HTTPS服務
一、常見的端口
http ------ 80 明文
https ------ 443 數據加密
dns ------ 53
ssh ------ 22
telent ------ 23
HTTPS = http + ssl或者tls (安全模式)
二、原理:
c(客戶端):
1、clienthello:支持哪些版本、支持哪些加密算法,隨機生成一組32字節數據random_c
3、clientkeyexchange:公鑰加密數據pre_master
s(服務器):
2、serverhello:確定版本、確定加密算法,隨機生成一組32個字節得數據random_s,生成公鑰和私鑰
servercertificate:證書、公鑰
4、data:服務端收到pre_master—私鑰進行解密
最后得會話密鑰:random_c+random_s+pre_master
三、實現安全------認證/鑒權
1、CA機構:認證某網站是安全的,給服務器的證書進行授權(相當于中介)
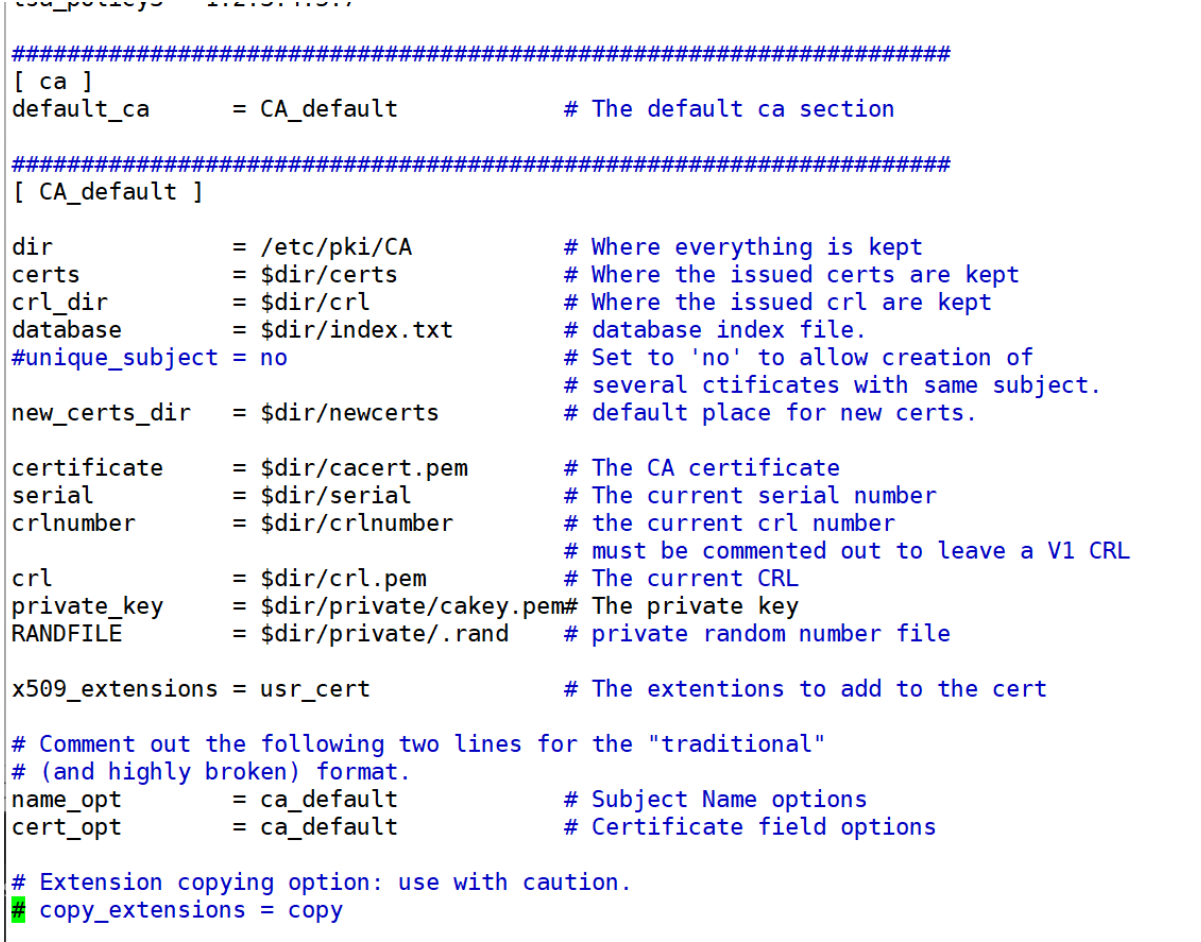
[root@stw ~]# vim /etc/pki/tls/openssl.cnf
dir = /etc/pki/CA(默認的CA的工作目錄)
certs = $dir/certs(/etc/pki/CA/certs,證書所在的目錄)
database = $dir/index.txt(/etc/pki/CA/index.txt,數據庫位置,現在沒有,需要生成)
certificate = $dir/cacert.pem(/etc/pki/CA/cacert.pem,CA的根證書,目前沒有,需要生成)
serial = $dir/serial( /etc/pki/CA/serial,序列號,目前不存在)
private_key = $dir/private/cakey.pem(私鑰,目前不存在,需要生成)
四、配置https服務
openssl: 命令的選項
-x509 :生成自簽名證書格式,專用于創建私有CA
-new :生成新證書的簽署請求
-key :生成請求時用到的私鑰文件路徑
-out :生成后的文件存放路徑,如果是自簽名操作,將直接生成簽署過的證書
-days :證書有效期 默認是365天
CA服務器:
1、生成私鑰
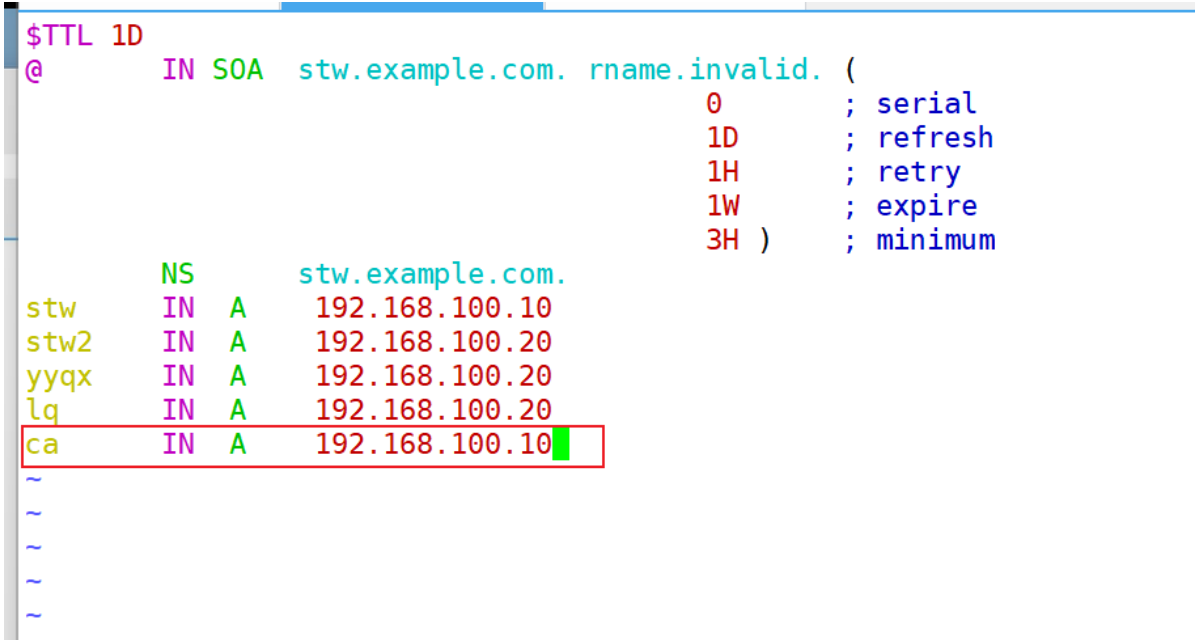
前提:在DNS服務器上的正向解析數據庫中添加ca.example.com的解析內容
[root@stw ~]# cd /var/named
[root@stw named]# vim stw.com
[root@stw named]# systemctl restart named
[root@stw named]# systemctl enable named
在主機CA上為主機CA生成私鑰
(umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem)
root用戶生成的文件默認的umask值是644,我們需要只讓自己能讀寫此文件,所以需要umask值為600,所以應該設置umask值為066(文件的最大執行權限為666,666-066=600,目錄的最大執行權限為777,777-077=700),對于文件來說給077和給066沒有區別,都是只讓自己讀取此文件。
[root@stw ~]# (umask 077;openssl genrsa -out /etc//pki/CA/private/cakey.pem)
Generating RSA private key, 2048 bit long modulus
....................+++
...........................+++
e is 65537 (0x10001)
2、生成自簽名證書
[root@stw ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:LQ
