一、數據接口分析
主頁地址:某得科技
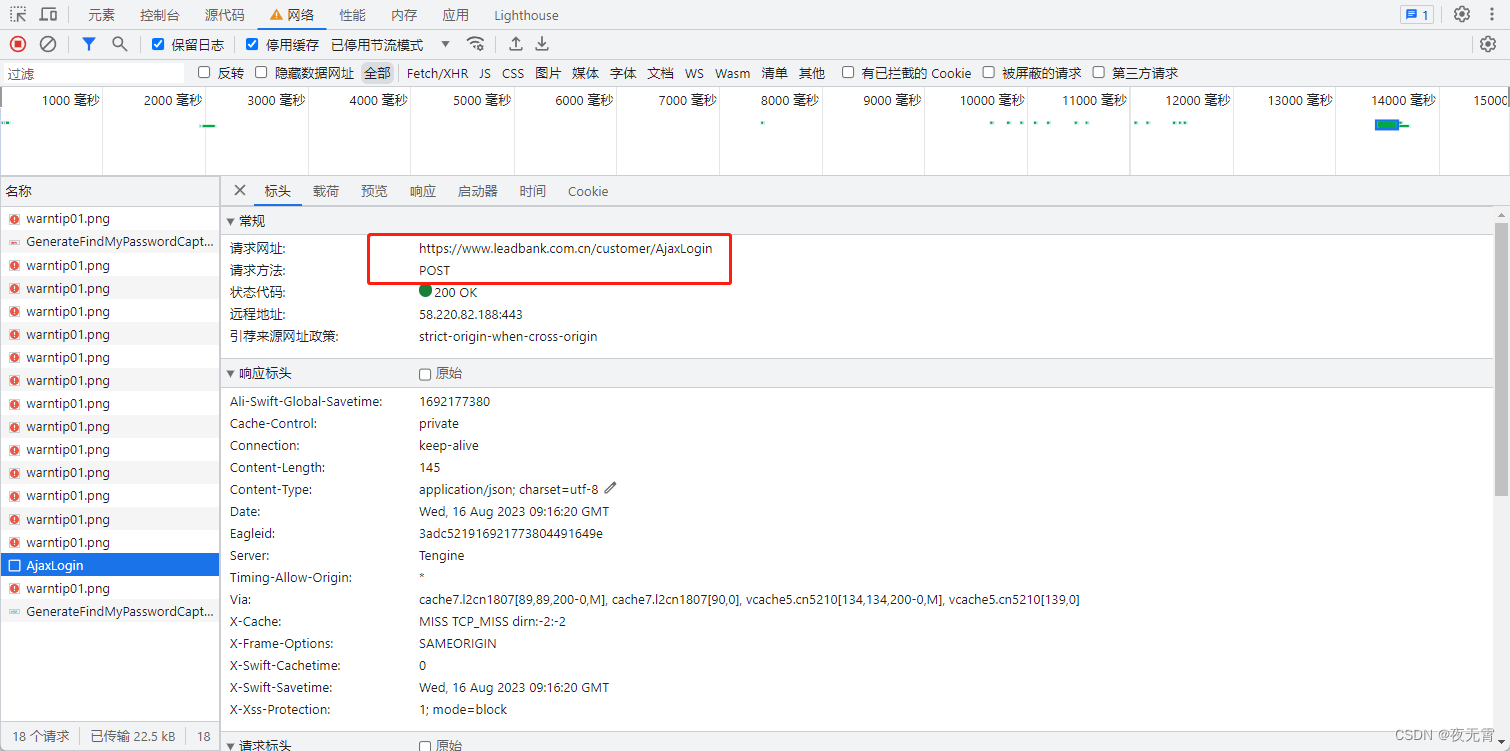
1、抓包
通過抓包可以發現數據接口是AjaxLogin
2、判斷是否有加密參數
-
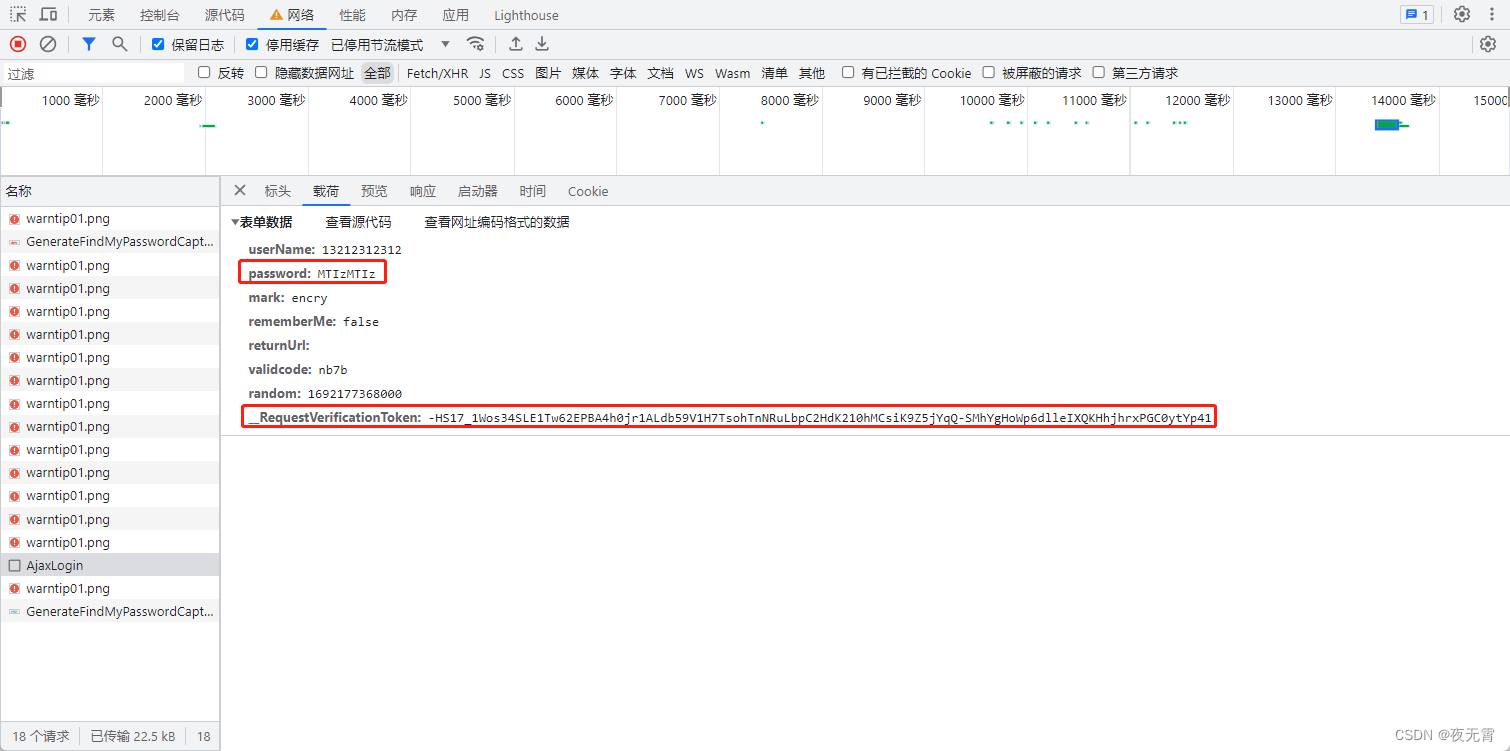
請求參數是否加密?
查看“載荷”模塊可以發現有一個password加密參數和一個__RequestVerificationToken
-
請求頭是否加密?
無 -
響應是否加密?
無 -
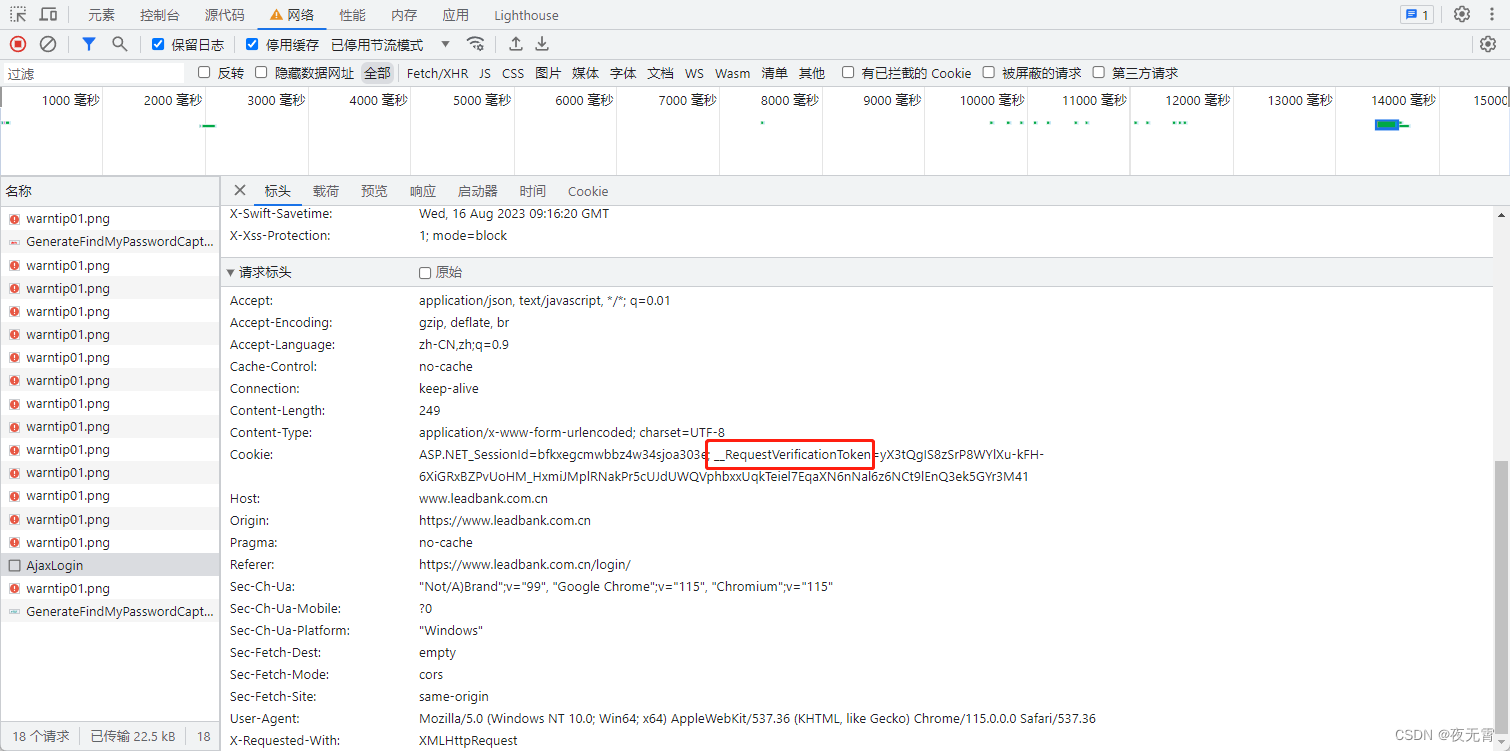
cookie是否加密?
查看cookie發現同樣有一個__RequestVerificationToken,但是與表單參數中的不同
二、加密位置定位
1、password
觀察表單中的加密參數password發現類似于base64轉碼,在控制臺進行測試,發現確實就是

2、表單參數__RequestVerificationToken
通過搜索關鍵字可以發現,表單中的__RequestVerificationToken是取的html靜態頁面中的數值

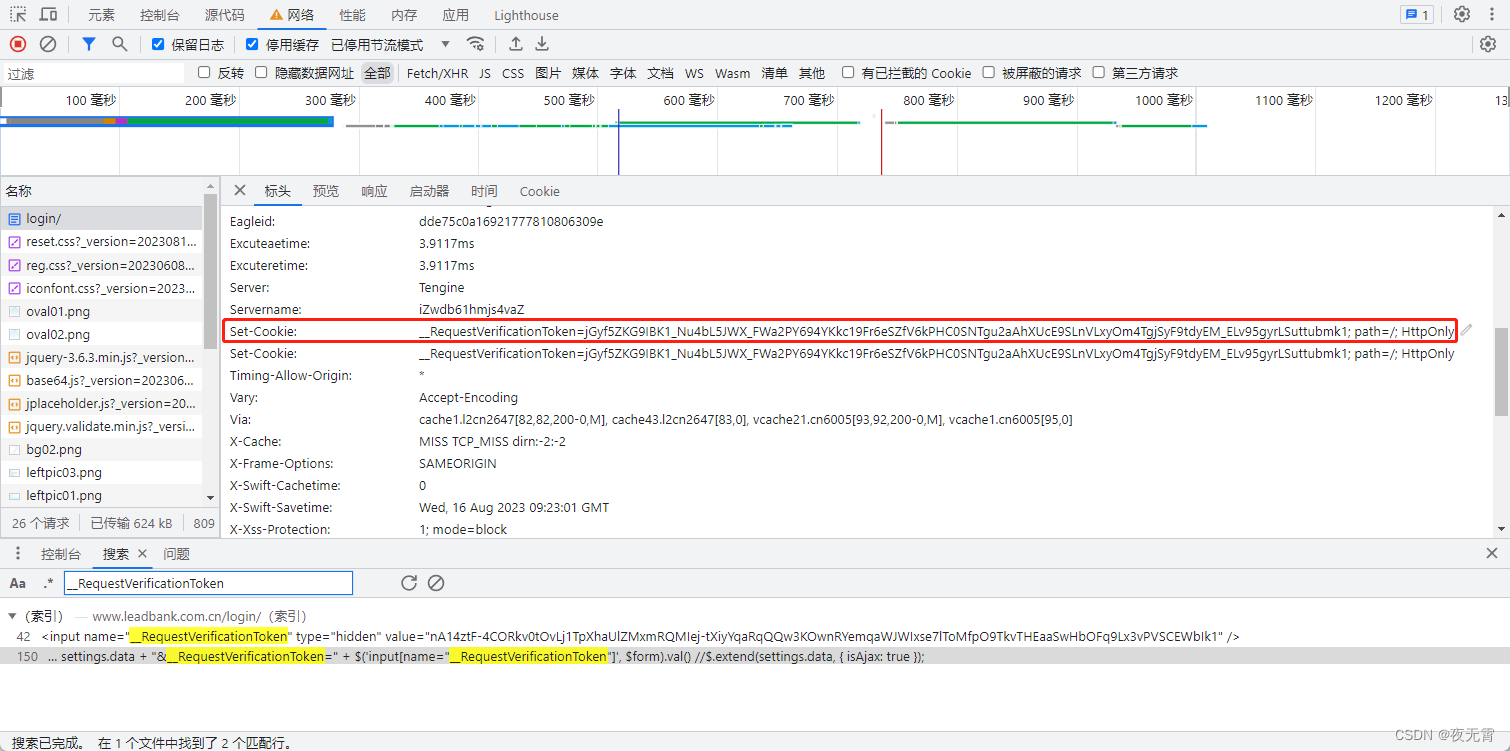
3、cookie中的__RequestVerificationToken
