前言:
?記得上半年還是去年,有道翻譯還是直接返回明文數據;現在也跟著,用接口返回加密數據了; 娛樂一下,破他的密文數據...
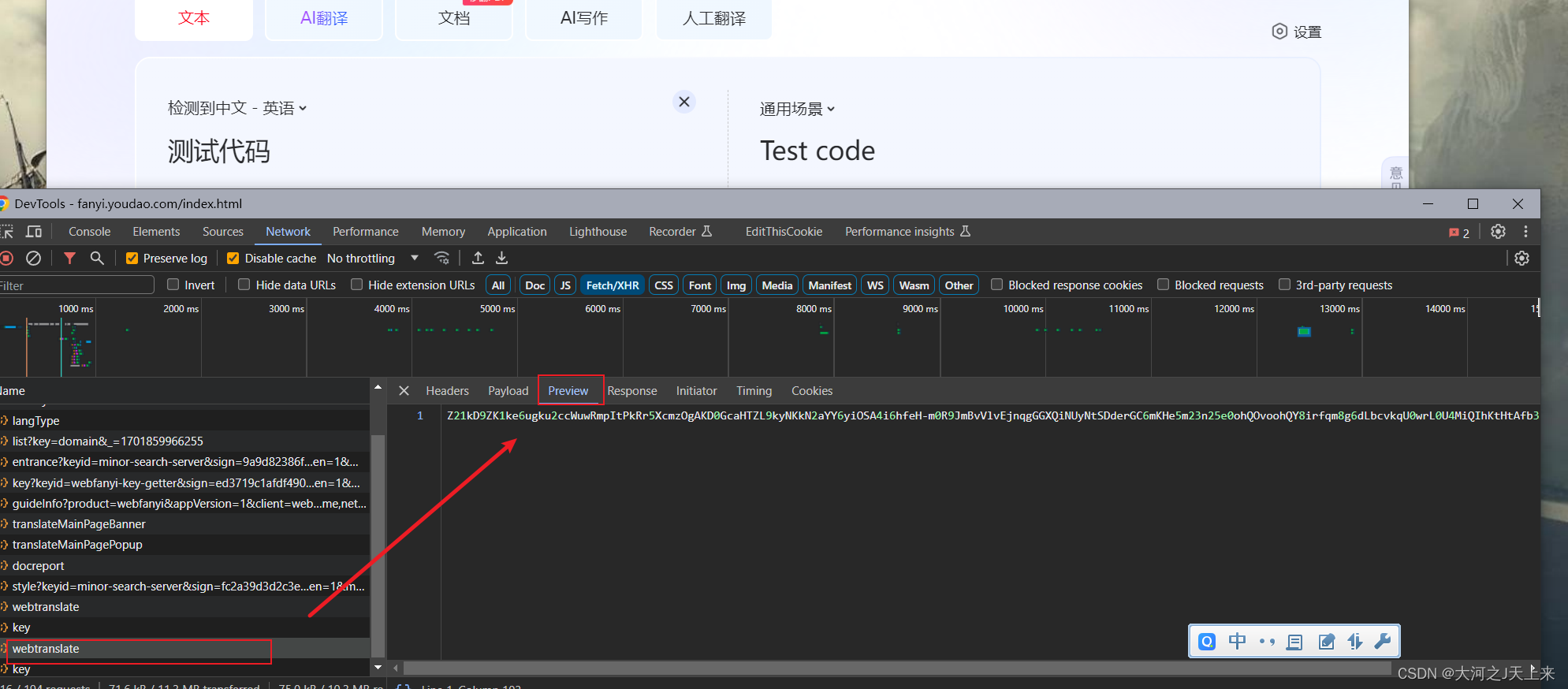
成品效果圖:
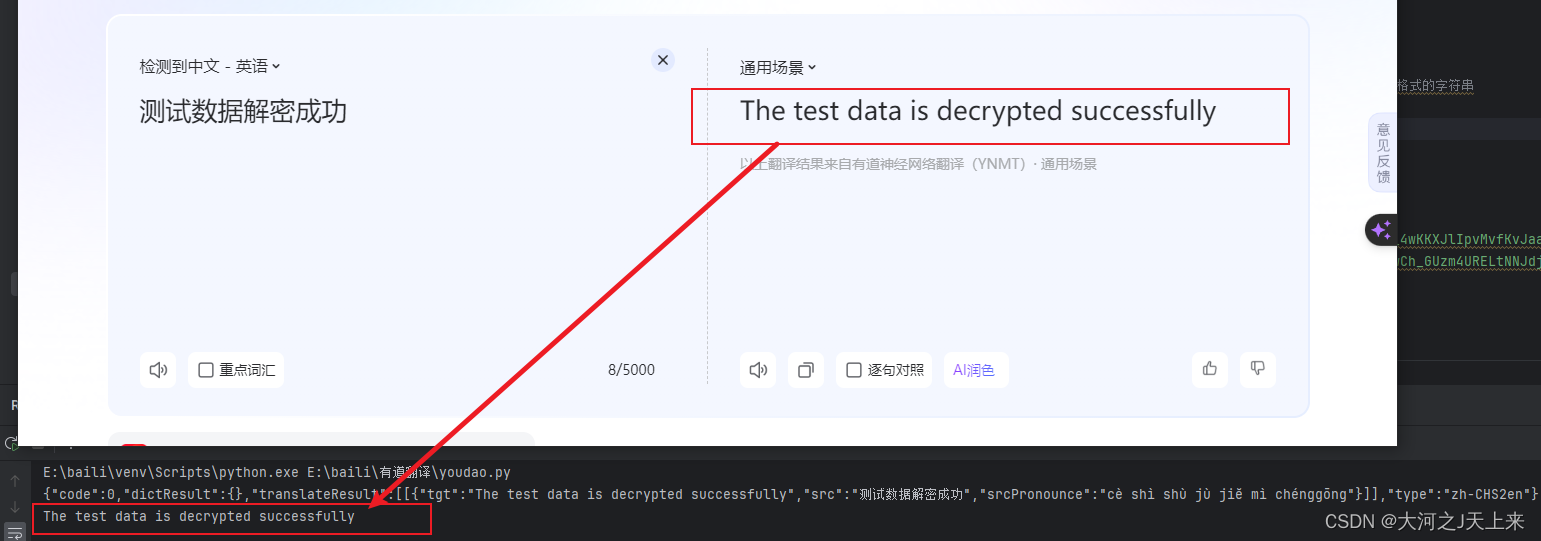
js部分:
對于找他的密文數據有點費時,針對密文--->搜他`地址`和`啟動器`不是特別容易,輾轉多時(搜:descrypt/json.parse 結合使用更快),有圖為證:

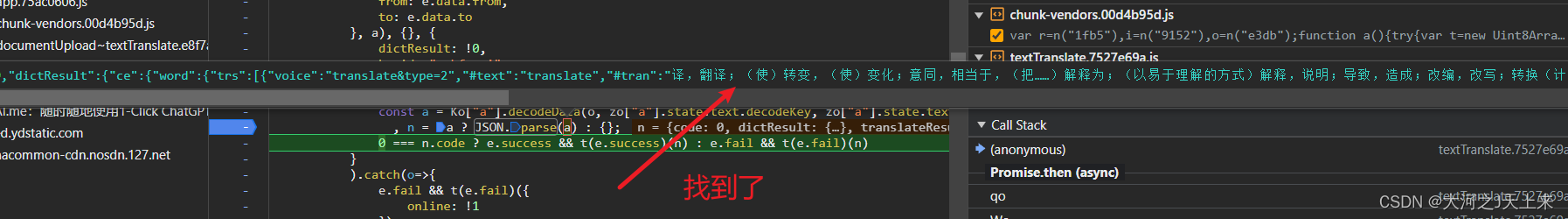
然后,對加密數據(發現他是aes加密...必須魔改)進行摳代碼:
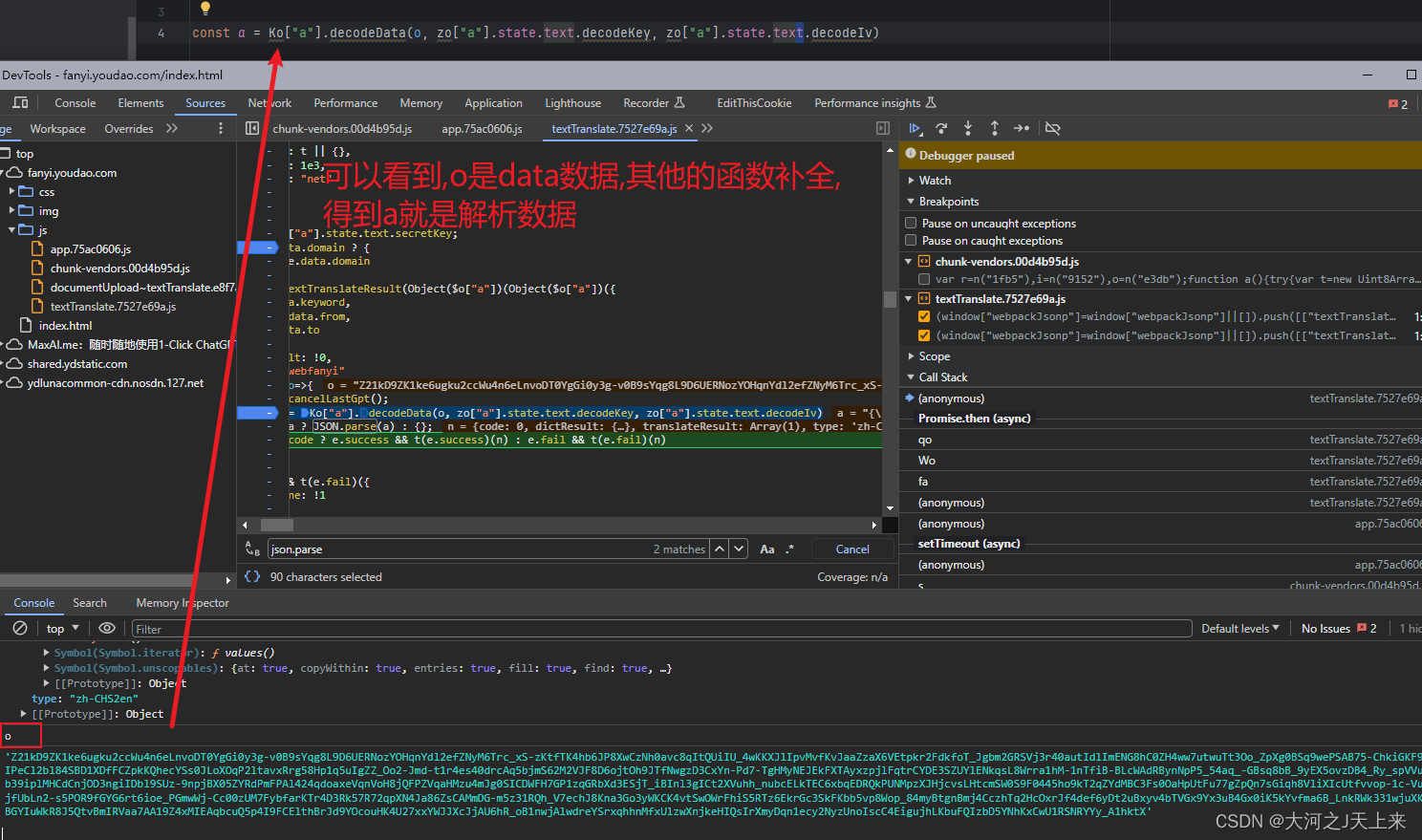
最終,自己魔改(原代碼很多,這是精簡后的版本---大家可以自行參照)完成:
const crypto = require('crypto');function f(t){if (!t) return null;// Buffer 對象用于 key 和 iv 參數const keyBuffer = Buffer.from([8,20,157,167,60,89,206,98,85,91,1,233,47,52,232,56]);const ivBuffer = Buffer.from([210,187,27,253,232,59,56,195,68,54,99,87,183,156,174,28]);// 使用 Buffer 對象let r = crypto.createDecipheriv("aes-128-cbc", keyBuffer, ivBuffer);let s = r.update(t, "base64", "utf-8");s += r.final("utf-8");return s;
}function jiemi(data) {return f(data)
}
針對這一塊,多次試驗發現,他的秘鑰和iv基本是固定的,所以直接套用了; 他的小坑就在于,如果你直接用他的代碼進行生成秘鑰和iv 就需要修改他的buffer格式...(這里有興趣的可以自己去摳摳試試)
最終:
import execjs
import jsonclass shengcheng():def __init__(self,data):self.data=datadef jiemi(self):mingwen = execjs.compile(open('shujujie.js', 'r', encoding='utf-8').read()).call('jiemi', self.data) #轉成銘文json格式的字符串print(mingwen) #用于篩選,需要的位置json_data = json.loads(mingwen) # 轉換為Python字典return json_data["translateResult"][0][0]["tgt"]#測試成功與否
data="Z21kD9ZK1ke6ugku2ccWu4n6eLnvoDT0YgGi0y3g-v0B9sYqg8L9D6UERNozYOHqnYdl2efZNyM6Trc_xS-zKtfTK4hb6JP8XwCzNh0avc8qItQUiIU_4wKKXJlIpvMvfKvJaaZzaX6VEtpkr2FdkfoT_Jgbm2GRSVj3r40autIdlImENG8hC0ZH4ww7utwuTt3Oo_ZpXg0BSq9wePSAB75-ChkiGKF9HTIPeCl2bl84SBD1XDfFCZpkKQhecYSs0JLoXOqP2ltavxRrg58Hp1q5uIgZZ_Oo2-Jmd-t1r4es40drcAq5bjmS62M2VJF8D6ojtOh9JTfNwgzD3CxYn-Pd7-TgHMyNEJEkFXTAyxzpjlFqtrCYDE3SZUYlENkqsL8Wrra1hM-1nTfiB-BLcWAdRBynNpP5_54aq_-GBsq8bB_9yEX5ovzDB4_Ry_spVVuUnb39iplMHCdCnjOD3ngiIDbl9SUz-9npjBX05ZYRdPmFPAl424qdoaxeVqnVoH8jQFPZVqaHMzu4mJg0SICDWFH7GP1zqGRbXd3ESjT_iBInl3gICt2XVuhh_nubcELkTEC6xbqEDRQkPUNMpzXJHjcvsLHtcmSW0S9F0445ho9kT2qZYdMBC3Fs0OaHpUtFu77gZpQn7sGiqh8VliXIcUtfvvop-1c-Vu5QjfUbLn2-s5POR9fGYG6rt6ioe_PGmwWj-Cc00zUM7FybfarKTr4D3Rk57R72qpXN4Ja86ZsCAMmDG-m5z31RQh_V7echJ8Kna3Go3yWKCK4vtSwOWrFhiS5RTz6EkrGc3SkFKbb5vp8Wop_84myBtgnBmj4CczhTq2HcOxrJf4def6yDt2uBxyv4bTVGx9Yx3uB4Gx0iK5kYvfma6B_LnkRWk331wjuXKQtBGYIuWkR8J5QtvBmIRVaa7AA19Z4xMIEAqbcuQ5p4I9FCElthBrJd9YOcouHK4U27xxYWJJXcJjAU6hR_oB1nwjAlwdreYSrxqhhnMfxUlzwXnjkeHIQsIrXmyDqn1ecy2NyzUnoIscC4EigujhLKbuFQIzbD5YNhKxCwU1RSNRYYy_A1hktX"
data1 ='Z21kD9ZK1ke6ugku2ccWuwRmpItPkRr5XcmzOgAKD0GcaHTZL9kyNKkN2aYY6yiOAuUGpZ7ENBTwF96PfL5x1bY7ml6fwu-TF83S-wOP7FZ-tPA2CwCh_GUzm4URELtNNJdjz8laGhynLZRmIDdXGzsyof5CH4f4HmMXalC1y1QFbY3YI7WOY_ESxSG7orHbOtDSUl2PIWETvdJNNr0s_igVhLaBVv9Eve_dur3bcenNl_7AbmsDj0kx8cyjkZWpWS0n7TkbUni6ZbeN99ClfQ=='
jie =shengcheng(data1).jiemi()
print(jie)經驗總結:
? 逆向web猶如盜墓,探龍點穴--->由大到小,從粗到細;耐心尋找他的棺槨位,然后....

)



)