Organizational Unit Name (eg, section) []:IT
Common Name (eg, your name or your server's hostname) []:ca.example.com
Email Address []:root@example.com
3、創建index.txt文件和serial文件
[root@stw ~]# cd /etc/pki/CA/
[root@stw CA]# ls
cacert.pem certs crl newcerts private
[root@stw CA]# touch index.txt
[root@stw CA]# echo 01 > serial //序列號里面不能為空
[root@stw CA]# ls
cacert.pem certs crl index.txt newcerts private serial
Web(https)服務器:
1、關聯DNS
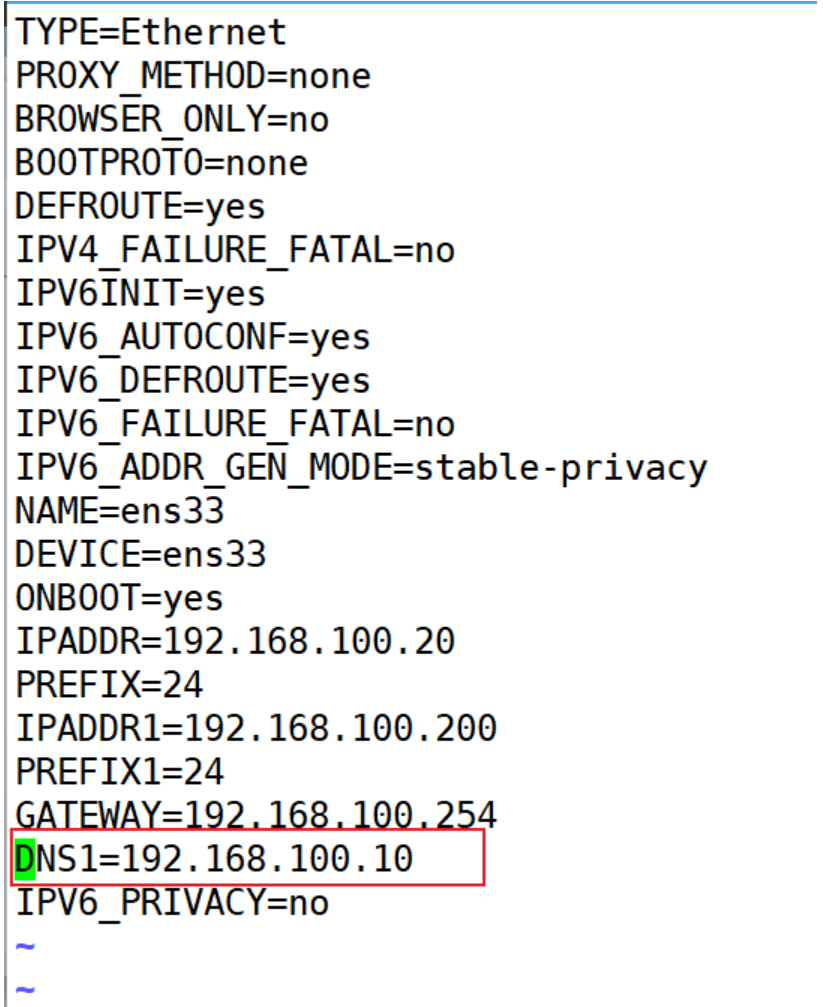
[root@stw2 ~]# cd /etc/sysconfig/network-scripts/
[root@stw2 network-scripts]# vim ifcfg-ens33
[root@stw2 network-scripts]# systemctl restart network
[root@stw2 ~]# nslookup ca.example.com
Server: 192.168.100.10
Address: 192.168.100.10#53Name: ca.example.com
Address: 192.168.100.10
2、生成私鑰放在對應的位置
[root@stw2 ~]# cd /etc/httpd
[root@stw2 httpd]# ls
conf conf.d conf.modules.d logs modules run
[root@stw2 httpd]# mkdir ssl
[root@stw2 httpd]# cd ssl
[root@stw2 ssl]# (umask 077;openssl genrsa -out /etc/httpd/ssl/httpd.key)
Generating RSA private key, 2048 bit long modulus
..............................................................+++
..........................................................+++
e is 65537 (0x10001)
3、生成自簽名證書放在對應位置
[root@stw2 ssl]# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:LQ
Organizational Unit Name (eg, section) []:IT
Common Name (eg, your name or your server's hostname) []:stw2.example.com
Email Address []:root@example.comPlease enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@stw2 ssl]#
4、把剛剛生成的證書發送給CA機構,讓CA機構為Web服務器的證書進行簽名
Web服務器:
[root@stw2 ssl]# scp httpd.csr root@ca.example.com:/etc/pki/CA
The authenticity of host 'ca.example.com (192.168.100.10)' can't be established.
