第十單元
selinux 的管理
一 顯示及更改 SELINUX 模式
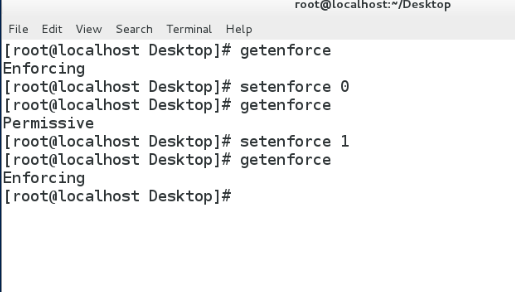
??getenforce ????###顯示selinux模式
??setenforce 0|1 ??????????????##0指permissive警告,1 表示 enforcing強制###
??
??vim ????/etc/sysconfig/selinux ??????###修改selinux開機狀態###
??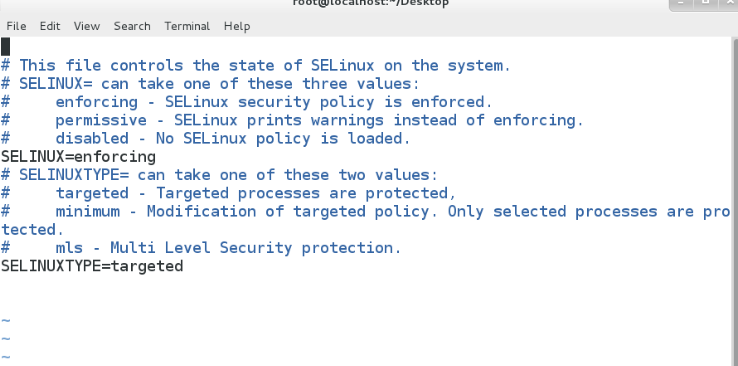
??注:disable表示關閉,enforcing表示強制,permissive表示警告,disable狀態切換到permissive狀態或則enforcing狀態要重啟系統
?
測試:將/mnt下的文件westos用mv移動到/var/ftp/pub目錄下,用lftp登入,查看當selinux為enforcing時,不能看到westos文件,當selinux為permissive時,能看到
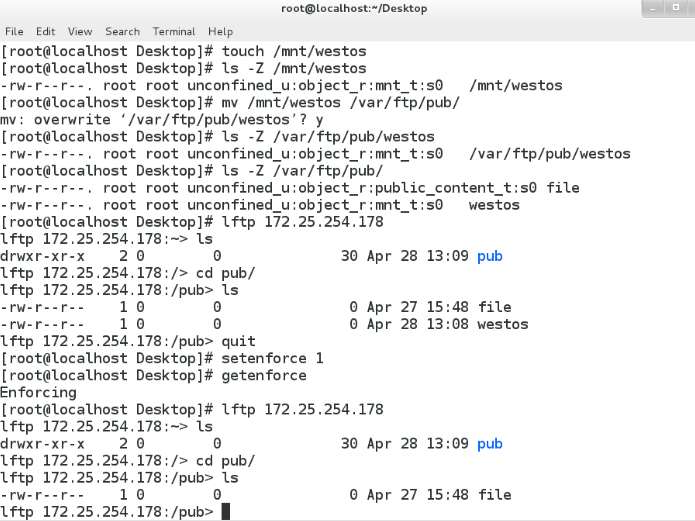
二 ?顯示 SELinux 文件上下文
1 將父目錄的上下文指定給新創建的文件。這對 vimcp 和 touch 等命令其作用 , 但是 , 如果文件是在其他位置創建的并且保留了權限 ( 與 mv 或 cp -a 一樣 ) 則還將保留 SELinux 上下文
2 顯示上下文
?ps ????axZ
?ps ???-ZC
?ls ????-Z
?
三 修改selinux安全上下文
chcon -t ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ??####一次性定制安全上下文 ??
