
Conference:ACM SIGSOFT International Symposium on Software Testing and Analysis (ISSTA)
CCF level:CCF A
Categories:Software Engineering/System Software/Programming Languages
Year:2023
第1~5篇區塊鏈文章 請點擊此處查看
6
Title:?
SmartState: Detecting State-Reverting Vulnerabilities in Smart Contracts via Fine-Grained State-Dependency Analysis
SmartState:通過細粒度狀態依賴性分析檢測智能合約中的狀態恢復漏洞
Authors:?

Key words:
bug finding, smart contract, static analysis, state dependency
bug查找、智能合約、靜態分析、狀態依賴
Abstract:?
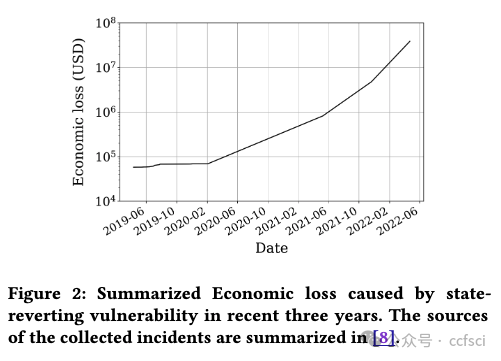
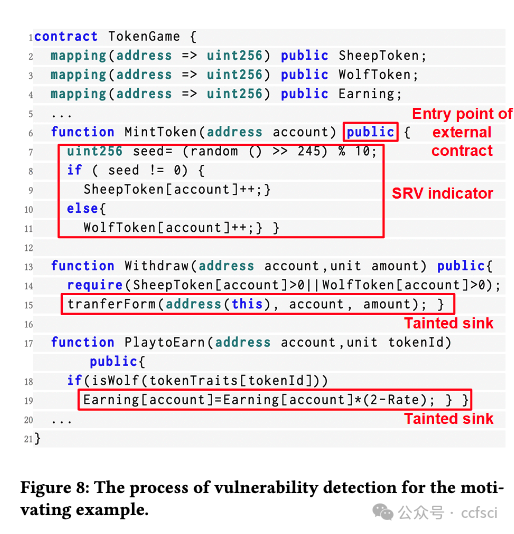
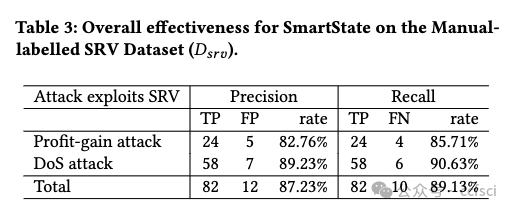
Smart contracts written in Solidity are widely used in different blockchain platforms such as Ethereum, TRON and BNB Chain. One of the unique designs in Solidity smart contracts is its statereverting mechanism for error handling and access control. Unfortunately, a number of recent security incidents showed that adversaries also utilize this mechanism to manipulate critical states of smart contracts, and hence, bring security consequences such as illegal profit-gain and Deny-of-Service (DoS). In this paper, we call such vulnerabilities as the State-reverting Vulnerability (SRV). Automatically identifying SRVs poses unique challenges, as it requires an in-depth analysis and understanding of the state-dependency relations in smart contracts. This paper presents SmartState, a new framework for detecting state-reverting vulnerability in Solidity smart contracts via finegrained state-dependency analysis. SmartState integrates a set of novel mechanisms to ensure its effectiveness. Particularly, Smart- State extracts state dependencies from both contract bytecode and historical transactions. Both of them are critical for inferring dependencies related to SRVs. Further, SmartState models the generic patterns of SRVs (i.e., profit-gain and DoS) as SRV indicators, and hence effectively identify SRVs based on the constructed statedependency graph. To evaluate SmartState, we manually annotated a ground-truth dataset which contains 91 SRVs in the real world. Evaluation results showed that SmartState achieves a precision of 87.23% and a recall of 89.13%. In addition, SmartState successfully identifies 406 new SRVs from 47,351 real-world smart contracts. 11 of these SRVs are from popular smart contracts with high transaction amounts (i.e., top 2000). In total, our reported SRVs affect a total amount of digital assets worth 428,600 USD.
