實驗目的
了解防火墻(ENSP中的USG5500)域間轉發策略配置、NAT(與路由器NAT配置命令不同)配置。
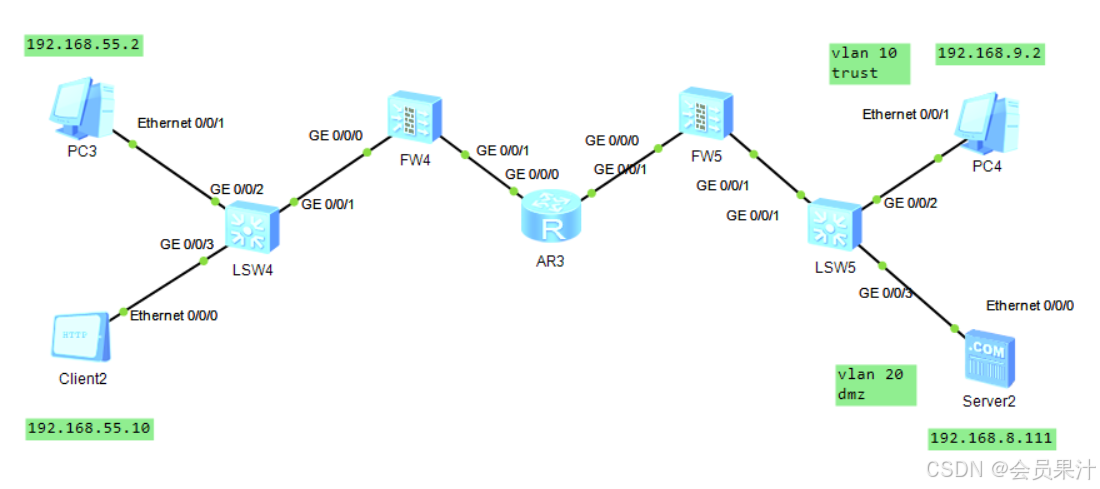
網絡拓撲
兩個防火墻連接分別連接一個內網,中間通過路由器連接。配置NAT之后,內網PC可以ping公網,client可以獲取server提供的服務(ftp和http)。服務器在dmz域,PC和client在trust域。
配置內容
右側交換機配置vlan區分業務。交換機和防火墻的連接應該可以使用鏈路聚合實現,但我沒有配置成功,干脆直接用一條鏈路。
域間安全策略
左側防火墻配置:
# 接口配置
interface GigabitEthernet0/0/0alias GE0/MGMTip address 192.168.55.254 255.255.255.0
#
interface GigabitEthernet0/0/1ip address 22.22.22.22 255.255.255.0
# 接口加入安全域
firewall zone trustadd interface GigabitEthernet0/0/0
#
firewall zone untrustadd interface GigabitEthernet0/0/1#
policy interzone trust untrust outboundpolicy 10action permitpolicy source 192.168.55.0 0.0.0.255
右側防火墻配置:
# 接口配置
interface GigabitEthernet0/0/0alias GE0/MGMTip address 33.33.33.3 255.255.255.0
#
interface GigabitEthernet0/0/1
# 子接口配置對應的vlan
interface GigabitEthernet0/0/1.10vlan-type dot1q 10alias GigabitEthernet0/0/1.10ip address 192.168.9.254 255.255.255.0
#
interface GigabitEthernet0/0/1.20vlan-type dot1q 20alias GigabitEthernet0/0/1.20ip address 192.168.8.254 255.255.255.0
# 接口加入安全域
firewall zone trustset priority 85add interface GigabitEthernet0/0/1.10
#
firewall zone untrustset priority 5add interface GigabitEthernet0/0/0
#
firewall zone dmzset priority 50add interface GigabitEthernet0/0/1.20# 域間安全策略# 訪問公網
policy interzone trust untrust outboundpolicy 10action permitpolicy source 192.168.9.0 0.0.0.255
# 公網訪問內網提供的服務
policy interzone dmz untrust inboundpolicy 10action permitpolicy service service-set ftppolicy service service-set httppolicy destination 192.168.8.0 0.0.0.255
ospf
路由器ospf配置:
# 通告直連IP和靜態路由
ospf 1 router-id 2.2.2.2 import-route staticarea 0.0.0.0 network 22.22.22.0 0.0.0.255 network 33.33.33.0 0.0.0.255
# 到左側nat地址池的路由
ip route-static 220.220.220.0 255.255.255.0 22.22.22.22
由于nat地址池與左側防火墻的外網接口不在同一網段,需要通告一條靜態路由。
nat配置
左側防火墻:
- 源nat
#nat address-group 1 220.220.220.220 220.220.220.230
#
nat-policy interzone trust untrust outboundpolicy 10action source-natpolicy source 192.168.55.0 0.0.0.255address-group 1 no-pat
基于域間安全策略配置,再配置源nat后,左側PC可以ping通在左側防火墻路由表內的公網IP。
右側防火墻:
- easyip
#
nat-policy interzone trust untrust outboundpolicy 1action source-natpolicy source 192.168.9.0 0.0.0.255easy-ip GigabitEthernet0/0/0
基于上面的配置,再配置easyip后,右側PC可以ping通在右側防火墻路由表內的公網IP。
- natserver
#nat server 0 protocol tcp global 33.33.33.3 ftp inside 192.168.8.111 ftpnat server 1 protocol tcp global 33.33.33.3 www inside 192.168.8.111 www
基于上面的配置,再配置natserver后,左側client可以獲取在右側服務器的http服務。
- aspf
#
firewall interzone dmz untrustdetect ftp
aspf與nat alg實現功能類似,使防火墻支持多端口協議服務
基于上面的配置,再配置natserver后,左側client可以獲取在右側服務器的ftp服務。
實驗效果
ping公網
左側主機ping通:
PC>ping 33.33.33.33Ping 33.33.33.33: 32 data bytes, Press Ctrl_C to break
