一.概述
1.DAI作用
①.使用DAI,管理員可以指定交換機的端口為信任和非信任端口:
信任端口可以轉發任何ARP信息
非信任端口的ARP消息要進行ARP檢測驗證
②.交換機執行如下的ARP驗證:
靜態ARP監控:為一個靜態的IP地址配置一個靜態ARP訪問控制列表
動態ARP監控:為DHCP指派的IP地址引用DHCP snooping綁定數據庫
2.DAI配置步驟
①確認DHCP snooping技術已經被激活,并且已經完全填充數據庫。
—沒有DHCP服務器,也需要配置DHCP snooping
②指定某端口為信任端口,也就是接受這個接口上的ARP欺騙威脅。
—交換機級聯的trunk接口必須配置為信任接口
③默認其他接口為非信任端口
④在每一個端口上設置ARP限速(可選)
—防止進行arp掃描
⑤配置一個ARP訪問控制列表,靜態IP映射到MAC.(可選)
⑥調整error-disable行為。
⑦在特定VLAN中啟用ARP Inspect功能。
3.測試拓撲
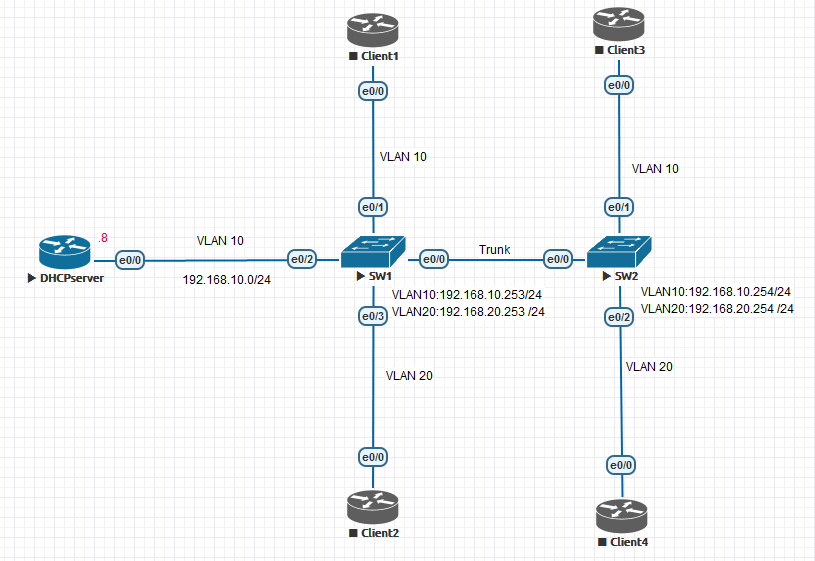
二.基本配置
1.DHCPserver
hostname DHCPserver
interface Ethernet0/0
ip address 192.168.10.8 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 192.168.10.254
ip dhcp relay information trust-all
ip dhcp excluded-address 192.168.10.8
ip dhcp excluded-address 192.168.10.254
ip dhcp excluded-address 192.168.20.254
ip dhcp excluded-address 192.168.10.253
ip dhcp excluded-address 192.168.20.253
ip dhcp pool vlan10Pool
network 192.168.10.0 255.255.255.0
default-router 192.168.10.254
ip dhcp pool vlan20Pool
network 192.168.20.0 255.255.255.0
default-router 192.168.20.254
2.host SW1
hostname SW1
VLAN 10
VLAN 20
interface Ethernet0/0
switchport trunk encapsulation dot1q
switchport mode trunk
spanning-tree portfast
interface range Ethernet0/1-2
switchport access vlan 10
switchport mode access
spanning-tree portfast
interface Ethernet0/3
switchport access vlan 20
switchport mode access
spanning-tree portfast
interface Vlan10
ip address 192.168.10.253 255.255.255.0
no shutdown
interface Vlan20
ip address 192.168.20.253 255.255.255.0
ip helper-address 192.168.10.8
no shutdown
!配置DHCP snooping
ip dhcp snooping
clock timezone GMT +8
do clock set 21:05:00 18 Apr 2020
ip dhcp snooping database unix:/dhcp.db
int rang e0/0, e0/2
ip dhcp snooping trust
int rang e0/1, e0/3
ip dhcp snooping limit rate 3
exit
ip dhcp snooping vlan 10,20
3.host SW2
hostname SW2
VLAN 10
VLAN 20
interface Ethernet0/0
switchport trunk encapsulation dot1q
switchport mode trunk
interface Ethernet0/1
switchport access vlan 10
switchport mode access
spanning-tree portfast
interface Ethernet0/2
switchport access vlan 20
switchport mode access
spanning-tree portfast
interface Vlan10
ip address 192.168.10.254 255.255.255.0
no shutdown
interface Vlan20
ip address 192.168.20.254 255.255.255.0
ip helper-address 192.168.10.8
no shutdown
ip route 0.0.0.0 0.0.0.0 192.168.10.253
!配置DHCP snooping
ip dhcp snooping
clock timezone GMT +8
do clock set 21:05:00 18 Apr 2020
ip dhcp snooping database unix:/dhcp.db
int e0/0
ip dhcp snooping trust
int rang e0/1-2
ip dhcp snooping limit rate 3
exit
ip dhcp snooping vlan 10,20
4.驗證
①Client1能正常獲取IP地址
Client1#show ip int br | in Ethernet0/0