用?Solidity?編寫的智能合約廣泛應用于以太坊、波場和 BNB Chain?等不同的區塊鏈平臺。Solidity 智能合約的獨特設計之一是其用于錯誤處理和訪問控制的狀態恢復機制。不幸的是,最近的一些安全事件表明,攻擊者還利用這種機制來操縱智能合約的關鍵狀態,從而帶來非法獲利和拒絕服務?(DoS) 等安全后果。在本文中,我們將此類漏洞稱為狀態恢復漏洞 (SRV)。自動識別 SRV 帶來了獨特的挑戰,因為它需要深入分析和理解智能合約中的狀態依賴關系。本文介紹了 SmartState,這是一種通過細粒度狀態依賴分析檢測 Solidity 智能合約中狀態恢復漏洞的新框架。SmartState 集成了一套新穎的機制來確保其有效性。特別是,Smart-State?從合約字節碼和歷史交易中提取狀態依賴關系。它們兩者對于推斷與 SRV 相關的依賴關系都至關重要。此外,SmartState 將 SRV 的通用模式(即利潤收益和 DoS)建模為 SRV 指標,從而根據構建的狀態依賴圖有效地識別 SRV。為了評估 SmartState,我們手動標注了一個包含現實世界中 91 個 SRV 的真實數據集。評估結果表明,SmartState 的準確率為 87.23%,召回率為 89.13%。此外,SmartState 還從 47,351 個現實世界智能合約中成功識別出 406 個新的 SRV。其中 11 個 SRV 來自交易金額較高的熱門智能合約(即前 2000 個)。總的來說,我們報告的 SRV 影響了總價值 428,600 美元的數字資產。




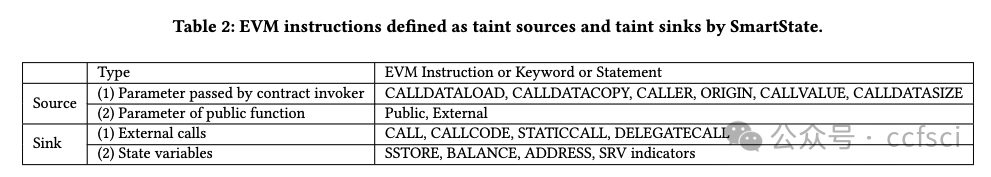
assertion-related state dependency (ASD)
temporal order state dependency (TSD)
Pdf link:
https://dl.acm.org/doi/10.1145/3597926.3598111
7
Title:?
Toward Automated Detecting Unanticipated Price Feed in Smart Contract
在智能合約中自動檢測意外價格饋送
Authors:?

Key words:
Smart Contract, Formal Verification, Price Oracle, DeFi
智能合約、形式化驗證、價格預言機、DeFi
Abstract:?
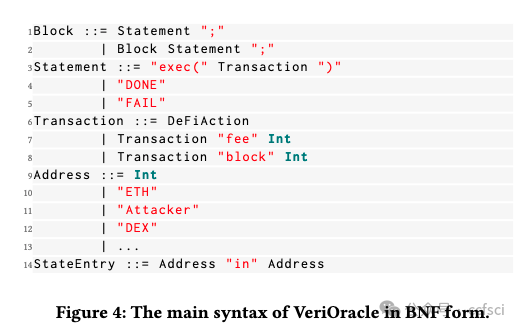
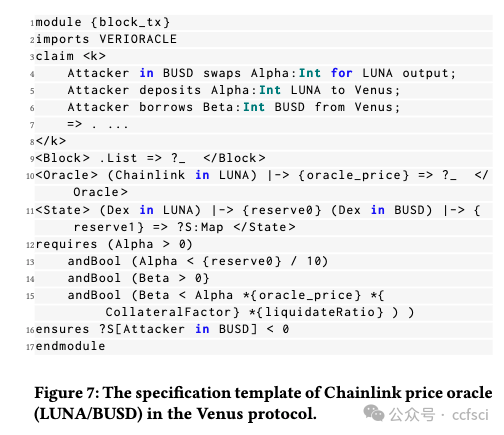
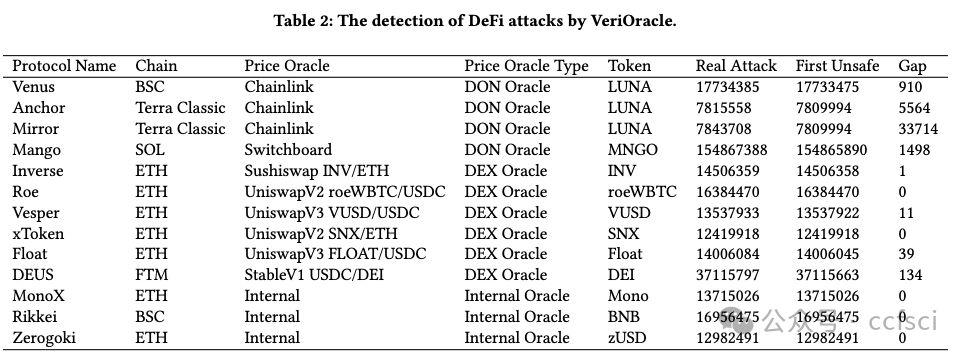