ECDSA key fingerprint is SHA256:R7/1dpul7cu8SnefsN2wQw5hKDL+xekk0ffasLS6OGI.
ECDSA key fingerprint is MD5:81:88:a1:16:52:83:c0:d5:59:ad:2b:3a:d5:52:02:bc.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'ca.example.com,192.168.100.10' (ECDSA) to the list of known hosts.
root@ca.example.com's password:
httpd.csr 100% 1033 339.7KB/s 00:00
CA服務器查看:
[root@stw CA]# ls
cacert.pem certs crl httpd.csr index.txt newcerts private serial
對Web服務器發送過來的證書進行認證授權
[root@stw CA]# openssl ca -in /etc/pki/CA/httpd.csr -out /etc/pki/CA/httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:Serial Number: 1 (0x1)ValidityNot Before: Aug 12 10:19:54 2025 GMTNot After : Aug 12 10:19:54 2026 GMTSubject:countryName = CNstateOrProvinceName = HBorganizationName = LQorganizationalUnitName = ITcommonName = stw2.example.comemailAddress = root@example.comX509v3 extensions:X509v3 Basic Constraints: CA:FALSENetscape Comment: OpenSSL Generated CertificateX509v3 Subject Key Identifier: 5B:8A:BD:D6:43:41:51:D0:6A:60:4D:4E:BD:8B:58:7C:F6:94:BD:A7X509v3 Authority Key Identifier: keyid:63:9E:05:A1:DA:A1:DA:74:9D:75:8D:B4:DF:D1:21:14:65:F9:DB:C6Certificate is to be certified until Aug 12 10:19:54 2026 GMT (365 days)
Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@stw CA]# ls
cacert.pem crl httpd.csr index.txt.attr newcerts serial
certs httpd.crt index.txt index.txt.old private serial.old
再把已經完成認證的證書發送回到Web服務器:
要先確認DNS中有stw2.example.com(Web服務器)的條目(這里已經存在此條目)
并且把DNS指向DNS服務器(這里的DNS服務器是自己)
[root@stw CA]# cd /etc/sysconfig/network-scripts/
[root@stw network-scripts]# vim ifcfg-ens33
[root@stw network-scripts]# systemctl restart network
[root@stw ~]# cd /etc/pki/CA
[root@stw CA]# scp httpd.crt root@stw2.example.com:/etc/httpd/ssl/
The authenticity of host 'stw2.example.com (192.168.100.20)' can't be established.
ECDSA key fingerprint is SHA256:R7/1dpul7cu8SnefsN2wQw5hKDL+xekk0ffasLS6OGI.
ECDSA key fingerprint is MD5:81:88:a1:16:52:83:c0:d5:59:ad:2b:3a:d5:52:02:bc.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'stw2.example.com,192.168.100.20' (ECDSA) to the list of known hosts.
