一、組網需求
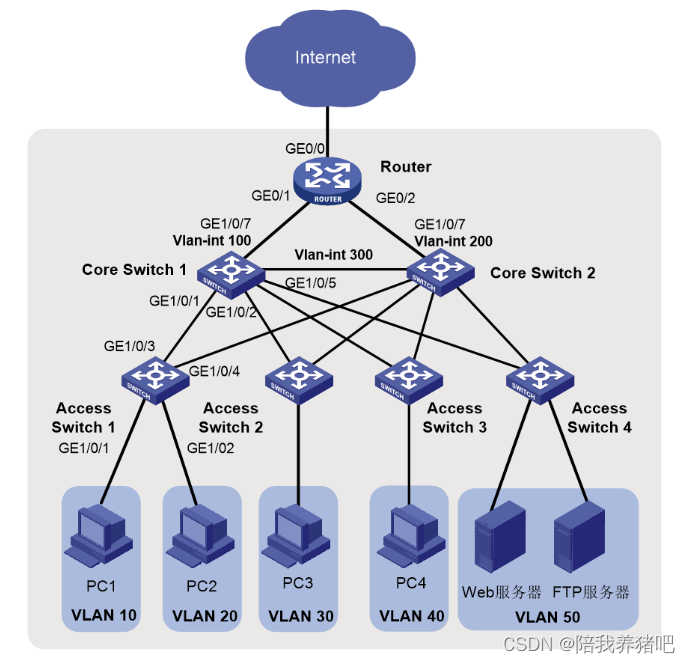
在中小園區中,S5130系列或S5130S系列以太網交換機通常部署在網絡的接入層,S5560X系列或
S6520X系列以太網交換機通常部署在網絡的核心,出口路由器一般選用MSR系列路由器。
- 核心交換機配置VRRP保證網絡可靠性。
- 園區網中不同的業務部門劃分到不同的VLAN中,部門間的業務在核心交換機上通過VLAN接口三層互通。
- 核心交換機作為DHCP服務器,為園區網用戶分配IP地址。
- 接入交換機上配置DHCP Snooping功能,防止內網用戶私接小路由器分配IP地址;同時配置IP Source Guard功能,防止內網用戶私自更改IP地址。
- 在出口路由器上對雙向流量配置基于IP的限速。
二、配置思路與數據規劃
(1)?????登錄設備
(2)?????配置管理IP地址和Telnet功能
(3)?????配置網絡互連互通
(4)?????配置核心交換機DHCP功能
(5)?????配置核心交換機OSPF功能
(6)?????配置核心交換可靠性功能
(7)?????配置限速
配置數據表
| 配置步驟 | 配置項 | 配置數據 | 說明 |
| 登錄設備 | 通過Console口登錄 | 設置傳輸速率等通信參數 | PC端通過終端仿真軟件登錄設備 |
| 配置管理IP和telnet功能 | 管理VLAN | VLAN 5 | 交換機缺省VLAN為VLAN 1。一般不將其配置為管理VLAN 本文將VLAN5配置為管理VLAN |
| 管理用以太網口或管理VLAN接口IP地址 | 10.10.1.1/24 | 此處以ACCSW1為例。 有管理用以太網口的交換機,可為管理用以太網口M-GigabitEthernet0/0/0配置IP地址用于登錄交換機。 沒有管理用以太網口的交換機,可為管理VLAN接口配置IP地址。 | |
| 配置接口和VLAN | 端口類型 | 連接交換機的端口建議設置為trunk,連接PC的端口設置為access。 | trunk類型端口一般用于連接交換機。 access類型端口一般用于連接PC。 hybrid類型端口是通用端口,既可以用來連接交換機,也可用來連接PC。 |
| VLAN ID | ACCSW1:VLAN 10、20 CORESW1:VLAN 10、20、30、40、50、100、300 | 為實現部門A和部門B二層隔離,將部門A劃分到VLAN10中,部門B劃分到VLAN20中。 核心交換機1通過Vlan-int100連接出口路由器 | |
| 核心交換機上配置DHCP服務器功能 | DHCP Server | CORESW1、CORESW2 | 在核心交換機1、核心交換機2上部署DHCPServer |
| 地址池 | VLAN 10:ip pool 10 VLAN 20:ip pool 20 | 部門A的終端從ip pool 10中獲取IP地址 部門B的終端從ip pool 20中獲取IP地址 | |
| 地址分配方式 | 基于全局地址池 | 無 | |
| 配置核心交換機路由 | IP地址 | 以CORESW1為例: Vlan-int10:192.168.10.1/24 Vlan-int20:192.168.20.1/24 Vlan-int100:172.16.1.1/24 Vlan-int300:172.16.3.1/24 | Vlan-int100用于核心交換機1與園區出口路由器對接。Vlan-int300用于核心交換機1與核心交換機2對接 在核心交換機1上配置Vlan-int10、Vlan-int20的IP地址后,部門A與部門B之間可以通過核心交換機1互訪 |
| 配置出口路由器 | 公網接口的IP地址 | GE0/0:202.101.100.2/30 | GE0/0為出口路由器連接Internet的接口,一般稱為公網接口 |
| 公網網關 | 202.101.100.1/30 | 該地址是與出口路由器對接的運營商設備的IP地址,出口路由器上需要配置一條缺省路由指向該地址,用于指導內網流量轉發至Internet | |
| DNS地址 | 202.101.100.199 | DNS服務器用于將域名解析成IP地址 | |
| 內網接口的IP地址 | GE0/1:172.16.1.2/24 GE0/2:172.16.2.2/24 | GE0/1、GE0/2為出口路由器連接內網的接口,GE0/1連接主設備,GE0/2連接備設備 | |
| 在接入交換機上配置DHCP Snooping和IP Source Guard | 信任接口 | GE1/0/1 GE1/0/2 | 配置信任接口后,用戶只會接收從信任接口進入的DHCP報文,防止內網私接小路由器為主機分配IP地址 |
三、配置步驟
3.1 配置接入交換機
PS:接入交換機ACCSW1、ACCSW2、ACCSW3和ACCSW4的配置基本相同。本文以配置接入
交換機ACCSW1為例說明配置方法。
3.1.1 通過Console口首次登錄設備
# 將PC斷電。
因為PC的串口不支持熱插拔,請不要在PC帶電的情況下,將串口線插入或者拔出PC。
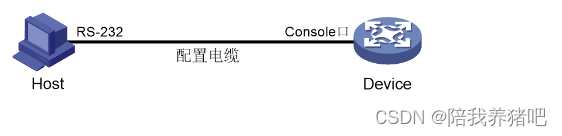
# 使用產品隨機附帶的配置口電纜連接PC機和設備。請先將配置口電纜的DB-9(孔)插頭插入PC
機的9芯(針)串口中,再將RJ-45插頭端插入設備的Console口中。
將設備與PC通過配置口電纜進行連接。
# 給PC上電。
# 在PC上打開終端仿真程序,按照要求設置終端參數。
終端參數設置:
| 參數 | 值 |
| 波特率 | 9600 |
| 數據位 | 8 |
| 停止位 | 1 |
| 奇偶校驗 | 無 |
| 流量控制 | 無 |
# 給設備上電。
在設備自檢結束后,用戶可鍵入回車進入命令交互界面。
PS:缺省情況下,通過Console登錄設備的認證方式為None,即不需要用戶名、密碼即可登錄設
備。首次登錄后,建議修改通過Console口登錄設備的認證方式以增強設備的安全性。
3.1.2 配置IP地址和Telnet
# 創建VLAN 5,并將接口Ten-GigabitEthernet1/0/10加入到VLAN 5中。假設連接網管的接口是
Ten-GigabitEthernet1/0/10。
<Sysname> system-view
System View: return to User View with Ctrl+Z.
[Sysname] sysname ACCSW1
[ACCSW1] vlan 5
[ACCSW1-vlan5] port ten-gigabitethernet 1/0/10
[ACCSW1-vlan5] quit# 創建VLAN接口5,并將接口IP地址配置為10.10.1.1/24。
[ACCSW1] interface vlan-interface 5
[ACCSW1-Vlan-interface5] ip address 10.10.1.1 24
[ACCSW1-Vlan-interface5] quit# 開啟Telnet服務? 。
[ACCSW1] telnet server enable# 配置Telnet登錄使用scheme認證方式。
[ACCSW1] line vty 0 63
[ACCSW1-line-vty0-63] authentication-mode scheme
[ACCSW1-line-vty0-63] quit# 創建本地用戶,并配置本地用戶的密碼、用戶角色和服務類型。本例中用戶名和密碼均為
admin,服務類型為telnet,用戶角色為network-admin。
[ACCSW1] local-user admin
New local user added.
[ACCSW1-luser-manage-admin] password simple hello12345
[ACCSW1-luser-manage-admin] authorization-attribute user-role network-admin
[ACCSW1-luser-manage-admin] service-type telnet
[ACCSW1-luser-manage-admin] quit# 在終端上通過Telnet登錄到設備,輸入正確的用戶名和密碼后,出現用戶視圖的命令行提示符表
示登錄成功。
C:\Users\Administrator> telnet 10.10.1.1
