In this lab, we’ll analyze the malware found in the file Lab06-04.exe.
Questions and Short Answers
What is the difference between the calls made from the main method in Labs 6-3 and 6-4?
A: The function at 0x401000 is the check Internet connection method, 0x401040 is the parse HTML method, 0x4012B5 is printf, and 0x401150 is the switch statement.
What new code construct has been added to main?
A: A for loop has been added to the main method.
What is the difference between this lab’s parse HTML function and those of the previous labs?
A: The function at 0x401040 now takes a parameter and calls sprintf with the format string Internet Explorer 7.50/pma%d. It builds a User-Agent for use during HTTP communication using the argument passed in.
How long will this program run? (Assume that it is connected to the Internet.)
A: This program will run for 1440 minutes (24 hours).
Are there any new network-based indicators for this malware?
A: Yes, a new User-Agent is used. It takes the form Internet Explorer 7.50/
pma%d, where %d is the number of minutes the program has been running.What is the purpose of this malware?
A: First, the program checks for an active Internet connection. If none is found, the program terminates. Otherwise, the program will use a unique User-Agent to attempt to download a web page containing a counter that tracks the number of minutes the program has been running. The web page downloaded contains an embedded HTML comment starting with
<!--. The next character is parsed from this comment and used in a switch statement to determine the action to take on the local system. These are hard-coded actions, including deleting a file, creating a directory, setting a registry run key, copying a file, and sleeping for 100 seconds. This program will run for 24 hours before terminating.
Detailed Analysis
We begin by performing basic static analysis on the binary. We see one new string of interest that was not in Lab 6-3, as follows:
Internet Explorer 7.50/pma%d
It looks like this program may use a dynamically generated User-Agent. Looking at the imports, we don’t see any Windows API functions that were not in Lab 6-3. When performing dynamic analysis, we also notice this User-Agent change when we see Internet Explorer 7.50/pma0.

注:可參考 Lab 6-2 相應部分。
Next, we perform more in-depth analysis with disassembly. We load the executable into IDA Pro and look at the main method, which is clearly structurally different from main in Lab 6-3, although many of the same functions are called. We see the functions 0x401000 (check Internet connection method), 0x401040 (parse HTML method), 0x4012B5 as printf, and 0x401150 (the switch statement). You should rename these functions as such in IDA Pro to make them easier to analyze.
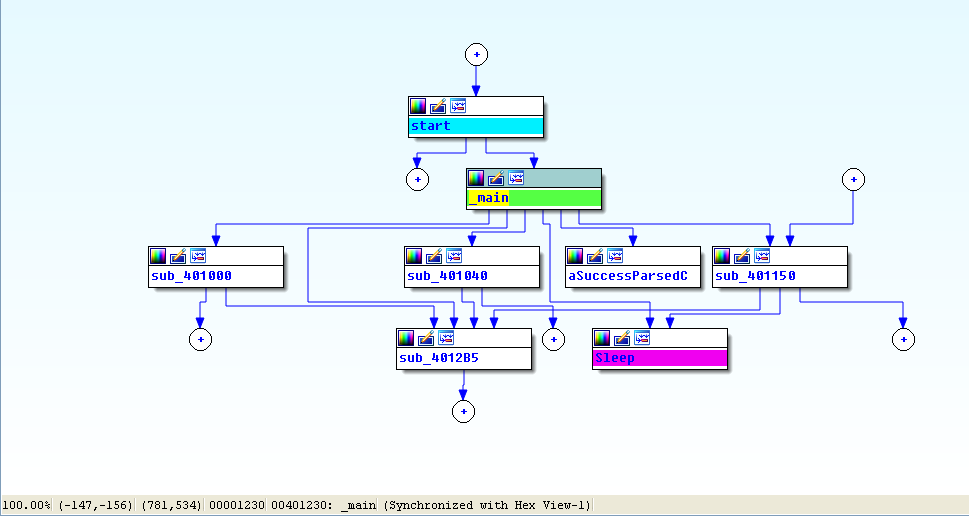
View -> Graphs -> Flow chart :
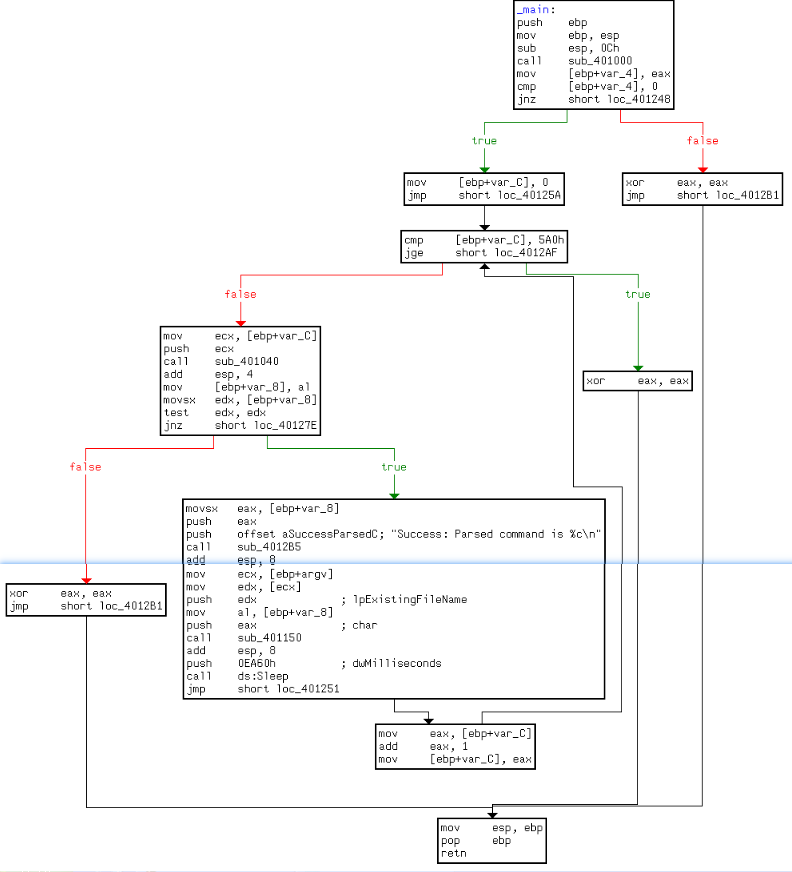
Looking at the main method in IDA Pro’s graphical view mode, we see an upward-facing arrow, which signifies looping. Listing 6-9L shows the loop structure.
