目錄
FunZip
Magic_Keyboard
Number_is_the_key
RSA_KU
成語學習
鋼鐵俠在解密
工業互聯網模擬仿真數據分析
精裝四合一
時間刺客
有人讓我給你帶個話
FunZip
題目給了一個txt,內容如下

一眼丁真,base隱寫,使用工具即可得到flag
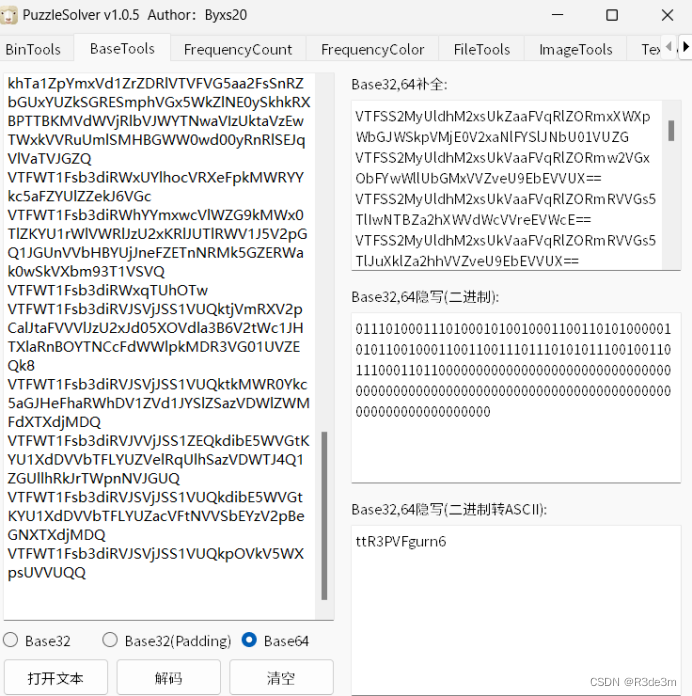
Flag:ISCC{ttR3PVFgurn6}
Magic_Keyboard
題?給了?段?頻,是敲鍵盤的聲?,需要知道敲的是什么鍵。
類似題:2021年pbctf有個題?叫 Ghost Writer ,跟這個題?類似,?上可以找到這個題?的wp
https://github.com/apoirrier/CTFs-writeups/blob/master/PBCTF2021/Misc/GhostWriter.md使?了GitHub上的?個項?acoustic_keylogger 。
它可以統計出哪?次按鍵是按的同?個鍵。使?該腳本跑出來以 abcdadadef 開頭的?串字符,這剛好對應 ISCC{ 的?六進制“495343437b”,最后兩個字符?定對應的是 } 的?六進制“7d”,其他的字符就需要反復的推敲。{}內部全都是?寫字?和_ ,所以最終還是很容易推出?張映射表的。注意{}內是正常的英文句子。
{"a":4,"b":9,"c":5,"d":3,"e":7,"f":"b","m":"d","g":6,"h":8,"i":"f","j":1,"k":2,"l":"c","n":"e"}
EXP:
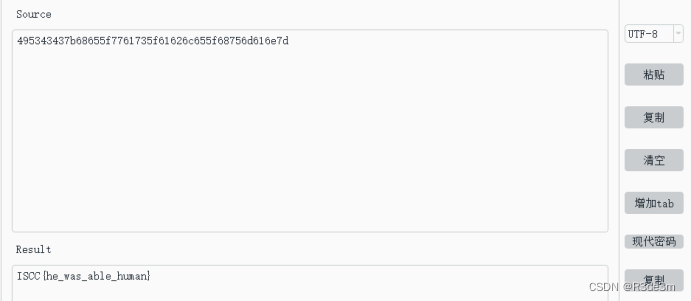
from sklearn.preprocessing import MinMaxScalerfrom librosa.feature import mfccimport numpy as npfrom scipy.io import wavfile as wavdef wav_read(filepath):sample_rate, data = wav.read(filepath)if type(data[0]) == np.ndarray:return data[:, 0]else:return datadef detect_keystrokes(sound_data, sample_rate=44100):threshold = 5000keystroke_duration = 0.3len_sample = int(sample_rate * keystroke_duration)keystrokes = []i = 0while i < len(sound_data):if abs(sound_data[i]) > threshold:a, b = i, i + len_sampleif b > len(sound_data):b = len(sound_data)while abs(sound_data[b]) > threshold and b > a:b -= 1keystroke = sound_data[a:b]trailing_zeros = np.array([0 for _ in range(len_sample - (b - a))])keystroke = np.concatenate((keystroke, trailing_zeros))keystrokes.append(keystroke)i = b - 1i += 1return np.array(keystrokes)def extract_features(keystroke, sr=44100, n_mfcc=16, n_fft=441, hop_len=110):spec = mfcc(y=keystroke.astype(float), sr=sr, n_mfcc=n_mfcc, n_fft=n_fft, hop_length=hop_len)return spec.flatten()data = wav_read("attachment-45.wav")keystrokes = detect_keystrokes(data)X = [extract_features(x) for x in keystrokes]X_norm = MinMaxScaler().fit_transform(X)letters = {}phrase = []current_letter = ord('a')for x in X_norm:if x[0] not in letters:letters[x[0]] = current_lettercurrent_letter += 1phrase.append(letters[x[0]])mappings = {}flag=("".join(mappings.get(char, char) for char in "".join([chr(x) for x in phrase])))print(flag)flag1=""dict1={"a":4,"b":9,"c":5,"d":3,"e":7,"f":"b","m":"d","g":6,"h":8,"i":"f","j":1,"k":2,"l":"c","n":"e"}for i in range(0,len(flag)):if flag[i] in dict1:flag1+=str(dict1[flag[i]])else:flag1+="_"print(flag1)運行后得到一串16進制字符
495343437b68655f7761735f61626c655f68756d616e7d
解密后得到flag:ISCC{he_was_able_human}
Number_is_the_key
仔細觀察后發現excel部分單元格被進行了加粗處理
將被加粗部分涂黑即可得到一個二維碼

手機掃碼后即可得到flag
ISCC{rKmjyi1HRnqd}
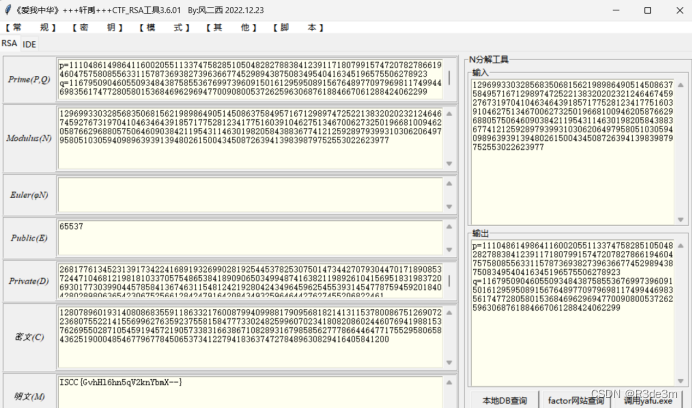
RSA_KU
Info:
n = 129699330328568350681562198986490514508637584957167129897472522138320202321246467459276731970410463464391857177528123417751603910462751346700627325019668100946205876629688057506460903842119543114630198205843883677412125928979399310306206497958051030594098963939139480261500434508726394139839879752553022623977e = 65537c = 128078960193140808683559118633217600879940998817909568182141311537800867512690722368075522141556996276359237558158477733024825996070234180820860244607694198815376269550287105459194572190573383166386710828931679858562777866446477175529580658436251900048546779677845065373412279418363747278489630829416405841200#(p-2)*(q-1) = 129699330328568350681562198986490514508637584957167129897472522138320202321246467459276731970410463464391857177528123417751603910462751346700627325019668067056973833292274532016607871906443481233958300928276492550916101187841666991944275728863657788124666879987399045804435273107746626297122522298113586003834#(p-1)*(q-2) = 