******************************************************************************
* Copyright (c) 2004-2019 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
****************************************************************************** login: admin
Password:
...PS:上述終端輸出信息是以S5560X-30C-PWR-EI設備(Release 1118P07版本)為例。
3.1.3??配置接口與VLAN
# 在接入交換機上創建VLAN 10和VLAN 20。
[ACCSW1] vlan 10 20# 將連接PC1的接口GigabitEthernet1/0/1加入VLAN 10,并配置為邊緣端口。
[ACCSW1] interface gigabitethernet 1/0/1
[ACCSW1-GigabitEthernet1/0/1] port link-type access
[ACCSW1-GigabitEthernet1/0/1] port acess vlan 10
[ACCSW1-GigabitEthernet1/0/1] stp edged-port
[ACCSW1-GigabitEthernet1/0/1] quit# 將連接PC1的接口GigabitEthernet1/0/2加入VLAN 20,并配置為邊緣端口。
[ACCSW1] interface gigabitethernet 1/0/2
[ACCSW1-GigabitEthernet1/0/2] port link-type access
[ACCSW1-GigabitEthernet1/0/2] port acess vlan 20
[ACCSW1-GigabitEthernet1/0/2] stp edged-port
[ACCSW1-GigabitEthernet1/0/2] quit# 將接口GigabitEthernet1/0/3和GigabitEthernet1/0/4的鏈路類型配置為Trunk并允許VLAN 10和
VLAN 20的報文通過。
[ACCSW1] interface gigabitethernet 1/0/3
[ACCSW1-GigabitEthernet1/0/3] port link-type trunk
[ACCSW1-GigabitEthernet1/0/3] port trunk permit vlan 10 20
[ACCSW1-GigabitEthernet1/0/3] quit
[ACCSW1] interface gigabitethernet 1/0/4
[ACCSW1-GigabitEthernet1/0/4] port link-type trunk
[ACCSW1-GigabitEthernet1/0/4] port trunk permit vlan 10 20
[ACCSW1-GigabitEthernet1/0/4] quit# 查看ACCSW1上VLAN 10和VLAN 20的配置信息。
[ACCSW1] display vlan 10VLAN ID: 10VLAN type: StaticRoute interface: Not configuredDescription: VLAN 0010Name: VLAN 0010Tagged ports:GigabitEthernet1/0/3GigabitEthernet1/0/4Untagged ports:GigabitEthernet1/0/1[ACCSW1] display vlan 20VLAN ID: 20VLAN type: StaticRoute interface: Not configuredDescription: VLAN 0020Name: VLAN 0020Tagged ports:GigabitEthernet1/0/3GigabitEthernet1/0/4Untagged ports:GigabitEthernet1/0/23.1.4 配置BPDU保護功能
[ACCSW1] stp bpdu-protection3.1.5 配置DHCP snooping
# 開啟DHCP Snooping功能。
[ACCSW1] dhcp snooping enable# 指定GigabitEthernet1/0/3為DHCP Snooping功能的信任端口。
[ACCSW1]?interface gigabitethernet 1/0/3[ACCSW1-GigabitEthernet1/0/3]?dhcp snooping trust[ACCSW1-GigabitEthernet1/0/3] quit3.1.6 配置IP Source Guard
# 開啟接口GigabitEthernet1/0/1、GigabitEthernet1/0/2的IPv4接口綁定功能,綁定源IP地址和
MAC地址,并啟用接口的DHCP Snooping 表項記錄功能。
[ACCSW1] interface gigabitethernet 1/0/1
[ACCSW1-GigabitEthernet1/0/1] ip verify source ip-address mac-address
[ACCSW1-GigabitEthernet1/0/1] dhcp snooping binding record
[ACCSW1-GigabitEthernet1/0/1] quit
[ACCSW1] interface gigabitethernet 1/0/2
[ACCSW1-GigabitEthernet1/0/2] ip verify source ip-address mac-address
[ACCSW1-GigabitEthernet1/0/2] dhcp snooping binding record
[ACCSW1-GigabitEthernet1/0/2] quit3.1.7 保存配置
# 保存接入交換機上的配置(以ACCSW1為例)。
[ACCSW1] save
The current configuration will be written to the device. Are you sure? [Y/N]:y
Please input the file name(*.cfg)[flash:/startup.cfg]
(To leave the existing filename unchanged, press the enter key):
flash:/startup.cfg exists, overwrite? [Y/N]:y
Validating file. Please wait...
Saved the current configuration to mainboard device successfully.3.2 配置核心交換機
PS:核心交換機CORESW1和CORESW2的配置基本相同。本文如無特殊說明,以配置核心交
換機CORESW1為例說明配置方法。?
3.2.1 配置接口與VLAN
# 創建VLAN 10、VLAN 20、VLAN 30、VLAN 40、VLAN 50、VLAN 100和VLAN 300。
<Sysname> system-view
[Sysname] sysname CORESW1
[CORESW1] vlan 10 20 30 40 50 100 300# 配置接口GigabitEthernet1/0/1的鏈路類型為Trunk,并允許VLAN 10和20的報文通過。
[CORESW1] interface gigabitethernet 1/0/1
[CORESW1-GigabitEthernet1/0/1] port link-type trunk
[CORESW1-GigabitEthernet1/0/1] port trunk permit vlan 10 20
[CORESW1-GigabitEthernet1/0/1] quit# 配置接口GigabitEthernet1/0/5的鏈路類型為Trunk,并允許VLAN 300的報文通過。
[CORESW1] interface gigabitethernet 1/0/5
[CORESW1-GigabitEthernet1/0/5] port link-type trunk
