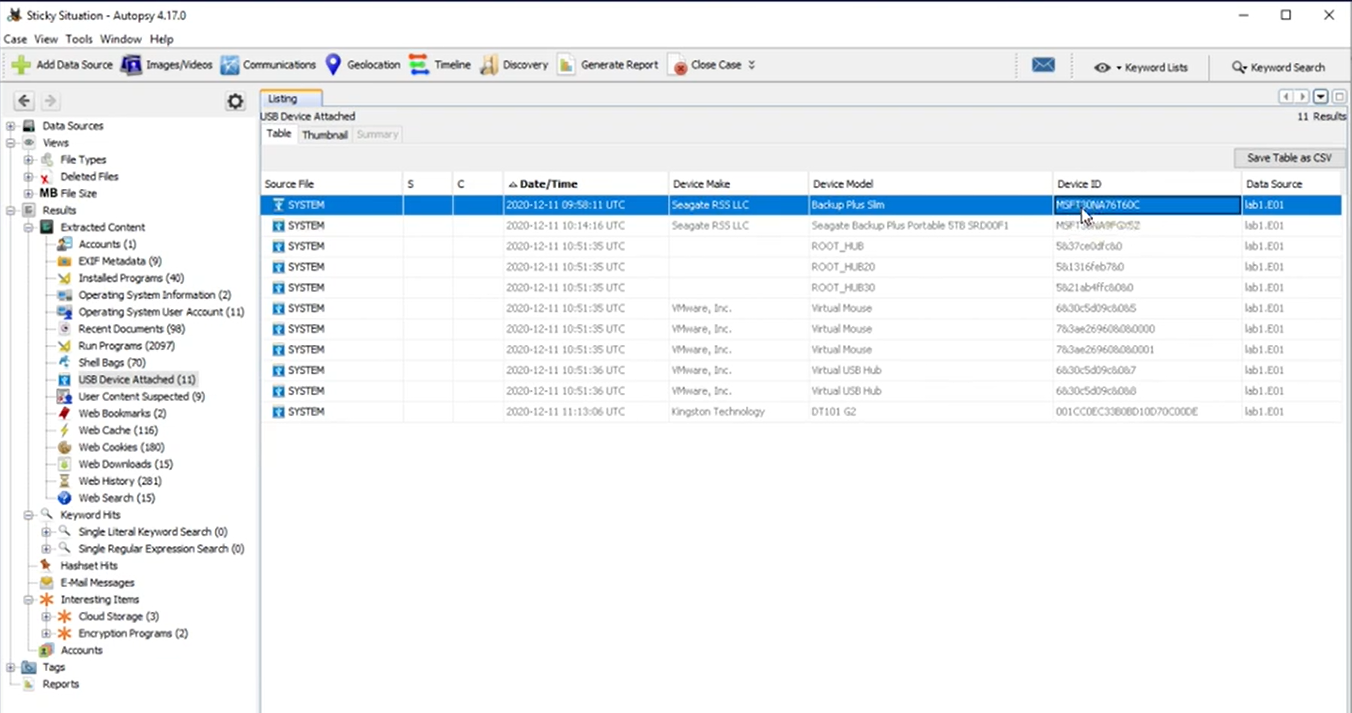
最后一個
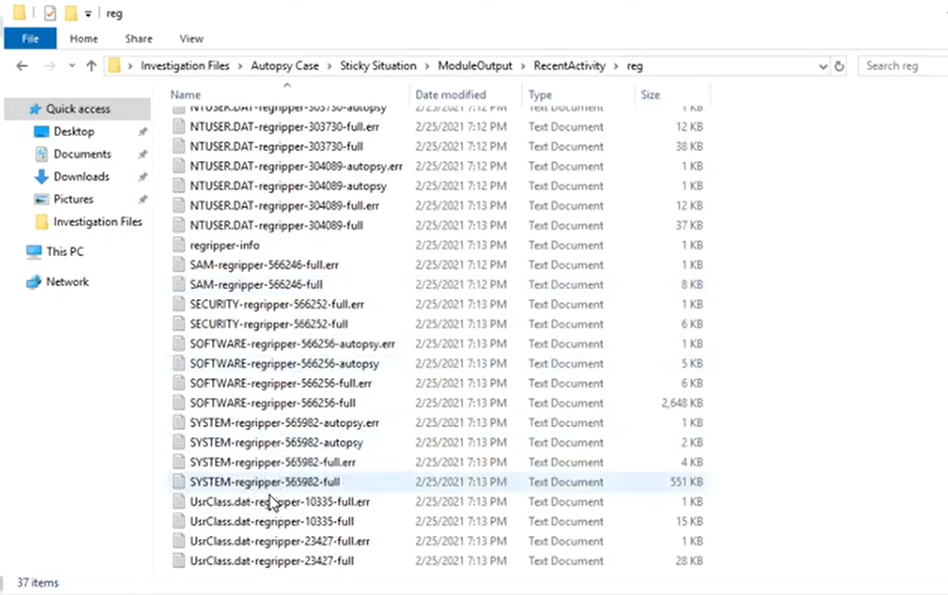
或者在提供的regripper文件里面找:
(RegRipper 是一個用于注冊表取證的開源工具,主要用于在Windows系統中分析注冊表數據。)
5. 首個USB大容量存儲設備廠商名稱 What is the vendor name of the first USB mass storage device?
