des算法密碼多長
This is a DES that was susceptible to attacks due to tremendous advances in computer hardware in cryptography. Hence, it was a very complex or competent algorithm it would be feasible to reuse DES rather than writing an of cryptography.
由于加密技術中計算機硬件的巨大進步,這是一種易于受到攻擊的DES 。 因此,這是一個非常復雜或稱職的算法,重用DES而不是編寫加密算法是可行的。
Required to this variation of DES were introduced known as multiple DES which was as follows as Shown:
引入這種DES變體所需的稱為多重DES ,如下所示:
1)雙DES (1) Double DES)
Mainly, Double DES is simple as it does that normal DES does. Double DES uses twp keys to say K1 and K2 in this algorithm. It first performs DES on the original plain text using K! to get the encrypted text in cryptography. Here, it again performs DES on the encrypted text but this time with the other key K2 in this algorithm.
主要是, Double DES很簡單,就像普通DES一樣。 在此算法中,雙DES使用twp鍵表示K1和K2。 它首先使用K對原始純文本執行DES! 以加密方式獲取加密的文本。 在這里,它再次對加密的文本執行DES,但是這次使用該算法中的另一個密鑰K2。
Firstly, the final output is the encryption of encrypted text with the original plain text encrypted twice with two different keys shown in the structure as given below:
首先,最終輸出是加密的文本的加密,原始的純文本用兩個不同的密鑰加密了兩次,結構如下所示:
While the doubly encrypted ciphertext block is first decrypted using the key K2 to produce singly encrypted ciphertext by plaintext or original text. Hence, this ciphertext block is then decrypted using the key K1 to obtain the original plain text block in cryptography.
首先使用密鑰K2對雙重加密的密文塊進行解密,以通過明文或原始文本生成單一加密的密文。 因此,然后使用密鑰K1對該密文塊進行解密以獲得密碼術中的原始明文塊。
Mainly, the cryptanalysis for the basic version of DES requires a search of 256 thus the assumption is Double DES require 2128 keys which is not true for the message.
主要是,對DES基本版本的密碼分析需要搜索256,因此假設Double DES需要2128個密鑰,這對于消息而言是不正確的。
Here, a Meet-in-the-middle attack is the drawback of double DES in this. Mainly, this attack involves encryption from one end, decryption from the other and matching the results in the middle hence the name in the message.
在此,中間相遇攻擊是雙重DES的缺點。 主要是,這種攻擊涉及從一端進行加密,從另一端進行解密以及在中間匹配結果,從而在消息中使用名稱。
Therefore, the simplest form of multiple encryptions has two encryption stages and two keys in this. Here, given a plaintext P and two encryption keys K1 and K2, ciphertext C is created as: C = E(K2, E(K1, P))
因此,多重加密的最簡單形式具有兩個加密階段和兩個密鑰。 在此,給定明文P和兩個加密密鑰K1和K2 ,將密文C創建為: C = E( K2 ,E( K1 ,P))
Then, Decryption requires that the keys be applied in reverse order as: P = D(K1, D(K2, C))
然后,解密要求以相反的順序應用密鑰,例如: P = D( K1 ,D( K2 ,C))
Now, For DES, this scheme involves a key length of 56 * 2 = 112 bits, resulting in a dramatic increase in cryptographic strength in this. Further, but we need to examine the algorithm more closely for this.
現在,對于DES,此方案涉及56 * 2 = 112位的密鑰長度,從而導致加密強度顯著提高。 此外,但是我們需要對此進行更仔細的研究。
2)三重DES (2) Triple DES)
Here, to improve the security of DES to a higher level triple DES was proposed in this. While this uses three stages on DES for encryption and decryption in cryptography.