[CORESW1-GigabitEthernet1/0/5] port trunk permit vlan 300
[CORESW1-GigabitEthernet1/0/5] quit# 配置其他接口的鏈路類型并允許對應的VLAN通過,具體配置過程略。
3.2.2 配置VLAN接口
# 創建VLAN接口10,并將接口的IP地址配置為192.168.10.1/24。
[CORESW1] interface vlan-interface 10
[CORESW1-Vlan-interface10] ip address 192.168.10.1?24
[CORESW1-Vlan-interface10] quit# 創建VLAN接口20,并將接口的IP地址配置為192.168.20.1/24。
[CORESW1] interface vlan-interface 20
[CORESW1-Vlan-interface20] ip address 192.168.20.1?24
[CORESW1-Vlan-interface20] quit# 創建VLAN接口100,并將接口的IP地址配置為172.16.1.1/24。
[CORESW1] interface vlan-interface 100
[CORESW1-Vlan-interface100] ip address 172.16.1.1?24
[CORESW1-Vlan-interface100] quit# 創建VLAN接口300,并將接口的IP地址配置為172.16.3.1/24。
[CORESW1] interface vlan-interface 300
[CORESW1-Vlan-interface300] ip address 172.16.3.1?24
[CORESW1-Vlan-interface300] quit# 創建其他VLAN接口,并配置IP地址,具體配置過程略。
# 查看CORESW1上VLAN 10、VLAN 20、VLAN 100、VLAN 300的配置信息。
[CORESW1] display vlan 10VLAN ID: 10VLAN type: StaticRoute interface: ConfiguredIPv4 address: 192.168.10.1IPv4 subnet mask: 255.255.255.0Description: VLAN 0010Name: VLAN 0010Tagged ports:GigabitEthernet1/0/1Untagged ports:?? None[CORESW1] display vlan 20VLAN ID: 20VLAN type: StaticRoute interface: ConfiguredIPv4 address: 192.168.20.1IPv4 subnet mask: 255.255.255.0Description: VLAN 0020Name: VLAN 0020Tagged ports:GigabitEthernet1/0/2Untagged ports:?? None[CORESW1] display vlan 100VLAN ID: 100VLAN type: StaticRoute interface: ConfiguredIPv4 address: 172.16.1.1IPv4 subnet mask: 255.255.255.0Description: VLAN 0100Name: VLAN 0100Tagged ports:?? NoneUntagged ports:?? None[CORESW1] display vlan 300VLAN ID: 300VLAN type: StaticRoute interface: ConfiguredIPv4 address: 172.16.3.1IPv4 subnet mask: 255.255.255.0Description: VLAN 0300Name: VLAN 0300Tagged ports:GigabitEthernet1/0/5Untagged ports:?? None3.2.3 配置VRRP備份
正常情況下內網用戶流量都上送到CORESW1進行處理,只有當CORESW1或CORESW1的上行
鏈路出故障之后,VRRP備份組切換CORESW2為主設備,內網用戶流量上送到CORESW2。
# 在CORESW1上配置VRRP備份組功能。
# 創建VRRP備份組1,并配置VRRP備份組1的虛擬IP地址為172.16.3.10。
[CORESW1] interface vlan-interface 300
[CORESW1-Vlan-interface300] vrrp vrid 1 virtual-ip 172.16.3.10# 設置CORESW1在VRRP備份組1中的優先級為120,高于CORESW2的優先級100,以保證
CORESW1成為Master負責轉發流量。
[CORESW1-Vlan-interface300] vrrp vrid 1 priority 120# 設置CORESW1工作在搶占方式,以保證CORESW1故障恢復后,能再次搶占成為Master,即只
要CORESW1正常工作,就由CORESW1負責轉發流量。為了避免頻繁地進行狀態切換,配置搶占
延遲時間為5000厘秒。
[CORESW1-Vlan-interface300] vrrp vrid 1 preempt-mode delay 5000
[CORESW1-Vlan-interface300] quit# 創建和上行接口GigabitEthernet1/0/7物理狀態關聯的Track項1。如果Track項的狀態為
Negative,則說明CORESW1的上行接口出現故障。
[CORESW1] track 1 interface gigabitethernet 1/0/7
[CORESW1-track-1] quit# 設置監視Track項。
[CORESW1] interface vlan-interface 300
[CORESW1-Vlan-interface300] vrrp vrid 1 track 1 priority reduced 30# 在CORESW2上配置VRRP備份組功能。創建VRRP備份組1,并配置VRRP備份組1的虛擬IP地
址為172.16.3.10。
<Sysname> system-view
[Sysname] sysname CORESW2
[CORESW2] interface vlan-interface 300
[CORESW2-Vlan-interface300] vrrp vrid 1 virtual-ip 172.16.3.10# 配置CORESW2在VRRP備份組1中的優先級為100。
[CORESW2-Vlan-interface300] vrrp vrid 1 priority 100# 配置CORESW2工作在搶占方式,搶占延遲時間為5000厘秒。
[CORESW2-Vlan-interface300] vrrp vrid 1 preempt-mode delay 5000
[CORESW2-Vlan-interface300] quit# 在CORESW1上使用display vrrp verbose命令查詢VRRP備份組信息。
[CORESW1] display vrrp verbose
IPv4 Virtual Router Information:Running mode : StandardTotal number of virtual routers : 1Interface Vlan-interface300VRID???????????? : 1?????????????????? Adver Timer? : 100Admin Status???? : Up????????????????? State??????? : MasterConfig Pri?????? : 120? ???????????????Running Pri? : 120Preempt Mode???? : Yes???????????????? Delay Time?? : 5000Auth Type??????? : NoneVirtual IP?????? : 172.16.3.10Virtual MAC????? : 0000-5e00-0101Master IP??????? : 172.16.3.1VRRP Track Information:Track Object?? : 1?????????????????? State : Positive?? Pri Reduced : 30# 在CORESW2上使用display vrrp verbose命令查詢VRRP備份組信息。
