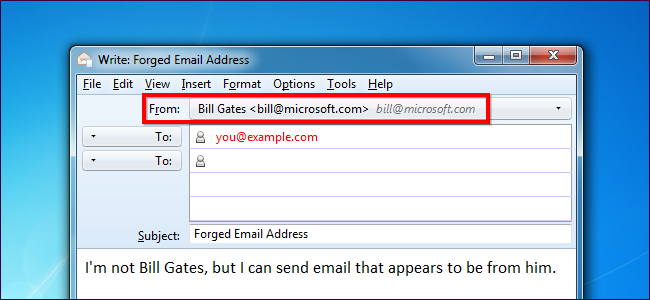
Consider this a public service announcement: Scammers can forge email addresses. Your email program may say a message is from a certain email address, but it may be from another address entirely.
考慮這是一項公共服務公告:詐騙者可以偽造電子郵件地址。 您的電子郵件程序可能會說一條消息來自某個電子郵件地址,但可能完全來自另一個地址。
Email protocols don’t verify addresses are legitimate — scammers, phishers, and other malicious individuals exploit this weakness in the system. You can examine a suspicious email’s headers to see if its address was forged.
電子郵件協議不會驗證地址是否合法-詐騙者,網絡釣魚者和其他惡意人員利用系統中的此漏洞。 您可以檢查可疑電子郵件的標題,以查看其地址是否為偽造。
電子郵件如何運作 (How Email Works)
Your email software displays who an email is from in the “From” field. However, no verification is actually performed – your email software has no way of knowing if an email is actually from who it says it’s from. Each email includes a “From” header, which can be forged – for example, any scammer could send you an email that appears to be from bill@microsoft.com. Your email client would tell you this is an email from Bill Gates, but it has no way of actually checking.
您的電子郵件軟件會在“發件人”字段中顯示電子郵件的發件人。 但是,實際上并沒有執行驗證–您的電子郵件軟件無法知道電子郵件實際上是來自其發件人。 每封電子郵件都包含一個“發件人”標頭,可以偽造該標頭-例如,任何詐騙者都可以向您發送一封電子郵件,該電子郵件似乎來自bill@microsoft.com。 您的電子郵件客戶端會告訴您這是來自比爾·蓋茨的電子郵件,但實際上無法檢查。
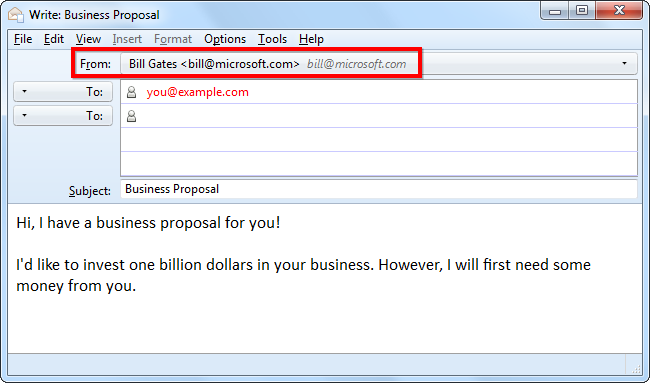
Emails with forged addresses may appear to be from your bank or another legitimate business. They’ll often ask you for sensitive information such as your credit card information or social security number, perhaps after clicking a link that leads to a phishing site designed to look like a legitimate website.
帶有偽造地址的電子郵件可能來自您的銀行或其他合法公司。 他們通常會要求您提供敏感信息,例如您的信用卡信息或社會安全號,也許是在單擊了指向仿冒網站的鏈接之后,該鏈接被設計為看起來像合法網站。
Think of an email’s “From” field as the digital equivalent of the return address printed on envelopes you receive in the mail. Generally, people put an accurate return address on mail. However, anyone can write anything they like in the return address field – the postal service doesn’t verify that a letter is actually from the return address printed on it.
將電子郵件的“發件人”字段想像成打印在郵件中收到的信封上的寄信人地址的數字形式。 通常,人們會在郵件中輸入準確的回信地址。 但是,任何人都可以在寄信人地址字段中寫任何喜歡的東西-郵政服務不會驗證信件實際上是從上面打印的寄信人地址發出的。
When SMTP (simple mail transfer protocol) was designed in the 1980s for use by academia and government agencies, verification of senders was not a concern.