上上圖有
6. 首個USB設備首次連接時間(系統本地時間) When was the first USB mass storage device connected for the first time? (system local time)
在"windows/inf"目錄下的"setupapi.dev.log"日志文件中可找到該記錄。
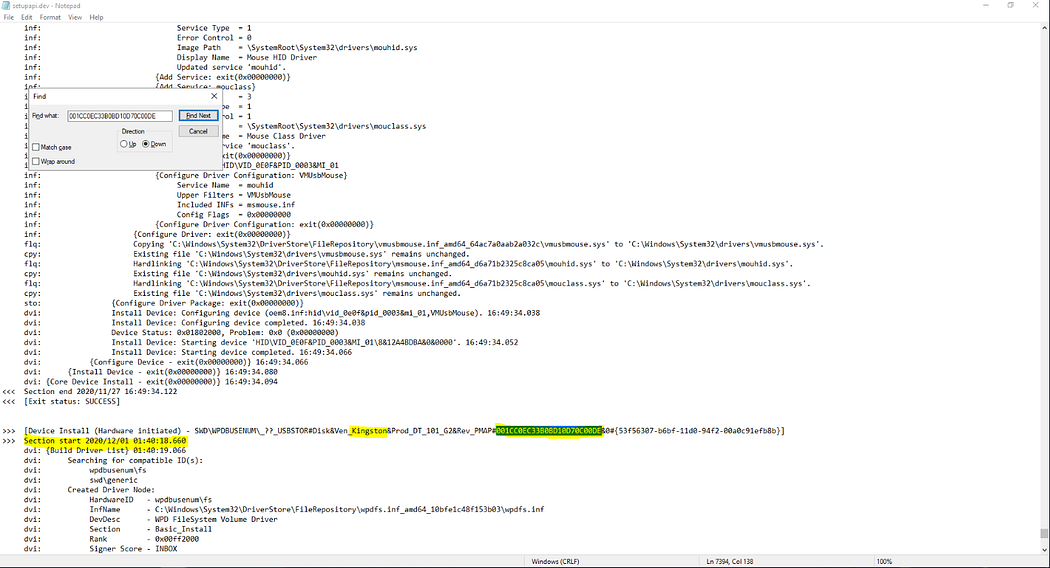
或者在提供的regripper文件里面找:
 7. 特定USB存儲設備的卷標 What is the Volume Label of the unique USB mass storage device?
7. 特定USB存儲設備的卷標 What is the Volume Label of the unique USB mass storage device?