[CORESW2] display vrrp verbose
IPv4 Virtual Router Information:Running mode : StandardTotal number of virtual routers : 1Interface Vlan-interface300VRID???????????? : 1?????????????????? Adver Timer? : 100Admin Status???? : Up????????????????? State??????? : BackupConfig Pri?????? : 100???????????????? Running Pri? : 100Preempt Mode???? : Yes???????????????? Delay Time?? : 5000Become Master??? : 27810ms leftAuth Type??????? : NoneVirtual IP?????? : 172.16.3.10Virtual MAC????? : 0000-5e00-0101Master IP??????? : 172.16.3.1# 由此可見,VRRP備份組創建成功,CORESW1為Master設備,CORESW2為Backup設備。
3.2.4 配置DHCP服務器,并查看配置
# 開啟DHCP服務。
[CORESW1] dhcp enable# 創建DHCP地址池1,用來為192.168.10.0/24網段內的客戶端分配動態IP地址,并配置DNS服務
器地址、出口網關、租期,為打印機配置固定的IP地址192.168.10.254。
[CORESW1] dhcp server ip-pool 1
[CORESW1-dhcp-pool-1] network 192.168.10.0 mask 255.255.255.0
[CORESW1-dhcp-pool-1] gateway-list 192.168.10.1
[CORESW1-dhcp-pool-1] dns-list?202.101.100.199
[CORESW1-dhcp-pool-1] expired day 30
[CORESW1-dhcp-pool-1] static-bind ip-address 192.168.10.254 24 client-identifier aabb-cccc-dd
[CORESW1-dhcp-pool-1] quit# 創建DHCP地址池2,用來為192.168.20.0/24網段內的客戶端分配動態IP地址,并配置DNS服務
器地址、出口網關、租期。
[CORESW1] dhcp server ip-pool 2
[CORESW1-dhcp-pool-2] network 192.168.20.0 mask 255.255.255.0
[CORESW1-dhcp-pool-2] gateway-list 192.168.20.1
[CORESW1-dhcp-pool-2] dns-list?202.101.100.199
[CORESW1-dhcp-pool-2] expired day 30
[CORESW1-dhcp-pool-2] quit# 配置VLAN接口10和VLAN接口20工作在DHCP服務器模式。
[CORESW1] interface vlan-interface 10
[CORESW1-Vlan-interface10] dhcp select server
[CORESW1-Vlan-interface10] quit
[CORESW1 interface vlan-interface 20
[CORESW1-Vlan-interface20] dhcp select server
[CORESW1-Vlan-interface20] quit# 使用display dhcp server pool命令查看DHCP地址池的信息。
[CORESW1] display dhcp server pool
Pool name: 1Network: 192.168.10.0 mask 255.255.255.0expired 30 0 0 0gateway-list 192.168.10.1static bindings:ip-address 192.168.10.254 mask 255.255.255.0client-identifier aabb-cccc-dd
Pool name: 2Network: 192.168.20.0 mask 255.255.255.0expired 30 0 0 0gateway-list 192.168.20.1?3.2.5 配置OSPF
CORESW1的OSPF配置。
[CORESW1] ospf 100 router-id 2.2.2.2
[CORESW1-ospf-100] area 0
[CORESW1-ospf-100-area-0.0.0.0] network 172.16.1.0 0.0.0.255
[CORESW1-ospf-100-area-0.0.0.0] network 172.16.3.0 0.0.0.255
[CORESW1-ospf-100-area-0.0.0.0] network 192.168.10.0 0.0.0.255
[CORESW1-ospf-100-area-0.0.0.0] network 192.168.20.0 0.0.0.255
[CORESW1-ospf-100-area-0.0.0.0] quit
[CORESW1-ospf-100] quitCORESW2的OSPF配置。
[CORESW2] ospf 100 router-id 3.3.3.3
[CORESW2-ospf-100] area 0
[CORESW2-ospf-100-area-0.0.0.0] network 172.16.2.0 0.0.0.255
[CORESW2-ospf-100-area-0.0.0.0] network 172.16.3.0 0.0.0.255
[CORESW2-ospf-100-area-0.0.0.0] network 192.168.10.0 0.0.0.255
[CORESW2-ospf-100-area-0.0.0.0] network 192.168.20.0 0.0.0.255
[CORESW2-ospf-100-area-0.0.0.0] quit
[CORESW2-ospf-100] quit# 使用display ospf peer命令查看CORESW1上的OSPF鄰居信息。
[CORESW1] display ospf peerOSPF Process 100 with Router ID 2.2.2.2Neighbor Brief InformationArea: 0.0.0.0Router ID?????? Address???????? Pri Dead-Time? State???????????? Interface3.3.3.3???????? 172.16.3.2????? 1?? 33???????? Full/DR?????????? Vlan300# 使用display ospf peer命令查看CORESW2上的OSPF鄰居信息。
[CORESW2] display ospf peerOSPF Process 100 with Router ID 3.3.3.3Neighbor Brief InformationArea: 0.0.0.0Router ID?????? Address???????? Pri Dead-Time? State???????????? Interface2.2.2.2???????? 172.16.3.1????? 1?? 36???????? Full/BDR????????? Vlan3003.2.6 保存配置
# 保存核心交換機上的配置(以CORESW1為例)。
[CORESW1] save