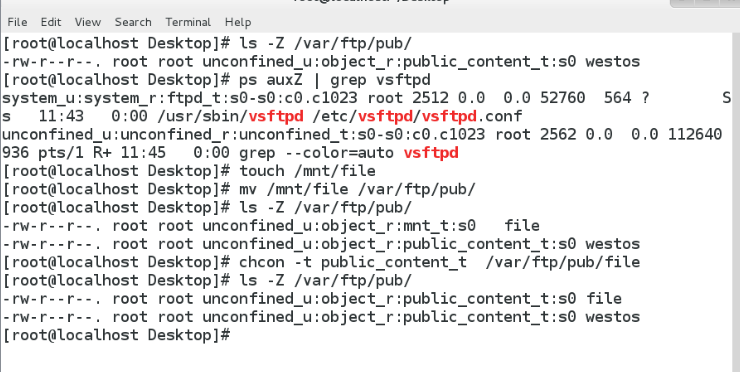
semanage ????????fcontext ???????####永久更改文件的上下文####\
測試:將selinux的模式改成enforcing,將匿名用戶家目錄改成/westos,用lftp登入,查看是否能看到/westos下的文件,發現無法看到,因為安全上下文不同,用semanage ????????fcontext更改安全上下文。
?
semanage fcontext -l | grep westos ??###查看內核上是否有指定文件的安全上下文###
?
semanage fcontext -a -t public_content_t '/westos(/.*)?'####-a指添加,-t指安全上下文的類型(/.*)?是格式,因為*和?有特殊意義,所以加上‘’轉義###
?
restorecon ???-RvvF ?????/westos/ ??????###刷新/westos###
?
?
過程如下:
?
[root@localhost Desktop]# ls /westos/
westosfile1 ??westosfile2 ?westosfile4 ?westosfile6 ?westosfile8
westosfile10 ?westosfile3 ?westosfile5 ?westosfile7 ?westosfile9
[root@localhost Desktop]# vim /etc/vsftpd/vsftpd.conf ??###將匿名用戶家目錄改成/westos
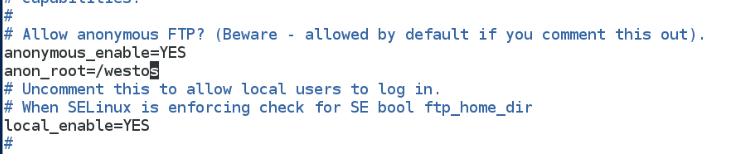
[root@localhost Desktop]# systemctl restart vsftpd.service
[root@localhost Desktop]# lftp 172.25.254.212
lftp 172.25.254.212:~> ls ???????????????????###測試發現看不到westos下的文件####
lftp 172.25.254.212:/> quit ?????????
[root@localhost Desktop]# ps auxZ | grep vsftpd ????###查看vsftp的進程信息,顯示安全上下文###
system_u:system_r:ftpd_t:s0-s0:c0.c1023 root 2426 0.0 ?0.0 52756 ?560 ? ???????Ss ??21:29 ??0:00 /usr/sbin/vsftpd /etc/vsftpd/vsftpd.conf
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 root 2469 0.0 ?0.0 112640 936 pts/0 R+ 21:30 ??0:00 grep --color=auto vsftpd
[root@localhost Desktop]# ls -Zd /var/ftp/ ????###ftpd_t的安全上下文可以訪問public_content_t的安全上下文###
drwxr-xr-x. root root system_u:object_r:public_content_t:s0 /var/ftp/
[root@localhost Desktop]# ls -Zd /westos/ ?###查看/westos的安全上下文###
drwxr-xr-x. root root system_u:object_r:default_t:s0 ??/westos/
[root@localhost Desktop]# semanage fcontext -l | grep westos ??###查看內核上是否有指定文件的安全上下文###
[root@localhost Desktop]# semanage fcontext -l | grep var/ftp ?###查看var/ftp在內核上的安全上下文###
/var/ftp(/.*)? ????????????????????????????????????all files ?????????system_u:object_r:public_content_t:s0
/var/ftp/bin(/.*)? ????????????????????????????????all files ?????????system_u:object_r:bin_t:s0
/var/ftp/etc(/.*)? ????????????????????????????????all files ?????????system_u:object_r:etc_t:s0
/var/ftp/lib(/.*)? ????????????????????????????????all files ?????????system_u:object_r:lib_t:s0
/var/ftp/lib/ld[^/]*\.so(\.[^/]*)* ????????????????regular file ??????system_u:object_r:ld_so_t:s0
?