在此,為了提高DES的安全性,提出了三重DES。 雖然這在DES上使用三個階段來進行加密中的加密和解密。
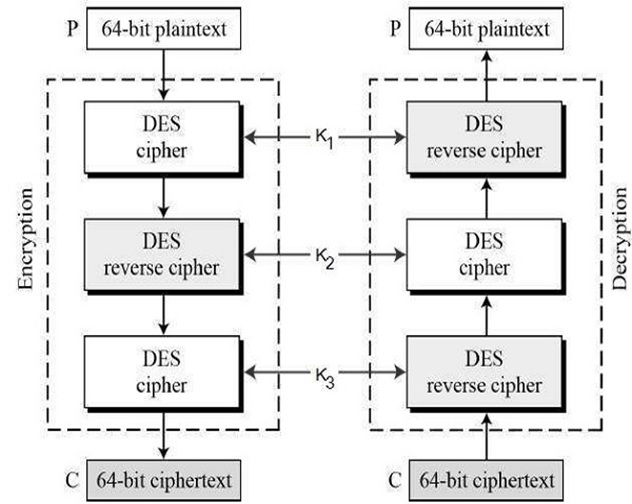
There basically of two versions of triple-DES are as given:
基本上有兩種版本的三重DES :
i. Triple DES with Two Keys
一世。 兩鍵三重DES
While in triple DES with two keys there are only two keys K1 used by the first and third stages and K2 used in the second stage in this. Basically, first, the plain text is encrypted with key K1 then the output of step one is decrypted with K2 and final the output second step is encrypted again with key K1 in cryptography.
在具有兩個密鑰的三重DES中,第一級和第三級僅使用兩個密鑰K1 ,第二級中僅使用兩個密鑰K2 。 基本上,首先,用密鑰K1加密純文本,然后用K2解密步驟1的輸出,最后再用密鑰K1再次加密輸出的第二步。
It is also called encrypt decrypt encrypt (ECE) mode in cryptography. Hence, Triple DES with two keys is not susceptible to the meet-in-the-middle attack in cryptography.
在密碼學中,它也稱為加密解密解密(ECE)模式。 因此,具有兩個密鑰的三重DES不會受到密碼學中的中間相遇攻擊。
ii. Triple DES with Three Keys
ii。 三鍵三鍵DES
It basically had the idea of Triple-DES with three keys:
它基本上具有使用三個密鑰的Triple-DES的想法:
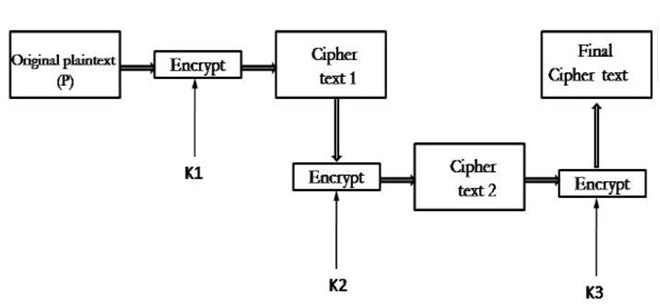
While the plain text block P is first encrypted with a key K1 then encrypts with a second key K2 and finally with a third key K3 where K1, K2, and K3 are all different from each other in this algorithm. This is Decryption is done in reverse order in this way. Therefore, this algorithm is mostly used in PGP and S/MIME in cryptography.
雖然首先使用密鑰K1加密純文本塊P ,然后使用第二密鑰K2加密,最后使用第三密鑰K3加密,其中該算法中的K1 , K2和K3都互不相同。 這就是解密以這種方式以相反的順序完成。 因此,此算法主要用于密碼學中的PGP和S / MIME。
Therefore, the DES cipher's key size of multiple of 56 bits of the message was generally enough when that algorithm was designed but the availability of increasing computational power made brute force attacks feasible in this algorithm. Thus, the Triple-DES provides a relatively simple method of increasing the key size of DES to secure against such attacks like that, without the need to design a completely new block cipher algorithm by this technique in cryptography.
因此,當設計該算法時,消息的56位的DES密碼的密鑰大小通常就足夠了,但是計算能力的提高使暴力攻擊在該算法中可行。 因此,Triple-DES提供了一種相對簡單的方法來增加DES的密鑰大小,以防止類似的攻擊,而無需通過這種技術在密碼學中設計一種全新的分組密碼算法。
MEET-IN-THE-MIDDLE ATTACK
遇見中間攻擊
Therefore, the use of double DES results in a mapping that is not equivalent to a single DES encryption in cryptography. Hence, but there is a way to attack this scheme, one that does not depend on any particular property of DES but that will work against any block encryption cipher in cryptography.
