一、拓撲圖
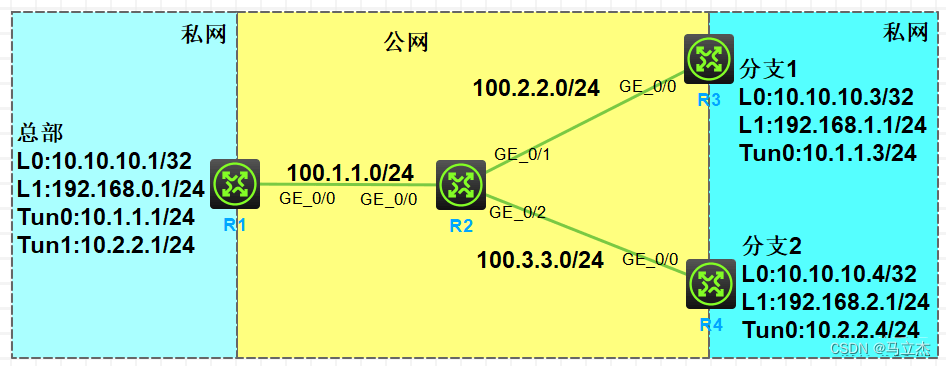
二、組網需求
- 某企業總部、分支1、分支2分別通過 R1,R3,R4 接入互聯網,配置默認路由連通公網
- 按照圖示配置 IP 地址,R1,R3,R4 分別配置 Loopback0 口匹配感興趣流,Loopback1 口模擬業務網段
- 總部擁有固定公網地址,在 R2 上配置 DHCP,對 R3 和 R4 動態分配 IP 地址,IP 地址網段如圖
- 總部、分支1、分支2配置 GRE over IPsec VPN 連通內網,要求總部使用模板來簡化配置
- 總部和分支之間配置 RIPv2 傳遞內網路由
注:設備IP地址為標志網段+設備號,如R1的G0/0端口的IP地址為1.1.1.1/24
三、配置步驟
1.配置各設備IP地址