The current configuration will be written to the device. Are you sure? [Y/N]:y
Please input the file name(*.cfg)[flash:/startup.cfg]
(To leave the existing filename unchanged, press the enter key):
flash:/startup.cfg exists, overwrite? [Y/N]:y
Validating file. Please wait...
Saved the current configuration to mainboard device successfully.3.3 配置出口路由器
3.3.1 配置內網接口和公網接口IP
# 配置內網接口IP地址。
[Router] interface GigabitEthernet 0/1
[Router-GigabitEthernet0/1] ip address 172.16.1.2 24
[Router-GigabitEthernet0/1] quit
[Router] interface GigabitEthernet 0/2
[Router-GigabitEthernet0/2] ip address 172.16.2.2 24
[Router-GigabitEthernet0/2] quit# 配置公網接口IP地址。
[Router] interface GigabitEthernet 0/0
[Router-GigabitEthernet0/0] ip address 202.101.100.2 30
[Router-GigabitEthernet0/0] quit3.3.2 配置允許上網的ACL
# 配置ACL。
[Router] acl basic 2000
[Router-acl-ipv4-basic-2000] rule permit source 192.168.10.0 0.0.0.255
[Router-acl-ipv4-basic-2000] rule permit source 192.168.20.0 0.0.0.255
[Router-acl-ipv4-basic-2000] rule permit source 172.16.1.0 0.0.0.255
[Router-acl-ipv4-basic-2000] rule permit source 172.16.2.0 0.0.0.255
[Router-acl-ipv4-basic-2000] rule permit source 172.16.3.0 0.0.0.255
[Router-acl-ipv4-basic-2000] quit# 配置報文過濾。
[Router] interface gigabitethernet 0/1
[Router-GigabitEthernet0/1] packet-filter 2000 inbound
[Router-GigabitEthernet0/1] quit
[Router] interface gigabitethernet 0/2
[Router-GigabitEthernet0/2] packet-filter 2000 inbound
[Router-GigabitEthernet0/2] quit
[Router] packet-filter default deny# 使用display acl命令查看ACL的配置信息。
[Router] display acl 200
Basic IPv4 ACL 2000, 5 rules,
ACL's step is 5, start ID is 0rule 0 permit source 192.168.10.0 0.0.0.255rule 5 permit source 192.168.20.0 0.0.0.255rule 10 permit source 172.16.1.0 0.0.0.255rule 15 permit source 172.16.2.0 0.0.0.255rule 20 permit source 172.16.3.0 0.0.0.255# 使用display packet-filter命令查看ACL在報文過濾中的應用情況。
[Router] display packet-filter interface gigabitethernet 0/1 inbound
Interface: GigabitEthernet0/1Inbound policy:IPv4 ACL 2000[Router] display packet-filter interface gigabitethernet 0/2 inbound
Interface: GigabitEthernet0/2Inbound policy:IPv4 ACL 20003.3.3 配置OSPF
配置一條缺省路由指向運營商。
[Router] ip route-static 0.0.0.0 0.0.0.0 202.101.100.1出口路由器的OSPF配置。在OSPF中引入缺省路由,從而連接內網和公網。
[Router] ospf 10 router-id 1.1.1.1
[Router-ospf-10] default-route-advertise always
[Router-ospf-10] area 0
[Router-ospf-10-area-0.0.0.0] network 172.16.1.0 0.0.0.255
[Router-ospf-10-area-0.0.0.0] network 172.16.2.0 0.0.0.255
[Router-ospf-10-area-0.0.0.0] quit
[Router-ospf-10] quit# 使用display ospf peer命令查看Router上的OSPF鄰居信息。
[Router] display ospf peerOSPF Process 100 with Router ID 1.1.1.1Neighbor Brief InformationArea: 0.0.0.0Router ID?????? Address???????? Pri Dead-Time? State???????????? Interface2.2.2.2???????? 172.16.1.1????? 1?? 31???????? Full/DR?????????? GE0/13.3.3.3???????? 172.16.2.1????? 1?? 39???????? Full/BDR????????? GE0/2# 使用display ospf routing命令查看CORESW1上的OSPF路由表信息。
[CORESW1] display ospf routingOSPF Process 100 with Router ID 2.2.2.2Routing TableTopology base (MTID 0)Routing for networkDestination??????? Cost???? Type??? NextHop???????? AdvRouter?????? Area172.16.1.0/24????? 1??????? Transit 0.0.0.0???????? 2.2.2.2???????? 0.0.0.0172.16.2.0/24????? 2??????? Transit 172.16.3.2????? 1.1.1.1????? ???0.0.0.0172.16.2.0/24????? 2??????? Transit 172.16.1.2????? 1.1.1.1???????? 0.0.0.0172.16.3.0/24????? 1??????? Transit 0.0.0.0???????? 3.3.3.3???????? 0.0.0.0Routing for ASEsDestination??????? Cost???? Type??? Tag???????? NextHop???????? AdvRouter0.0.0.0/0????????? 1??????? Type2?? 1?????????? 172.16.1.2????? 1.1.1.1Total nets: 5Intra area: 4? Inter area: 0? ASE: 1? NSSA: 0# 使用display ospf routing命令查看CORESW2上的OSPF路由表信息。