129699330328568350681562198986490514508637584957167129897472522138320202321246467459276731970410463464391857177528123417751603910462751346700627325019668066482326285878341068180156082719320570801770055174426452966817548862938770659420487687194933539128855877517847711670959794869291907075654200433400668220458exp:(軒禹秒了)
成語學習
首先打開流量包,過濾http協議,發現上傳了一張圖片
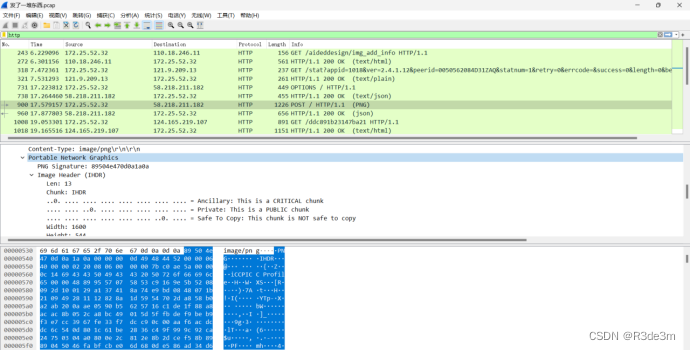
將圖片導出后修改寬高后得到key
key:57pmYyWt

然后用key作為密碼去解壓壓縮包,解壓出來的內容為something_copy103。后面加上.zip后綴,解壓后發現O7avZhikgKgbF這個文件夾下面有flag文件,內容如下:
《你信我啊》
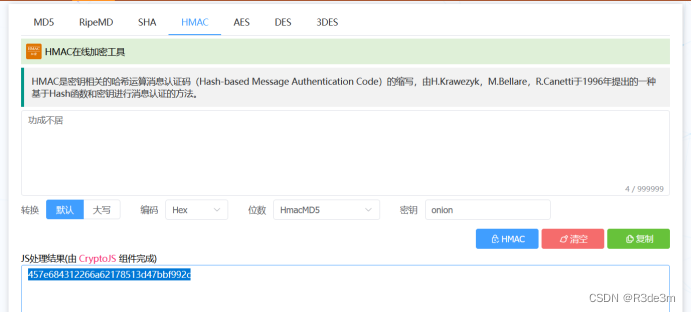
李維斯特指著墻上的“功成不居”邊享用onion邊和你說,你千萬不要拿我的食物去加密啊。
然后用在線網址解密https://www.mklab.cn/utils/hmac ,其中“功成不居”是密文,密鑰是onion,加密后得到flag為:457e684312266a62178513d47bbf992c
即:ISCC{457e684312266a62178513d47bbf992c}
鋼鐵俠在解密
題目給了一個圖片:ironman.bmp和一個txt,txt內容如下:
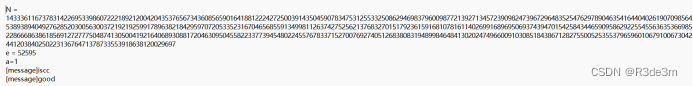
首先將圖片放到靜謐之眼里面進行解密,得到一個新的txt文件,內容為:
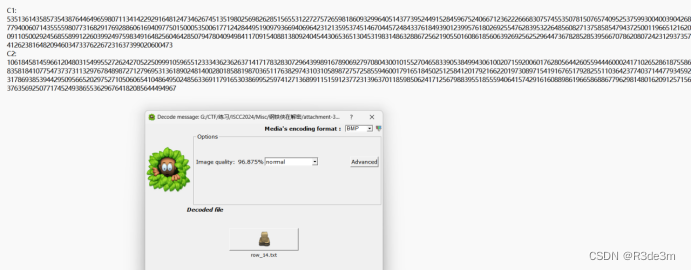
網上找個板子(half-gcd),sage腳本跑完就能得到flag
ISCC{huan_ran_bing_shi_263}
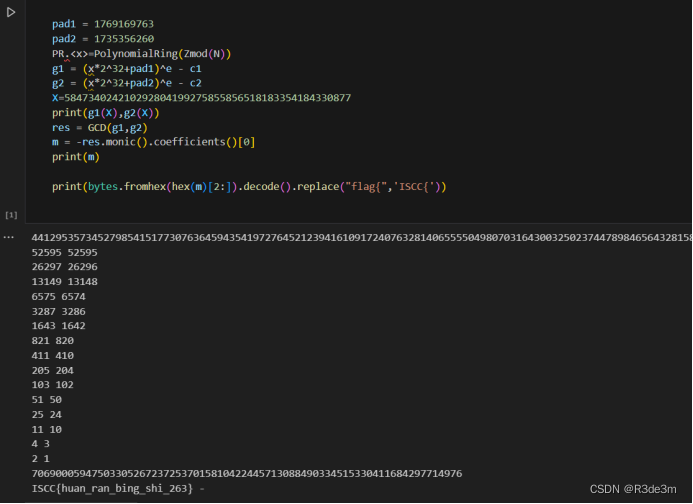
Exp:
#sagedef HGCD(a, b):if 2 * b.degree() <= a.degree() or a.degree() == 1:return 1, 0, 0, 1m = a.degree() // 2a_top, a_bot = a.quo_rem(x ^ m)b_top, b_bot = b.quo_rem(x ^ m)R00, R01, R10, R11 = HGCD(a_top, b_top)c = R00 * a + R01 * bd = R10 * a + R11 * bq, e = c.quo_rem(d)d_top, d_bot = d.quo_rem(x ^ (m // 2))e_top, e_bot = e.quo_rem(x ^ (m // 2))S00, S01, S10, S11 = HGCD(d_top, e_top)RET00 = S01 * R00 + (S00 - q * S01) * R10RET01 = S01 * R01 + (S00 - q * S01) * R11RET10 = S11 * R00 + (S10 - q * S11) * R10RET11 = S11 * R01 + (S10 - q * S11) * R11return RET00, RET01, RET10, RET11def GCD(a, b):print(a.degree(), b.degree())q, r = a.quo_rem(b)if