root@stw2.example.com's password:
httpd.crt 100% 4557 1.1MB/s 00:00
[root@stw CA]#
Web服務器查看:
[root@stw2 ssl]# ls
httpd.crt httpd.csr httpd.key
安裝apche http擴展模塊mod_ssl
[root@stw2 ~]# yum -y install mod_ssl
修改主配置文件
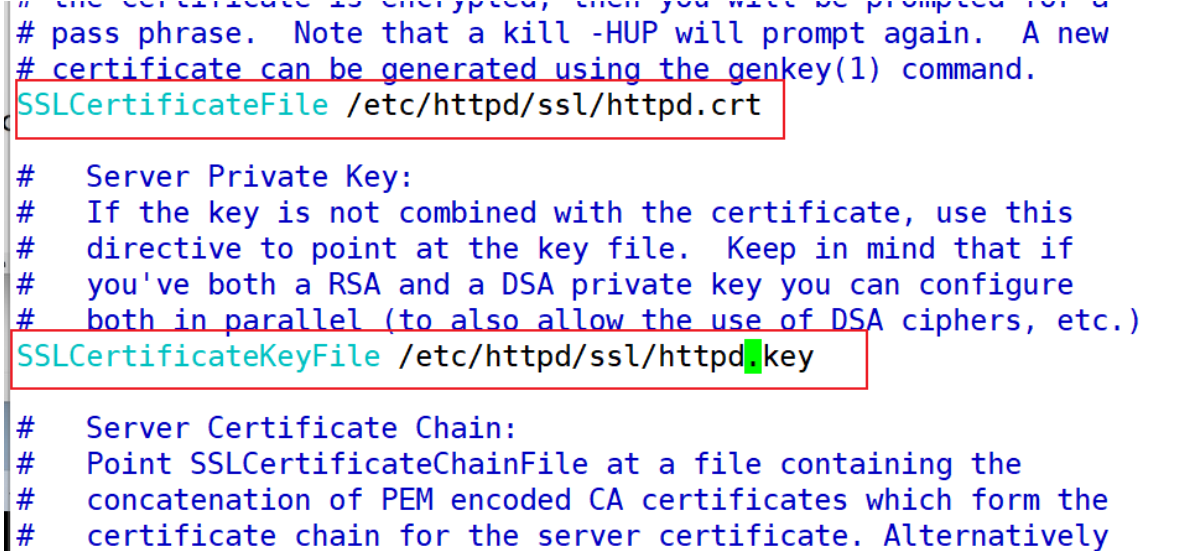
[root@stw2 ~]# vim /etc/httpd/conf.d/ssl.conf
部署網頁(虛擬主機中部署)
[root@stw2 conf.d]# vim httpd-vhosts.conf
[root@stw2 conf.d]# systemctl restart httpd
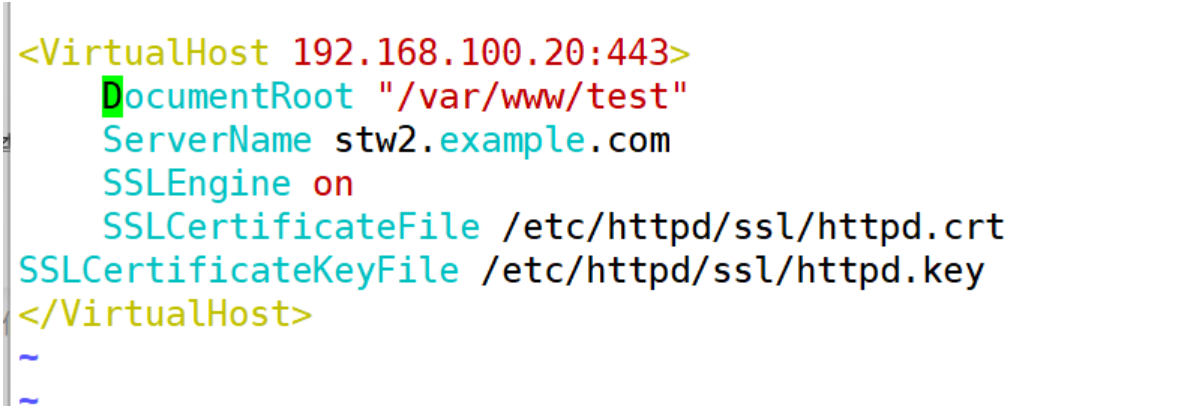
客戶端:
查看是否能解析到Web服務器
[root@stw3 ~]# nslookup
> stw2.example.com
Server: 192.168.100.10
Address: 192.168.100.10#53Name: stw2.example.com
Address: 192.168.100.20
將根證書傳遞到客戶端
[root@stw3 ~]# scp root@192.168.100.10:/etc/pki/CA/cacert.pem .
The authenticity of host '192.168.100.10 (192.168.100.10)' can't be established.