[CORESW2] display ospf routingOSPF Process 100 with Router ID 3.3.3.3Routing TableTopology base (MTID 0)Routing for networkDestination??????? Cost???? Type??? NextHop???????? AdvRouter?????? Area172.16.1.0/24????? 2??????? Transit 172.16.3.1????? 2.2.2.2???????? 0.0.0.0172.16.1.0/24????? 2??????? Transit 172.16.2.2????? 2.2.2.2???????? 0.0.0.0172.16.2.0/24????? 1??????? Transit 0.0.0.0???????? 1.1.1.1???????? 0.0.0.0172.16.3.0/24????? 1??????? Transit 0.0.0.0???????? 3.3.3.3???????? 0.0.0.0Routing for ASEsDestination??????? Cost???? Type??? Tag???????? NextHop???????? AdvRouter0.0.0.0/0????????? 1??????? Type2?? 1?????????? 172.16.2.2????? 1.1.1.1Total nets: 5Intra area: 4? Inter area: 0? ASE: 1? NSSA: 0?3.3.4 配置DNS解析
[Router] dns server 202.101.100.199
[Router] dns proxy enable3.3.5 配置基于IP或IP網段的限速
# 配置CAR列表。
[Router] qos carl 1 source-ip-address range 192.168.10.1 to 192.168.10.254 per-address shared-bandwidth
[Router] qos carl 2 source-ip-address range 192.168.20.1 to 192.168.20.254 per-address shared-bandwidth
[Router] qos carl 3 destination-ip-address range 192.168.10.1 to 192.168.10.254 per-address shared-bandwidth
[Router] qos carl 4 destination-ip-address range 192.168.20.1 to 192.168.20.254 per-address shared-bandwidth# 配置限速。
[Router] interface gigabitethernet 0/1
[Router-GigabitEthernet0/1] qos car inbound carl 1 cir 512
[Router-GigabitEthernet0/1] qos car inbound carl 2 cir 512
[Router-GigabitEthernet0/1] qos car outbound carl 3 cir 512
[Router-GigabitEthernet0/1] qos car outbound carl 4 cir 512
[Router-GigabitEthernet0/1] quit
[Router] interface gigabitethernet 0/2
[Router-GigabitEthernet0/2] qos car inbound carl 1 cir 512
[Router-GigabitEthernet0/2] qos car inbound carl 2 cir 512
[Router-GigabitEthernet0/2] qos car outbound carl 3 cir 512
[Router-GigabitEthernet0/2] qos car outbound carl 4 cir 512
[Router-GigabitEthernet0/2] quit# 使用display qos carl命令查看CAR列表。
[Router]?display qos carl
List? Rules
1???? source-ip-address range 192.168.10.1 to 192.168.10.254 per-address shared-bandwidth
2???? source-ip-address range 192.168.20.1 to 192.168.20.254 per-address shared-bandwidth
3???? destination-ip-address range 192.168.10.1 to 192.168.10.254 per-address shared-bandwidth
4???? destination-ip-address range 192.168.20.1 to 192.168.20.254 per-address shared-bandwidth# 使用display qos car interface命令查看接口的流量監管配置情況和統計信息。
[Router]?display qos car interface gigabitethernet 0/1
Interface: GigabitEthernet0/1Direction: inboundRule: If-match carl 1CIR 512 (kbps), CBS 32000 (Bytes), EBS 0 (Bytes)Green action? : passYellow action : passRed action??? : discardGreen packets : 0 (Packets), 0 (Bytes)Yellow packets: 0 (Packets), 0 (Bytes)Red packets?? : 0 (Packets), 0 (Bytes)Rule: If-match carl 2CIR 512 (kbps), CBS 32000 (Bytes), EBS 0 (Bytes)Green action? : passYellow action : passRed action??? : discardGreen packets : 0 (Packets), 0 (Bytes)Yellow packets: 0 (Packets), 0 (Bytes)Red packets?? : 0 (Packets), 0 (Bytes)Direction: outboundRule: If-match carl 3CIR 512 (kbps), CBS 32000 (Bytes), EBS 0 (Bytes)Green action? : passYellow action : passRed action??? : discardGreen packets : 0 (Packets), 0 (Bytes)Yellow packets: 0 (Packets), 0 (Bytes)Red packets?? : 0 (Packets), 0 (Bytes)Rule: If-match carl 4CIR 512 (kbps), CBS 32000 (Bytes), EBS 0 (Bytes)Green action? : passYellow action : passRed action??? : discardGreen packets : 0 (Packets), 0 (Bytes)Yellow packets: 0 (Packets), 0 (Bytes)Red packets?? : 0 (Packets), 0 (Bytes)[Router]?display qos car interface gigabitethernet 0/2