Tunnel口的IP地址配置(以Tun0為例):
[R1]interface Tunnel 0 mode gre
[R1-Tunnel0]ip address 10.1.1.1 242.配置默認路由
(1)為R1配置默認路由,使全網可通
[R1]ip route-static 0.0.0.0 0 100.1.1.2(2)為R3配置默認路由,使全網可通
[R3]ip route-static 0.0.0.0 0 100.2.2.2(3)為R4配置默認路由,使全網可通
[R4]ip route-static 0.0.0.0 0 100.3.3.23.配置DHCP
在R2上配置DHCP,模擬運營商分配IP地址給R3、R4
(1)開啟 DHCP 服務
#
[R2]dhcp enable
[R2]interface GigabitEthernet 0/1
[R2-GigabitEthernet0/1]dhcp select server
[R2]interface GigabitEthernet 0/2
[R2-GigabitEthernet0/2]dhcp select server(2)配置 DHCP 地址池
#
[R2]dhcp server ip-pool 1
[R2-dhcp-pool-1]network 100.2.2.0 mask 255.255.255.0
[R2-dhcp-pool-1]gateway-list 100.2.2.2
#
[R2]dhcp server ip-pool 2
[R2-dhcp-pool-1]network 100.3.3.0 mask 255.255.255.0
[R2-dhcp-pool-1]gateway-list 100.3.3.2
#(3)在R3、R4上,開啟端口獲取DHCP地址
#
[R3]interface GigabitEthernet 0/0
[R3-GigabitEthernet0/0]ip address dhcp-alloc
#
[R4]interface GigabitEthernet 0/0
[R4-GigabitEthernet0/0]ip address dhcp-alloc
#檢查:在R2上查看,已分配IP地址。
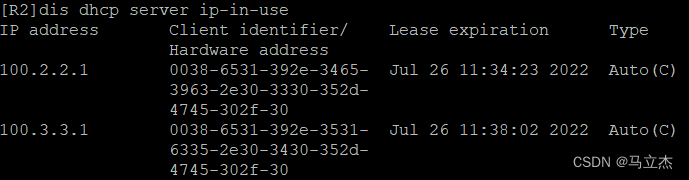
4.配置 GRE over IPsec VPN
4.1.在 R1 上配置 GRE over IPsec VPN
(1)在 R1 上配置GRE tunnel 口,指定源目IP為雙方 LoopBack 口。
[R1]interface Tunnel0
[R1-Tunnel0]source LoopBack 0
[R1-Tunnel0]destination 10.10.10.3
[R1]interface Tunnel1
[R1-Tunnel1]source LoopBack 0
[R1-Tunnel1]destination 10.10.10.4(2)在 R1 上配置 FQDN 名為 zb
[R1]ike identity fqdn zb(3)在 R1 上創建 IKE 提議,使用默認配置即可
[R1]ike proposal 1(4)在 R1 上創建 IKE 預共享密鑰
[R1]ike keychain fz
[R1-ike-keychain-fz]pre-shared-key hostname fz1 key simple 123
[R1-ike-keychain-fz]pre-shared-key hostname fz2 key simple 123(5)在 R1 上創建 IKE Profile
[R1]ike profile fz1
[R1-ike-profile-fz1]exchange-mode aggressive
[R1-ike-profile-fz1]match remote identity fqdn fz1
[R1-ike-profile-fz1]priority 1
[R1-ike-profile-fz1]keychain fz[R1]ike profile fz2
[R1-ike-profile-wh]exchange-mode aggressive
[R1-ike-profile-wh]match remote identity fqdn fz2
[R1-ike-profile-wh]proposal 1
[R1-ike-profile-wh]keychain fz(6)在 R1 上創建 IPsec 轉換集,對兩個分支可以使用同一個轉換集
[R1]ipsec transform-set fz
[R1-ipsec-transform-set-fz]esp authentication-algorithm sha1
[R1-ipsec-transform-set-fz]esp encryption-algorithm aes-cbc-128(7)在 R1 上分別創建對上海和武漢分支的 IPsec 策略模板
[R1]ipsec policy-template fz1 1
[R1-ipsec-policy-template-sh-1]transform-set fz
[R1-ipsec-policy-template-sh-1]ike-profile fz1
[R1]ipsec policy-template fz2 1
[R1-ipsec-policy-template-wh-1]transform-set fz
[R1-ipsec-policy-template-wh-1]ike-profile fz2 (8)在 R1 上創建 IPsec 策略,綁定兩個模板
[R1]ipsec policy fz 1 isakmp template fz1
[R1]ipsec policy fz 2 isakmp template fz2(9)在 R1 的公網接口上下發 IPsec 策略
[R1]interface GigabitEthernet 0/0
[R1-GigabitEthernet0/0]ipsec apply policy fz4.2.在 R3 上配置 GRE over IPsec VPN
(1)在 R3 上配置 GRE Tunnel 口
[R3]interface Tunnel0
[R3-Tunnel0]source LoopBack 0
[R3-Tunnel0]destination 10.10.10.1(2)配置 ACL
[R3]acl advanced 3000
[R3-acl-ipv4-adv-3000]rule permit ip source 10.10.10.3 0 destination 10.10.10.1 0(3)在 R3 上配置 FQDN 名為 fz1
[R3]ike identity fqdn fz1(4)在 R3 上創建 IKE 提議