Decentralized finance (DeFi) based on smart contracts has reached a total value locked (TVL) of over USD 200 billion in 2022. In DeFi ecosystems, price oracles play a critical role in providing real-time price feeds for cryptocurrencies to ensure accurate asset pricing in smart contracts. However, the price oracle also faces security issues, including the possibility of unanticipated price feeds, which can lead to imbalances in debt and assets in the DeFi protocol. However, existing solutions cannot effectively combine transactions and code for real-time monitoring of price oracles. To address this limitation, we first categorize price oracles as either DON oracles, DEX oracles, or internal oracles based on trusted parties, and analyze their security risks, data sources, price duration, and query fees. Then, we propose VeriOracle, a formal verification framework for the automated detection of unanticipated price feeds in smart contracts. VeriOracle can deploy a formal semantic model of the price oracle on the blockchain to detect the status of smart contracts and identify unanticipated price feed transactions in real time. We apply VeriOracle to verify over 500,000 transactions of 13 vulnerable DeFi protocols in the real world. The experimental results show that (1) VeriOracle is effective and it can detect unanticipated price feeds before DeFi attacks (33,714 blocks ahead of the attacker in the best case); (2) VeriOracle is efficient in that its verification time (about 4s) is less than the block time of Ethereum (about 14s), which means VeriOracle can