r == 0:return bR00, R01, R10, R11 = HGCD(a, b)c = R00 * a + R01 * bd = R10 * a + R11 * bif d == 0:return c.monic()q, r = c.quo_rem(d)if r == 0:return dreturn GCD(d, r)c1= 5351361435857354387644649659807113414229291648124734626745135198025698262851565531227275726598186093299640514377395244915284596752406671236222666830757455350781507657409525375993004003904268779400607143555598077316829176928860616940977501500053500617712428449519097936694069642312135953745146704457248433761849390123995761802692554762839532264856082713758585479437250011966512162009110500292456855899122603992497598349164825604642850794780409498411709154088138092404544306536513045319831486328867256219055016086185606392692562529644736782852853956670786208072423129373574126238164820946034733762267231637399020600473c2= 10618458145966120480315499552726242705225099910596551233343623626371417178328307296439989167890692797080430010155270465833905384994306100207159200601762805644260559444600024171026528618755868358184107754737373113297678489872712796953136189024814002801858819870365117638297431031058987275725855946001791651845025125841201792166220197308971541916765179282551103642377403714477934592317869385394429509566520297527105060654104864950248563369117916530386995259741271368991151591237723139637011859850624171256798839551855594064157429161608898619665868867796298148016209125715637635692507717452493865536296764182085644494967N= 14333611673783142269533986072221892120042043537656734360856590164188122242725003914350459078347531255332508629469837960098772139271345723909824739672964835254762978904635416440402619070985645389389404927628520300563003721921925991789638218429597072053352316704656855913499811263742752562137683270151792361591681078161140269916896950693743947015425