因此,使用雙DES會導致映射不等同于密碼學中的單個DES加密。 因此,但是有一種方法可以攻擊這種方案,該方案不依賴于DES的任何特定屬性,但是可以與密碼學中的任何塊加密密碼一起工作。
Therefore, the algorithm known as a meet-in-the-middle attack was first described in [DIFF77]. It is based on the observation that we can say if we have it
因此,在[DIFF77]中首先描述了稱為中間相遇攻擊的算法。 基于觀察,我們可以說是否擁有

Here, it has given a known pair, (P, C), the attack proceeds as follows as see. Firstly, encrypt P for all 256 possible values of K1 in this. While storing these results in a table and then sort the table by the values of X. Next, decrypt C using all 256 possible values of K2 in cryptography. Therefore, as each decryption is produced, check the result against the table for a match by this. Either if a match occurs, then test the two resulting keys against a new known-plaintext–ciphertext pair in cryptography. Hence, if the two keys produce the correct ciphertext, accept them as the correct keys in this algorithm.
在這里,它給出了一個已知的對(P,C) ,攻擊如下所示進行。 首先,在此為K1的所有256個可能值加密P。 將這些結果存儲在表中后,再按X的值對表進行排序。 接下來,使用密碼學中K2的所有256個可能值解密C。 因此,隨著每次解密的進行,以此將結果對照表進行核對。 如果發生匹配,則針對密碼學中新的已知明文-密文對測試兩個結果密鑰。 因此,如果兩個密鑰產生正確的密文,則在此算法中將它們接受為正確的密鑰。
For Example, for any given plaintext or original text P, 264 possible ciphertext values could be produced by double DES in this. This was Double DES uses, in effect, a 112-bit key, so that there are 2112 possible keys apply to messages. Therefore, on mean, for a given plaintext or original text P, the number of different 112-bit keys that will produce a given ciphertext as C is given: 2112/264 = 248
例如,對于任何給定的明文或原始文本P ,在此可以通過雙DES產生264個可能的密文值。 實際上,這是Double DES使用的112位密鑰,因此有2112種可能的密鑰適用于消息。 因此,平均而言,對于給定的純文本或原始文本P,給出將產生給定密文作為C的不同112位密鑰的數目: 2112/264 = 248
While, the foregoing procedure will produce about 248 false alarms on the first (P, C) pair in this. Therefore, a similar argument indicates that with an additional 64 bits of known plaintext and ciphertext, the false alarm rate is reduced to 248 - 64 = 2 - 16 in mathematics. While putting another way, if the meet-in-the-middle attack is performed on two blocks of known plaintext–ciphertext, the probability that the correct keys are determined is 1 - 2 - 16 in this way. Thus, the result is that a known-plaintext attack will succeed against double DES, which has a key size of 112 bits, with an effort on the order of 256, which is not much more than the 255 required for single DES in cryptography.
同時,上述過程將在此第一對(P,C)上產生約248個錯誤警報。 因此,類似的論點表明,在已知的明文和密文有另外的64位的情況下,錯誤警報率在數學上降低為248-64 = 2-16。 換句話說,如果對已知的明文-密文的兩個塊執行中間相遇攻擊,則以這種方式確定正確密鑰的可能性為1-2-16。 因此,結果是,已知的明文攻擊將成功抵御密鑰大小為112位的雙DES,而付出的努力約為256,這不超過密碼術中單個DES所需的255。
Image source: https://www.tutorialspoint.com/cryptography/triple_des.htm
圖片來源: https : //www.tutorialspoint.com/cryptography/triple_des.htm
翻譯自: https://www.includehelp.com/cryptography/multiple-des.aspx
des算法密碼多長



函數)