當SMTP(簡單郵件傳輸協議)在1980年代設計用于學術界和政府機構時,發件人的驗證就不再是問題。
如何調查電子郵件的標題 (How to Investigate an Email’s Headers)
You can see more details about an email by digging into the email’s headers. This information is located in different areas in different email clients – it may be known as the email’s “source” or “headers.”
您可以通過查看電子郵件標題來查看有關電子郵件的更多詳細信息。 此信息位于不同電子郵件客戶端的不同區域中-可能稱為電子郵件的“源”或“標題”。
(Of course, it’s generally a good idea to disregard suspicious emails entirely – if you’re at all unsure about an email, it’s probably a scam.)
(當然,完全不考慮可疑電子郵件通常是個好主意-如果您完全不確定電子郵件,那可能是騙局。)
In Gmail, you can examine this information by clicking the arrow at the top right corner of an email and selecting Show original. This displays the email’s raw contents.
在Gmail中,您可以通過單擊電子郵件右上角的箭頭并選擇顯示原始信息來檢查此信息。 這將顯示電子郵件的原始內容。
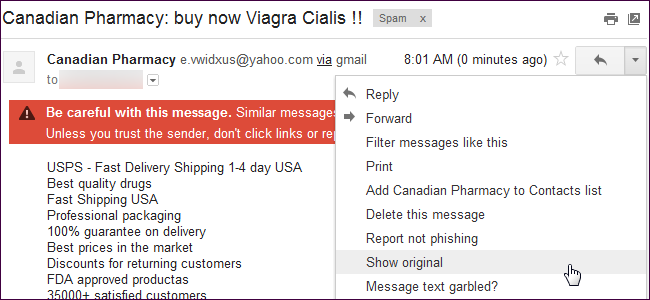
Below you’ll find the contents of an actual spam email with a forged email address. We’ll explain how to decode this information.
您將在下面找到帶有偽造電子郵件地址的實際垃圾郵件的內容。 我們將解釋如何解碼此信息。
Delivered-To: [MY EMAIL ADDRESS] Received: by 10.182.3.66 with SMTP id a2csp104490oba; Sat, 11 Aug 2012 15:32:15 -0700 (PDT) Received: by 10.14.212.72 with SMTP id x48mr8232338eeo.40.1344724334578; Sat, 11 Aug 2012 15:32:14 -0700 (PDT) Return-Path: <e.vwidxus@yahoo.com> Received: from 72-255-12-30.client.stsn.net (72-255-12-30.client.stsn.net. [72.255.12.30]) by mx.google.com with ESMTP id c41si1698069eem.38.2012.08.11.15.32.13; Sat, 11 Aug 2012 15:32:14 -0700 (PDT) Received-SPF: neutral (google.com: 72.255.12.30 is neither permitted nor denied by best guess record for domain of e.vwidxus@yahoo.com) client-ip=72.255.12.30; Authentication-Results: mx.google.com; spf=neutral (google.com: 72.255.12.30 is neither permitted nor denied by best guess record for domain of e.vwidxus@yahoo.com) smtp.mail=e.vwidxus@yahoo.com Received: by vwidxus.net id hnt67m0ce87b for <[MY EMAIL ADDRESS]>; Sun, 12 Aug 2012 10:01:06 -0500 (envelope-from <e.vwidxus@yahoo.com>) Received: from vwidxus.net by web.vwidxus.net with local (Mailing Server 4.69) id 34597139-886586-27/./PV3Xa/WiSKhnO+7kCTI+xNiKJsH/rC/ for root@vwidxus.net; Sun, 12 Aug 2012 10:01:06 –0500
傳遞至:[我的電子郵件地址]接收:10.182.3.66之前,SMTP ID為a2csp104490oba; 周六,2012年8月11日15:32:15 -0700(PDT)接收:SMTP ID為x48mr8232338eeo.40.1344724334578的10.14.212.72; 2012年8月11日,星期六,15:32:14 -0700(PDT)返回路徑:<e.vwidxus@yahoo.com>接收:來自72-255-12-30.client.stsn.net(72-255-12 -30.client.stsn.net。[72.255.12.30])由mx.google.com提供,ESMTP ID為c41si1698069eem.38.2012.08.11.15.32.13; 2012年8月11日,星期六,15:32:14 -0700(PDT)收到-SPF:中性(e.vwidxus@yahoo.com的域的最佳猜測記錄既不允許也不拒絕google.com:72.255.12.30)客戶- ip = 72.255.12.30; 身份驗證結果:mx.google.com; spf = neutral(對于e.vwidxus@yahoo.com域的最佳猜測記錄,既不允許也不拒絕google.com:72.255.12.30)smtp.mail=e.vwidxus@yahoo.com接收:通過vwidxus.net id hnt67m0ce87b用于<[我的電子郵件地址]>; Sun,2012年8月12日10:01:06 -0500(來自<e.vwidxus@yahoo.com>的信封)接收:來自web.vwidxus.net的vwidxus.net,具有本地(Mailing Server 4.69)ID 34597139-886586- 27 /./ PV3Xa / WiSKhnO + 7kCTI + xNiKJsH / rC / for root@vwidxus.net; 2012年8月12日,星期日:10:01:06 –0500