843446590958629225545563635366985228666863861856912727775048741305004192164068930881720463095045582233773945480224557678337152700769274051268380831948998464841302024749660091030851843867128275500525355379659601067910067304244120384025022313676471378733553918638120029697e = 52595pad1 = 1769169763pad2 = 1735356260PR.<x>=PolynomialRing(Zmod(N))g1 = (x*2^32+pad1)^e - c1g2 = (x*2^32+pad2)^e - c2X=584734024210292804199275855856518183354184330877print(g1(X),g2(X))res = GCD(g1,g2)m = -res.monic().coefficients()[0]print(m)print(bytes.fromhex(hex(m)[2:]).decode().replace("flag{",'ISCC{'))工業互聯網模擬仿真數據分析
步驟如下
第一問
在某些網絡會話中,數據包可能保持固定大小,請給出含有此確定性特征的會話IP地址和數據包字節大小值。
只有192.168.1.2à192.168.1.4的Length大小不變
結果:192.168.1.2,192.168.1.4,24
第二問
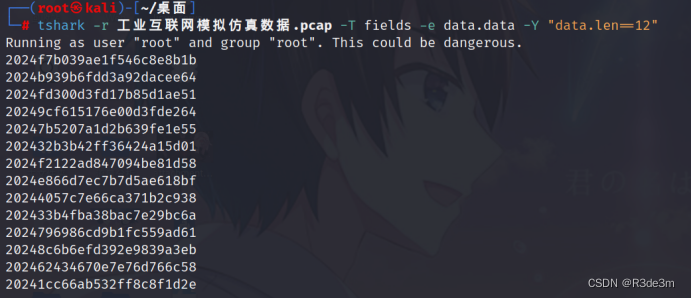
題目二:通信包數據某些字段可能為確定的,請給出確定字節數值。
tshark -r a.pcap -T fields -e data.data -Y "data.len==12" 2024f7b039ae1f546c8e8b1b 2024b939b6fdd3a92dacee64 2024fd300d3fd17b85d1ae51 20249cf615176e00d3fde264 20247b5207a1d2b639fe1e55 202432b3b42ff36424a15d01 2024f2122ad847094be81d58 2024e866d7ec7b7d5ae618bf 20244057c7e66ca371b2c938 202433b4fba38bac7e29bc6a 2024796986cd9b1fc559ad61 20248c6b6efd392e9839a3eb 202462434670e7e76d766c58 20241cc66ab532ff8c8f1d2e很明顯就是前面的2024
第三問
一些網絡通信業務在時間序列上有確定性規律,請提供涉及的IP地址及時間規律數值(小數點后兩位)
看文末的流量分組
第五組?-?192.168.1.3????192.168.1.5,?這一組的時間間隔固定
結果:192.168.1.3,192.168.1.5,0.06
第四問
一些網絡通信業務存在邏輯關聯性,請提供涉及的IP地址
看文末的流量分組,就能看出這三個IP是有業務關聯性的
192.168.1.3?-->?192.168.1.2?-->?192.168.1.6
結果:192.168.1.2,192.168.1.3,192.168.1.6
第五問
網絡數據包往往會添加數據完整性校驗值,請分析出數據校驗算法名稱及校驗值在數據包的起始位和結束位(倒數位)
五個字符的校驗算法,先假設是?CRC16?或者?CRC32?倒數位必為1
嘗試CRC16 CRC32并嘗試0-10為起始位
為CRC16,4,1時成功提交
所有的結果:
192.168.1.2,192.168.1.4,24
2024
192.168.1.3,192.168.1.5,0.06
192.168.1.2,192.168.1.3,192.168.1.6
CRC16,4,1
運行后得到flag