Interface: GigabitEthernet0/2Direction: inboundRule: If-match carl 1CIR 512 (kbps), CBS 32000 (Bytes), EBS 0 (Bytes)Green action? : passYellow action : passRed action??? : discardGreen packets : 0 (Packets), 0 (Bytes)Yellow packets: 0 (Packets), 0 (Bytes)Red packets?? : 0 (Packets), 0 (Bytes)Rule: If-match carl 2CIR 512 (kbps), CBS 32000 (Bytes), EBS 0 (Bytes)Green action? : passYellow action : passRed action??? : discardGreen packets : 0 (Packets), 0 (Bytes)Yellow packets: 0 (Packets), 0 (Bytes)Red packets?? : 0 (Packets), 0 (Bytes)Direction: outboundRule: If-match carl 3CIR 512 (kbps), CBS 32000 (Bytes), EBS 0 (Bytes)Green action? : passYellow action : passRed action??? : discardGreen packets : 0 (Packets), 0 (Bytes)Yellow packets: 0 (Packets), 0 (Bytes)Red packets?? : 0 (Packets), 0 (Bytes)Rule: If-match carl 4CIR 512 (kbps), CBS 32000 (Bytes), EBS 0 (Bytes)Green action? : passYellow action : passRed action??? : discardGreen packets : 0 (Packets), 0 (Bytes)Yellow packets: 0 (Packets), 0 (Bytes)Red packets?? : 0 (Packets), 0 (Bytes)3.3.6 保存配置
# 保存出口路由器Router上的配置。
[Router] save
The current configuration will be written to the device. Are you sure? [Y/N]:y
Please input the file name(*.cfg)[flash:/startup.cfg]
(To leave the existing filename unchanged, press the enter key):
flash:/startup.cfg exists, overwrite? [Y/N]:y
Validating file. Please wait...
Saved the current configuration to mainboard device successfully.3.4? 驗證配置
3.4.1 同一個部門內部兩臺PC間可以ping通。
# 以VLAN 10所在的業務部門為例,PC間是通過ACCSW1實現二層互通的。如果用戶間互ping測
試正常,則說明二層互通正常。
<PC1> ping 192.168.10.83
Ping 192.168.10.83 (192.168.10.83): 56 data bytes, press CTRL+C to break
56 bytes from 192.168.10.83: icmp_seq=0 ttl=255 time=1.328 ms
56 bytes from 192.168.10.83: icmp_seq=1 ttl=255 time=0.808 ms
56 bytes from 192.168.10.83: icmp_seq=2 ttl=255 time=0.832 ms
56 bytes from 192.168.10.83: icmp_seq=3 ttl=255 time=0.904 ms
56 bytes from 192.168.10.83: icmp_seq=4 ttl=255 time=0.787 ms--- Ping statistics for 192.168.10.83 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.787/0.932/1.328/0.202 ms3.4.2 兩個不同部門內的PC可以ping通。
# 部門間的通信是通過CORESW1或CORESW2實現的。如果用戶之間互ping測試正常,則說明兩
個部門之間通過VLAN接口實現三層互通正常。
<PC1> ping 192.168.20.5
Ping 192.168.20.5 (192.168.20.5): 56 data bytes, press CTRL+C to break
56 bytes from 192.168.20.5: icmp_seq=0 ttl=255 time=69.146 ms
56 bytes from 192.168.20.5: icmp_seq=1 ttl=255 time=1.735 ms
56 bytes from 192.168.20.5: icmp_seq=2 ttl=255 time=1.356 ms
56 bytes from 192.168.20.5: icmp_seq=3 ttl=255 time=1.302 ms
56 bytes from 192.168.20.5: icmp_seq=4 ttl=255 time=1.379 ms--- Ping statistics for 192.168.20.5 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.302/14.984/69.146/27.082 ms3.4.3 每個部門各選一臺PC可以ping通外網。
# 以VLAN 10所在的業務部門為例,通過在PC1上ping公網網關地址(即與出口路由器對接的運營
商設備的IP地址)來驗證是否可以訪問外網,如果ping測試正常,則說明內網用戶訪問外網正常。
測試方法與步驟1類似。
3.5 配置文件
3.5.1 接入交換機ACCSW1
#sysname ACCSW1
#telnet server enable
#dhcp snooping enable
#
vlan 5
#
vlan 10
#
vlan 20
#stp bpdu-protection
#
interface Vlan-interface5ip address 10.10.1.1 255.255.255.0
#
interface GigabitEthernet1/0/1port link-mode bridgeport access vlan 10stp edged-portip verify source ip-address mac-addressdhcp snooping binding record
#
interface GigabitEthernet1/0/2port link-mode bridgeport access vlan 20stp edged-portip verify source ip-address mac-addressdhcp snooping binding record
#
interface GigabitEthernet1/0/3port link-mode bridgeport link-type trunkport trunk permit vlan 10 20dhcp snooping trust
#
interface GigabitEthernet1/0/4port link-mode bridgeport link-type trunkport trunk permit vlan 10 20
#
interface Ten-GigabitEthernet1/0/10port link-mode bridgeport access vlan 5
#
line vty 0 63authentication-mode scheme