detect unsafe transactions in real time; and (3) VeriOracle is extendable for verifying defense strategies. Attacks using unanticipated price feeds can only succeed in particular smart contract states. VeriOracle can verify which smart contract states can defend against attacks.
基于智能合約的去中心化金融?(DeFi) 已在 2022 年達到超過 2000 億美元的總鎖定價值?(TVL)。在 DeFi 生態系統中,價格預言機在為加密貨幣提供實時價格信息以確保智能合約中資產定價準確方面發揮著關鍵作用。然而,價格預言機也面臨安全問題,包括可能出現意外的價格信息,這可能導致 DeFi 協議中的債務和資產不平衡。然而,現有的解決方案無法有效地結合交易和代碼來實時監控價格預言機。為了解決這一限制,我們首先根據可信方將價格預言機分類為?DON 預言機、DEX 預言機或內部預言機,并分析它們的安全風險、數據來源、價格持續時間和查詢費用。然后,我們提出了 VeriOracle,這是一個用于自動檢測智能合約中意外價格信息的形式化驗證框架。VeriOracle 可以在區塊鏈上部署價格預言機的形式化語義模型,以檢測智能合約的狀態并實時識別意外的價格饋送交易。我們應用 VeriOracle 驗證了現實世界中 13 個易受攻擊的 DeFi 協議的 500,000 多筆交易。實驗結果表明:(1)VeriOracle 是有效的,它可以在 DeFi 攻擊之前檢測到意外的價格饋送(最好情況下比攻擊者提前 33,714 個區塊);(2)VeriOracle 的驗證時間(約 4 秒)小于以太坊的出塊時間(約 14 秒),這意味著 VeriOracle 可以實時檢測不安全的交易;(3)VeriOracle 可擴展以驗證防御策略。使用意外價格饋送的攻擊只能在特定的智能合約狀態下成功。VeriOracle 可以驗證哪些智能合約狀態可以抵御攻擊。
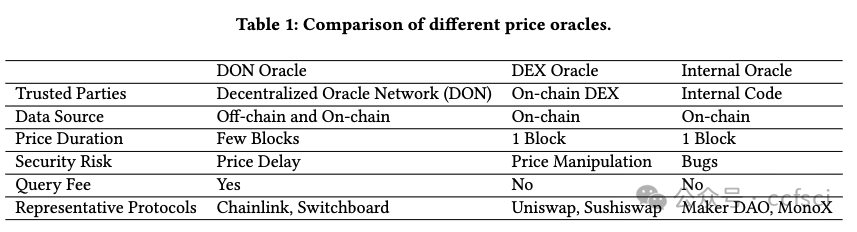
?decentralized exchanges (DEX)
Decentralized Oracle Networks (DONs)
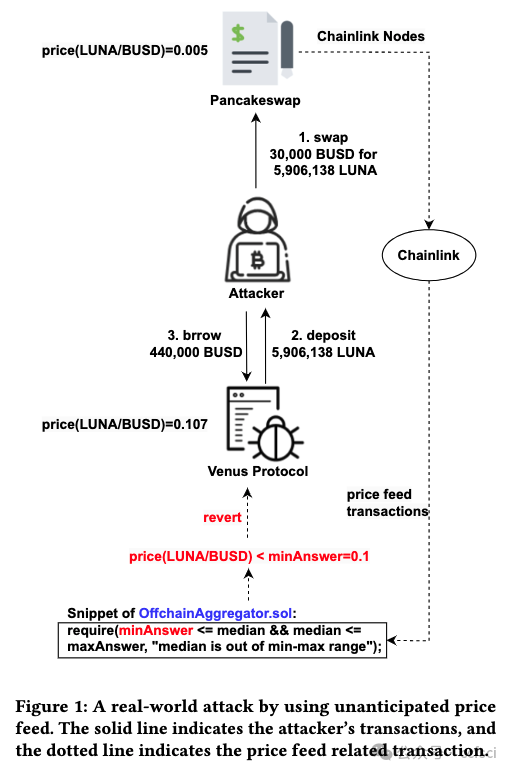
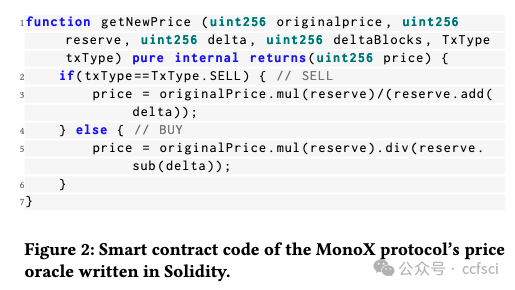
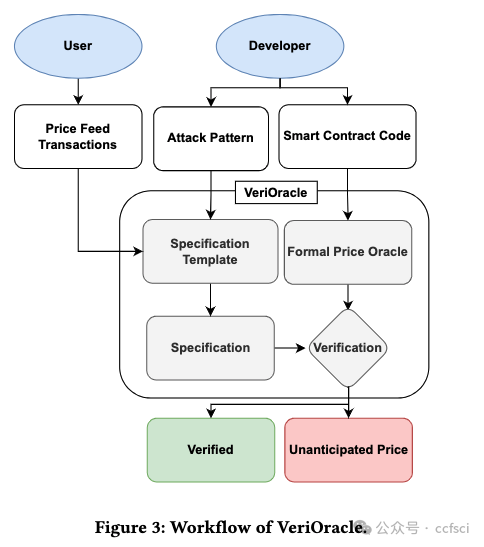

Pdf link:
https://dl.acm.org/doi/10.1145/3597926.3598133
8
Title:?
Detecting State Inconsistency Bugs in DApps via On-Chain Transaction Replay and Fuzzing
通過鏈上交易重放和模糊測試檢測 DApp 中的狀態不一致錯誤
Authors:?