精裝四合一
拿到圖片后放入010editor發現每張圖片的最下面都有一堆多余數據,那就把IEND及之前的數據全部刪除,留下多余數據看看。
一堆亂碼,可能是讓我們進行異或,觀察了一下每段數據都有較多的FF,就全選,異或ff試試。(四張都異或)
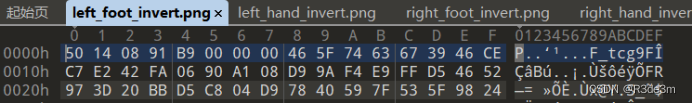
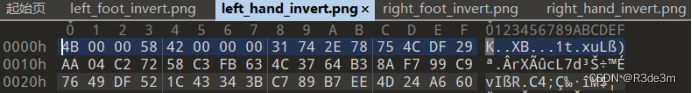
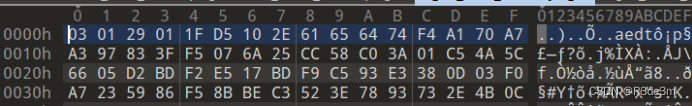
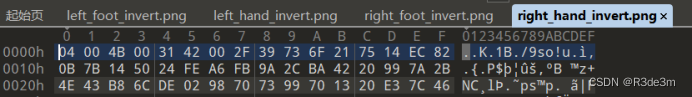
我們發現異或后的四個圖片的文件頭居然是50 4B 03 04,是我們熟悉的zip文件頭,寫腳本,將每段數據的字節按文件順序進行拼接。
Exp:
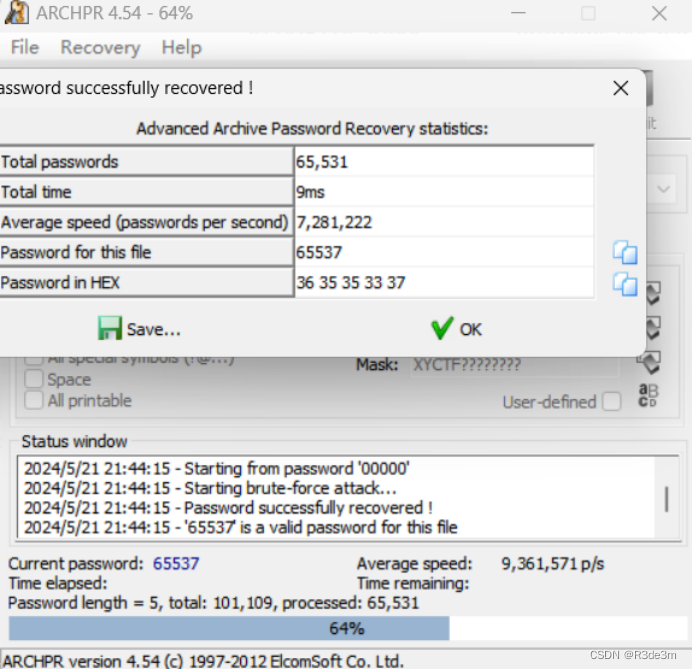
tp1 = open("./left_foot_invert.png", "rb")tp2 = open("./left_hand_invert.png", "rb")tp3 = open("./right_foot_invert.png", "rb")tp4 = open("./right_hand_invert.png", "rb")fp5 = open("key.zip", "wb")for i in range(3176):fp5.write(tp1.read(1))fp5.write(tp2.read(1))fp5.write(tp3.read(1))fp5.write(tp4.read(1))fp5.write(tp1.read(1))運行后得到key.zip,是加密的,爆破一下得到密鑰為65537(rsa中常用的e,后續可能會用到rsa解密)
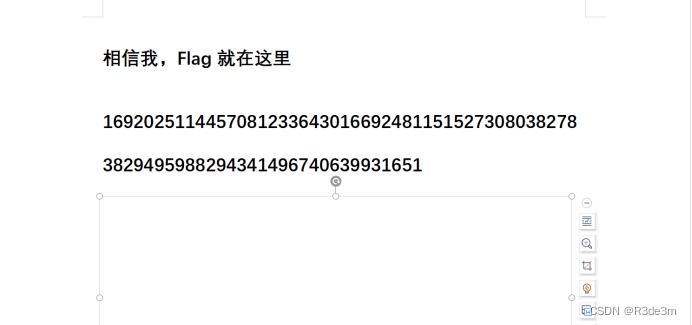
解壓后得到一個word文檔,里面有一個圖片,將圖片移開后,ctrl+a全選,換個主題即可得到一串數字:
16920251144570812336430166924811515273080382783829495988294341496740639931651
猜測其為rsa里面的n,factor分解后得到p,q
p=100882503720822822072470797230485840381
q=167722355418488286110758738271573756671
Exp:
import gmpy2from Crypto.Util.number import *n = 16920251144570812336430166924811515273080382783829495988294341496740639931651#分解n在線網站:http://www.factordb.com/,得到p,qp = 100882503720822822072470797230485840381q = 167722355418488286110758738271573756671e = 65537phi_n = (p - 1) * (q - 1)d = gmpy2.invert(e, phi_n)c = bytes_to_long(open("./true_flag.jpeg", "rb").read())m = pow(c, d, n)flag = long_to_bytes(m)print(flag)運行后即可得到flag:ISCC{NbJY499CcSrP198}
b'\x02\x18\t\xcb\x7f\x9dT\xcc\xe1\x00ISCC{NbJY499CcSrP198}'
時間刺客
題目給了流量包”給你也用不了.pcap”和一個加密的7z文件,首先我們先分析一下流量包發現很多鍵盤鼠標流量
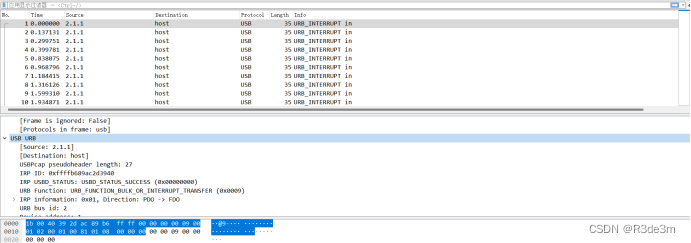
結合題目描述,可以初步判斷出為鍵盤流量
我們可以利用tshark提取出有效數據段
tshark -r 給你也用不了.pcap -T fields -e usb.capdata > usbdata.txt得到以下數據:
