一、PRESENT算法介紹
PRESENT是一種超輕量級分組密碼算法,由Bogdanov等人在2007年提出,專門為資源受限環境如RFID標簽和傳感器網絡設計。該算法在硬件實現上僅需1570個門等效電路(GE),在保持較高安全性的同時實現了極小的硬件占用空間。PRESENT標準文檔下載地址為:PRESENT: An Ultra-Lightweight Block Cipher。
PRESENT采用SPN結構,分組長度為64位,支持80位和128位兩種密鑰長度。算法包含31輪加密操作,每輪由輪密鑰加、S盒替換和P盒置換三個步驟組成。其中S盒是一個4位輸入輸出的非線性變換,P盒則是一個64位的線性置換層。這種簡潔的結構使得PRESENT在硬件實現上非常高效。
安全性方面,PRESENT設計時充分考慮了差分分析和線性分析等攻擊方法。通過理論證明,任何5輪差分特征至少包含10個活躍S盒,25輪差分特征的概率上限為,線性分析則需約
個已知明文才能成功攻擊,這些安全指標完全滿足輕量級應用場景的需求。
二、C語言實現
我們提供的C代碼完整實現了PRESENT-80算法,包括加密、解密和密鑰擴展功能。實現中定義了幾個關鍵組件:
首先定義了算法核心的S盒和P盒置換表。S盒是一個16元素的查找表,實現非線性變換;P盒則定義了64位狀態的置換規則。代碼中同時包含了正向和反向的S盒/P盒,分別用于加密和解密過程。
present_permutation函數實現了通用的置換操作,根據傳入的置換規則表對輸入數據進行重排。這個函數被P盒置換(PSub)和逆P盒置換(InvPSub)復用,通過不同的置換規則表實現不同的置換效果。
密鑰擴展部分(present_key_expansion和keyUpdate)實現了80位主密鑰到32個輪密鑰的派生過程。每輪密鑰通過旋轉、S盒變換和輪計數器異或等操作生成,確保了密鑰材料的充分混淆。
加密過程(present_encrypt_block)遵循算法標準結構:31輪迭代處理,每輪包含輪密鑰加、S盒替換和P盒置換,最后再進行一次輪密鑰加作為后處理。解密過程(present_decrypt_block)則逆向執行這些操作。
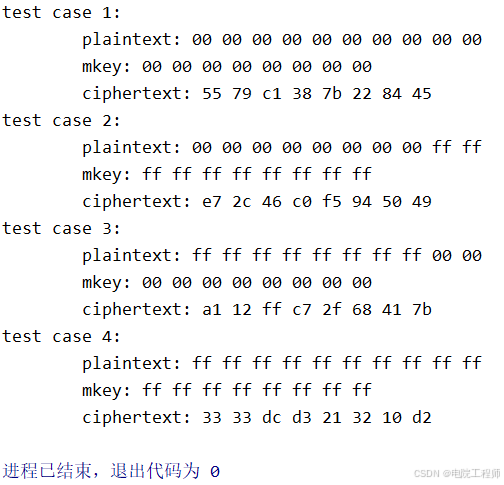
代碼中還包含了四個測試用例,驗證了實現與標準測試向量的正確性。這些測試用例來自于標準文檔,覆蓋了全零、全一的明文和密鑰組合,能夠有效驗證算法的基本功能。
#include<stdio.h>
#include<stdint.h>static const uint8_t present_sbox[16] = {0xC, 0x5, 0x6, 0xB, 0x9, 0x0, 0xA, 0xD, 0x3, 0xE, 0xF, 0x8, 0x4, 0x7, 0x1,0x2};
static const uint8_t present_inv_sbox[16] = {0x5, 0xE, 0xF, 0x8, 0xC, 0x1, 0x2, 0xD, 0xB, 0x4, 0x6, 0x3, 0x0, 0x7, 0x9,0xA};static const uint8_t present_pbox[64] = {0, 4, 8, 12, 16, 20, 24, 28,32, 36, 40, 44, 48, 52, 56, 60,1, 5, 9, 13, 17, 21, 25, 29,33, 37, 41, 45, 49, 53, 57, 61,2, 6, 10, 14, 18, 22, 26, 30,34, 38, 42, 46, 50, 54, 58, 62,3, 7, 11, 15, 19, 23, 27, 31,35, 39, 43, 47, 51, 55, 59, 63
};static const uint8_t present_inv_pbox[64] = {0, 16, 32, 48, 1, 17, 33, 49,2, 18, 34, 50, 3, 19, 35, 51,4, 20, 36, 52, 5, 21, 37, 53,6, 22, 38, 54, 7, 23, 39, 55,8, 24, 40, 56, 9, 25, 41, 57,10, 26, 42, 58, 11, 27, 43, 59,12, 28, 44, 60, 13, 29, 45, 61,14, 30, 46, 62, 15, 31, 47, 63
};void present_permutation(const uint8_t *src, uint8_t *res, const uint8_t *rule, uint8_t len) {uint8_t dest_pos, dest_bit;for (uint8_t i = 0; i < len; i++) {res[i] = 0;for (uint8_t j = 0; j < 8; j++) {dest_pos = rule[8 * i + j];dest_bit = (src[dest_pos >> 3] >> (7 - (dest_pos & 0x07))) & 0x01;res[i] = res[i] | (dest_bit << (7 - j));}}
}void addRoundKey(uint8_t *state, const uint8_t *ikey, uint8_t r) {for (uint8_t i = 0; i < 8; i++) {state[i] ^= ikey[8 * r + i];}
}void SubByte(uint8_t *state) {for (int i = 0; i < 8; i++) {uint8_t s0 = present_sbox[state[i] & 0xf];uint8_t s1 = present_sbox[state[i] >> 4];state[i] = s0 | s1 << 4;}
}void InvSubByte(uint8_t *state) {for (int i = 0; i < 8; i++) {uint8_t s0 = present_inv_sbox[state[i] & 0xf];uint8_t s1 = present_inv_sbox[state[i] >> 4];state[i] = s0 | s1 << 4;}
}void PSub(uint8_t *state) {uint8_t tmp[8] = {0};for (uint8_t i = 0; i < 8; i++) {tmp[i] = state[i];}present_permutation(tmp, state, present_pbox, 8);
}void InvPSub(uint8_t *state) {uint8_t tmp[8] = {0};for (uint8_t i = 0; i < 8; i++) {tmp[i] = state[i];}present_permutation(tmp, state, present_inv_pbox, 8);
}void keyUpdate(uint8_t *key, uint8_t rc) {uint8_t k[10] = {key[7] << 5 | key[8] >> 3, key[8] << 5 | key[9] >> 3, key[9] << 5 | key[0] >> 3, key[0] << 5 | key[1] >> 3,key[1] << 5 | key[2] >> 3,key[2] << 5 | key[3] >> 3, key[3] << 5 | key[4] >> 3, key[4] << 5 | key[5] >> 3, key[5] << 5 | key[6] >> 3,key[6] << 5 | key[7] >> 3};k[0] = (k[0] & 0xf) | (present_sbox[k[0] >> 4] << 4);rc = rc & 0x1f;k[7] ^= rc >> 1;k[8] ^= rc << 7;for (uint8_t i = 0; i < 10; i++) {key[i] = k[i];}