…
…
From: “Canadian Pharmacy” e.vwidxus@yahoo.com
來自:“加拿大藥房” e.vwidxus@yahoo.com
There are more headers, but these are the important ones – they appear at the top of the email’s raw text. To understand these headers, start from the bottom – these headers trace the email’s route from its sender to you. Each server that receives the email adds more headers to the top — the oldest headers from the servers where the email started out are located at the bottom.
頭更多,但這些頭很重要-它們出現在電子郵件原始文本的頂部。 要了解這些標頭,請從底部開始-這些標頭跟蹤電子郵件從發件人到您的路由。 每個接收電子郵件的服務器在頂部都添加了更多標頭-電子郵件開始的服務器中最舊的標頭位于底部。
The “From” header at the bottom claims the email is from an @yahoo.com address – this is just a piece of information included with the email; it could be anything at all. However, above it we can see that the email was first received by “vwidxus.net” ?(below) before being received by Google’s email servers (above). This is a red flag – we’d expect the see the lowest “Received:” header on the list as one of Yahoo!’s email servers.
底部的“發件人”標頭聲稱電子郵件來自@ yahoo.com地址-這只是電子郵件中包含的一部分信息; 可能什么都沒有。 但是,在其上方,我們可以看到該電子郵件首先由“ vwidxus.net”(如下)接收,然后再由Google的電子郵件服務器(上方)接收。 這是一個危險信號–我們希望將列表中最低的“ Received:”標頭視為Yahoo!的電子郵件服務器之一。
The IP addresses involved may also clue you in – if you receive a suspicious email from an American bank but the IP address it was received from resolves to Nigeria or Russia, that’s likely a forged email address.
如果您從一家美國銀行收到可疑的電子郵件,但是從解決者那里收到的該IP地址是發往尼日利亞或俄羅斯的IP地址,則所涉及的IP地址也可能為您提供線索,這很可能是偽造的電子郵件地址。
In this case, the spammers have access to the address “e.vwidxus@yahoo.com”, where they want to receive replies to their spam, but they’re forging the “From:” field anyway. Why? Likely because they can’t send massive amounts of spam via Yahoo!’s servers – they’d get noticed and be shut down. Instead, they’re sending spam from their own servers and forging its address.
在這種情況下,垃圾郵件發送者可以訪問“ e.vwidxus@yahoo.com”地址,希望在該地址接收對垃圾郵件的答復,但是無論如何,他們都在偽造“發件人:”字段。 為什么? 可能是因為它們無法通過Yahoo!的服務器發送大量垃圾郵件-它們會受到注意并被關閉。 相反,他們是從自己的服務器發送垃圾郵件并偽造其地址。
翻譯自: https://www.howtogeek.com/121532/htg-explains-how-scammers-forge-email-addresses-and-how-you-can-tell/








![[轉載]unix環境高級編程備忘:理解保存的設置用戶ID,設置用戶ID位,有效用戶ID,實際用戶ID...](http://pic.xiahunao.cn/[轉載]unix環境高級編程備忘:理解保存的設置用戶ID,設置用戶ID位,有效用戶ID,實際用戶ID...)



)