From 33.33.33.33: bytes=32 seq=1 ttl=254 time=78 ms
From 33.33.33.33: bytes=32 seq=2 ttl=254 time=47 ms
From 33.33.33.33: bytes=32 seq=3 ttl=254 time=63 ms
From 33.33.33.33: bytes=32 seq=4 ttl=254 time=47 ms
From 33.33.33.33: bytes=32 seq=5 ttl=254 time=47 ms--- 33.33.33.33 ping statistics ---5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 47/56/78 ms
防火墻會話表:
[F1]display firewall session table
19:53:05 2025/05/10Current Total Sessions : 5icmp VPN:public --> public 192.168.55.2:3390[220.220.220.220:3390]-->33.33.33
.33:2048icmp VPN:public --> public 192.168.55.2:3646[220.220.220.220:3646]-->33.33.33
.33:2048icmp VPN:public --> public 192.168.55.2:3902[220.220.220.220:3902]-->33.33.33
.33:2048icmp VPN:public --> public 192.168.55.2:4158[220.220.220.220:4158]-->33.33.33
.33:2048icmp VPN:public --> public 192.168.55.2:4414[220.220.220.220:4414]-->33.33.33
.33:2048右側主機ping通:
PC>ping 22.22.22.2Ping 22.22.22.2: 32 data bytes, Press Ctrl_C to break
From 22.22.22.2: bytes=32 seq=1 ttl=254 time=46 ms
From 22.22.22.2: bytes=32 seq=2 ttl=254 time=47 ms
From 22.22.22.2: bytes=32 seq=3 ttl=254 time=32 ms
From 22.22.22.2: bytes=32 seq=4 ttl=254 time=31 ms
From 22.22.22.2: bytes=32 seq=5 ttl=254 time=31 ms--- 22.22.22.2 ping statistics ---5 packet(s) transmitted5 packet(s) received0.00% packet lossround-trip min/avg/max = 31/37/47 ms
右側防火墻會話表:
[F2]display firewall session table
19:56:13 2025/05/10Current Total Sessions : 5icmp VPN:public --> public 192.168.9.2:52542[33.33.33.3:2053]-->22.22.22.2:20
48icmp VPN:public --> public 192.168.9.2:52798[33.33.33.3:2054]-->22.22.22.2:20
48icmp VPN:public --> public 192.168.9.2:53054[33.33.33.3:2055]-->22.22.22.2:20
48icmp VPN:public --> public 192.168.9.2:53310[33.33.33.3:2056]-->22.22.22.2:20
48icmp VPN:public --> public 192.168.9.2:53566[33.33.33.3:2057]-->22.22.22.2:20
48
ftp服務


左側防火墻會話表:
[F1]display firewall session table
20:01:20 2025/05/10Current Total Sessions : 3ftp VPN:public --> public 192.168.55.10:2057[220.220.220.221:2057]-->33.33.33
.3:21ftp VPN:public --> public 192.168.55.10:2059[220.220.220.221:2059]-->33.33.33
.3:21tcp VPN:public --> public 192.168.55.10:2060[220.220.220.221:2060]-->33.33.33
.3:2053
右側防火墻會話表:
[F2]display firewall session table
20:02:01 2025/05/10Current Total Sessions : 4ftp VPN:public --> public 220.220.220.221:2057+->33.33.33.3:21[192.168.8.111:
21]ftp VPN:public --> public 220.220.220.221:2059+->33.33.33.3:21[192.168.8.111:
21]ftp VPN:public --> public 220.220.220.221:2061+->33.33.33.3:21[192.168.8.111:
21]ftp-data VPN:public --> public 220.220.220.221:2062-->33.33.33.3:2054[192.168
.8.111:2054])












全部被“重置連接”或超時)

)