}void present_key_expansion(const uint8_t *mkey, uint8_t *ikey) {uint8_t mk[10];for (uint8_t i = 0; i < 10; i++) {mk[i] = mkey[i];ikey[i] = mkey[i];}for (uint8_t i = 1; i < 32; i++) {keyUpdate(mk, i);for (uint8_t j = 0; j < 8; j++) {ikey[8 * i + j] = mk[j];}}
}void present_encrypt_block(const uint8_t *plain, uint8_t *cipher, uint8_t *ikey) {uint8_t state[8];for (uint8_t i = 0; i < 8; i++) {state[i] = plain[i];}for (int r = 1; r < 32; r++) {addRoundKey(state, ikey, r - 1);SubByte(state);PSub(state);}addRoundKey(state, ikey, 31);for (uint8_t i = 0; i < 8; i++) {cipher[i] = state[i];}
}void present_decrypt_block(const uint8_t *cipher, uint8_t *plain, uint8_t *ikey) {uint8_t state[8];for (uint8_t i = 0; i < 4; i++) {state[i] = cipher[3 - i];state[i + 4] = cipher[7 - i];}for (int i = 31; i >= 1; i--) {addRoundKey(state, ikey, i);InvPSub(state);InvSubByte(state);}addRoundKey(state, ikey, 0);for (uint8_t i = 0; i < 4; i++) {plain[i] = state[3 - i];plain[i + 4] = state[7 - i];}
}void print_data(uint8_t *data, int data_len, const char *name) {printf("\t%s: ", name);for (int i = 0; i < data_len; i++) {printf("%02x ", data[i]);}printf("\n");
}void test_case1() {printf("test case 1:\n");uint8_t mkey[] = {0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00};uint8_t plain[] = {0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00};uint8_t ikey[256] = {0};uint8_t cipher[8] = {0};print_data(plain, 10, "plaintext");print_data(mkey, 8, "mkey");present_key_expansion(mkey, ikey);present_encrypt_block(plain, cipher, ikey);print_data(cipher, 8, "ciphertext");
}void test_case2() {printf("test case 2:\n");uint8_t mkey[] = {0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff};uint8_t plain[] = {0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00};uint8_t ikey[256] = {0};uint8_t cipher[8] = {0};print_data(plain, 10, "plaintext");print_data(mkey, 8, "mkey");present_key_expansion(mkey, ikey);present_encrypt_block(plain, cipher, ikey);print_data(cipher, 8, "ciphertext");
}void test_case3() {printf("test case 3:\n");uint8_t mkey[] = {0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00};uint8_t plain[] = {0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff};uint8_t ikey[256] = {0};uint8_t cipher[8] = {0};print_data(plain, 10, "plaintext");print_data(mkey, 8, "mkey");present_key_expansion(mkey, ikey);present_encrypt_block(plain, cipher, ikey);print_data(cipher, 8, "ciphertext");
}void test_case4() {printf("test case 4:\n");uint8_t mkey[] = {0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff};uint8_t plain[] = {0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff};uint8_t ikey[256] = {0};uint8_t cipher[8] = {0};print_data(plain, 10, "plaintext");print_data(mkey, 8, "mkey");present_key_expansion(mkey, ikey);present_encrypt_block(plain, cipher, ikey);print_data(cipher, 8, "ciphertext");
}int main() {test_case1();test_case2();test_case3();test_case4();return 0;
}?
三、總結
PRESENT算法通過精心設計的簡潔結構,在資源受限環境中實現了安全性與效率的良好平衡。其硬件友好的特性使其成為物聯網安全領域的理想選擇。提供的C語言實現完整展現了算法的工作流程,模塊化設計清晰,便于理解和移植。
這種輕量級密碼算法代表了密碼學在物聯網時代的發展方向,即在有限資源下提供足夠的安全保障。隨著物聯網設備的普及,類似PRESENT這樣的高效密碼算法將發揮越來越重要的作用。我們的代碼實現不僅可用于學術研究,也可應用于實際的嵌入式安全解決方案中。




》——有你在的地方才最美)

)


)








)