卷標信息存儲于軟件注冊表配置單元中,通過之前獲取的序列號即可定位。
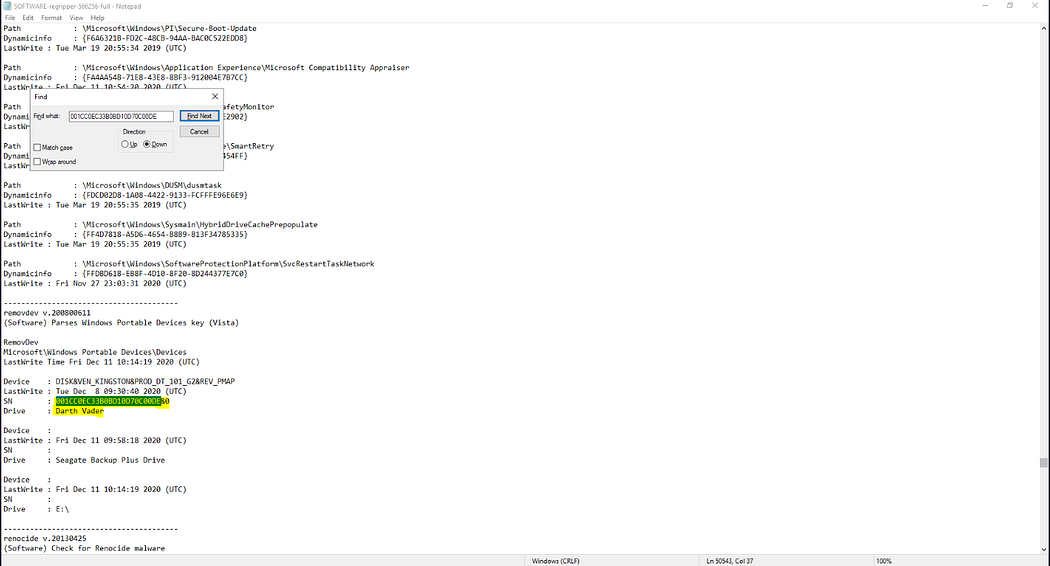
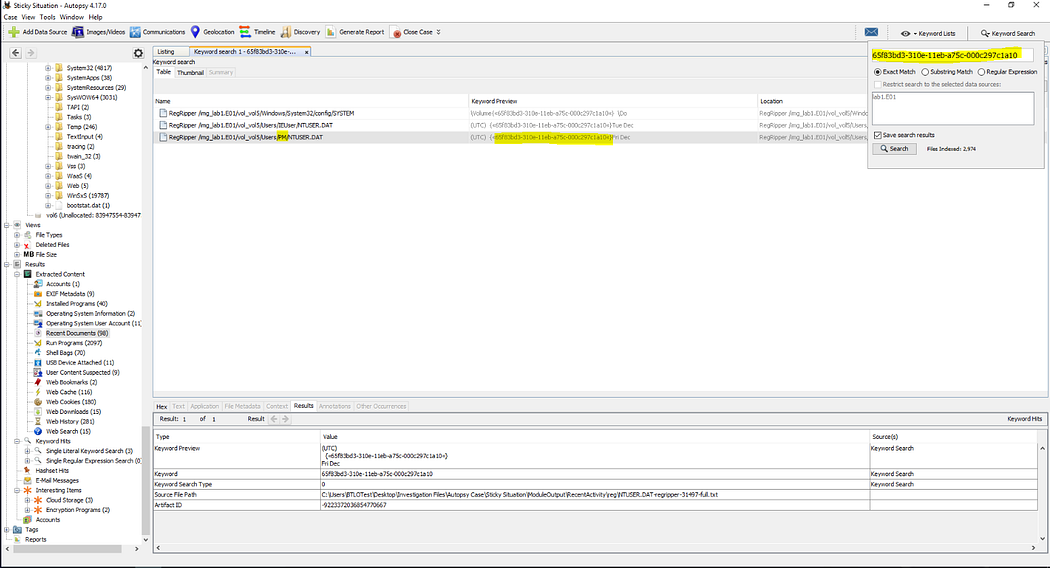
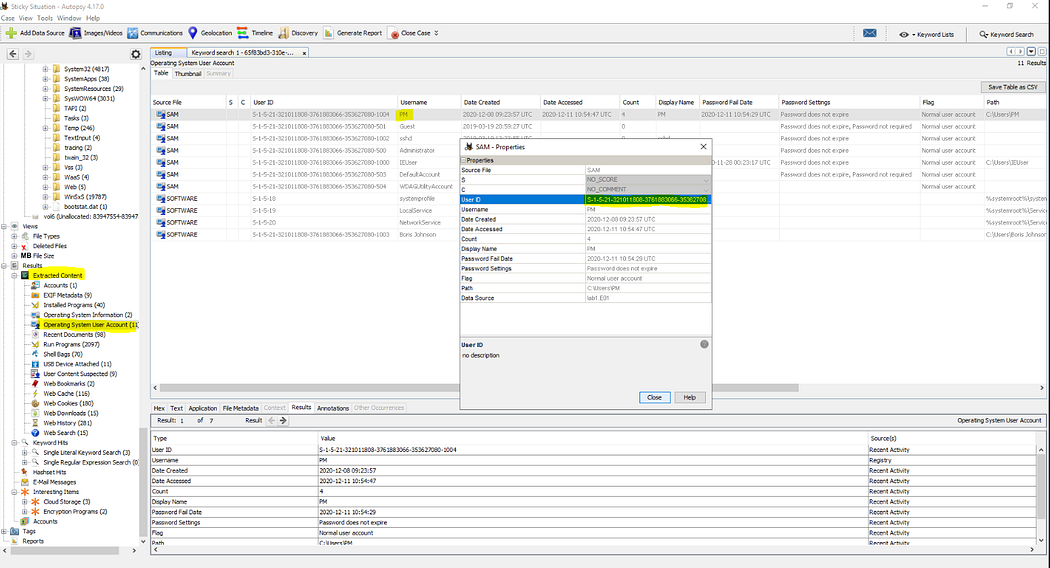
8. 找出使用過USB設備的用戶及其SID Find the user that used the USB Device. What is the user’s SID?
通過系統注冊表中"MountedDevices"鍵值獲取設備GUID后,進行關鍵詞搜索即可關聯用戶。在"提取內容→操作系統用戶賬戶→PM→屬性"中可查看用戶SID。