0000090000000000000000000000000000000f000000000000000000000000000000040000000000000000000000000000000a00000000000000000000000000200000000000000020002f0000000000200000000000000000000000000000000000130000000000000000000000000000001500000000000000000000000000000020000000000000000000000000000000220000000000000000000000000000002200000000000000000000000000200000000000000020002d000000000020000000000000000000000000000000000027000000000000000000000000000000110000000000000000000000000000001a0000000000000000000000000000000400000000000000000000000000000015000000000000000000000000000000070000000000000000000000000000001600000000000000000000000000200000000000000020002d0000000000200000000000000000000000000000000000040000000000000000000000000000001f00000000000000000000000000000009000000000000000000000000000000080000000000000000000000000000000800000000000000000000000000000023000000000000000000000000000000080000000000000000000000000000002700000000000000000000000000200000000000000020003000000000002000000000000000000000000000000001000000000000000100060000000000接下來使用腳本處理一下,得到
FLAGPR3550NWARDSA2FEE6E0
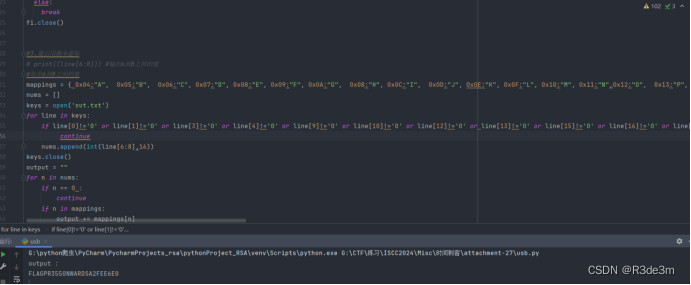
EXP:
#1.使用腳本刪除空行with open('usbdata.txt', 'r', encoding='utf-8') as f:lines = f.readlines()lines = filter(lambda x: x.strip(), lines)with open('usbdata.txt', 'w', encoding='utf-8') as f:f.writelines(lines)#2.將上面的文件用腳本分隔,加上冒號;f=open('usbdata.txt','r')fi=open('out.txt','w')while 1:a=f.readline().strip()if a:if len(a)==16:#鍵盤流量的話len為16鼠標為8out=''for i in range(0,len(a),2):if i+2 != len(a):out+=a[i]+a[i+1]+":"else:out+=a[i]+a[i+1]fi.write(out)fi.write('\n')else:breakfi.close()#3.最后用腳本提取# print((line[6:8])) #輸出6到8之間的值#取出6到8之間的值mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." }nums = []keys = open('out.txt')for line in keys:if line[0]!