ECDSA key fingerprint is SHA256:R7/1dpul7cu8SnefsN2wQw5hKDL+xekk0ffasLS6OGI.
ECDSA key fingerprint is MD5:81:88:a1:16:52:83:c0:d5:59:ad:2b:3a:d5:52:02:bc.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.10' (ECDSA) to the list of known hosts.
root@192.168.100.10's password: cacert.pem 100% 1375 324.9KB/s 00:00
[root@stw3 ~]# ls
anaconda-ks.cfg Desktop Downloads Music Public Videos
cacert.pem Documents initial-setup-ks.cfg Pictures Templates
在瀏覽器中上傳,讓瀏覽器知道這個站點是安全的
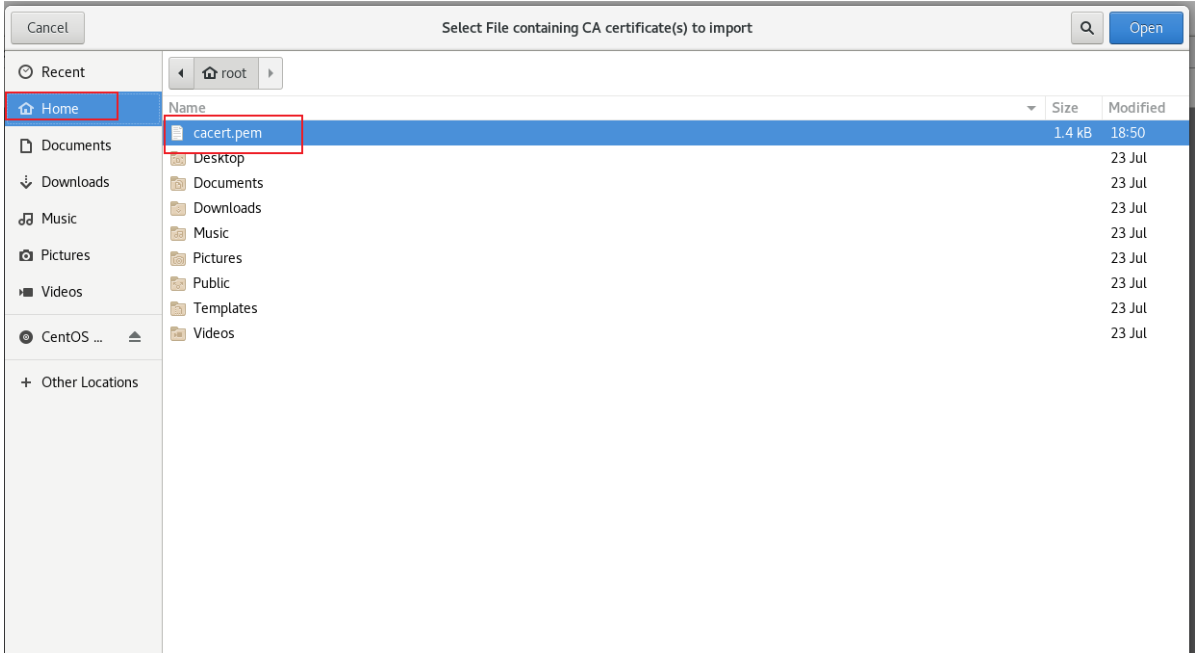
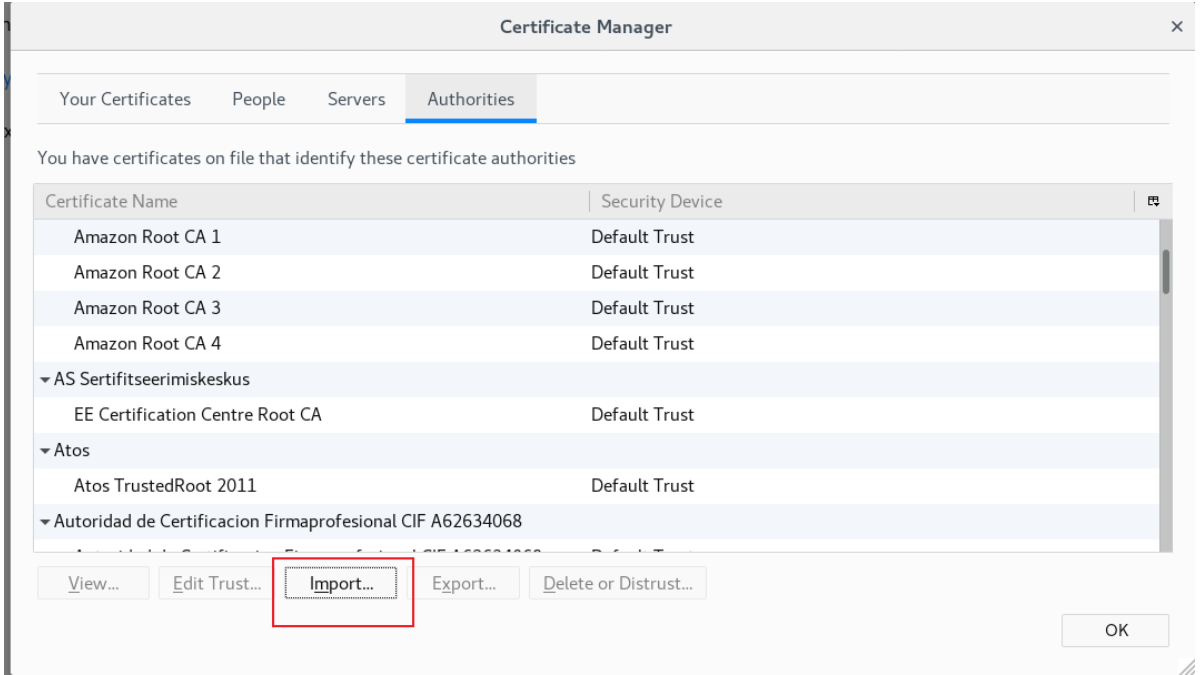
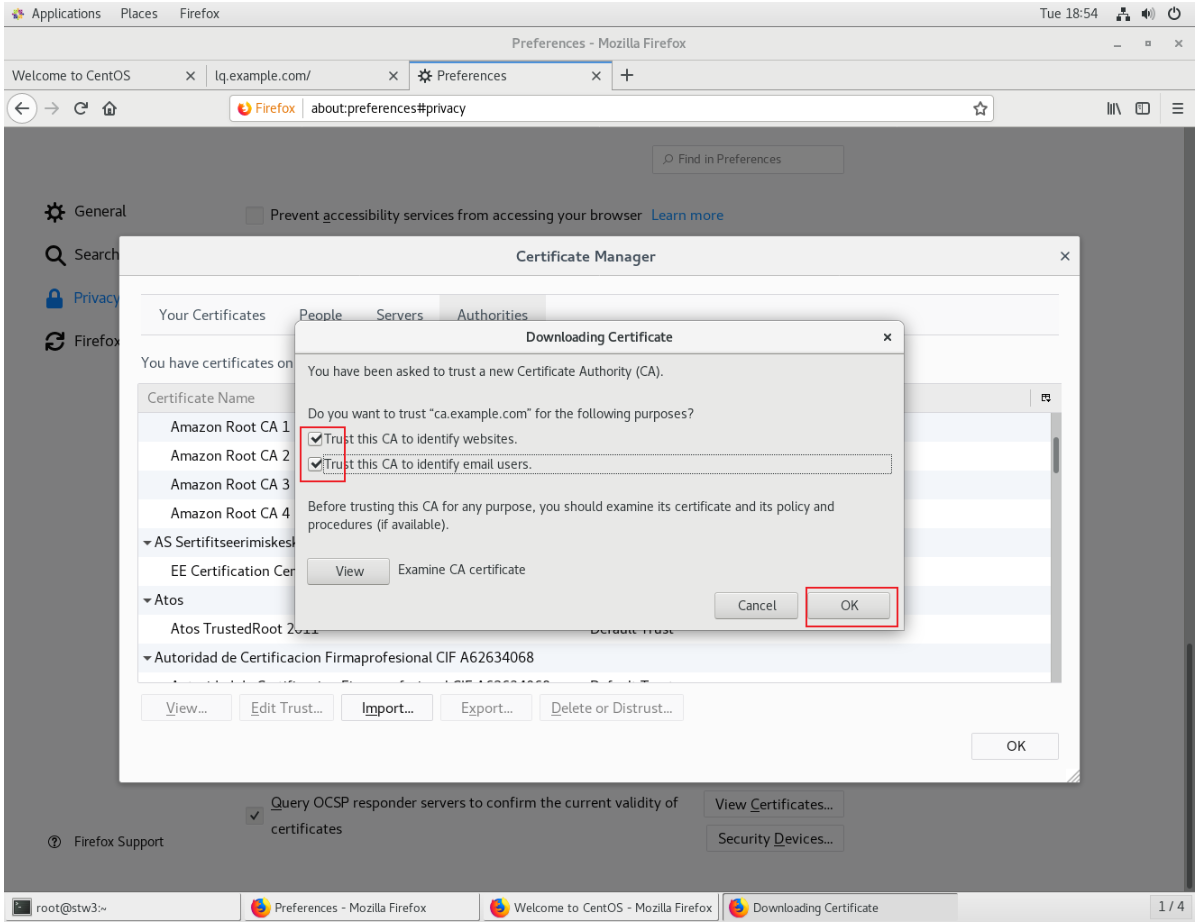
Web服務器:
在剛剛設置的網頁中寫入內容
[root@stw2 ~]# cd /var/www
[root@stw2 www]# ls
cgi-bin html luoqi yyqx