[root@localhost Desktop]# semanage fcontext -a -t public_content_t '/westos(/.*)?'####-a指添加,-t指安全上下文的類型(/.*)?###
[root@localhost Desktop]# semanage fcontext -l | grep westos
/westos(/.*)? ?????????????????????????????????????all files ?????????system_u:object_r:public_content_t:s0 ???????????###all files指目錄和目錄下的文件,包括新建立的文件###
[root@localhost Desktop]# ls -Zd /westos/
drwxr-xr-x. root root system_u:object_r:default_t:s0 ??/westos/
[root@localhost Desktop]# restorecon -RvvF /westos/ ??###刷新/westos###
restorecon reset /westos context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile1 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile2 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile3 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile4 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile5 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile6 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile7 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile8 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile9 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
restorecon reset /westos/westosfile10 context system_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
[root@localhost Desktop]# lftp 172.25.254.212 ??###測試能否能看到###
lftp 172.25.254.212:~> ls
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile1
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile10
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile2
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile3
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile4
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile5
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile6
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile7
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile8
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:43 westosfile9
lftp 172.25.254.212:/> quit
[root@localhost Desktop]# touch /westos/westosfile11
[root@localhost Desktop]# lftp 172.25.254.100
lftp 172.25.254.100:~> ls
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile1
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile10
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 29 01:27 westosfile11
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile2
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile3
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile4
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile5
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile6
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile7
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile8
-rw-r--r-- ???1 0 ???????0 ??????????????0 Apr 23 05:30 westosfile9
lftp 172.25.254.100:/>
?
?
四 setsebool
?
1 定義:SELinux 布爾值是更改 SELinux 策略行為的開關。是可以啟用或禁用的規則。
?
selinux為了安全在默認情況下有些動作是不允許執行的,例如默認情況下不允許寫權限,因為可能會導致一些病毒***的可執行文件上傳,這些規則可通過getsebool看到,可使用 SELinux 布爾值來調整策略 , 以有選擇地進行調整。setsebool -P 修改 SELinux 策略 , -P指永久保留修改
例:默認情況下,lftp允許本地用戶上傳文件,當是selinux卻不允許上傳,因此上傳不了,用setsebool修改bool值。
?
getsebool ???-a ??| ??grep ???ftp ?????###查看ftp的布爾值###
setsebool ??????-P ????ftp_home_dir ?????1 ????###使本地用戶有寫權限###
?
過程如下:
[root@localhost Desktop]# getenforce ????###selinux在Enforcing情況下默認不允許寫權限,因為可能會導致一些病毒***的可執行文件上傳,因此是不安全的###
Enforcing
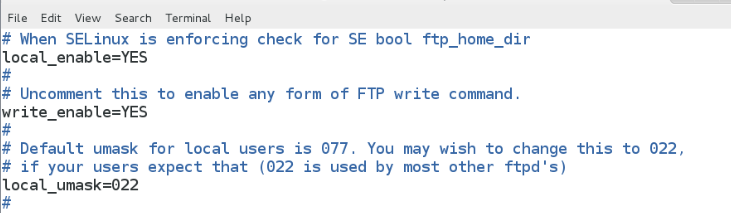
[root@localhost Desktop]# lftp 172.25.254.212 -u student ?##在配置文件允許上傳文件,但是沒有將setsebool打開情測試能否上傳###
?
Password:
lftp student@172.25.254.212:~> ls ?????
-rw-r--r-- ???1 1000 ????1000 ????????2048 Apr 23 05:45 passwd
lftp student@172.25.254.212:~> put /etc/passwd
put: Access failed: 553 Could not create file. (passwd) ??###上傳不了###
lftp student@172.25.254.212:~> quit
[root@localhost Desktop]# getsebool -a | grep ftp ??###查看
ftp_home_dir --> off
ftpd_anon_write --> off
ftpd_connect_all_unreserved --> off
ftpd_connect_db --> off
ftpd_full_access --> off
ftpd_use_cifs --> off
ftpd_use_fusefs --> off
ftpd_use_nfs --> off
ftpd_use_passive_mode --> off
httpd_can_connect_ftp --> off
httpd_enable_ftp_server --> off
sftpd_anon_write --> off
sftpd_enable_homedirs --> off
sftpd_full_access --> off
sftpd_write_ssh_home --> off
tftp_anon_write --> off
tftp_home_dir --> off
[root@localhost Desktop]# setsebool -P ftp_home_dir 1
[root@localhost Desktop]# getenforce
Enforcing
[root@localhost Desktop]# lftp 172.25.254.212 -u student
Password:
lftp student@172.25.254.212:~> ls ?????
-rw-r--r-- ???1 1000 ????1000 ????????2048 Apr 23 05:45 passwd
lftp student@172.25.254.212:~> put /etc/passwd
2048 bytes transferred
lftp student@172.25.254.212:~> ls
-rw-r--r-- ???1 1000 ????1000 ????????2048 Apr 29 02:09 passwd
轉載于:https://blog.51cto.com/12774272/1920403













)



)

環境配置)