#
local-user admin class managepassword hash $h$6$ZJSf20ub4uEzjy2F$cXW3O3Jt5Ci21ECze7w2MdRpLebMaE4vXBo59frUrIZs+Knxw76oNBu+HiB0zqkTfrnw1Phe0rSRa5d+OSIIbg==service-type telnetauthorization-attribute user-role network-adminauthorization-attribute user-role network-operator# 接入交換機ACCSW2、ACCSW3、ACCSW4:
接入交換機ACCSW2、ACCSW3、ACCSW4除了VLAN ID、管理VLAN接口IP地址、接口編號與
ACCSW1不同外,其他配置與ACCSW1相同,配置文件略。
3.5.2 核心交換機CORESW1
#sysname CORESW1
#
track 1 interface GigabitEthernet1/0/7
#
ospf 100 router-id 3.3.3.3area 0.0.0.0network 172.16.1.0 0.0.0.255network 172.16.3.0 0.0.0.255network 192.168.10.0 0.0.0.255network 192.168.20.0 0.0.0.255
#dhcp enable
#
vlan 10
#
vlan 20
#
vlan 30
#
vlan 40
#
vlan 50
#
vlan 100
#
vlan 300
#
ftth
#
dhcp server ip-pool 1gateway-list 192.168.10.1network 192.168.10.0 mask 255.255.255.0dns-list 202.101.100.199expired day 30static-bind ip-address 192.168.10.254 mask 255.255.255.0 client-identifier aabb-cccc-dd
#
dhcp server ip-pool 2gateway-list 192.168.20.1network 192.168.20.0 mask 255.255.255.0dns-list 202.101.100.199expired day 30
#
interface Vlan-interface10ip address 192.168.10.1 255.255.255.0
#
interface Vlan-interface20ip address 192.168.20.1 255.255.255.0
#
interface Vlan-interface100ip address 172.16.1.1 255.255.255.0
#
interface Vlan-interface30ip address 172.16.3.1 255.255.255.0vrrp vrid 1 virtual-ip 172.16.3.10vrrp vrid 1 priority 120vrrp vrid 1 preempt-mode delay 5000vrrp vrid 1 track 1 priority reduced 30
#
interface GigabitEthernet1/0/1port link-mode bridgeport link-type trunkport trunk permit vlan 10
#
interface GigabitEthernet1/0/2port link-mode bridgeport link-type trunkport trunk permit vlan 20
#
interface GigabitEthernet1/0/5port link-mode bridgeport link-type trunkport trunk permit vlan 300
##?核心交換機CORESW2:
核心交換機CORESW2除了VLAN ID、接口編號、OSPF的router-id、VRRP備份組1的優先級與
CORESW1不同外,其他配置與CORESW1相同,配置文件略。
3.5.3 出口路由器Router
#sysname Router
#packet-filter default deny
#qos carl 1 source-ip-address range 192.168.10.1 to 192.168.10.254 per-address shared-bandwidthqos carl 2 source-ip-address range 192.168.20.1 to 192.168.20.254 per-address shared-bandwidthqos carl 3 destination-ip-address range 192.168.10.1 to 192.168.10.254 per-address shared-bandwidthqos carl 4 destination-ip-address range 192.168.20.1 to 192.168.20.254 per-address shared-bandwidth
#
ospf 10 router-id 1.1.1.1default-route-advertise alwaysarea 0.0.0.0network 172.16.1.0 0.0.0.255network 172.16.2.0 0.0.0.255
#dns proxy enabledns server 202.101.100.199
#
interface GigabitEthernet0/1port link-mode routeip address 172.16.1.2 255.255.255.0packet-filter 2000 inboundqos car inbound carl 1 cir 512 cbs 32000 ebs 0 green pass red discard yellow passqos car inbound carl 2 cir 512 cbs 32000 ebs 0 green pass red discard yellow passqos car outbound carl 3 cir 512 cbs 32000 ebs 0 green pass red discard yellow passqos car outbound carl 4 cir 512 cbs 32000 ebs 0 green pass red discard yellow pass
#
interface GigabitEthernet0/2port link-mode routeip address 172.16.2.2 255.255.255.0packet-filter 2000 inboundqos car inbound carl 1 cir 512 cbs 32000 ebs 0 green pass red discard yellow passqos car inbound carl 2 cir 512 cbs 32000 ebs 0 green pass red discard yellow passqos car outbound carl 3 cir 512 cbs 32000 ebs 0 green pass red discard yellow passqos car outbound carl 4 cir 512 cbs 32000 ebs 0 green pass red discard yellow pass
#
interface GigabitEthernet0/0port link-mode routeip address 202.101.100.2 255.255.255.252
#ip route-static 0.0.0.0 0 202.101.100.1
#
acl basic 2000rule 0 permit source 192.168.10.0 0.0.0.255rule 5 permit source 192.168.20.0 0.0.0.255rule 10 permit source 172.16.1.0 0.0.0.255rule 15 permit source 172.16.2.0 0.0.0.255rule 20 permit source 172.16.3.0 0.0.0.255
#









 | (WSDM24)預訓練推薦系統:因果去偏視角)






)