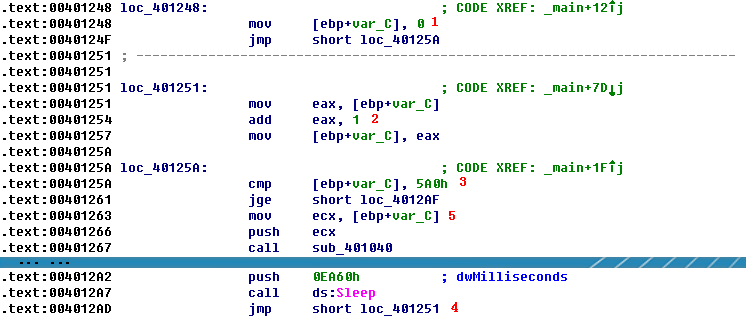
The variable var_C is the local variable used for the loop counter. The counter is initialized to 0 at \({\color{red} 1 }\), jumps past the incrementing at \({\color{red} 2 }\), performs a check at \({\color{red} 3 }\), and loops back to the incrementor when it gets to \({\color{red} 4 }\). The presence of these four code sections tells us that we are looking at a for loop code construct. If the var_C (counter) is greater than or equal to 0x5A0 (1440), the loop will end. Otherwise, the code starting at \({\color{red} 5 }\) is executed. The code pushes var_C on the stack before calling 0x401040, and then sleeps for 1 minute before looping up at \({\color{red}4}\) and incrementing the counter by one. Therefore, this process will repeat for 1440 minutes, which is equal to 24 hours.
In previous labs, 0x401040 did not take a parameter, so we need to investigate this further. Listing 6-10L shows the start of 0x401040.
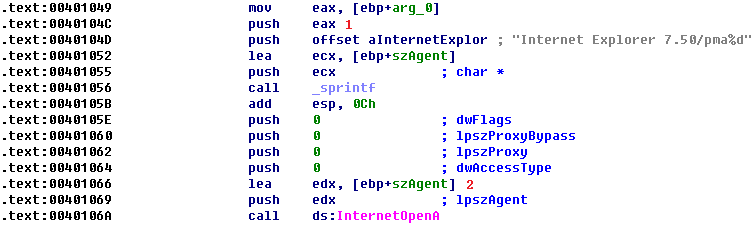
Here, arg_0 is the only parameter, and main is the only method calling 0x401040, so we conclude that arg_0 is always the counter (var_C) from the main method. Arg_0 is pushed on the stack at? \({\color{red}1}\), along with a format string and a destination. We also see that sprintf is called, which creates the string and stores it in the destination buffer, the local variable labeled szAgent. And szAgent is passed to InternetOpenA at \({\color{red}2}?\), which means that every time the counter increases, the User-Agent will change. This mechanism can be used by an attacker managing and monitoring a web server to track how long the malware has been running.
To summarize, the program checks for an active Internet connection using the if construct. If no connection is found, the program terminates. Otherwise, the program uses a unique User-Agent to attempt to download a web page containing a counter from a for loop construct. This counter contains the number of minutes the program has been running. The web page contains an embedded HTML comment and is read into an array construct of characters and compared to <!--. The next character is parsed from this comment and used in a switch construct to determine what action to take on the local system. These are hard-coded actions, including deleting a file, creating a directory, setting a registry run key, copying a file, and sleeping for 100 seconds. This program will run for 1440 minutes (24 hours) before terminating.
Preference
惡意代碼分析實戰 Lab 6-4 習題筆記







)