Mingxi Ye,Sun Yat-sen University,China
Yuhong Nan,Sun Yat-sen University
Zibin Zheng,Sun Yat-sen University
Dongpeng Wu, Sun Yat-sen University
Huizhong Li, WeBank,China
Abstract:?
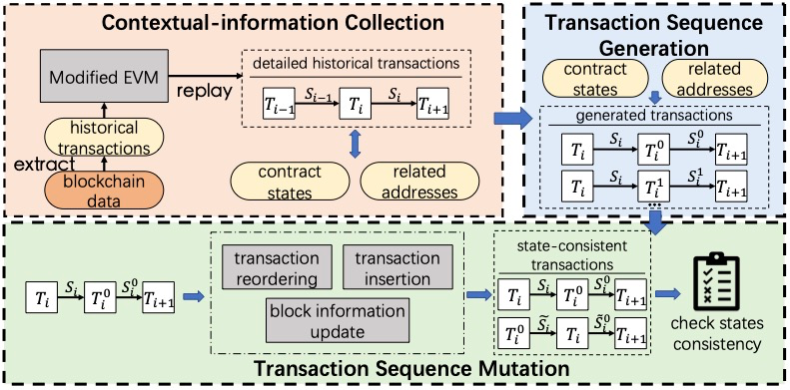
Decentralized applications (DApps) consist of multiple smart contracts running on Blockchain. With the increasing popularity of the DApp ecosystem, vulnerabilities in DApps could bring significant impacts such as financial losses. Identifying vulnerabilities in DApps is by no means trivial, as modern DApps consist of complex interactions across multiple contracts. Previous research suffers from either high false positives or false negatives, due to the lack of precise contextual information which is mandatory for confirming smart contract vulnerabilities when analyzing smart contracts. In this paper, we present IcyChecker, a new fuzzing-based framework to effectively identify State inconsistency (SI) Bugs – a specific type of bugs that can cause vulnerabilities such as re-entrancy, front-running with complex patterns. Different from prior works, IcyChecker utilizes a set of accurate contextual information for contract fuzzing by replaying the on-chain historical transactions. Besides, instead of designing specific testing oracles which are required by other fuzzing approaches, IcyChecker implements novel mechanisms to mutate a set of fuzzing transaction sequences, and further identify SI bugs by observing their state differences. Evaluation of IcyChecker over the top 100 popular DApps showed it effectively identifies a total number of 277 SI bugs, with a precision of 87%. By comparing IcyChecker with other state-of-the-art tools (i.e., Smartian, Confuzzius, and Sailfish), we show IcyChecker not only identifies more SI bugs but also with much lower false positives, thanks to its integration of accurate on-chain data and unique fuzzing strategies. Our research sheds light on new ways of detecting smart contract vulnerabilities in DApps.
?
去中心化應用程序(DApps)由在區塊鏈上運行的多個智能合約組成。隨著 DApp 生態系統的日益普及,DApp 中的漏洞可能會帶來重大影響,例如財務損失。識別 DApp 中的漏洞絕非易事,因為現代 DApp 包含跨多個合約的復雜交互。先前的研究存在高誤報率或漏報率,這是因為缺乏精確的上下文信息,而這些信息在分析智能合約時對于確認智能合約漏洞是必不可少的。在本文中,我們提出了?IcyChecker,這是一個基于模糊測試的新框架,可有效識別狀態不一致(SI)錯誤 - 這是一種特定類型的錯誤,可能導致諸如重入、具有復雜模式的搶先交易等漏洞。與之前的研究不同,IcyChecker 通過重放鏈上歷史交易,利用一組準確的上下文信息進行合約模糊測試。此外,IcyChecker 無需設計其他模糊測試方法所需的特定測試預言機,而是實現了新穎的機制來改變一組模糊測試交易序列,并通過觀察它們的狀態差異進一步識別 SI 錯誤。對前 100 個流行 DApp?的 IcyChecker 評估表明,它有效識別了總共 277 個 SI 錯誤,準確率為 87%。通過將 IcyChecker 與其他最先進的工具(即 Smartian、Confuzzius 和 Sailfish)進行比較,我們發現 IcyChecker 不僅可以識別出更多的 SI 錯誤,而且由于其集成了準確的鏈上數據和獨特的模糊測試策略,誤報率也低得多。我們的研究為檢測 DApp 中的智能合約漏洞的新方法提供了啟示。
Pdf link:
https://dl.acm.org/doi/10.1145/3597926.3598057
9
Title:?