9. 該USB設備最后分配的盤符 What is the last drive letter assigned to the USB device?
繼續分析第7題提供的截圖即可獲得該信息。
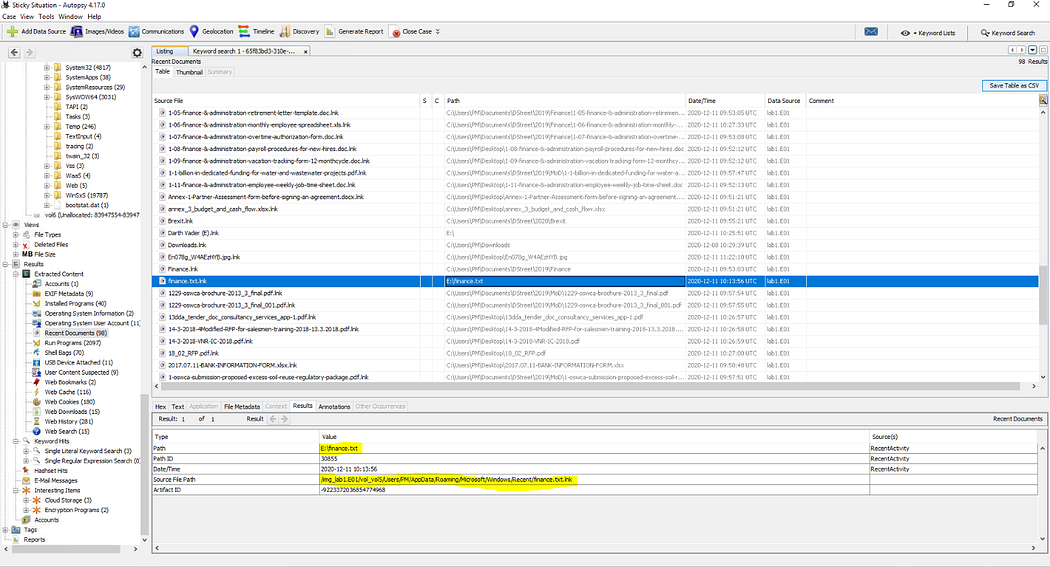
10. 被竊取的文件名是什么 What is the filename of the document stolen?
綜合所有取證證據后,通過"提取內容→最近文檔"中的LNK文件即可立即鎖定被盜文檔。






:從LED冬奧會、奧運會及春晚等等大屏,到手機小屏,快來挖一挖里面都有什么)

)