[root@stw2 www]# mkdir test
[root@stw2 www]# ls
cgi-bin html luoqi test yyqx
[root@stw2 www]# cd test
[root@stw2 test]# echo ssstttwww > index.html
客戶端訪問
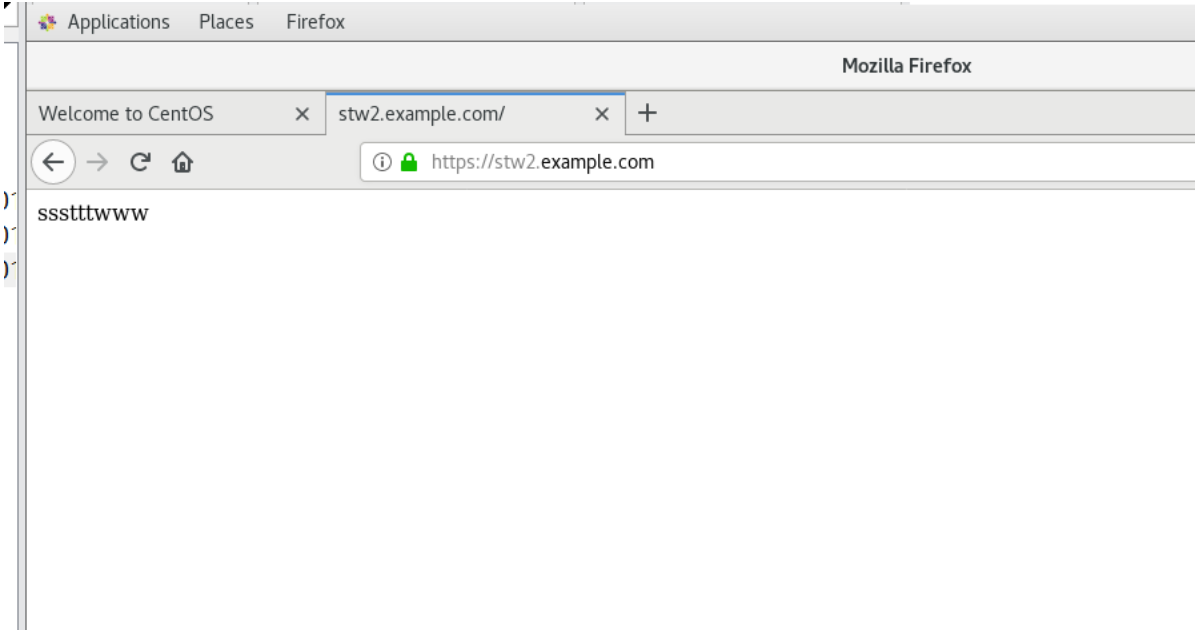
也可以命令訪問
[root@stw3 ~]# curl -k https://192.168.100.20
ssstttwww
五、訪問動態網頁
Web服務器:
1、安裝服務
[root@stw2 ~]# yum -y install mod_swgi
2、創建目錄并且導入文件
[root@stw2 ~]# mkdir /var/www/wsgi
[root@stw2 ~]# cd /var/www/wsgi
[root@stw2 wsgi]# ls
cacert.pem css images index.html python.txt
DNS服務器:
1、將Web服務器的條目添加到DNS
[root@stw ~]# vim /var/named/stw.com
[root@stw ~]# systemctl restart network
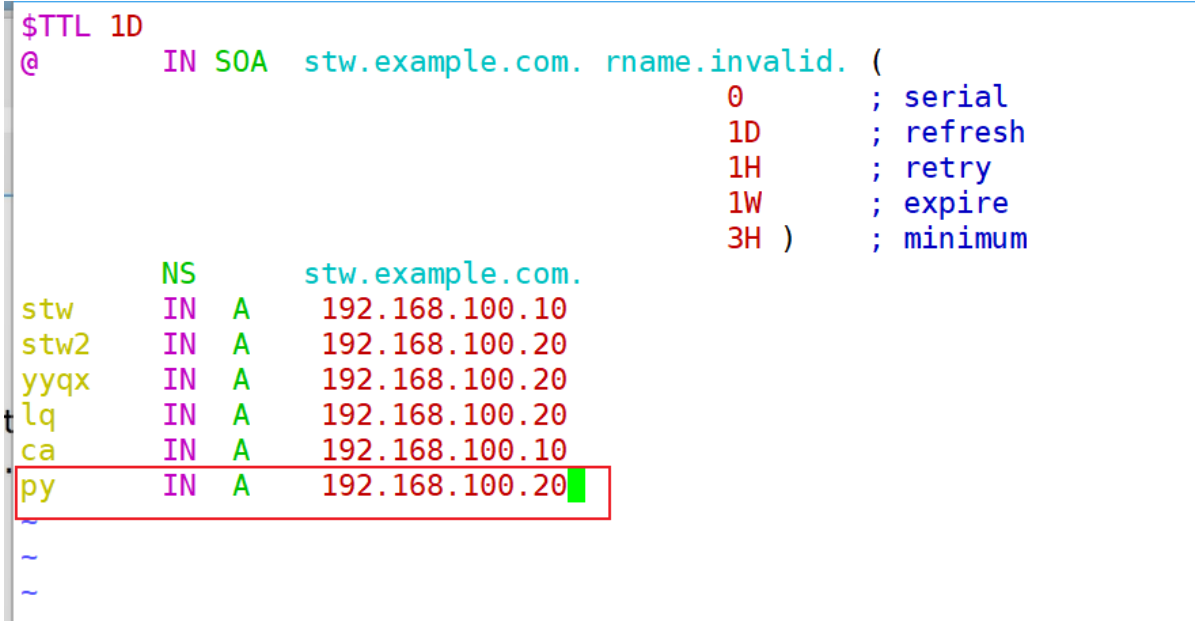
Web服務器:
1、將導入進來的腳本更改后綴名并加上執行權限
[root@stw2 wsgi]# ls
cacert.pem css images index.html python.txt