清除cookie之后刷新頁面,可以發現,是在請求靜態頁面時服務器設置的cookie
三、思路
首先請求html頁面,獲取到表單中的__RequestVerificationToken以及cookie,再根據獲取到數據發送登錄請求。
四、避坑
在發送請求時會遇到一個報錯
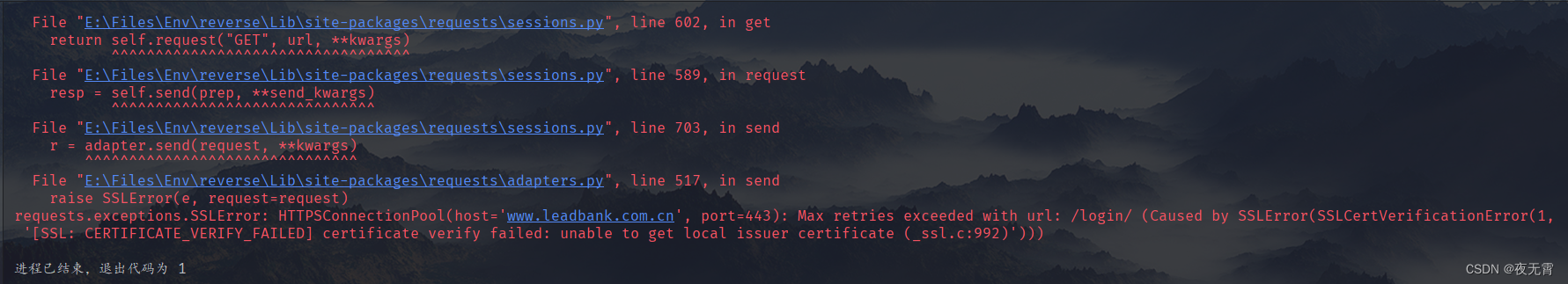
在發送請求時加上一個verify=False的參數就可以了
源代碼:
"""
Email:912917367@qq.com
Date: 2023/8/16 16:38
"""
import base64
import reimport requestsclass Spider:def __init__(self, username, password):self.session = requests.session()self.session.headers = {"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7","Accept-Language": "zh-CN,zh;q=0.9","Cache-Control": "no-cache","Connection": "keep-alive","Pragma": "no-cache","Sec-Fetch-Dest": "document","Sec-Fetch-Mode": "navigate","Sec-Fetch-Site": "none","Sec-Fetch-User": "?1","Upgrade-Insecure-Requests": "1","User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36","sec-ch-ua": "^\\^Not/A)Brand^^;v=^\\^99^^, ^\\^Google","sec-ch-ua-mobile": "?0","sec-ch-ua-platform": "^\\^Windows^^"}self.token = ''self.username = ''self.password = ''def get_token(self):url = "https://www.leadbank.com.cn/login/"# url = "https://www.baidu.com"response = self.session.get(url, verify=False)pattern = r'<input name="__RequestVerificationToken" type="hidden" value="(.*?)"'self.token = re.findall(pattern, response.text)[0]def login(self):encoded_bytes = base64.b64encode(self.password.encode('utf-8'))pwd = encoded_bytes.decode('utf-8')url = "https://www.leadbank.com.cn/customer/AjaxLogin"data = {"userName": self.username,"password": pwd,"mark": "encry","rememberMe": "false","returnUrl": "","validcode": "n948","random": "1692176276000","__RequestVerificationToken": self.token}response = self.session.post(url, data=data, verify=False)print(response.text)print(response)if __name__ == '__main__':s = Spider('賬號', '密碼')s.get_token()s.login()

)




)
)










NFS服務、DHCP服務)