DeFiTainter: Detecting Price Manipulation Vulnerabilities in DeFi Protocols
DeFiTainter:檢測 DeFi 協議中的價格操縱漏洞
Authors:?

Key words:
vulnerability detection, smart contract, taint analysis
漏洞檢測、智能合約、污點分析
Abstract:?
DeFi protocols are programs that manage high-value digital assets on blockchain. The price manipulation vulnerability is one of the common vulnerabilities in DeFi protocols, which allows attackers to gain excessive profits by manipulating token prices. In this paper, we propose DeFiTainter, an inter-contract taint analysis framework for detecting price manipulation vulnerabilities. DeFiTainter features two innovative mechanisms to ensure its effectiveness. The first mechanism is to construct a call graph for inter-contract taint analysis by restoring call information, not only from code constants but also from contract storage and function parameters. The second mechanism is a high-level semantic induction tailored for detecting price manipulation vulnerabilities, which accurately identifies taint sources and sinks and tracks taint data across contracts. Extensive evaluation of real-world incidents and high-value DeFi protocols shows that DeFiTainter outperforms existing approaches and achieves state-of-the-art performance with a precision of 96% and a recall of 91.3% in detecting price manipulation vulnerabilities. Furthermore, DeFiTainter uncovers three previously undisclosed price manipulation vulnerabilities.
DeFi 協議是管理區塊鏈上高價值數字資產的程序。價格操縱漏洞是 DeFi 協議中常見的漏洞之一,攻擊者可以通過操縱代幣價格獲取超額利潤。本文提出了 DeFiTainter,一個用于檢測價格操縱漏洞的合約間污點分析框架。DeFiTainter 具有兩種創新機制來確保其有效性。第一種機制是通過恢復調用信息來構建合約間污點分析的調用圖,不僅從代碼常量,而且從合約存儲和函數參數中恢復調用信息。第二種機制是專門為檢測價格操縱漏洞而定制的高級語義歸納,它可以準確識別污點源和污點接收器并跟蹤跨合約的污點數據。對現實世界事件和高價值 DeFi 協議的廣泛評估表明,DeFiTainter 優于現有方法,在檢測價格操縱漏洞方面以 96% 的準確率和 91.3% 的召回率實現了最先進的性能。此外,DeFiTainter 還發現了三個以前未披露的價格操縱漏洞。
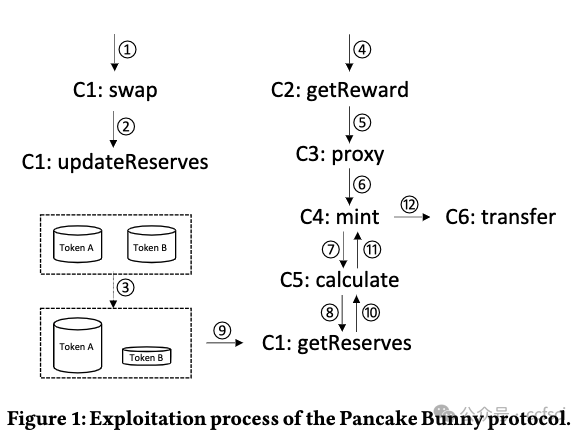

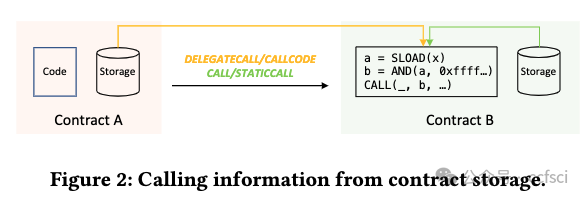
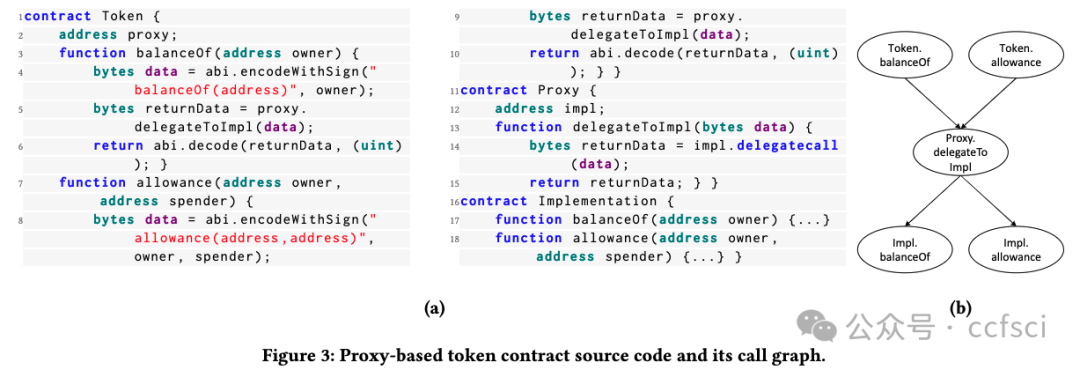

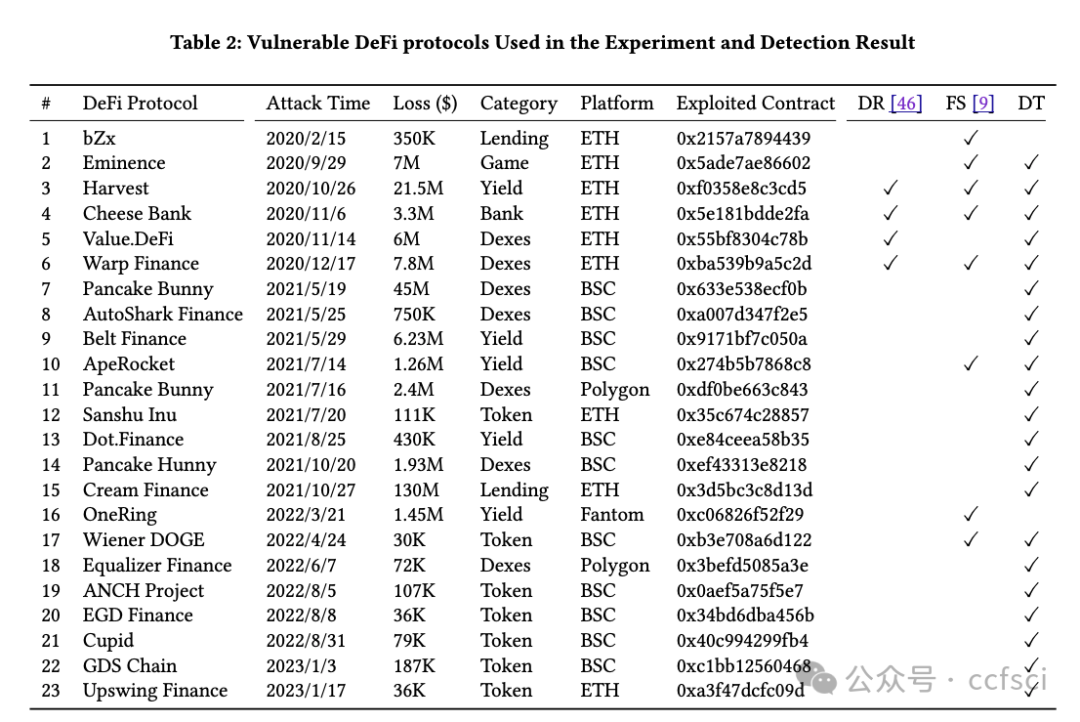
Pdf link:
https://dl.acm.org/doi/10.1145/3597926.3598124

關注我們,持續接收區塊鏈最新論文
洞察區塊鏈技術發展趨勢
Follow us to keep receiving the latest blockchain papers
Insight into Blockchain Technology Trends




)
)








)

)
: Access denied for user ‘root‘@‘localhost‘ (using password: NO))