[root@stw2 wsgi]# cat python.txt
def application(environ, start_response):status = '200 OK'output = 'Hello World!'response_headers = [('Content-type', 'text/plain'),('Content-Length', str(len(output)))]start_response(status, response_headers)return [output]
[root@stw2 wsgi]# mv python.txt test.py
[root@stw2 wsgi]# ll
total 12
-rw-r--r--. 1 root root 1375 Aug 12 19:27 cacert.pem
drwxr-xr-x. 2 root root 23 Aug 12 19:27 css
drwxr-xr-x. 2 root root 68 Aug 12 19:27 images
-rw-r--r--. 1 root root 2251 Aug 12 19:27 index.html
-rw-r--r--. 1 root root 282 Aug 12 19:27 test.py
[root@stw2 wsgi]# chmod +x test.py
[root@stw2 wsgi]# ll
total 12
-rw-r--r--. 1 root root 1375 Aug 12 19:27 cacert.pem
drwxr-xr-x. 2 root root 23 Aug 12 19:27 css
drwxr-xr-x. 2 root root 68 Aug 12 19:27 images
-rw-r--r--. 1 root root 2251 Aug 12 19:27 index.html
-rwxr-xr-x. 1 root root 282 Aug 12 19:27 test.py
2、更改配置文件
[root@stw2 wsgi]# vim /etc/httpd/conf.d/httpd-vhosts.conf
[root@stw2 wsgi]# systemctl restart httpd
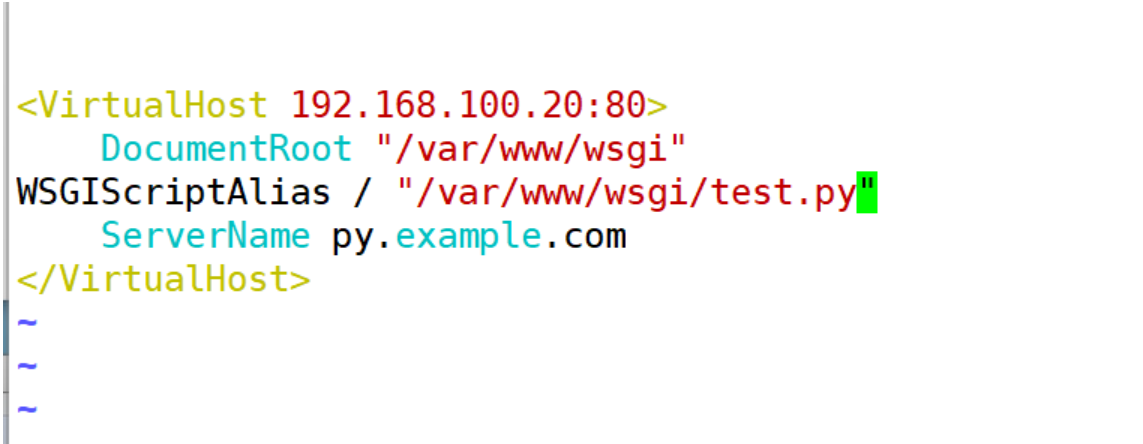
客戶端訪問hello world
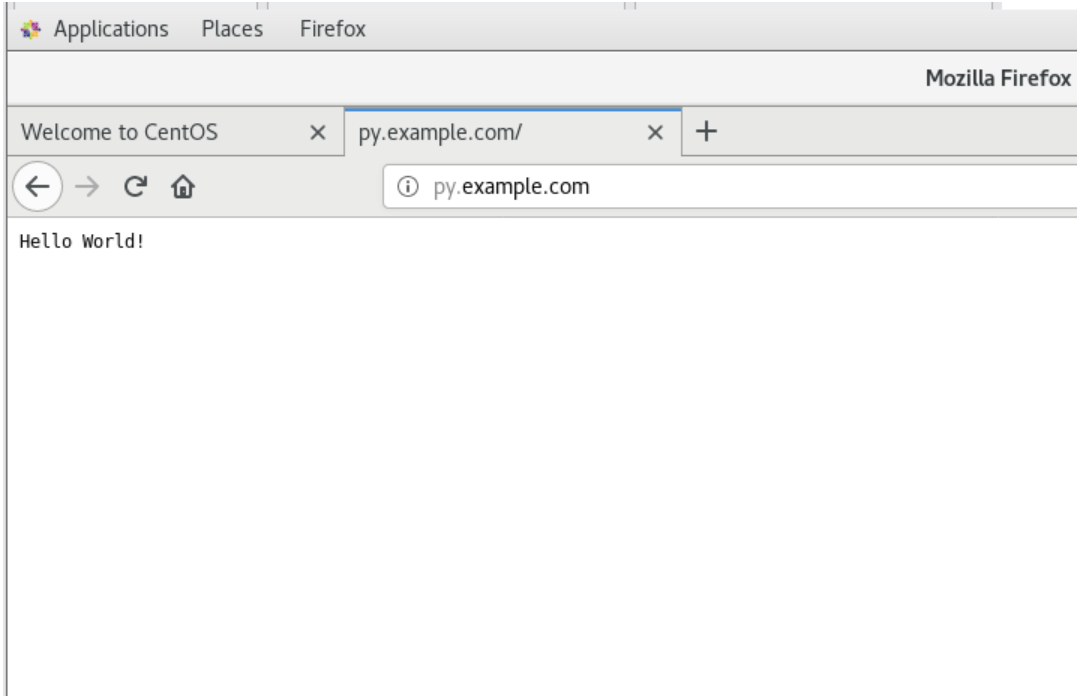
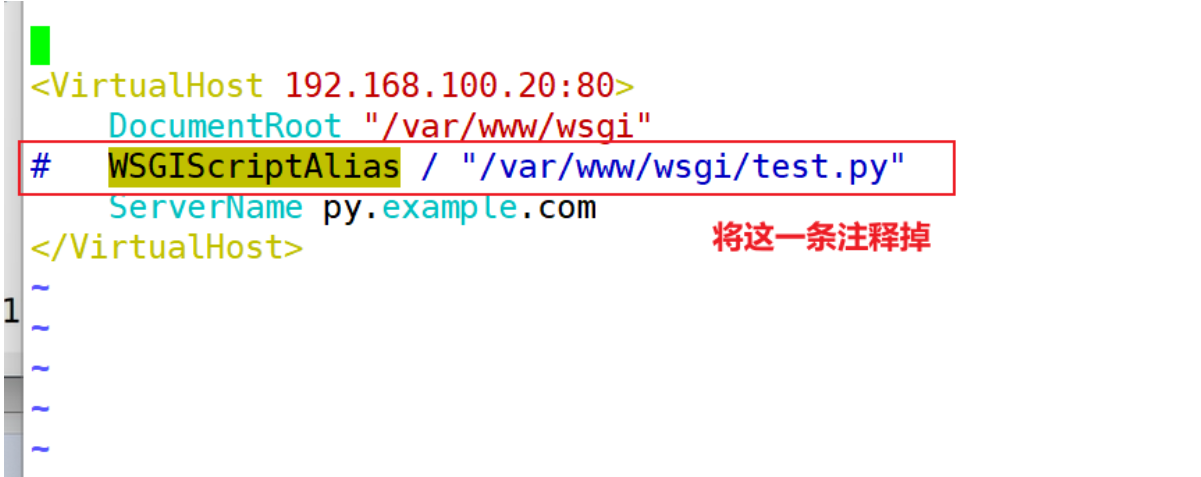
web服務器:
更改配置文件
[root@stw2 wsgi]# vim /etc/httpd/conf.d/httpd-vhosts.conf
[root@stw2 wsgi]# systemctl restart httpd
客戶端測試
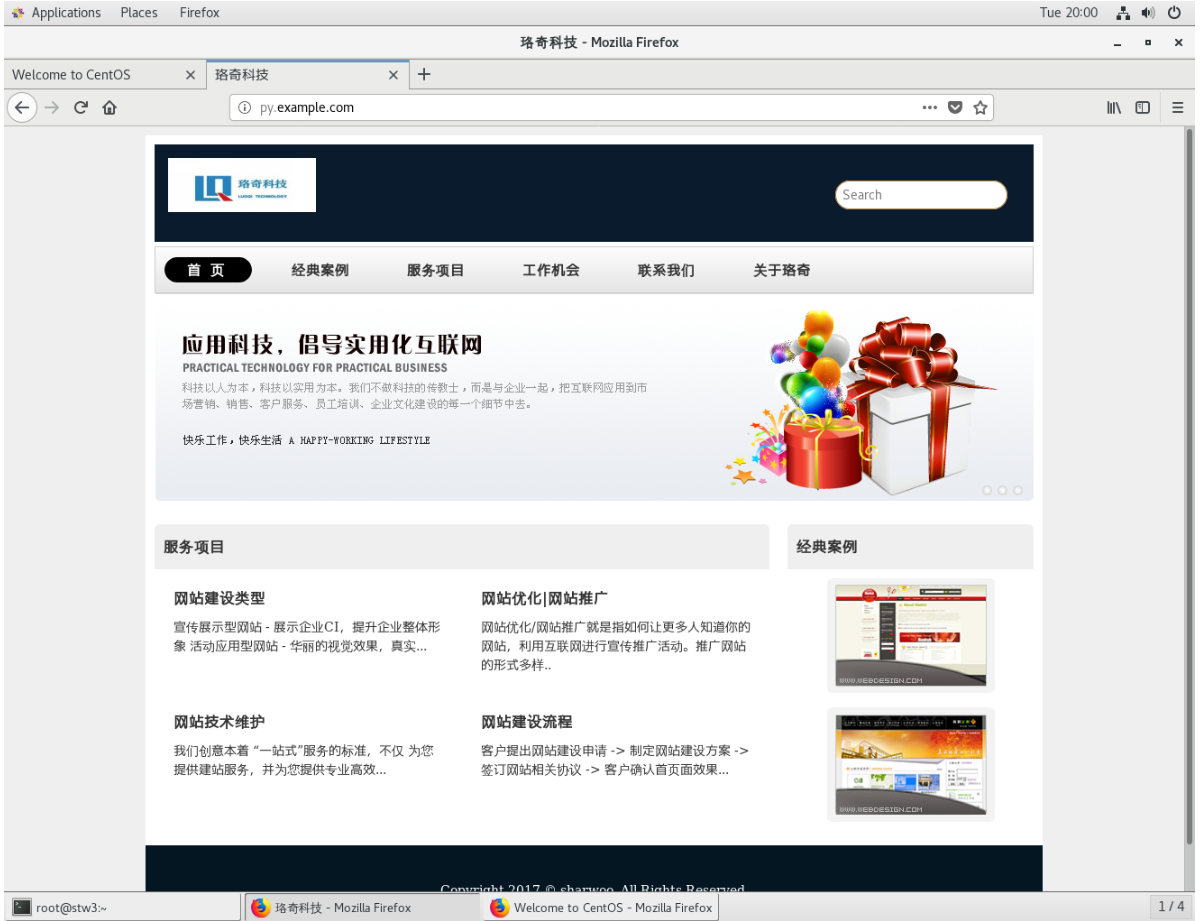
)



)


)






:動手實操,基于STC8編寫單任務執行程序,感悟MCU指令的執行過程)


![面試經典150題[001]:合并兩個有序數組(LeetCode 88)](http://pic.xiahunao.cn/面試經典150題[001]:合并兩個有序數組(LeetCode 88))