='0' or line[1]!='0' or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0':continuenums.append(int(line[6:8],16))keys.close()output = ""for n in nums:if n == 0 :continueif n in mappings:output += mappings[n]else:output += '[unknown]'print ('output :\n' + output)得到的并不是flag,用pr3550nwardsa2fee6e0去解密7z文件,成功得到一個新的rar文件,但是也是加密的,猜測密鑰為大寫的剛才的“flag”:PR3550NWARDSA2FEE6E0,得到一堆空文件,仔細觀察發現時間有問題
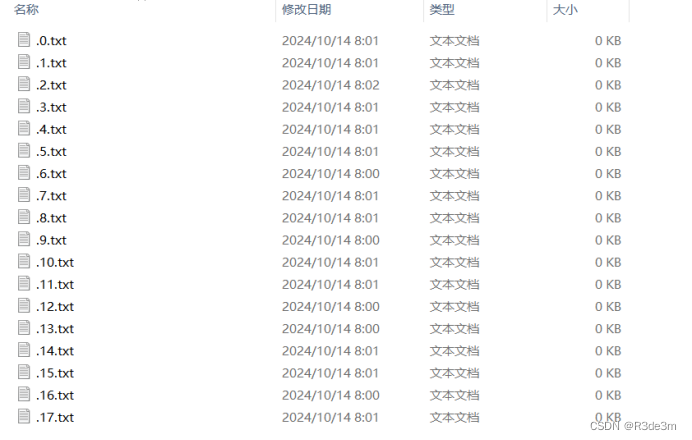
寫個時間戳腳本,可以得到flag

Exp:
import timeimport os# 設置包含文件的文件夾路徑folder_path = r"G:\CTF\練習\ISCC2024\Misc\時間刺客\attachment-27\20" # 使用原始字符串以避免轉義字符問題# 初始化一個空字符串以保存結果字符b = ""# 循環處理從0到17(包括)的文件for i in range(18):# 構造當前文件的完整路徑file_path = os.path.join(folder_path, ".%s.txt" % i)# 獲取文件的最后修改時間并轉換為time.struct_time對象mtime = time.localtime(os.path.getmtime(file_path))# 將time.struct_time轉換為格式化字符串,然后解析回time.struct_time以確保格式正確mtime = int(time.mktime(time.strptime(time.strftime('%Y-%m-%d %H:%M:%S', mtime), "%Y-%m-%d %H:%M:%S")))# 通過減去特定的基準值并轉換為字符來計算字符b += chr(mtime - 1728864000)# 打印結果print("ISCC{%s}" % b)有人讓我給你帶個話
題目給了一個圖片和一個文件
首先使用foremost對tony.png進行分離得到新的圖片,名稱為:lyra.png

百度搜索后在github上發現項目工具lyra(1.3.2)
在kali上首先安裝好bazel_5.3.2
(1)下載軟件包
curl -O https://mirrors.huaweicloud.com/bazel/5.3.2/bazel_5.3.2-linux-x86_64.deb
(2)安裝軟件包
sudo dpkg -i bazel_5.3.2-linux-x86_64.deb
(3)檢查是否安裝成功(查看版本)
bazel --version
搭建好環境后將另外一個未命名文件修改后綴名為.lyra,這里我改名為key.lyra
運行得到一段音頻
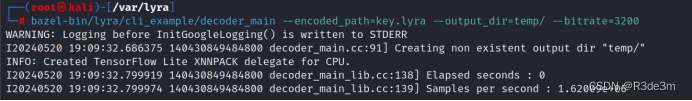
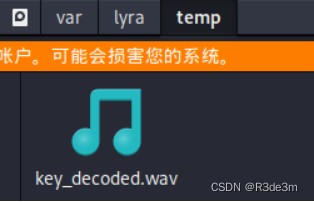
使用在線轉換工具語音轉文字|語音識別-在線錄音轉文字-錄音轉文字助手?將音頻轉化為文本
得到一串關于核心價值觀的字符
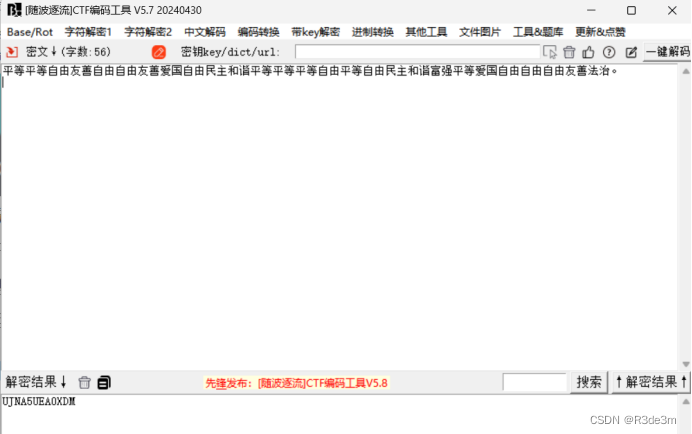
平等平等自由友善自由自由友善愛國自由民主和諧平等平等平等自由平等自由民主和諧富強平等愛國自由自由自由友善法治。

解密后得到flag
ISCC{UJNA5UEA0XDM}
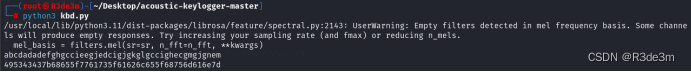



















 葉子游戲新聞)