[R3]ike proposal 1(5)在 R3 上創建 IKE 預共享密鑰,匹配對端公網地址
[R3]ike keychain zb
[R3-ike-keychain-zb]pre-shared-key address 100.1.1.1 key simple 123(6)在 R3 上創建 IKE Profile
[R3]ike profile zb
[R3-ike-profile-bj]exchange-mode aggressive
[R3-ike-profile-bj]match remote identity fqdn zb
[R3-ike-profile-bj]proposal 1
[R3-ike-profile-bj]keychain zb(7)在 R3 上創建 IPsec 轉換集
[R3]ipsec transform-set zb
[R3-ipsec-transform-set-fz]esp authentication-algorithm sha1
[R3-ipsec-transform-set-fz]esp encryption-algorithm aes-cbc-128(8)在 R3 上創建 IPsec 策略
[R3]ipsec policy zb 1 isakmp
[R3-ipsec-policy-isakmp-zb-1]security acl 3000
[R3-ipsec-policy-isakmp-zb-1]remote-address 100.1.1.1
[R3-ipsec-policy-isakmp-zb-1]ike-profile zb
[R3-ipsec-policy-isakmp-zb-1]transform-set zb(9)在 R3 的公網接口上下發 IPsec 策略
[R3]interface GigabitEthernet 0/0
[R3-GigabitEthernet0/0]ipsec apply policy zb4.3.在 R4 上配置 GRE over IPsec VPN
(1)在 R4 上配置 GRE Tunnel 口
[R4]interface Tunnel0
[R4-Tunnel0]source LoopBack 0
[R4-Tunnel0]destination 10.10.10.1(2)配置 ACL
[R4]acl advanced 3000
[R4-acl-ipv4-adv-3000]rule permit ip source 10.10.10.4 0 destination 10.10.10.1 0(3)在 R4 上配置 FQDN 名為 fz2
[R4]ike identity fqdn fz2(4)在 R4 上創建 IKE 提議
[R4]ike proposal 1(5)在 R4 上創建 IKE 預共享密鑰,匹配對端公網地址
[R4]ike keychain zb
[R4-ike-keychain-zb]pre-shared-key address 100.1.1.1 key simple 123(6)在 R4 上創建 IKE Profile
[R4]ike profile zb
[R4-ike-profile-bj]exchange-mode aggressive
[R4-ike-profile-bj]match remote identity fqdn zb
[R4-ike-profile-bj]proposal 1
[R4-ike-profile-bj]keychain zb(7)在 R4 上創建 IPsec 轉換集
[R4]ipsec transform-set zb
[R4-ipsec-transform-set-fz]esp authentication-algorithm sha1
[R4-ipsec-transform-set-fz]esp encryption-algorithm aes-cbc-128(8)在 R4 上創建 IPsec 策略
[R4]ipsec policy zb 1 isakmp
[R4-ipsec-policy-isakmp-zb-1]security acl 3000
[R4-ipsec-policy-isakmp-zb-1]remote-address 100.1.1.1
[R4-ipsec-policy-isakmp-zb-1]ike-profile zb
[R4-ipsec-policy-isakmp-zb-1]transform-set zb(9)在 R4 的公網接口上下發 IPsec 策略
[R4]interface GigabitEthernet 0/0
[R4-GigabitEthernet0/0]ipsec apply policy zb
5.配置 RIP
(1)在 R1,R3,R4 上分別配置 RIPv2,宣告 Tunnel 口網段和各自業務網段
[R1]rip
[R1-rip-1]version 2
[R1-rip-1]undo summary
[R1-rip-1]network 192.168.0.1 0.0.0.255
[R1-rip-1]network 10.1.1.0 0.0.0.255
[R1-rip-1]network 10.2.2.0 0.0.0.255[R3]rip
[R3-rip-1]version 2
[R3-rip-1]undo summary
[R3-rip-1]network 192.168.1.0 0.0.0.255
[R3-rip-1]network 10.1.1.0 0.0.0.255[R4]rip
[R4-rip-1]version 2
[R4-rip-1]undo summary
[R4-rip-1]network 192.168.2.0 0.0.0.255
[R4-rip-1]network 10.2.2.0 0.0.0.255(2)在 R1,R3,R4 上分別配置到達其他兩個站點環回口的靜態路由,下一跳指向公網
[R1]ip route-static 10.10.10.3 32 100.1.1.2
[R1]ip route-static 10.10.10.4 32 100.1.1.2
#[R3]ip route-static 10.10.10.1 32 100.2.2.2#
[R4]ip route-static 10.10.10.1 32 100.3.3.2四、總結
注意:ipsec配置完成后,需通過ping觸發sa。野蠻模式須用被動端ping主動端。
查看ike/ipse命令:display ike sa / display ipsec sa
)





)

的維度)
)
)

![51 單片機[2-1]:點亮一個LED](http://pic.xiahunao.cn/51 單片機[2-1]:點亮一個LED)
)


)


)