Ethernet0/0 192.168.10.1 YES DHCP up up
Client1#
②Client2能正常獲取IP地址
Client2#show ip int br | in Ethernet0/0
Ethernet0/0 192.168.20.1 YES DHCP up up
Client2#
③Client3能正常獲取IP地址
Client3#show ip int br | in Ethernet0/0
Ethernet0/0 192.168.10.2 YES DHCP up up
Client3#
④Client4能正常獲取IP地址
Client4#show ip int br | in Ethernet0/0
Ethernet0/0 192.168.20.2 YES DHCP up up
Client4#
三.配置交換機的ARP監控
1.配置啟用DAI交換機之間的互聯鏈路接口為信任端口
SW1和SW2
int e0/0
ip arp inspection trust
2.對非信任端口ARP進行限速
SW1和SW2
int range E0/1-3
ip arp inspection limit rate 10
3.為非信任端口上的所有靜態主機配置ARP監控豁免的ACL
SW1
arp access-list xll-ARP-Filter
permit ip host 192.168.10.8 mac host aabb.cc00.4000
ip arp inspection filter xll-ARP-Filter vlan 10
備注:如果ip arp inspection filter xll-ARP-Filter vlan 10 static,則只檢測靜態綁定的,不檢測由DHCP snooping動態生成的庫。
4.設置違規端口error-disable自動恢復時間為180秒
SW1和SW2
errdisable recovery cause arp-inspection
errdisable recovery interval 180
5.在特定vlan啟用ARP監控
SW1和SW2
ip arp inspection vlan 10,20
四.驗證
1.Client1~4都能ping通DHCPserver
Client1#ping 192.168.10.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.8, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 5/5/5 ms
Client1#
Client2#ping 192.168.10.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Client2#
Client3#ping 192.168.10.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.8, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Client3#
Client4#ping 192.168.10.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Client4#
DHCPserver(config)#int e0/0
DHCPserver(config-if)#mac
DHCPserver(config-if)#mac?
mac-address mace
2.如果手工修改DHCPserver的E0/0接口mac地址,SW1會報錯
DHCPserver(config-if)#mac-a
DHCPserver(config-if)#mac-address 1.1.1
DHCPserver(config-if)#
SW1(config)#
*Apr 18 14:25:05.424: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Et0/2, vlan 10.([0001.0001.0001/192.168.10.8/aabb.cc80.2000/192.168.10.254/22:25:04 GMT Sat Apr 18 2020])
*Apr 18 14:25:05.424: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Et0/2, vlan 10.([0001.0001.0001/192.168.10.8/aabb.cc80.1000/192.168.10.253/22:25:04 GMT Sat Apr 18 2020])
*Apr 18 14:25:05.424: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Et0/2, vlan 10.([0001.0001.0001/192.168.10.8/aabb.cc00.7000/192.168.10.3/22:25:04 GMT Sat Apr 18 2020])
SW1(config)#do sho
*Apr 18 14:25:05.424: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Et0/2, vlan 10.([0001.0001.0001/192.168.10.8/aabb.cc00.5000/192.168.10.4/22:25:04 GMT Sat Apr 18 2020])
*Apr 18 14:25:05.424: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Et0/2, vlan 10.([0001.0001.0001/192.168.10.8/ffff.ffff.ffff/192.168.10.8/22:25:04 GMT Sat Apr 18 2020])


)
)

)







深度解析:從標準架構到商用實踐)




)
